Best AI tools for< Network Security Analyst >
Infographic
20 - AI tool Sites
Cyguru
Cyguru is an all-in-one cloud-based AI Security Operation Center (SOC) that offers a comprehensive range of features for a robust and secure digital landscape. Its Security Operation Center is the cornerstone of its service domain, providing AI-Powered Attack Detection, Continuous Monitoring for Vulnerabilities and Misconfigurations, Compliance Assurance, SecPedia: Your Cybersecurity Knowledge Hub, and Advanced ML & AI Detection. Cyguru's AI-Powered Analyst promptly alerts users to any suspicious behavior or activity that demands attention, ensuring timely delivery of notifications. The platform is accessible to everyone, with up to three free servers and subsequent pricing that is more than 85% below the industry average.
Flexxon
Flexxon is a leading industrial SSD & NAND manufacturer dedicated to ensuring data security and reliability. They offer a wide range of industrial-grade SSD and NAND products, including USB flash memory devices, memory cards, PATA SSD, SATA SSD, eMMC storage solutions, and PCIe NVMe SSD. Their flagship product is the Flexxon CyberSecure SSD, which is the world's first AI-powered cybersecurity solution providing real-time data protection at the storage level. Flexxon values product longevity, quality, and reliability, offering customizable memory solutions and strong technical support to their customers worldwide.
chckr.io
The website chckr.io is experiencing a privacy error due to an expired security certificate. Users are warned that their connection may not be private, potentially exposing sensitive information to attackers. The site provides information about the security warning, certificate details, and suggestions to improve web security. It aims to enhance user awareness and security practices on the web.
AirMDR
AirMDR is an AI-powered Managed Detection and Response (MDR) application that revolutionizes cybersecurity by leveraging artificial intelligence to automate routine tasks, enhance alert triage, investigation, and response processes. The application offers faster, higher-quality, and more affordable cybersecurity solutions, supervised by human experts. AirMDR aims to deliver unprecedented speed, superior quality, and cost-effective outcomes to cater to the unique demands of security operations centers.
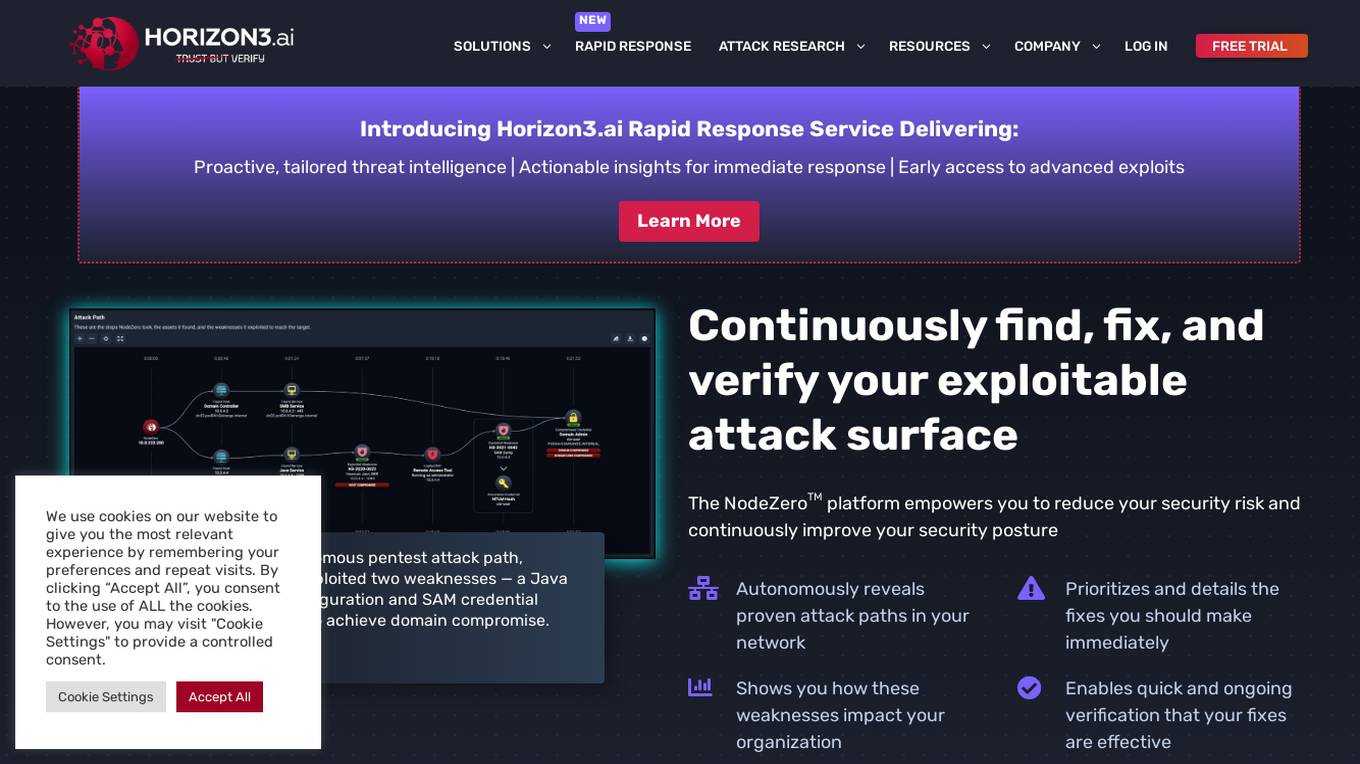
NodeZero™ Platform
Horizon3.ai Solutions offers the NodeZero™ Platform, an AI-powered autonomous penetration testing tool designed to enhance cybersecurity measures. The platform combines expert human analysis by Offensive Security Certified Professionals with automated testing capabilities to streamline compliance processes and proactively identify vulnerabilities. NodeZero empowers organizations to continuously assess their security posture, prioritize fixes, and verify the effectiveness of remediation efforts. With features like internal and external pentesting, rapid response capabilities, AD password audits, phishing impact testing, and attack research, NodeZero is a comprehensive solution for large organizations, ITOps, SecOps, security teams, pentesters, and MSSPs. The platform provides real-time reporting, integrates with existing security tools, reduces operational costs, and helps organizations make data-driven security decisions.
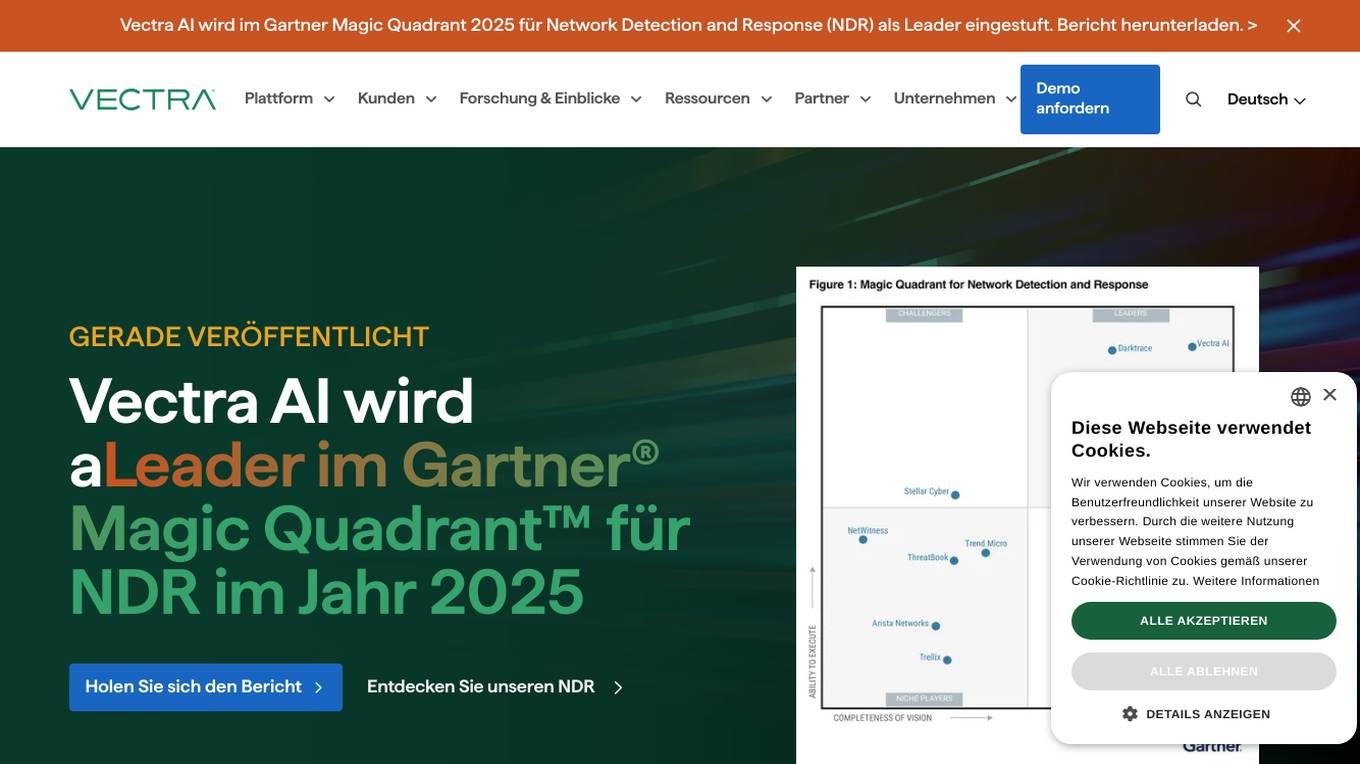
Vectra AI
Vectra AI is a leading cybersecurity AI application that stops attacks that others cannot. It is recognized in the Gartner Magic Quadrant 2025 for Network Detection and Response (NDR) as a leader. Vectra AI's platform protects modern networks from advanced threats by providing real-time attack signal intelligence and AI-driven detections. It equips security analysts with the information needed to quickly stop attacks across various security application scenarios. The application covers a wide range of security areas such as SOC modernization, SIEM optimization, IDS replacement, EDR extension, cloud resilience, and more.
Hive Defender
Hive Defender is an advanced, machine-learning-powered DNS security service that offers comprehensive protection against a vast array of cyber threats including but not limited to cryptojacking, malware, DNS poisoning, phishing, typosquatting, ransomware, zero-day threats, and DNS tunneling. Hive Defender transcends traditional cybersecurity boundaries, offering multi-dimensional protection that monitors both your browser traffic and the entirety of your machine’s network activity.
ForbiddenGuard
The website is currently displaying a '403 Forbidden' error, which indicates that the server is refusing to respond to the request. This error message is typically shown when the server understands the request made by the client but refuses to fulfill it. The 'openresty' mentioned in the text is likely the web server software being used. It is important to troubleshoot and resolve the 403 Forbidden error to regain access to the desired content on the website.

403 Forbidden
The website is currently displaying a '403 Forbidden' error message, indicating that access to the page is restricted. This error typically occurs when the server understands the request made by the client, but refuses to fulfill it. The '403 Forbidden' message may be due to insufficient permissions, IP blocking, or other security measures. Users encountering this error are advised to contact the website administrator for assistance.

403 Forbidden Error Handler
The website encountered a 403 Forbidden error, indicating that the user does not have permission to access the resource. This error is commonly encountered when trying to access a webpage or resource without the necessary authorization. The ErrorDocument was unable to handle the request, resulting in the Forbidden error message.
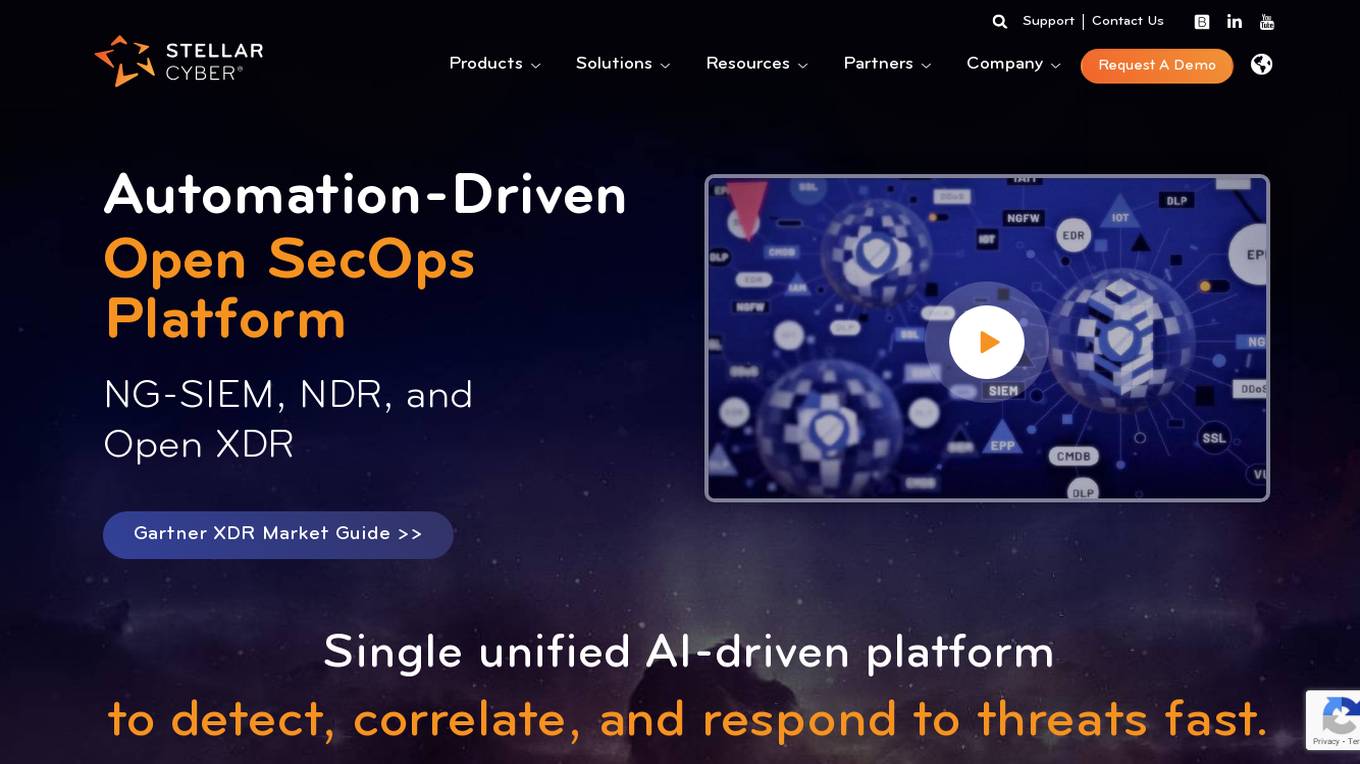
Stellar Cyber
Stellar Cyber is an AI-driven unified security operations platform powered by Open XDR. It offers a single platform with NG-SIEM, NDR, and Open XDR, providing security capabilities to take control of security operations. The platform helps organizations detect, correlate, and respond to threats fast using AI technology. Stellar Cyber is designed to protect the entire attack surface, improve security operations performance, and reduce costs while simplifying security operations.
Security Certificate Advisor
The website provides information about a privacy error related to a security certificate expiration for the IP address 147.139.135.71. It warns users about potential data theft and advises on correcting system clock settings. The site also mentions Certificate Transparency and offers options to enhance web security.

TeddyAI Web Security Checker
The website teddyai.oiedu.co.uk appears to be experiencing a privacy error, indicating that the connection is not private. The error message warns that attackers might be attempting to steal sensitive information such as passwords, messages, or credit card details. The security certificate for the website is from cpcalendars.bigcityrealty.net, suggesting a potential misconfiguration or a security threat. Users are advised to proceed with caution due to the security risks associated with the site.
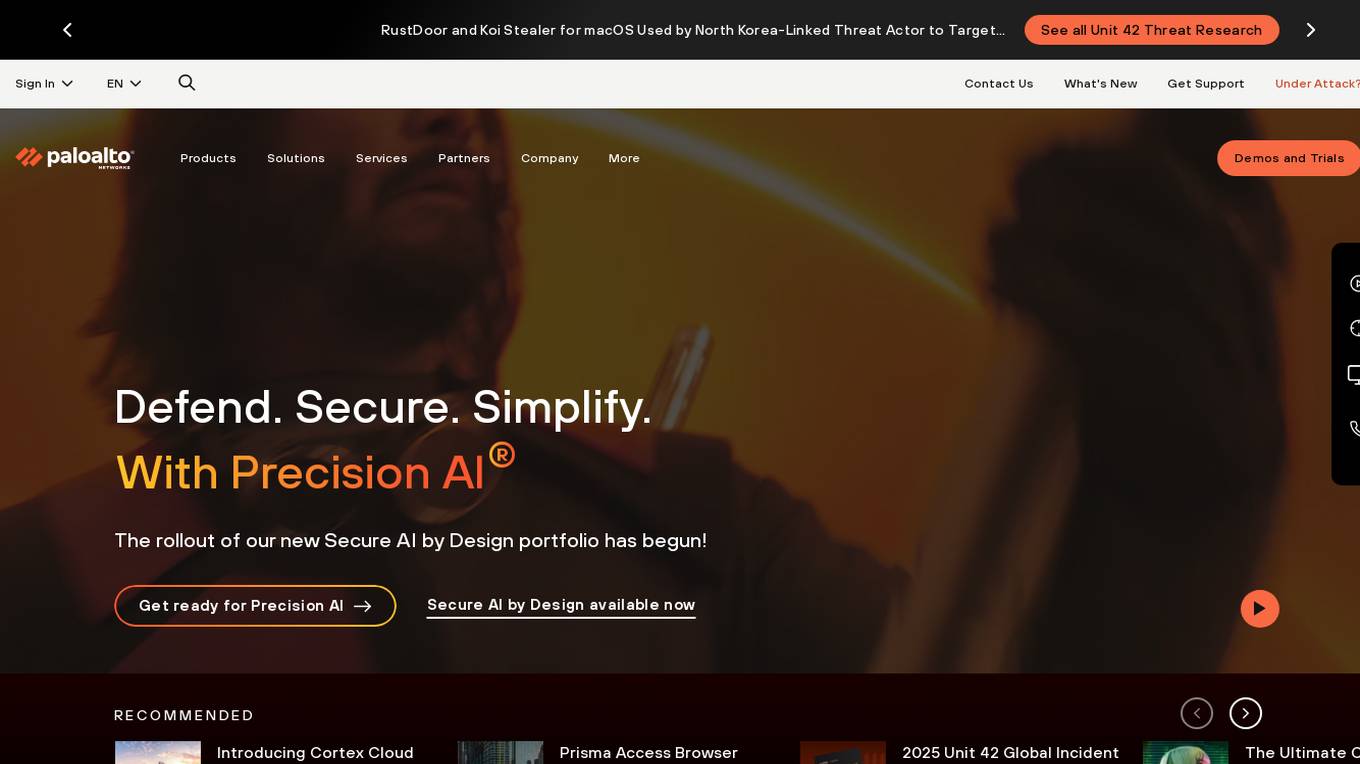
Palo Alto Networks
Palo Alto Networks is a cybersecurity company offering advanced security solutions powered by Precision AI to protect modern enterprises from cyber threats. The company provides network security, cloud security, and AI-driven security operations to defend against AI-generated threats in real time. Palo Alto Networks aims to simplify security and achieve better security outcomes through platformization, intelligence-driven expertise, and proactive monitoring of sophisticated threats.
klu.ai
klu.ai is an AI-powered platform that focuses on security verification for online connections. It ensures a safe browsing experience by reviewing and enhancing the security measures of the user's connection. The platform utilizes advanced algorithms to detect and prevent potential threats, providing users with a secure environment for their online activities.
zoo.replicate.dev
The website zoo.replicate.dev is a platform that focuses on security and privacy. It provides encryption to protect user information and alerts users about potential security risks such as invalid certificates. The site aims to enhance web security by preventing unauthorized access and attacks. Users are informed about network errors and advised to enable enhanced protection for a secure browsing experience.
Netify
Netify provides network intelligence and visibility. Its solution stack starts with a Deep Packet Inspection (DPI) engine that passively collects data on the local network. This lightweight engine identifies applications, protocols, hostnames, encryption ciphers, and other network attributes. The software can be integrated into network devices for traffic identification, firewalling, QoS, and cybersecurity. Netify's Informatics engine collects data from local DPI engines and uses the power of a public or private cloud to transform it into network intelligence. From device identification to cybersecurity risk detection, Informatics provides a way to take a proactive approach to manage network threats, bottlenecks, and usage. Lastly, Netify's Data Feeds provide data to help vendors understand how applications behave on the Internet.

AitoCards
The website aitocards.com seems to be facing a privacy error related to its SSL certificate. The error message indicates that the connection is not private and warns about potential attackers trying to steal sensitive information such as passwords, messages, or credit card details. The certificate in question is issued by cloudflare-dns.com, and the warning suggests that the site's security certificate is invalid. Users are advised to proceed to the site at their own risk, as it may be unsafe due to a potential misconfiguration or interception by an attacker.
GetLuminal
GetLuminal.com is a website that provides information about a security certificate error related to the website itself. The site warns users about potential privacy risks and advises on actions to take when encountering such errors. It offers insights into security certificate expiration, potential threats from attackers, and guidance on system clock settings. Users can learn about security measures, certificate transparency, and how to enhance web security.

chat.baseflow.io
The website chat.baseflow.io is experiencing a privacy error, indicating that the connection is not secure. Users are warned that attackers might be trying to steal sensitive information such as passwords, messages, or credit cards. The error message suggests that the security certificate for the website is not trusted by the user's computer's operating system, potentially due to misconfiguration or a security breach. The site advises users to proceed with caution and offers options to enhance security.
7 - Open Source Tools

aircrack-ng
Aircrack-ng is a comprehensive suite of tools designed to evaluate the security of WiFi networks. It covers various aspects of WiFi security, including monitoring, attacking (replay attacks, deauthentication, fake access points), testing WiFi cards and driver capabilities, and cracking WEP and WPA PSK. The tools are command line-based, allowing for extensive scripting and have been utilized by many GUIs. Aircrack-ng primarily works on Linux but also supports Windows, macOS, FreeBSD, OpenBSD, NetBSD, Solaris, and eComStation 2.
airgeddon
Airgeddon is a versatile bash script designed for Linux systems to conduct wireless network audits. It provides a comprehensive set of features and tools for auditing and securing wireless networks. The script is user-friendly and offers functionalities such as scanning, capturing handshakes, deauth attacks, and more. Airgeddon is regularly updated and supported, making it a valuable tool for both security professionals and enthusiasts.

airgorah
Airgorah is a WiFi security auditing software written in Rust that utilizes the aircrack-ng tools suite. It allows users to capture WiFi traffic, discover connected clients, perform deauthentication attacks, capture handshakes, and crack access point passwords. The software is designed for testing and discovering flaws in networks owned by the user, and requires root privileges to run on Linux systems with a wireless network card supporting monitor mode and packet injection. Airgorah is not responsible for any illegal activities conducted with the software.
aif
Arno's Iptables Firewall (AIF) is a single- & multi-homed firewall script with DSL/ADSL support. It is a free software distributed under the GNU GPL License. The script provides a comprehensive set of configuration files and plugins for setting up and managing firewall rules, including support for NAT, load balancing, and multirouting. It offers detailed instructions for installation and configuration, emphasizing security best practices and caution when modifying settings. The script is designed to protect against hostile attacks by blocking all incoming traffic by default and allowing users to configure specific rules for open ports and network interfaces.
pwnagotchi
Pwnagotchi is an AI tool leveraging bettercap to learn from WiFi environments and maximize crackable WPA key material. It uses LSTM with MLP feature extractor for A2C agent, learning over epochs to improve performance in various WiFi environments. Units can cooperate using a custom parasite protocol. Visit https://www.pwnagotchi.ai for documentation and community links.

air-script
Air Script is a versatile tool designed for Wi-Fi penetration testing, offering automated and user-friendly features to streamline the hacking process. It allows users to easily capture handshakes from nearby networks, automate attacks, and even send email notifications upon completion. The tool is ideal for individuals looking to efficiently pwn Wi-Fi networks without extensive manual input. With additional tools and options available, Air Script caters to a wide range of users, including script kiddies, hackers, pentesters, and security researchers. Whether on the go or using a Raspberry Pi, Air Script provides a convenient solution for network penetration testing and password cracking.

airgeddon-plugins
airgeddon-plugins is a collection of plugins for the airgeddon tool, designed to enhance its functionality and address specific issues related to wireless network security. These plugins include features such as performing dictionary online attacks on WPA3 networks, allowing all characters on Captive Portal passwords, and fixing compatibility issues with certain Realtek chipsets. The plugins are designed to be deployed within the airgeddon tool directory, providing additional capabilities and options for users.
20 - OpenAI Gpts
Network Operations Advisor
Ensures efficient and effective network performance and security.
A Monitoring Expert
Expert in host monitoring setup, providing seamless network monitoring solutions.
Cyber security analyst
Designed to help cybersecurity analysts # ISO # NIST # COBIT # SANS # PCI DSS
ethicallyHackingspace (eHs)® (IoN-A-SCP)™
Interactive on Network (IoN) Automation SCP (IoN-A-SCP)™ AI-copilot (BETA)
Le VPN - Your Secure Internet Proxy
Bypass Internet censorship & improve your security online
Log Analyzer
I'm designed to help You analyze any logs like Linux system logs, Windows logs, any security logs, access logs, error logs, etc. Please do not share information that You would like to keep private. The author does not collect or process any personal data.
BashEmulator GPT
BashEmulator GPT: A Virtualized Bash Environment for Linux Command Line Interaction. It virtualized all network interfaces and local network