
aif
None
Stars: 147
Arno's Iptables Firewall (AIF) is a single- & multi-homed firewall script with DSL/ADSL support. It is a free software distributed under the GNU GPL License. The script provides a comprehensive set of configuration files and plugins for setting up and managing firewall rules, including support for NAT, load balancing, and multirouting. It offers detailed instructions for installation and configuration, emphasizing security best practices and caution when modifying settings. The script is designed to protect against hostile attacks by blocking all incoming traffic by default and allowing users to configure specific rules for open ports and network interfaces.
README:
-= Arno's Iptables Firewall(AIF) =-
Single- & multi-homed firewall script with DSL/ADSL support
~ In memory of my dear parents ~
(C) Copyright 2001-2024 by Arno van Amersfoort & Lonnie Abelbeck Web : https://github.com/arno-iptables-firewall/aif Email : a r n o DOT v a n DOT a m e r s f o o r t AT g m a i l DOT c o m (note: you must remove all spaces and substitute the @ and the . at the proper locations!)
This program is free software; you can redistribute it and/or modify it under the terms of the GNU General Public License version 2 as published by the Free Software Foundation.
This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details.
You should have received a copy of the GNU General Public License along with this program; if not, write to the Free Software Foundation, Inc., 59 Temple Place - Suite 330, Boston, MA 02111-1307, USA.
Almost all my work is distributed under the terms of the GNU GPL License, which means it's free (open-source) software. If you like my work or you want me to implement a certain feature, you are encouraged to donate money. You can (preferably) donate directly to me through my bank account (mail me for my IBAN number (International Bank Account Number). My favourite charity organisations are:
- foundations for cancer research (in The Netherlands: "KWF Kanker Bestrijding");
- foundations for brain desease research (in The Netherlands: "De Hersenstichting");
- foundations for the welfare of animals ("IFAW" or in the Netherlands: "De Dierenbescherming")
Note that ALL donations I receive go to one of the above foundations.
I don't provide enduser support by email, I'm simply too busy to help everybody out with every (trivial) issue. Bugs may be reported on Github. Please ask any other questions on Stackexchange/Stackoverflow/Reddit/etc. Also consult the FAQs before reporting a problem/question. Furthermore read the information in the troubleshooting section below!
/bin/arno-iptables-firewall : The actual firewall script, core of Arno's Iptables Firewall(AIF). You should put this file in eg. /usr/local/sbin/ . You should make sure it's executable (use "chmod 700 or chmod +x).
/bin/arno-fwfilter : A pipe filter script to make the firewall-log better readable. It can be used for example in conjuction with a tail to log your firewall to local tty10 (-12). It can be used for both /var/log/messages and /var/log/firewall (or whatever name you configured syslogd), depending on the log-level specified in the configuration file. An example on how to use it can be found in the beginning of the fwfilter script. Any options for fwfilter can be configured within the script itself. You should put this file in eg. /usr/local/bin/.
/etc/arno-iptables-firewall/firewall.conf : The configuration file used for Arno's Iptables Firewall(AIF). Normally you should put it in /etc/arno-iptables-firewall/. Make sure root is owner/group (with "chown 0:0").
/etc/arno-iptables-firewall/plugins/ : Any plugin config files (.conf files) are stored here.
/etc/arno-iptables-firewall/conf.d/ : Put any (override) configuration files in the directory. Any files here with a .conf-extension(!) will be sourced AFTER the main firewall.conf file has been read.
/etc/arno-iptables-firewall/custom-rules : Put any (iptables) custom rules in this file. This file should be put in /etc/arno-iptables-firewall/ . Make sure root is owner/group (with "chown 0:0").
/lib/systemd/system/arno-iptables-firewall.service : The systemd service file. Depending on your system it should be put in either /usr/lib/systemd/system, /lib/systemd/system or /etc/systemd/system
/etc/init.d/arno-iptables-firewall : The init.d script (for older systems still using init.d). On some (older) distributions you may need to put it in /etc/rc.d/ (instead of /etc/init.d). You should make sure it's executable (use "chmod 700 or chmod +x). Inside this script you can also enable VERBOSE(=1) logging for eg. debugging purposes.
/share/arno-iptables-firewall/environment : This is the environment-file required by the firewall and plugins. It contains several global functions. It should normally be put in /usr/local/share/.
/share/arno-iptables-firewall/plugins/ : Put any plugin binaries (.plugin files) for my firewall in this directory. It should normally be put in /usr/local/share/.
/share/man/man8/arno-iptables-firewall.8 : A man page for the arno-iptables-firewall script.
/share/man/man1/arno-fwfilter.1 : A man page for the arno-fwfilter script.
/CHANGELOG : The version changelog of my firewall.
/README : "This" file.
/configure.sh : Script to setup a basic configuration.
/install.sh : Install script to deploy my firewall on your system.
/uninstall.sh : Uninstall script to remove my firewall from your system.
/contrib/ : Directory contains any misc. (user contributed) files (scripts etc.) It also contains examples on how to modify your syslogger to log your firewall stuff into a separate file.
-
If possible try to start the firewall before you enable your (ADSL) internet connection. For an ppp-interface that doesn't exist yet you can use the wildcard device called "ppp+" (but you can only use ppp+ if there aren't any other ppp interfaces!).
-
Don't change any (security) settings ('EXPERT SETTINGS') if you don't really understand what they mean. Changing them anyway could have a big impact on the security of your machine.
-
I get a lot of emails from people complaining that their webserver etc. stopped working after installing my firewall. This is the CORRECT behaviour for a firewall: BLOCKING ALL incoming traffic by default! Configure your eg. OPEN_TCP accordingly!
-
For IPv4 addresses you can use IP ranges in all variables by specifying it as eg. "192.168.1.10-50" (which would make the range start with 192.168.1.10 and end at 192.168.1.50). Note that this only works for Class-C(/24) ranges, so specifying eg. 192.168.1.1-192.168.2.1 does NOT work!
-
My firewall has mixed IPv4/IPv6 support. You can switch from IPv4-only to IPv4/IPv6 support by simply setting "IPV6_SUPPORT=1" in the config file.
-
You can use the $ANYPORT and $ANYHOST macros to specify "ALL ports" or "ALL hosts" in the configuration variables/rules.
-
The configuration variables use several "special" (seperator) characters: ' ' (space): Used to seperate rules (eg. 'rule1 rule2') ',' : Used for lists of ports, hosts or protocols (eg. '21,22,23') '
' : Used for host-port seperation (eg. '192.168.1.122') '>' : Used for source-to-target seperation (eg. '192.168.1.1>10.0.0.3') '#' : Used for external interface(-IP) restrictions (eg. 'eth0>rule') Also see 5)You may want to have a look at the configuration file in /etc/arno-iptables-firewall/ for additional information (and examples)
-
For configuration-variables/rules which are related to the external (internet) interface one can restrict the interface(s) for which it is applied to by adding either "{interface1,interface2,...}#" or "{interface_ip1,interface_ip2}#" at the beginning of the rule. The latter is especially handy for aliased interfaces. Example 1: OPEN_TCP="eth0#22", would only open TCP port 22 (SSH) for interface eth0 Example 2: OPEN_TCP="1.2.3.4#22", would only open TCP port 22 (SSH) for interface which has the IP 1.2.3.4
This feature can also be used to enable NAT port forwarding for certain (external) interfaces. Examples: Example 1: NAT_FORWARD_TCP="eth0#0/0
22>{internal_host}" means: - Forwards TCP port 22; - Forward is available for the whole world (0/0); - Forward is applied to eth0 only; - {internal_host} is the host the port should be forwarded to. Example 2: NAT_FORWARD_TCP="1.2.3.4#0/080>{internal_host}" means: - Forwards TCP port 80; - Forward is available for the whole world (0/0); - Forward is applied to the (external) (aliased) interface with IP 1.2.3.4; - {internal_host} is the host the port should be forwarded to. -
Port ranges should be written as port_start:port_end, eg. "137:139" would select ports 137,138 and 139.
If you want to have it running ASAP or are a novice user, than this is the part that's important. Remember that my firewall has a lot of other useful features which will NOT be used in this way. On the other hand, various security features are enabled by default to protect you from hostile attacks.
-
First we've to check whether your Linux setup is OK in order to make the script work correctly: - It needs iptables and iproute(2) to be installed (probably come as packages with your distro). - It requires a POSIX compliant /bin/sh (should live on any UNIX system by default) - My scripts need the following binaries (in your path): iptables (obviously), ip (from the iproute package), sysctl, modprobe, logger, uname, date, awk, tr, grep, sed, cut, head, tail, wc, which, & cat. - If you plan to use DNS resolving (eg. for certain plugins) then the binary 'dig' (from the dnsutils package) or as a fall-back 'nslookup' should also be available.
-
Now we need to determine whether you have a single- or dual-homed machine. Single means you ONLY have one network-interface, which is the one connected to the outside "evil" world (internet). Dual-homed also have a local subnet connected to an additional network interface.
-
Run the install script and follow the instructions: ./install.sh
a) Configure your external network interfaces, EXT_IF. In case of a dual(multi)-homed it's the interface which is connected to the internet, in case of a LAN it's the one connected to your network. When you have an (dynamically) IP assigned to you (by your ISP) via DHCP, you should set "EXT_IF_DHCP_IP=1" else leave it off (0, default). If you have multiple (non-aliased) external interfaces, you should ALL specify them here (space separated). Note that for aliased interfaces you should only specify the "parent"-interface in EXT_IF. So if you have eth0, eth0:1 and eth0:2, you should make EXT_IF="eth0" (only).
b) When your public IP is assigned to you by your ISP (through DHCP) then you should enable support for an DHCP external assigned IP.
c) Now we configure what ports should be open for the outside world. If you eg. are running an HTTP-server(port 80), an SSH-server(port 22), and/or an FTP-server (port 21) which should be accessible from the internet you should configure the OPEN_TCP / OPEN_UDP variables like this: OPEN_TCP="21 22 80" OPEN_UDP=""
d) For dual-homed machines you should also configure INT_IF, the interface used for the local network and you should set your local subnet range in "INTERNAL_NET=". If you want your internal network to be able to access the internet (aka. internet-sharing), you should also enable NAT (masquerading) by setting "NAT=1"). For single-homed machines (part of a LAN), you shouldn't touch INT_IF (leave it disabled) and just stick to using EXT_IF.
-
Now your firewall is ready but I'd suggest to review this additional info:
a) In case you use an (A)DSL modem (which works with a PPtP connection to your machine) you should enable the dsl-ppp-modem plugin (You can verify this with 'ifconfig', if a ppp device with your public IP exists you need this).
We must enable/configure the dsl-ppp-modem plugin via /etc/arno-iptables-firewall/dsl-ppp-modem.conf by setting ENABLED=1. Now we must configure the network interface(ethX) to which your modem is physically connected (=MODEM_IF, which is commented(#) out by default), and this is NOT ppp+, ppp0 etc.! Here are some examples on how to do it for some providers (it's assumed that the modem is connected to eth0):
PPPoE connection with a static public IP (eg. MxStream in the Netherlands) (setup with the ADSL4Linux package from http://www.adsl4linux.nl):
- MODEM_IF="eth0"
- MODEM_IF_IP="10.0.0.150"
- MODEM_IP="10.0.0.138" # Make sure this IP corresponds to the one used by your modem!
T-DSL (Germany) with a dynamic public IP:
- MODEM_IF="eth0"
- MODEM_IF_IP="192.168.99.1"
- MODEM_IP=""
PPPoA connection with a dynamic public IP:
- MODEM_IF="eth0"
- MODEM_IF_IP="" # This MUST be unset("") (default)
- MODEM_IP="10.0.0.138" # Make sure this IP corresponds to the one used by your modem!
NOTE 1: For extra security you can set the IP of your modem (MODEM_IP), but it's not neccessary (anymore). If you don't know its IP or believe it doesn't have an IP, you can leave MODEM_IP="". The same applies for the IP of the modem network interface (MODEM_IF_IP).
NOTE 2: If both your modem AND your network interface don't have an IP you probably don't have to configure your modem settings (at all).
NOTE 3: In case of a PPPoA (PPP-over-ATM) you MUST leave MODEM_IF_IP empty(="")!
NOTE 4: Don't forget to set EXT_IF_DHCP_IP=1 in firewall.conf too, in case your ISP uses DHCP.
b) In case your on a corporate network which uses public IPs I'd suggest to add your local subnet (range) to "FULL_ACCESS_HOSTS".
c) Some people mentioned that protocols like IRC or some (older) FTP/POP3/SMTP servers don't work (properly) if port 113(Identd) is filtered (firewalled). I really hate the fact that these type of protocols still depend on the "not-so-secure" IDENT-protocol. But if you really need it, you can do 2 things to make them work properly:
- If you don't want to run an IDENT-daemon, simply add port 113 to the REJECT_TCP-variable (Recommended).
- Or if you really want to run an IDENT-daemon, you should add port 113 to the OPEN_TCP-variable. (Not recommended)
-
You're now ready to start the firewall by issueing: "/etc/init.d/arno-iptables-firewall start" Everything should be working OK now, if it doesn't, carefully review all steps and your configuration. For troubleshouting you can first consult the FAQs on my webpage.
NOTE 1: Make sure that when you use NAT, you should properly configure the client's "default gateway" and the (public) DNS server(s) it should use! Note that you don't have to setup any proxy settings in eg. your client's browser.
NOTE 2: Additional (more advanced) options are (also) explained in the configuration-file comments and in the QA's on my webpage (eg. IPSec VPN support).
- Check your settings (.conf) at least 10 times. It's quite common for a
human being to make mistakes.
TIPS / Common errors:
- Make sure that EXT_IF, MODEM_IF and/or INT_IF are not the same. If they are, YOU made a mistake, as they can never EVER be the same!
- Another error I once saw was someone that used something like "127.0.0.0/24" for his local subnet. "127.0.0.0" is the address of the local loopback and therefor should never ever appear in the configuration file!
- Obtain the latest version of your (distribution) kernel & iptables.
- Make sure your (self-built) kernel supports all required options.
- Carefully inspect the output generated when issueing "arno-iptables-firewall start"
- Read the README file at least 3 times
- Download the latest (beta) version of my script and check whether this fixes your problem.
- Read the README file one more time and review your .conf-file also one more time, just in case ;-)
- Do NOT send enduser requests to my personal email address, instead post
your question/problem on the firewall mailing list. Provide us with:
- your (firewall) *.conf files
- the screen output of "/usr/local/sbin/arno-iptables-firewall start" (or whatever it is located)
- the output of 'ifconfig'
- (firewall) logs
- the version of my script you're using (or date if you use the development script)
- detailed explanation of your setup
- and anything else that might help Remember that people that don't obey these rules, get a low, very low priority, or won't get any reaction at all!
As of version 1.8.7-RC2 my firewall also supports plugins -> little scripts that implement specific functionality.
- Plugin config files can be found in /etc/arno-iptables-firewall/plugins/
- All plugins have an option called "ENABLED" (in their config file) which is set to 0 by default, meaning it is disabled. So if you actually want to use a plugin, you have to make ENABLED=1
- Plugins can have their own additional set of configuration variables, don't forget to set/review those too.
Everyone is invited to write their own plugins to implement other things, and to submit to us.
-
When you write your own plugins, make sure you know what you're doing. You can severely compromise security or break things with buggy plugins.
-
Submit plugins to me, if you think they can be of use to others, but note that I always reserve the right to decline the plugin (because it was eg. poorly written). Submitted plugins must be (at least) compatible with the GPLv2 license.
-
The plugin should have/use these variables:
- PLUGIN_NAME (Plugin name/description)
- PLUGIN_VERSION (Plugin version)
- PLUGIN_CONF_FILE (Location of the plugin config file)
Furthermore it should honour the ENABLED variable from the config-file to enable/disable the plugin.
Use one of my plugins as a template(skeleton) for writing your own plugins (I recommend to have a look at the "SSH Brute-Force protection"-plugin), in this way it's easier to understand it for me and for others.
-
Plugins should have a separate config file (.conf) with all user variables(settings). It should at least contain the "ENABLED="-variable to enable/disable the plugin.
-
Plugins should also have a separate file with their CHANGELOG (.changelog)
-
Plugins should be preferably POSIX shell compatible (eg. work with "Dash")
-
Plugins can use all variables/functions/chains from the main-script and main configuration file. Plugin specific configuration variables should be put inside the plugin's configuration file (.conf).
-
Make sure that when you create new iptables-chains, they don't conflict with the main script or other plugins. The same goes for the iptables MARK-module, make sure that you use an unique MARK-number that doesn't conflict with other plugins.
-
Plugins should in principle always cleanup up their own chains (and possibly other stuff) they created at start when stopping.
-
A list of available chains created by AIF's main script can be found below. Note that I strongly recommend NOT to directly use any builtin iptables chains like INPUT/OUTPUT/FORWARD/PREROUTING/POSTROUTING. Only do this when it's absolutely necessary!
BASE_INPUT_CHAIN - Base input chain. For internal use by AIF only! BASE_OUTPUT_CHAIN - Base output chain. For internal use by AIF only! BASE_FORWARD_CHAIN - Base forward chain. For internal use by AIF only! INPUT_CHAIN - AIF's main INPUT chain. Use this if you want to insert rules in the INPUT chain OUTPUT_CHAIN - AIF's main OUTPUT chain. Use this if you want to insert rules in the OUTPUT chain FORWARD_CHAIN - AIF's main FORWARD chain. Use this if you want to insert rules in the FORWARD chain EXT_INPUT_CHAIN - External-net INPUT chain EXT_OUTPUT_CHAIN - External-net OUTPUT chain EXT_BROADCAST_CHAIN - External-net chain for broadcast traffic EXT_MULTICAST_CHAIN - External-net chain for multicast traffic EXT_FORWARD_IN_CHAIN - External-net FORWARD chain for INcoming traffic EXT_FORWARD_OUT_CHAIN - External-net FORWARD chain for OUTgoing traffic EXT_ICMP_FLOOD_CHAIN - External-net chain where ICMP packets go which are considered a "flood" DMZ_FORWARD_IN_CHAIN - DMZ FORWARD chain for INcoming traffic DMZ_FORWARD_OUT_CHAIN - DMZ FORWARD chain for OUTgoing traffic DMZ_INET_FORWARD_CHAIN - DMZ to internet/external-net forward chain DMZ_INPUT_CHAIN - DMZ INPUT chain DMZ_LAN_FORWARD_CHAIN - DMZ to LAN/internal-net forward chain DMZ_OUTPUT_CHAIN - DMZ output chain INET_DMZ_FORWARD_CHAIN - External-net(internet) to DMZ forward chain HOST_BLOCK_SRC - Chain containing the list of inbound blocked hosts HOST_BLOCK_DST - Chain containing the list of outbound blocked hosts HOST_BLOCK_SRC_DROP - Chain where packets from dropped inbound blocked hosts go HOST_BLOCK_DST_DROP - Chain where packets from dropped outbound blocked hosts go INT_INPUT_CHAIN - Internal-net INPUT chain INT_OUTPUT_CHAIN - Internal-net OUTPUT chain LAN_LAN_FORWARD_CHAIN - LAN to LAN (Inter-LAN) forward chain (AIF private use only) LAN_INET_FORWARD_CHAIN - LAN to internet (external net) forward chain POST_INPUT_CHAIN - This chain is always processed last(post) in the INPUT chain POST_OUTPUT_CHAIN - This chain is always processed last(post) in the OUTPUT chain POST_FORWARD_CHAIN - This chain is always processed last(post in the FORWARD chain POST_INPUT_DROP_CHAIN - Packets dropped at the end of the INPUT chain end up in this chain (Used for eg. IDS) RESERVED_NET_CHK - This chain holds the list of reserved nets to check against SPOOF_CHK - This chain contains rules for spoof checking VALID_CHK - This chain contains rules for checking whether a packet is valid NAT_POSTROUTING_CHAIN - NAT (-t nat) POSTROUTING chain NAT_PREROUTING_CHAIN - NAT (-t nat) PREROUTING chain POST_NAT_POSTROUTING_CHAIN - This chain is always processed last(post) in the NAT (-t nat) POSTROUTING chain POST_NAT_PREROUTING_CHAIN - This chain is always processed last(post) in the NAT (-t nat) PREROUTING chain
My firewall also supports multirouting (loadbalancing), optionally in conjunction with NAT. Although this works with both conventional masquerading and SNAT, it's strongly recommended to use SNAT. This is because the latter is known to have a much lower chance of causing problems. Also note that I haven't found a way (yet) to make this work with dynamic external(internet) IP's, meaning you need static IP's from your ISP.
First of all, if you want to use multirouting, make sure that your (vanilla)-kernel has the following network features enabled (eg. when building from source):
- CONFIG_IP_ADVANCED_ROUTER=y
- CONFIG_IP_MULTIPLE_TABLES=y
- CONFIG_IP_ROUTE_MULTIPATH=y
Second, you should configure/enable the multiroute-plugin. And last but not least, you should setup the firewall: adding (all) the used external interfaces to EXT_IF. And when SNAT is used, add the corresponding external IPs to NAT_STATIC_IP. That's it!
NOTE: Redundant connections are (currently) not supported! This is limitation of the (current) Linux kernel (not of my firewall).
For the firewall to work properly you need the following options enabled (as modules or compiled in your kernel):
- "Loadable module support" - "Enable loadable module support" (If you want to build iptables as modules) - "Automatic kernel module loading" (Strongly recommended if you build iptables as modules) (Only available in newer 2.6 kernels)
- "Networking", "Networking Support", "Networking Options" : - "Packet socket" (If you want to use dhcp client and/or server) - "TCP/IP networking" - "IP: Multicasting" - "IP: advanced router" - "IP: policy routing" (If you want to use load balancing, eg. multiroute masquerading) - "IP: equal cost multipath" (If you want to use load balancing, eg. multiroute masquerading) - "IP: TCP syncookie support" - ("Network packet filtering") - "Core Netfilter Configuration" (For kernel =>2.6.16) - "Netfilter Xtables support (Required for ip_tables)" - "MARK" target support (Only required for special purposes like eg. traffic shaping & kernel 2.6 VPN support) - "conntrack" connection tracking match support - "limit" match support - "mac" address match support (If you want to use MAC filtering) - "state" match support - "tcpmss" match support (If you want to use tcpmss clamping) - "IP: Netfilter Configuration": - "Connection tracking" - "Connection tracking flow accounting" (If you want to do accounting on your network traffic. (kernel 2.6 only) - "FTP protocol support" - "IP tables support" (NOTE: The order of sub-options can differ between kernel versions): - "Multiple port match support" - "TOS match support" (If you want to use TOS mangling) - "recent match support" (required for IDS & SSH brute-force protection) - "TTL match support" (If you want to use TTL manipulation) - "limit match support" (kernel <2.6.16) - "MAC address match support" (If you want to use MAC filtering) (kernel <2.6.16) - "Multiple port match support" (kernel <2.6.16) - "tcpmss match support" (If you use tcpmss clamping) (kernel <2.6.16) - "Connection state match support" (Kernel <2.6.16) - "Packet filtering" (kernel <2.6.16) - "REJECT target support" - "LOG target support" - "TCPMSS target support (If you want to use tcpmss-clamping) - "Full NAT" (If you use NAT/masquerading aka internet-sharing or transparent proxies) - "MASQUERADE target" (If you want to use masquerading) - "REDIRECT target support" (If you want to use port- forwarding, -redirection or transparent proxies) - "Packet mangling" - "TOS target support" (If you want to use TOS mangling) - "MARK target support" (Only required for special purposes like eg. traffic shaping & kernel 2.6 VPN support) (kernel <2.6.16) - "TTL target support" (if you want to use TTL manipulation
Some kernel versions, or series of versions, may have unique issues, below are topics related to the scope of this firewall script.
-
Starting with kernel version 2.6.27, CONFIG_NF_CT_ACCT is deprecated, the result when the "nf_conntrack" module is loaded and the kernel has CONFIG_NF_CT_ACCT=y set, the following message is displayed:
"CONFIG_NF_CT_ACCT is deprecated and will be removed soon. Please use nf_conntrack.acct=1 kernel paramater, acct=1 nf_conntrack module option or sysctl net.netfilter.nf_conntrack_acct=1 to enable it."
The message is harmless, and can be safely ignored. The main script also sets net.netfilter.nf_conntrack_acct=1 in the case CONFIG_NF_CT_ACCT is not set.
Though, if you find this message annoying, it can be silenced via "make menuconfig":
-- Core Netfilter Configuration --Netfilter connection tracking support [ ] Connection tracking flow accounting
if "Connection tracking flow accounting" can't be disabled, then disabling
< > "connbytes" per-connection counter match support
may be required because of dependencies. The resulting configuration settings are:
CONFIG_NF_CONNTRACK=m
CONFIG_NF_CT_ACCT was scheduled to be removed in 2.6.29, but has not yet been removed, as of writing.
For Tasks:
Click tags to check more tools for each tasksFor Jobs:
Alternative AI tools for aif
Similar Open Source Tools

aif
Arno's Iptables Firewall (AIF) is a single- & multi-homed firewall script with DSL/ADSL support. It is a free software distributed under the GNU GPL License. The script provides a comprehensive set of configuration files and plugins for setting up and managing firewall rules, including support for NAT, load balancing, and multirouting. It offers detailed instructions for installation and configuration, emphasizing security best practices and caution when modifying settings. The script is designed to protect against hostile attacks by blocking all incoming traffic by default and allowing users to configure specific rules for open ports and network interfaces.
SwarmUI
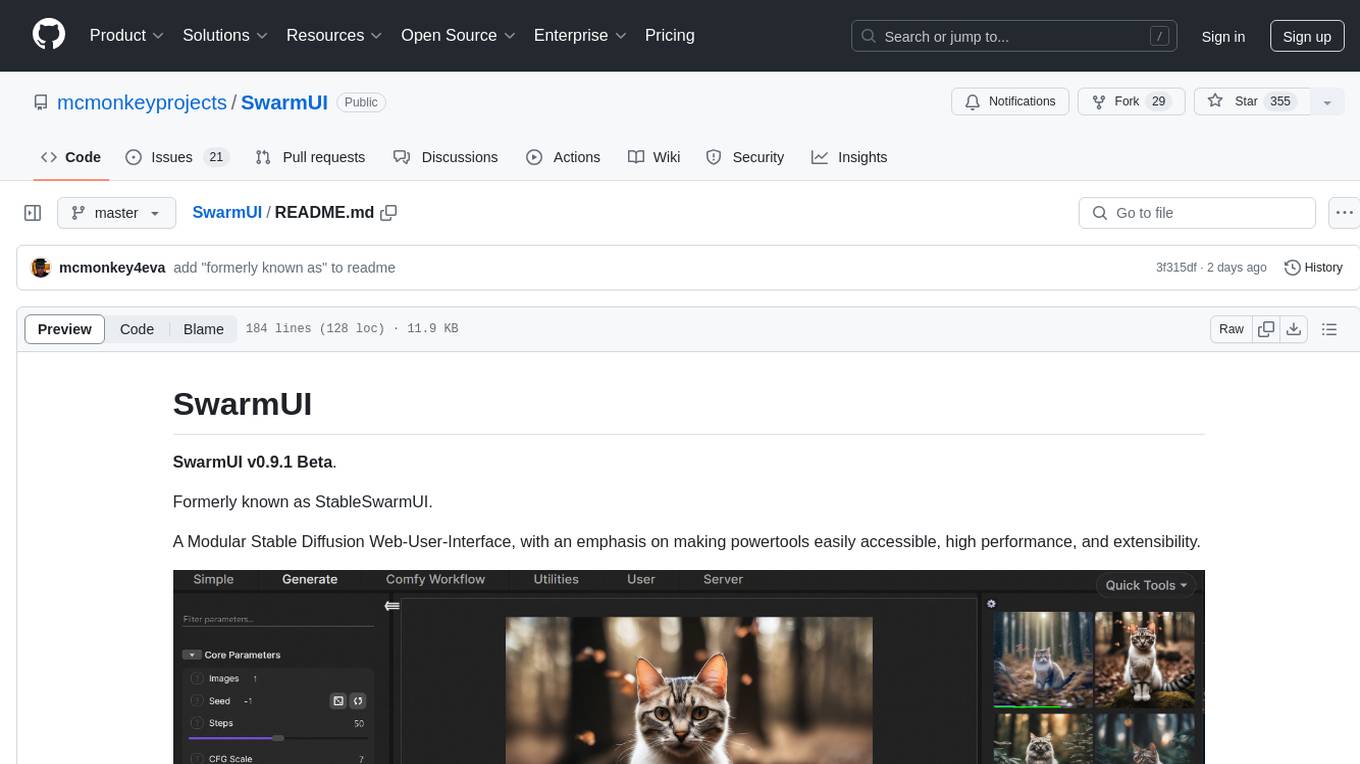
SwarmUI is a modular stable diffusion web-user-interface designed to make powertools easily accessible, high performance, and extensible. It is in Beta status, offering a primary Generate tab for beginners and a Comfy Workflow tab for advanced users. The tool aims to become a full-featured one-stop-shop for all things Stable Diffusion, with plans for better mobile browser support, detailed 'Current Model' display, dynamic tab shifting, LLM-assisted prompting, and convenient direct distribution as an Electron app.
superflows
Superflows is an open-source alternative to OpenAI's Assistant API. It allows developers to easily add an AI assistant to their software products, enabling users to ask questions in natural language and receive answers or have tasks completed by making API calls. Superflows can analyze data, create plots, answer questions based on static knowledge, and even write code. It features a developer dashboard for configuration and testing, stateful streaming API, UI components, and support for multiple LLMs. Superflows can be set up in the cloud or self-hosted, and it provides comprehensive documentation and support.
ray-llm
RayLLM (formerly known as Aviary) is an LLM serving solution that makes it easy to deploy and manage a variety of open source LLMs, built on Ray Serve. It provides an extensive suite of pre-configured open source LLMs, with defaults that work out of the box. RayLLM supports Transformer models hosted on Hugging Face Hub or present on local disk. It simplifies the deployment of multiple LLMs, the addition of new LLMs, and offers unique autoscaling support, including scale-to-zero. RayLLM fully supports multi-GPU & multi-node model deployments and offers high performance features like continuous batching, quantization and streaming. It provides a REST API that is similar to OpenAI's to make it easy to migrate and cross test them. RayLLM supports multiple LLM backends out of the box, including vLLM and TensorRT-LLM.
blurt
Blurt is a Gnome shell extension that enables accurate speech-to-text input in Linux. It is based on the command line utility NoteWhispers and supports Gnome shell version 48. Users can transcribe speech using a local whisper.cpp installation or a whisper.cpp server. The extension allows for easy setup, start/stop of speech-to-text input with key bindings or icon click, and provides visual indicators during operation. It offers convenience by enabling speech input into any window that allows text input, with the transcribed text sent to the clipboard for easy pasting.
AIOC
AIOC is an All-in-one-Cable for Ham Radio enthusiasts, providing a cheap and hackable digital mode USB interface with features like sound-card, virtual tty, and CM108 compatible HID endpoint. It supports various software and tested radios for functions like programming, APRS, and Dual-PTT HTs. Users can fabricate and assemble the AIOC using specific instructions, and program it using STM32CubeIDE. The tool can be used for tasks like programming radios, asserting PTT, and accessing audio data channels. Future work includes configurable AIOC settings, virtual-PTT, and virtual-COS features.

airbyte_serverless
AirbyteServerless is a lightweight tool designed to simplify the management of Airbyte connectors. It offers a serverless mode for running connectors, allowing users to easily move data from any source to their data warehouse. Unlike the full Airbyte-Open-Source-Platform, AirbyteServerless focuses solely on the Extract-Load process without a UI, database, or transform layer. It provides a CLI tool, 'abs', for managing connectors, creating connections, running jobs, selecting specific data streams, handling secrets securely, and scheduling remote runs. The tool is scalable, allowing independent deployment of multiple connectors. It aims to streamline the connector management process and provide a more agile alternative to the comprehensive Airbyte platform.
jaison-core
J.A.I.son is a Python project designed for generating responses using various components and applications. It requires specific plugins like STT, T2T, TTSG, and TTSC to function properly. Users can customize responses, voice, and configurations. The project provides a Discord bot, Twitch events and chat integration, and VTube Studio Animation Hotkeyer. It also offers features for managing conversation history, training AI models, and monitoring conversations.
lingo
Lingo is a lightweight ML model proxy that runs on Kubernetes, allowing you to run text-completion and embedding servers without changing OpenAI client code. It supports serving OSS LLMs, is compatible with OpenAI API, plug-and-play with messaging systems, scales from zero based on load, and has zero dependencies. Namespaced with no cluster privileges needed.
claude.vim
Claude.vim is a Vim plugin that integrates Claude, an AI pair programmer, into your Vim workflow. It allows you to chat with Claude about what to build or how to debug problems, and Claude offers opinions, proposes modifications, or even writes code. The plugin provides a chat/instruction-centric interface optimized for human collaboration, with killer features like access to chat history and vimdiff interface. It can refactor code, modify or extend selected pieces of code, execute complex tasks by reading documentation, cloning git repositories, and more. Note that it is early alpha software and expected to rapidly evolve.
civitai
Civitai is a platform where people can share their stable diffusion models (textual inversions, hypernetworks, aesthetic gradients, VAEs, and any other crazy stuff people do to customize their AI generations), collaborate with others to improve them, and learn from each other's work. The platform allows users to create an account, upload their models, and browse models that have been shared by others. Users can also leave comments and feedback on each other's models to facilitate collaboration and knowledge sharing.

brokk
Brokk is a code assistant designed to understand code semantically, allowing LLMs to work effectively on large codebases. It offers features like agentic search, summarizing related classes, parsing stack traces, adding source for usages, and autonomously fixing errors. Users can interact with Brokk through different panels and commands, enabling them to manipulate context, ask questions, search codebase, run shell commands, and more. Brokk helps with tasks like debugging regressions, exploring codebase, AI-powered refactoring, and working with dependencies. It is particularly useful for making complex, multi-file edits with o1pro.
AIS-catcher-for-Android
AIS-catcher for Android is a multi-platform AIS receiver app that transforms your Android device into a dual channel AIS receiver. It directly accesses a Software Defined Radio USB device to pick up AIS signals from nearby vessels, visualizing them on a built-in map or sending messages via UDP to plotting apps. The app requires a RTL-SDR dongle or an AirSpy device, a simple antenna, an Android device with USB connector, and an OTG cable. It is designed for research and educational purposes under the GPL license, with no warranty. Users are responsible for prudent use and compliance with local regulations. The app is not intended for navigation or safety purposes.
CyberScraper-2077
CyberScraper 2077 is an advanced web scraping tool powered by AI, designed to extract data from websites with precision and style. It offers a user-friendly interface, supports multiple data export formats, operates in stealth mode to avoid detection, and promises lightning-fast scraping. The tool respects ethical scraping practices, including robots.txt and site policies. With upcoming features like proxy support and page navigation, CyberScraper 2077 is a futuristic solution for data extraction in the digital realm.

Sentient
Sentient is a personal, private, and interactive AI companion developed by Existence. The project aims to build a completely private AI companion that is deeply personalized and context-aware of the user. It utilizes automation and privacy to create a true companion for humans. The tool is designed to remember information about the user and use it to respond to queries and perform various actions. Sentient features a local and private environment, MBTI personality test, integrations with LinkedIn, Reddit, and more, self-managed graph memory, web search capabilities, multi-chat functionality, and auto-updates for the app. The project is built using technologies like ElectronJS, Next.js, TailwindCSS, FastAPI, Neo4j, and various APIs.
bia-bob
BIA `bob` is a Jupyter-based assistant for interacting with data using large language models to generate Python code. It can utilize OpenAI's chatGPT, Google's Gemini, Helmholtz' blablador, and Ollama. Users need respective accounts to access these services. Bob can assist in code generation, bug fixing, code documentation, GPU-acceleration, and offers a no-code custom Jupyter Kernel. It provides example notebooks for various tasks like bio-image analysis, model selection, and bug fixing. Installation is recommended via conda/mamba environment. Custom endpoints like blablador and ollama can be used. Google Cloud AI API integration is also supported. The tool is extensible for Python libraries to enhance Bob's functionality.
For similar tasks

aif
Arno's Iptables Firewall (AIF) is a single- & multi-homed firewall script with DSL/ADSL support. It is a free software distributed under the GNU GPL License. The script provides a comprehensive set of configuration files and plugins for setting up and managing firewall rules, including support for NAT, load balancing, and multirouting. It offers detailed instructions for installation and configuration, emphasizing security best practices and caution when modifying settings. The script is designed to protect against hostile attacks by blocking all incoming traffic by default and allowing users to configure specific rules for open ports and network interfaces.
For similar jobs

last_layer
last_layer is a security library designed to protect LLM applications from prompt injection attacks, jailbreaks, and exploits. It acts as a robust filtering layer to scrutinize prompts before they are processed by LLMs, ensuring that only safe and appropriate content is allowed through. The tool offers ultra-fast scanning with low latency, privacy-focused operation without tracking or network calls, compatibility with serverless platforms, advanced threat detection mechanisms, and regular updates to adapt to evolving security challenges. It significantly reduces the risk of prompt-based attacks and exploits but cannot guarantee complete protection against all possible threats.

aircrack-ng
Aircrack-ng is a comprehensive suite of tools designed to evaluate the security of WiFi networks. It covers various aspects of WiFi security, including monitoring, attacking (replay attacks, deauthentication, fake access points), testing WiFi cards and driver capabilities, and cracking WEP and WPA PSK. The tools are command line-based, allowing for extensive scripting and have been utilized by many GUIs. Aircrack-ng primarily works on Linux but also supports Windows, macOS, FreeBSD, OpenBSD, NetBSD, Solaris, and eComStation 2.

reverse-engineering-assistant
ReVA (Reverse Engineering Assistant) is a project aimed at building a disassembler agnostic AI assistant for reverse engineering tasks. It utilizes a tool-driven approach, providing small tools to the user to empower them in completing complex tasks. The assistant is designed to accept various inputs, guide the user in correcting mistakes, and provide additional context to encourage exploration. Users can ask questions, perform tasks like decompilation, class diagram generation, variable renaming, and more. ReVA supports different language models for online and local inference, with easy configuration options. The workflow involves opening the RE tool and program, then starting a chat session to interact with the assistant. Installation includes setting up the Python component, running the chat tool, and configuring the Ghidra extension for seamless integration. ReVA aims to enhance the reverse engineering process by breaking down actions into small parts, including the user's thoughts in the output, and providing support for monitoring and adjusting prompts.

AutoAudit
AutoAudit is an open-source large language model specifically designed for the field of network security. It aims to provide powerful natural language processing capabilities for security auditing and network defense, including analyzing malicious code, detecting network attacks, and predicting security vulnerabilities. By coupling AutoAudit with ClamAV, a security scanning platform has been created for practical security audit applications. The tool is intended to assist security professionals with accurate and fast analysis and predictions to combat evolving network threats.

aif
Arno's Iptables Firewall (AIF) is a single- & multi-homed firewall script with DSL/ADSL support. It is a free software distributed under the GNU GPL License. The script provides a comprehensive set of configuration files and plugins for setting up and managing firewall rules, including support for NAT, load balancing, and multirouting. It offers detailed instructions for installation and configuration, emphasizing security best practices and caution when modifying settings. The script is designed to protect against hostile attacks by blocking all incoming traffic by default and allowing users to configure specific rules for open ports and network interfaces.

watchtower
AIShield Watchtower is a tool designed to fortify the security of AI/ML models and Jupyter notebooks by automating model and notebook discoveries, conducting vulnerability scans, and categorizing risks into 'low,' 'medium,' 'high,' and 'critical' levels. It supports scanning of public GitHub repositories, Hugging Face repositories, AWS S3 buckets, and local systems. The tool generates comprehensive reports, offers a user-friendly interface, and aligns with industry standards like OWASP, MITRE, and CWE. It aims to address the security blind spots surrounding Jupyter notebooks and AI models, providing organizations with a tailored approach to enhancing their security efforts.

Academic_LLM_Sec_Papers
Academic_LLM_Sec_Papers is a curated collection of academic papers related to LLM Security Application. The repository includes papers sorted by conference name and published year, covering topics such as large language models for blockchain security, software engineering, machine learning, and more. Developers and researchers are welcome to contribute additional published papers to the list. The repository also provides information on listed conferences and journals related to security, networking, software engineering, and cryptography. The papers cover a wide range of topics including privacy risks, ethical concerns, vulnerabilities, threat modeling, code analysis, fuzzing, and more.
DeGPT
DeGPT is a tool designed to optimize decompiler output using Large Language Models (LLM). It requires manual installation of specific packages and setting up API key for OpenAI. The tool provides functionality to perform optimization on decompiler output by running specific scripts.