Best AI tools for< Cybersecurity Consultant >
Infographic
27 - AI tool Sites
Security Certificate Advisor
The website provides information about a privacy error related to a security certificate expiration for the IP address 147.139.135.71. It warns users about potential data theft and advises on correcting system clock settings. The site also mentions Certificate Transparency and offers options to enhance web security.
GetLuminal
GetLuminal.com is a website that provides information about a security certificate error related to the website itself. The site warns users about potential privacy risks and advises on actions to take when encountering such errors. It offers insights into security certificate expiration, potential threats from attackers, and guidance on system clock settings. Users can learn about security measures, certificate transparency, and how to enhance web security.
notionsmith.ai
The website notionsmith.ai appears to be experiencing a privacy error related to its security certificate. The error message indicates that the connection is not private and warns of potential information theft. The site's security certificate is issued by Microsoft Azure RSA TLS Issuing CA 08, with the subject *.azurewebsites.net. The error message suggests that the site's security certificate common name is invalid, potentially due to a misconfiguration or an attacker intercepting the connection. Users are advised to proceed to the site at their own risk, as it is flagged as unsafe.
chckr.io
The website chckr.io is experiencing a privacy error due to an expired security certificate. Users are warned that their connection may not be private, potentially exposing sensitive information to attackers. The site provides information about the security warning, certificate details, and suggestions to improve web security. It aims to enhance user awareness and security practices on the web.
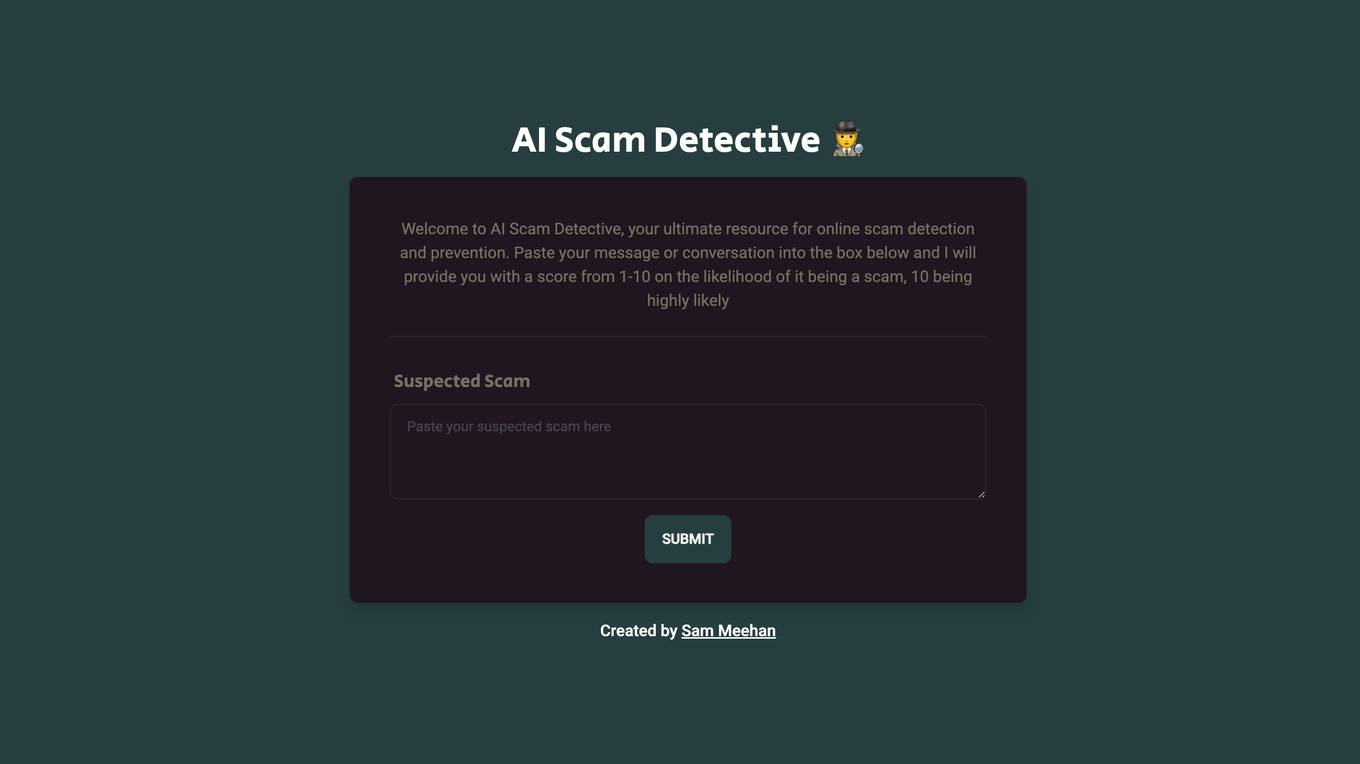
AI Scam Detective
AI Scam Detective is an AI tool designed to help users detect and prevent online scams. Users can input messages or conversations into the tool, which then provides a scam likelihood score from 1 to 10. The tool aims to empower users to identify potential scams and protect themselves from fraudulent activities. Created by Sam Meehan.

AitoCards
The website aitocards.com seems to be facing a privacy error related to its SSL certificate. The error message indicates that the connection is not private and warns about potential attackers trying to steal sensitive information such as passwords, messages, or credit card details. The certificate in question is issued by cloudflare-dns.com, and the warning suggests that the site's security certificate is invalid. Users are advised to proceed to the site at their own risk, as it may be unsafe due to a potential misconfiguration or interception by an attacker.
medium.engineering
medium.engineering is a website that focuses on verifying the security of user connections before allowing access to its content. It ensures that users are human by conducting a verification process that may take a few seconds. The site emphasizes the importance of enabling JavaScript and cookies for a seamless browsing experience. Powered by Cloudflare, medium.engineering prioritizes performance and security in delivering its services.
CopyCopAI
CopyCopAI.com is an AI-powered tool designed to assist users in verifying their identity and ensuring secure connections. The tool performs security checks to prevent unauthorized access and protect user data. By enabling JavaScript and cookies, users can proceed with the verification process. CopyCopAI.com leverages AI technology to enhance performance and security, with the support of Cloudflare services.
dexa.ai
dexa.ai is an AI-powered platform that focuses on security verification for user connections. It ensures a secure browsing experience by reviewing and verifying the security of connections before allowing access. The platform utilizes AI algorithms to detect and prevent potential security threats, providing users with a safe online environment. dexa.ai prioritizes performance and security, leveraging Cloudflare technology to enhance protection and speed for users.

www.atom.com
The website www.atom.com is a platform that provides security verification services to ensure a safe and secure connection for users. It verifies the authenticity of users by checking for human interaction, enabling JavaScript and cookies, and reviewing the security of connections. The platform is powered by Cloudflare to enhance performance and security measures.

chat.baseflow.io
The website chat.baseflow.io is experiencing a privacy error, indicating that the connection is not secure. Users are warned that attackers might be trying to steal sensitive information such as passwords, messages, or credit cards. The error message suggests that the security certificate for the website is not trusted by the user's computer's operating system, potentially due to misconfiguration or a security breach. The site advises users to proceed with caution and offers options to enhance security.
Privacy Observer
Privacy Observer is an AI-powered tool that makes privacy accessible by scanning and analyzing privacy policies of websites. It helps users understand when websites request excessive personal information without the need to read lengthy policies. The tool provides a detailed score for each website, ensuring users can make informed decisions about their online privacy. With features like unlimited background scans, anonymous checks by humans, and a user-friendly browser extension, Privacy Observer aims to empower users to protect their privacy online.
ForbiddenGuard
The website is currently displaying a '403 Forbidden' error, which indicates that the server is refusing to respond to the request. This error message is typically shown when the server understands the request made by the client but refuses to fulfill it. The 'openresty' mentioned in the text is likely the web server software being used. It is important to troubleshoot and resolve the 403 Forbidden error to regain access to the desired content on the website.
Pentest Copilot
Pentest Copilot by BugBase is an ultimate ethical hacking assistant that guides users through each step of the hacking journey, from analyzing web apps to root shells. It eliminates redundant research, automates payload and command generation, and provides intelligent contextual analysis to save time. The application excels at data extraction, privilege escalation, lateral movement, and leaving no trace behind. With features like secure VPN integration, total control over sessions, parallel command processing, and flexibility to choose between local or cloud execution, Pentest Copilot offers a seamless and efficient hacking experience without the need for Kali Linux installation.
klu.ai
klu.ai is an AI-powered platform that focuses on security verification for online connections. It ensures a safe browsing experience by reviewing and enhancing the security measures of the user's connection. The platform utilizes advanced algorithms to detect and prevent potential threats, providing users with a secure environment for their online activities.
ZeroGPTDetector
ZeroGPTDetector is a website that focuses on verifying human users and ensuring secure connections. It performs security checks to prevent automated bots from accessing the site. Users may encounter a brief waiting period during the verification process. The site utilizes JavaScript and cookies for seamless browsing. Powered by Cloudflare, ZeroGPTDetector prioritizes performance and security for a safe online experience.
Aura
Aura is an all-in-one digital safety platform that uses artificial intelligence (AI) to protect your family online. It offers a wide range of features, including financial fraud protection, identity theft protection, VPN & online privacy, antivirus, password manager & smart vault, parental controls & safe gaming, and spam call protection. Aura is easy to use and affordable, and it comes with a 60-day money-back guarantee.
Concentric AI
Concentric AI is a Managed Data Security Posture Management tool that utilizes Semantic Intelligence to provide comprehensive data security solutions. The platform offers features such as autonomous data discovery, data risk identification, centralized remediation, easy deployment, and data security posture management. Concentric AI helps organizations protect sensitive data, prevent data loss, and ensure compliance with data security regulations. The tool is designed to simplify data governance and enhance data security across various data repositories, both in the cloud and on-premises.
NodeZero™ Platform
Horizon3.ai Solutions offers the NodeZero™ Platform, an AI-powered autonomous penetration testing tool designed to enhance cybersecurity measures. The platform combines expert human analysis by Offensive Security Certified Professionals with automated testing capabilities to streamline compliance processes and proactively identify vulnerabilities. NodeZero empowers organizations to continuously assess their security posture, prioritize fixes, and verify the effectiveness of remediation efforts. With features like internal and external pentesting, rapid response capabilities, AD password audits, phishing impact testing, and attack research, NodeZero is a comprehensive solution for large organizations, ITOps, SecOps, security teams, pentesters, and MSSPs. The platform provides real-time reporting, integrates with existing security tools, reduces operational costs, and helps organizations make data-driven security decisions.
Traceable
Traceable is an AI-driven application designed to enhance API security for Cloud-Native Apps. It collects API traffic across the application landscape and utilizes advanced context-based behavioral analytics AI engine to provide insights on APIs, data exposure, threat analytics, and forensics. The platform offers features for API cataloging, activity monitoring, endpoint details, ownership, vulnerabilities, protection against security events, testing, analytics, and more. Traceable also allows for role-based access control, policy configuration, data classification, and integration with third-party solutions for data collection and security. It is a comprehensive tool for API security and threat detection in modern cloud environments.
Coalition for Secure AI (CoSAI)
The Coalition for Secure AI (CoSAI) is an open ecosystem of AI and security experts dedicated to sharing best practices for secure AI deployment and collaborating on AI security research and product development. It aims to foster a collaborative ecosystem of diverse stakeholders to invest in AI security research collectively, share security expertise and best practices, and build technical open-source solutions for secure AI development and deployment.

Traceable
Traceable is an intelligent API security platform designed for enterprise-scale security. It offers unmatched API discovery, attack detection, threat hunting, and infinite scalability. The platform provides comprehensive protection against API attacks, fraud, and bot security, along with API testing capabilities. Powered by Traceable's OmniTrace Engine, it ensures unparalleled security outcomes, remediation, and pre-production testing. Security teams trust Traceable for its speed and effectiveness in protecting API infrastructures.
CloudDefense.AI
CloudDefense.AI is an industry-leading multi-layered Cloud Native Application Protection Platform (CNAPP) that safeguards cloud infrastructure and cloud-native apps with expertise, precision, and confidence. It offers comprehensive cloud security solutions, vulnerability management, compliance, and application security testing. The platform utilizes advanced AI technology to proactively detect and analyze real-time threats, ensuring robust protection for businesses against cyber threats.

Dropzone AI
Dropzone AI is an award-winning AI application designed to reinforce Security Operations Centers (SOCs) by providing autonomous AI analysts. It replicates the techniques of elite analysts to autonomously investigate alerts, covering various use cases such as phishing, endpoint, network, cloud, identity, and insider threats. The application offers pre-trained AI agents that work alongside human analysts, automating investigation tasks and providing fast, detailed, and accurate reports. With built-in integrations with major security tools, Dropzone AI aims to reduce Mean Time to Respond (MTTR) and allow analysts to focus on addressing real threats.
Alston & Bird Privacy, Cyber & Data Strategy Blog
Alston & Bird Privacy, Cyber & Data Strategy Blog is an AI tool that provides insights and updates on key data privacy, cybersecurity issues, and regulations. The blog covers a wide range of topics such as COPPA Rule amendments, AI advisory in healthcare, DHS Playbook for AI deployment, cybersecurity sanctions, and data breach notification laws. It aims to keep readers informed about the latest developments in privacy, cyber, and data strategy.
Varonis
Varonis is an AI-powered data security platform that provides end-to-end data security solutions for organizations. It offers automated outcomes to reduce risk, enforce policies, and stop active threats. Varonis helps in data discovery & classification, data security posture management, data-centric UEBA, data access governance, and data loss prevention. The platform is designed to protect critical data across multi-cloud, SaaS, hybrid, and AI environments.
AI QA Monkey
AI QA Monkey is a free website security scanner that offers instant security audits to check website security scores. The tool scans for vulnerabilities such as leaked sensitive data, open ports, passwords, .env files, and WordPress vulnerabilities. It provides a detailed security report with actionable insights and AI-powered fixes. Users can export reports in PDF, JSON, or CSV formats. AI QA Monkey is designed to help businesses improve their security posture and comply with GDPR regulations.
37 - Open Source Tools

last_layer
last_layer is a security library designed to protect LLM applications from prompt injection attacks, jailbreaks, and exploits. It acts as a robust filtering layer to scrutinize prompts before they are processed by LLMs, ensuring that only safe and appropriate content is allowed through. The tool offers ultra-fast scanning with low latency, privacy-focused operation without tracking or network calls, compatibility with serverless platforms, advanced threat detection mechanisms, and regular updates to adapt to evolving security challenges. It significantly reduces the risk of prompt-based attacks and exploits but cannot guarantee complete protection against all possible threats.

aircrack-ng
Aircrack-ng is a comprehensive suite of tools designed to evaluate the security of WiFi networks. It covers various aspects of WiFi security, including monitoring, attacking (replay attacks, deauthentication, fake access points), testing WiFi cards and driver capabilities, and cracking WEP and WPA PSK. The tools are command line-based, allowing for extensive scripting and have been utilized by many GUIs. Aircrack-ng primarily works on Linux but also supports Windows, macOS, FreeBSD, OpenBSD, NetBSD, Solaris, and eComStation 2.

reverse-engineering-assistant
ReVA (Reverse Engineering Assistant) is a project aimed at building a disassembler agnostic AI assistant for reverse engineering tasks. It utilizes a tool-driven approach, providing small tools to the user to empower them in completing complex tasks. The assistant is designed to accept various inputs, guide the user in correcting mistakes, and provide additional context to encourage exploration. Users can ask questions, perform tasks like decompilation, class diagram generation, variable renaming, and more. ReVA supports different language models for online and local inference, with easy configuration options. The workflow involves opening the RE tool and program, then starting a chat session to interact with the assistant. Installation includes setting up the Python component, running the chat tool, and configuring the Ghidra extension for seamless integration. ReVA aims to enhance the reverse engineering process by breaking down actions into small parts, including the user's thoughts in the output, and providing support for monitoring and adjusting prompts.

AutoAudit
AutoAudit is an open-source large language model specifically designed for the field of network security. It aims to provide powerful natural language processing capabilities for security auditing and network defense, including analyzing malicious code, detecting network attacks, and predicting security vulnerabilities. By coupling AutoAudit with ClamAV, a security scanning platform has been created for practical security audit applications. The tool is intended to assist security professionals with accurate and fast analysis and predictions to combat evolving network threats.
aif
Arno's Iptables Firewall (AIF) is a single- & multi-homed firewall script with DSL/ADSL support. It is a free software distributed under the GNU GPL License. The script provides a comprehensive set of configuration files and plugins for setting up and managing firewall rules, including support for NAT, load balancing, and multirouting. It offers detailed instructions for installation and configuration, emphasizing security best practices and caution when modifying settings. The script is designed to protect against hostile attacks by blocking all incoming traffic by default and allowing users to configure specific rules for open ports and network interfaces.

watchtower
AIShield Watchtower is a tool designed to fortify the security of AI/ML models and Jupyter notebooks by automating model and notebook discoveries, conducting vulnerability scans, and categorizing risks into 'low,' 'medium,' 'high,' and 'critical' levels. It supports scanning of public GitHub repositories, Hugging Face repositories, AWS S3 buckets, and local systems. The tool generates comprehensive reports, offers a user-friendly interface, and aligns with industry standards like OWASP, MITRE, and CWE. It aims to address the security blind spots surrounding Jupyter notebooks and AI models, providing organizations with a tailored approach to enhancing their security efforts.

Academic_LLM_Sec_Papers
Academic_LLM_Sec_Papers is a curated collection of academic papers related to LLM Security Application. The repository includes papers sorted by conference name and published year, covering topics such as large language models for blockchain security, software engineering, machine learning, and more. Developers and researchers are welcome to contribute additional published papers to the list. The repository also provides information on listed conferences and journals related to security, networking, software engineering, and cryptography. The papers cover a wide range of topics including privacy risks, ethical concerns, vulnerabilities, threat modeling, code analysis, fuzzing, and more.
DeGPT
DeGPT is a tool designed to optimize decompiler output using Large Language Models (LLM). It requires manual installation of specific packages and setting up API key for OpenAI. The tool provides functionality to perform optimization on decompiler output by running specific scripts.
AirGuard
AirGuard is an anti-tracking protection app designed to protect Android users from being tracked by AirTags and other Find My devices. The app periodically scans the surroundings for potential tracking devices and notifies the user if being followed. Users can play a sound on AirTags, view tracked locations, and participate in a research study on privacy protection. AirGuard does not monetize through ads or in-app purchases and ensures all tracking detection and notifications happen locally on the user's device.
awesome-llm-security
Awesome LLM Security is a curated collection of tools, documents, and projects related to Large Language Model (LLM) security. It covers various aspects of LLM security including white-box, black-box, and backdoor attacks, defense mechanisms, platform security, and surveys. The repository provides resources for researchers and practitioners interested in understanding and safeguarding LLMs against adversarial attacks. It also includes a list of tools specifically designed for testing and enhancing LLM security.
PentestGPT
PentestGPT provides advanced AI and integrated tools to help security teams conduct comprehensive penetration tests effortlessly. Scan, exploit, and analyze web applications, networks, and cloud environments with ease and precision, without needing expert skills. The tool utilizes Supabase for data storage and management, and Vercel for hosting the frontend. It offers a local quickstart guide for running the tool locally and a hosted quickstart guide for deploying it in the cloud. PentestGPT aims to simplify the penetration testing process for security professionals and enthusiasts alike.
AI-Security-and-Privacy-Events
AI-Security-and-Privacy-Events is a curated list of academic events focusing on AI security and privacy. It includes seminars, conferences, workshops, tutorials, special sessions, and covers various topics such as NLP & LLM Security, Privacy and Security in ML, Machine Learning Security, AI System with Confidential Computing, Adversarial Machine Learning, and more.
openshield
OpenShield is a firewall designed for AI models to protect against various attacks such as prompt injection, insecure output handling, training data poisoning, model denial of service, supply chain vulnerabilities, sensitive information disclosure, insecure plugin design, excessive agency granting, overreliance, and model theft. It provides rate limiting, content filtering, and keyword filtering for AI models. The tool acts as a transparent proxy between AI models and clients, allowing users to set custom rate limits for OpenAI endpoints and perform tokenizer calculations for OpenAI models. OpenShield also supports Python and LLM based rules, with upcoming features including rate limiting per user and model, prompts manager, content filtering, keyword filtering based on LLM/Vector models, OpenMeter integration, and VectorDB integration. The tool requires an OpenAI API key, Postgres, and Redis for operation.
cheating-based-prompt-engine
This is a vulnerability mining engine purely based on GPT, requiring no prior knowledge base, no fine-tuning, yet its effectiveness can overwhelmingly surpass most of the current related research. The core idea revolves around being task-driven, not question-driven, driven by prompts, not by code, and focused on prompt design, not model design. The essence is encapsulated in one word: deception. It is a type of code understanding logic vulnerability mining that fully stimulates the capabilities of GPT, suitable for real actual projects.

GhidrOllama
GhidrOllama is a script that interacts with Ollama's API to perform various reverse engineering tasks within Ghidra. It supports both local and remote instances of Ollama, providing functionalities like explaining functions, suggesting names, rewriting functions, finding bugs, and automating analysis of specific functions in binaries. Users can ask questions about functions, find vulnerabilities, and receive explanations of assembly instructions. The script bridges the gap between Ghidra and Ollama models, enhancing reverse engineering capabilities.

air-script
Air Script is a versatile tool designed for Wi-Fi penetration testing, offering automated and user-friendly features to streamline the hacking process. It allows users to easily capture handshakes from nearby networks, automate attacks, and even send email notifications upon completion. The tool is ideal for individuals looking to efficiently pwn Wi-Fi networks without extensive manual input. With additional tools and options available, Air Script caters to a wide range of users, including script kiddies, hackers, pentesters, and security researchers. Whether on the go or using a Raspberry Pi, Air Script provides a convenient solution for network penetration testing and password cracking.
garak
Garak is a vulnerability scanner designed for LLMs (Large Language Models) that checks for various weaknesses such as hallucination, data leakage, prompt injection, misinformation, toxicity generation, and jailbreaks. It combines static, dynamic, and adaptive probes to explore vulnerabilities in LLMs. Garak is a free tool developed for red-teaming and assessment purposes, focusing on making LLMs or dialog systems fail. It supports various LLM models and can be used to assess their security and robustness.
burpference
Burpference is an open-source extension designed to capture in-scope HTTP requests and responses from Burp's proxy history and send them to a remote LLM API in JSON format. It automates response capture, integrates with APIs, optimizes resource usage, provides color-coded findings visualization, offers comprehensive logging, supports native Burp reporting, and allows flexible configuration. Users can customize system prompts, API keys, and remote hosts, and host models locally to prevent high inference costs. The tool is ideal for offensive web application engagements to surface findings and vulnerabilities.
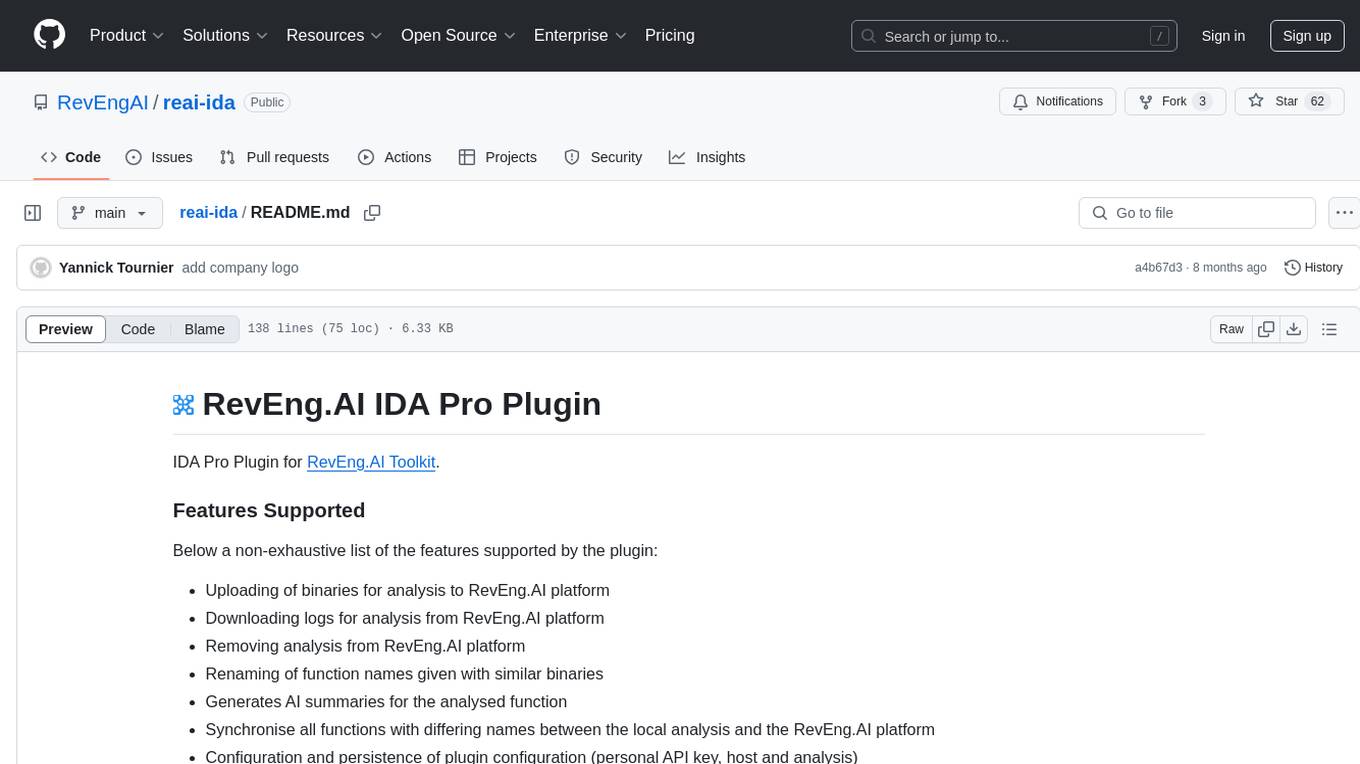
reai-ida
RevEng.AI IDA Pro Plugin is a tool that integrates with the RevEng.AI platform to provide various features such as uploading binaries for analysis, downloading analysis logs, renaming function names, generating AI summaries, synchronizing functions between local analysis and the platform, and configuring plugin settings. Users can upload files for analysis, synchronize function names, rename functions, generate block summaries, and explain function behavior using this plugin. The tool requires IDA Pro v8.0 or later with Python 3.9 and higher. It relies on the 'reait' package for functionality.
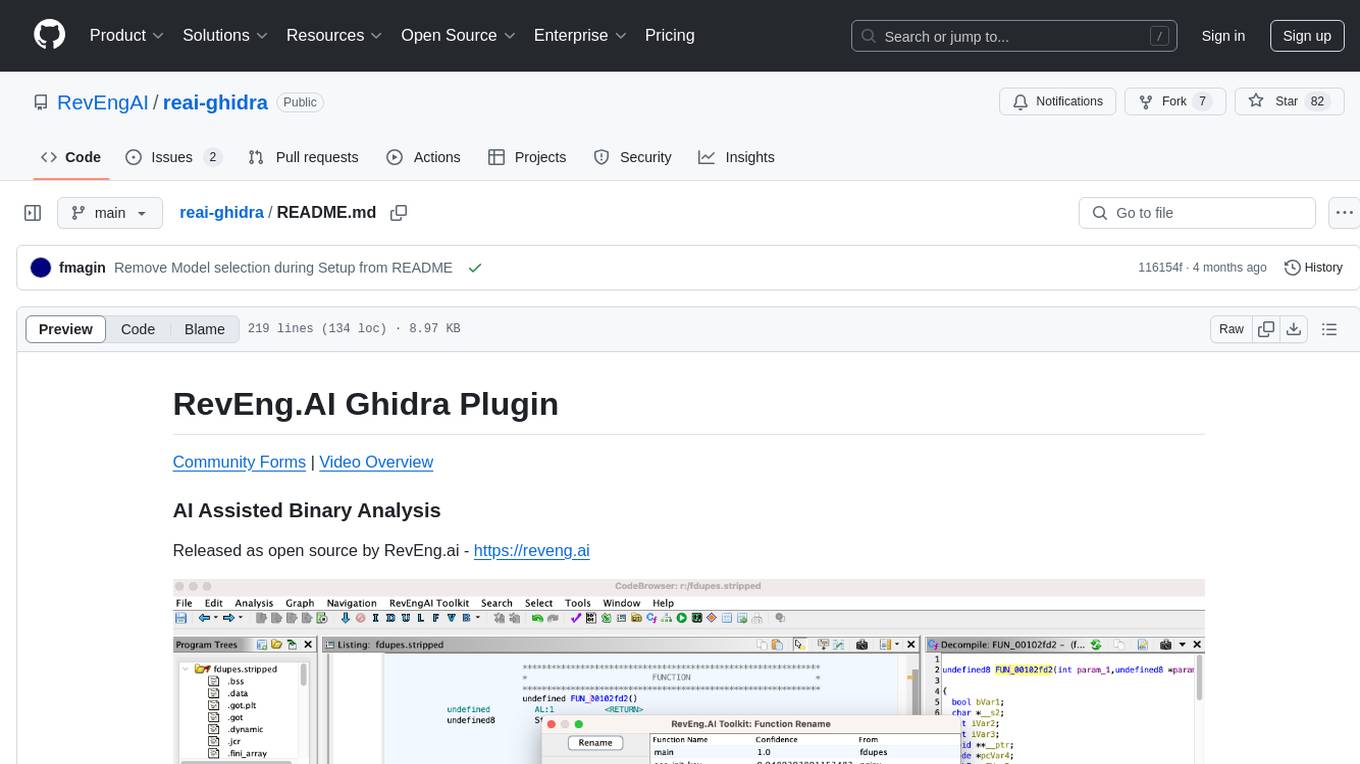
reai-ghidra
The RevEng.AI Ghidra Plugin by RevEng.ai allows users to interact with their API within Ghidra for Binary Code Similarity analysis to aid in Reverse Engineering stripped binaries. Users can upload binaries, rename functions above a confidence threshold, and view similar functions for a selected function.
vulnrepo
VULNRΞPO is a vulnerability report generator and repository tool that prioritizes security by using browser-based encryption and storing data locally. It offers features such as custom templates for pentesters, importing issues from various security scanners, multiple report formats (TXT, HTML, DOCX, PDF), attachment support with checksum verification, changelog tracking, issue export to bugtrackers, AES encryption for report sharing, API integration for backend storage, report template customization, audit tool for research completeness, and local LLM model usage. The tool is designed for efficient vulnerability management and secure report generation.

airgeddon-plugins
airgeddon-plugins is a collection of plugins for the airgeddon tool, designed to enhance its functionality and address specific issues related to wireless network security. These plugins include features such as performing dictionary online attacks on WPA3 networks, allowing all characters on Captive Portal passwords, and fixing compatibility issues with certain Realtek chipsets. The plugins are designed to be deployed within the airgeddon tool directory, providing additional capabilities and options for users.
gitleaks
Gitleaks is a tool for detecting secrets like passwords, API keys, and tokens in git repos, files, and whatever else you wanna throw at it via stdin. It can be installed using Homebrew, Docker, or Go, and is available in binary form for many popular platforms and OS types. Gitleaks can be implemented as a pre-commit hook directly in your repo or as a GitHub action. It offers scanning modes for git repositories, directories, and stdin, and allows creating baselines for ignoring old findings. Gitleaks also provides configuration options for custom secret detection rules and supports features like decoding encoded text and generating reports in various formats.
PrivHunterAI
PrivHunterAI is a tool that detects authorization vulnerabilities using mainstream AI engines such as Kimi, DeepSeek, and GPT through passive proxying. The core detection function relies on open APIs of related AI engines and supports data transmission and interaction over HTTPS protocol. It continuously improves by adding features like scan failure retry mechanism, response Content-Type whitelist, limiting AI request size, URL analysis, frontend result display, additional headers for requests, cost optimization by filtering authorization keywords before calling AI, and terminal output of request package records.
pentagi
PentAGI is an innovative tool for automated security testing that leverages cutting-edge artificial intelligence technologies. It is designed for information security professionals, researchers, and enthusiasts who need a powerful and flexible solution for conducting penetration tests. The tool provides secure and isolated operations in a sandboxed Docker environment, fully autonomous AI-powered agent for penetration testing steps, a suite of 20+ professional security tools, smart memory system for storing research results, web intelligence for gathering information, integration with external search systems, team delegation system, comprehensive monitoring and reporting, modern interface, API integration, persistent storage, scalable architecture, self-hosted solution, flexible authentication, and quick deployment through Docker Compose.

llamator
LLAMATOR is a Red Teaming Python framework designed for testing chatbots and LLM systems. It provides support for custom attacks, a wide range of attack options in English and Russian, custom configuration of chat clients, history tracking of attack requests and responses in Excel and CSV formats, and test report generation in DOCX format. The tool is classified under OWASP as addressing prompt injection, system prompt leakage, and misinformation. It is supported by the AI Security Lab ITMO, Raft Security, and AI Talent Hub, and is licensed under the Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International license.
CyberSentinel-AI
CyberSentinel AI is a powerful automated security monitoring and AI analysis system designed to help security researchers and enthusiasts track the latest security vulnerabilities (CVE) and security-related repositories on GitHub in real-time. It utilizes artificial intelligence technology for in-depth analysis and automatically publishes valuable security intelligence to a blogging platform. The system features multiple data sources monitoring, intelligent AI analysis using OpenAI and Gemini engines, fully automated workflow with 24/7 monitoring, daily briefings, and dynamic blacklists, flexible configuration and management with support for multiple tokens, configurable parameters, and detailed logging, and automatic blog publishing with integrated blogging platform and Markdown reports.
scabench
ScaBench is a comprehensive framework designed for evaluating security analysis tools and AI agents on real-world smart contract vulnerabilities. It provides curated datasets from recent audits and official tooling for consistent evaluation. The tool includes features such as curated datasets from Code4rena, Cantina, and Sherlock audits, a baseline runner for security analysis, a scoring tool for evaluating findings, a report generator for HTML reports with visualizations, and pipeline automation for complete workflow execution. Users can access curated datasets, generate new datasets, download project source code, run security analysis using LLMs, and evaluate tool findings against benchmarks using LLM matching. The tool enforces strict matching policies to ensure accurate evaluation results.
Awesome-AI-Security
Awesome-AI-Security is a curated list of resources for AI security, including tools, research papers, articles, and tutorials. It aims to provide a comprehensive overview of the latest developments in securing AI systems and preventing vulnerabilities. The repository covers topics such as adversarial attacks, privacy protection, model robustness, and secure deployment of AI applications. Whether you are a researcher, developer, or security professional, this collection of resources will help you stay informed and up-to-date in the rapidly evolving field of AI security.
textcoder
Textcoder is a proof-of-concept tool for steganographically encoding secret messages into ordinary text using arithmetic coding based on a statistical model derived from an LLM. It encrypts the secret message to produce a pseudorandom bit stream, which is then decompressed to generate text that appears randomly sampled from the LLM while encoding the secret message in specific token choices.
httpjail
httpjail is a cross-platform tool designed for monitoring and restricting HTTP/HTTPS requests from processes using network isolation and transparent proxy interception. It provides process-level network isolation, HTTP/HTTPS interception with TLS certificate injection, script-based and JavaScript evaluation for custom request logic, request logging, default deny behavior, and zero-configuration setup. The tool operates on Linux and macOS, creating an isolated network environment for target processes and intercepting all HTTP/HTTPS traffic through a transparent proxy enforcing user-defined rules.
binary_ninja_mcp
This repository contains a Binary Ninja plugin, MCP server, and bridge that enables seamless integration of Binary Ninja's capabilities with your favorite LLM client. It provides real-time integration, AI assistance for reverse engineering, multi-binary support, and various MCP tools for tasks like decompiling functions, getting IL code, managing comments, renaming variables, and more.

ramparts
Ramparts is a fast, lightweight security scanner designed for the Model Context Protocol (MCP) ecosystem. It scans MCP servers to identify vulnerabilities and provides security features such as discovering capabilities, multi-transport support, session management, static analysis, cross-origin analysis, LLM-powered analysis, and risk assessment. The tool is suitable for developers, MCP users, and MCP developers to ensure the security of their connections. It can be used for security audits, development testing, CI/CD integration, and compliance with security requirements for AI agent deployments.
pentest-agent
Pentest Agent is a lightweight and versatile tool designed for conducting penetration testing on network systems. It provides a user-friendly interface for scanning, identifying vulnerabilities, and generating detailed reports. The tool is highly customizable, allowing users to define specific targets and parameters for testing. Pentest Agent is suitable for security professionals and ethical hackers looking to assess the security posture of their systems and networks.
nono
nono is a secure, kernel-enforced capability shell for running AI agents and any POSIX style process. It leverages OS security primitives to create an environment where unauthorized operations are structurally impossible. It provides protections against destructive commands and securely stores API keys, tokens, and secrets. The tool is agent-agnostic, works with any AI agent or process, and blocks dangerous commands by default. It follows a capability-based security model with defense-in-depth, ensuring secure execution of commands and protecting sensitive data.
llmxcpg
LLMxCPG is a framework for vulnerability detection using Code Property Graphs (CPG) and Large Language Models (LLM). It involves a two-phase process: Slice Construction where an LLM generates queries for a CPG to extract a code slice, and Vulnerability Detection where another LLM classifies the code slice as vulnerable or safe. The repository includes implementations of baseline models, information on datasets, scripts for running models, prompt templates, query generation examples, and configurations for fine-tuning models.
burp-ai-agent
Burp AI Agent is an extension for Burp Suite that integrates AI into your security workflow. It provides 7 AI backends, 53+ MCP tools, and 62 vulnerability classes. Users can configure privacy modes, perform audit logging, and connect external AI agents via MCP. The tool allows passive and active AI scanners to find vulnerabilities while users focus on manual testing. It requires Burp Suite, Java 21, and at least one AI backend configured.
12 - OpenAI Gpts
CyberSphere Mentor
Friendly Cybersecurity Mentor offering expert advice on the industry and careers.
PentestGPT
A cybersecurity expert aiding in penetration testing. Check repo: https://github.com/GreyDGL/PentestGPT