
HydraDragonPlatform
Dynamic and static analysis with Real Time Malware/Executable Analysis Platform for Windows, including open-source XDR (2 EDR projects), ClamAV, YARA-X, machine learning AI, behavioral analysis, Unpacker, Deobfuscator, Decompiler, website signatures, Ghidra, Suricata, Sigma, Kernel based protection and much more than you can imagine.
Stars: 146
Hydra Dragon Automatic Malware/Executable Analysis Platform offers dynamic and static analysis for Windows, including open-source XDR projects, ClamAV, YARA-X, machine learning AI, behavioral analysis, Unpacker, Deobfuscator, Decompiler, website signatures, Ghidra, Suricata, Sigma, Kernel based protection, and more. It is a Unified Executable Analysis & Detection Framework.
README:
- Dynamic and static analysis with Real Time Malware/Executable Analysis Platform for Windows, including open-source XDR (2 EDR projects), ClamAV, YARA-X, machine learning AI, behavioral analysis, Unpacker, Deobfuscator, Decompiler, website signatures, Ghidra, Suricata, Sigma, Kernel based protection and much more than you can imagine.
- HydraDragonPlatform - Unified Executable Analysis & Detection Framework
This project is licensed under the GNU Affero General Public License v3.0 (AGPLv3).
See the LICENSE file for more information.
- This program assumes the PC is in a clean state and is not subject to post-infection.
- This project doesn't replace your daily AV and this project not an AV.
- It's very experimental program and you need to be careful.
- I made very dumb choices in past. It damaged my project but now I improving it.
- We are not going to detect too old samples. See here: https://blog.clamav.net/2025/12/clamav-signature-retirement.html
- You must uninstall it manually; the auto-uninstaller won't work.
- The ClamAV update issue is temporary during setup; you can safely ignore it.
- Disable Secure Boot if the driver installation fails.
- We recommend waiting until the antivirus fully opens, even if some protections are already active.
- You can manually terminate the antivirus, but a virus cannot, because the antivirus driver can detect whether the request comes from a user or not. So don't worry if you managed to close it manually.
- Quarantine folder: C:\ProgramData\HydraDragonAntivirus\Quarantine
- Pe header removed: https://www.virustotal.com/gui/file/9b7e921e971fe7523ba83a4599b4006ad214854eb043372129e4f5a68c5a427f
- Original: https://www.virustotal.com/gui/file/1ef6c1a4dfdc39b63bfe650ca81ab89510de6c0d3d7c608ac5be80033e559326
- So we ignore files looks like junk data (fully unknown)
- What is the difference and why does YARA still flag it as malware? Because your YARA rule doesn't check for unknown file types and I only removed the pe header and went to detections 0. So this god mode rule will save this antivirus right now!
- Malware Database: Download Link
- Benign Database: Download Link (outdated now I have 204k samples also I have javascript samples)
- Note: The collection only contains PE files smaller than 10MB. Due to my USB stick being broken and no longer recoverable, approximately 6,000 benign samples were lost forever. Some of these samples were even not available on VirusTotal.
- Password: infected
- Install malicious (datamaliciousorder) and benign (data2) database, then install requirements.txt from train.py and just run train.py with the same folder as datamaliciousorder and data2.
- Then delete results.pkl and rename ml_definitions.pkl to results.pkl to consolidate the pickled data.
- This very complex task. I need create wiki for that. Please contact me.
- I now using 11.4.3: https://ghidra-sre.org/
- Setup file on release HydraDragonAntivirus.exe
- Ghidra: %ProgramFiles%\aHydraDragonAntivirus\hydradragon\ghidra
- Ghidra Run: %ProgramFiles%\aHydraDragonAntivirus\hydradragon\ghidra\ghidraRun.bat
- Ghidra scripts: %ProgramFiles%\aHydraDragonAntivirus\hydradragon\scripts
- https://github.com/Yamato-Security/hayabusa/releases/tag/v3.7.0 (hayabusa-3.7.0-win-x64.zip)
- Any logs will be removed when you restart the programme. So be careful!
- You have to restart the program after the analysis.
- Please don't share your IP in the logs.
- Make sure that the ClamAV database is installed without problems.
- We strongly recommend that you take a snapshot and then go back when you have finished your work.
- Make your username hydradragonav (for example and for avoid anti analysis).
- The installer also includes daily.cvd, main.cvd, bytecode.cvd due to download issues with the ClamAV database.
- Here is the server link: https://discord.gg/Rdyw59xqMC
- Create too many files to detect ransomware.
Note 1:.
- Allow Java on the Windows firewall, as it'll decompile the PE file.
Note 2:
- If you find an issue, please create an issue. Antivirus software might be triggered by website signatures because they are not obfuscated, so exclude the
%ProgramFiles%\aHydraDragonAntivirus\hydradragonfolder. Due to risks please only use in a VM.
Note 3:
-
https://github.com/GDATAAdvancedAnalytics/de4dotEx/releases/tag/3.2.4
-
https://www.rathlev-home.de/index-e.html?tools/prog-e.html#unpack
-
https://github.com/glmcdona/Process-Dump/releases/tag/v2.1.1
-
https://github.com/HydraDragonAntivirus/HydraDragonPythonReverser
-
I used these projects to decompile (with a current custom database of Detect-It-Easy).
-
I used these projects for AI.
-
I used these projects for EDR (Notice newest forks added to main repo instead of other repo).
-
I used this project for MBR Protection.
-
I used these projects to protect the antivirus.
-
I used these projects to optimize the antivirus.
Note 4:.
- You will need an internet connection to install. It's not an offline installer.
Note 5:
- Don't forget to do a clean up, as it takes up too much space while processing files against ransomware, etc.
- You need too much storage because it logs everything.
Note 6:
- I have collected every malicious IP, domain from the Internet. So there must be big false positives, but I handle them.
Note 7:
- Inno Setup version 6.6.1
Tip 1:
- Don't use suspicious VM names on your machine. (John Doe, etc.)
Tip 2:
- Use VSCode, VSCodium, or another editor to see live changes to .log files.
Tip 3:
- Close the Windows Firewall on the VM to avoid any firewall blocking. We are testing this program not Windows Firewall.
Does this collect data?
- No. We can allow GridinSoft and many other companies to collect data. Unlike other companies, they freely allow the use of their cloud, but I'm not allowing that.
How do I use it?
- Just run the shortcut from the desktop, then run advanced dynamic and static analysis on a file.
How good is it?
- It's very good at every type of analysis and it balances everything with allowing you configure more aggressive or less aggressive.
Why does my antivirus detect this as malware?
- It's a false positive. It's contains the website, HIPS signatures without obfuscation. It's a fully open source executable analysis product.
Why is it 2GB+?
- Because of website signatures, Ghidra, ClamAV and Java Development Kit. Website signatures are not very effective but they can detect old and new viruses. I can remove them if you want. Ghidra is for decompiling but takes too much space. Java Development Kit is for Ghidra. That's 1GB+ Note that it's a completely local (except update database) and professional open source antivirus.
Why does the antivirus.exe application take too long to run?
- Sometimes you may have to wait 5+ minutes (or less) the first time you run the programme as a lot of things load.
Which Windows versions are supported?
- Windows 10 no longer offically supported. Switch to Windows 11 25H2.
What are the minimum RAM and disk space requirements?
- A minimum of 8 GB of RAM is required: 3 GB is used by ClamAV, and the remaining 5 GB is used by other engines.
Any sponsors or supporters?
- Yes, there are supporters for this project. Xcitium (Comodo) has expressed interest in supporting this project by providing malware samples, and Cisco Talos ClamAV community projects. But it's still a one man project.
Are you using leaked YARA rules?
- No we don't but if you have proof please create issue we can remove it.
Why don't you use NictaSoft, GridinSoft and Bitdefender cloud?
- It could significantly boost my antivirus. However, there are some problems. These services are not open source unless you pay. We're not only focused on detection, but also committed to maintaining open-source principles.
Other related things?
- I used yarGen to create machinelearning.yar.
How many repositories did you look at for this project?
- For YARA and website signatures, I looked at many projects-possibly more than 1,000.
Why doesn't the program open?
- Your installation might be broken. You can check the logs to determine the issue, because if the connection was lost during installation, it can affect the installation significantly. Try reinstalling to fix the problem.
- All credits goes to Emirhan Uçan (yes it's one man project)
- Thanks to Hacı Murad for collecting and compiling some machine learning signatures.
This document describes all the output directories used by the executalbe analysis tool for various extraction, decompilation, and unpacking operations.
This document describes the output directories used by the HydraDragon analysis tool and what each directory contains. Keep this README next to the analysis output so analysts can quickly find decompiled/ extracted artifacts.
- Each extractor/decompiler writes into a dedicated directory under the analysis root.
- Tools create numbered subfolders (
1/,2/, ...) to avoid overwrites when the same packer/result is processed multiple times. - Filenames and subfolders are preserved where possible to make tracing back to the original artifact easier.
- Directories are created automatically by the extraction/decompilation modules.
-
Packer/Obfuscator extraction:
hydra_dragon_dumper_extracted/,upx_extracted/,themida_unpacked/,vmprotect_unpacked/,debloat/ -
.NET analysis:
dotnet/,obfuscar/,de4dot_extracted/,net_reactor_extracted/,un_confuser_ex_extracted/ -
Android/APK:
jadx_decompiled/,androguard/ -
Python:
pyinstaller_extracted/,pyarmor8_and_9_extracted/,pyarmor7_extracted/,nuitka/,nuitka_extracted/,nuitka_source_code/,cx_freeze_extracted/,pylingual_extracted/,python_deobfuscated/,python_deobfuscated_marshal_pyc/,pycdas_extracted/,python_source_code/ -
JavaScript / Node / Electron:
webcrack_javascript_deobfuscated/,asar/,npm_pkg_extracted/,decompiled_jsc/ -
Java:
jar_extracted/,FernFlower_decompiled/ -
Installer / archive:
inno_setup_unpacked/,advanced_installer_extracted/,installshield_extracted/,zip_extracted/,seven_zip_extracted/,tar_extracted/,general_extracted_with_7z/,pe_extracted/ -
Script decompilers:
autohotkey_decompiled/,autoit_extracted/ -
Go / Ungarbler outputs:
ungarbler/,ungarbler_string/ -
Misc / analysis artifacts:
decompiled/,ole2/,memory/,resource_extractor/,html_extracted/
(Each line shows directory name and the purpose of files found there.)
-
hydra_dragon_dumper_extracted/— Hydra Dragon Dumper (Mega Dumper Fork) output extracted. -
enigma1_extracted/— Enigma Virtual Box extracted files. -
decompiled/— General decompiled files from miscellaneous tools. -
upx_extracted/— UPX (Ultimate Packer for eXecutables) extracted files. -
webcrack_javascript_deobfuscated/— JavaScript files deobfuscated with webcrack. -
inno_setup_unpacked/— Inno Setup unpacked installer files. -
autohotkey_decompiled/— AutoHotkey script decompiled outputs. -
themida_unpacked/— Themida unpacked outputs. -
nuitka/— Nuitka onefile extracted directory. -
ole2/— OLE2 extracted resources and compound file structures. -
dotnet/— .NET decompiled sources. -
jadx_decompiled/— APK decompiled with JADX (Java sources). -
androguard/— APK decompiled output from androguard (smali/java). -
asar/— ASAR (Electron) archive extracted contents. -
npm_pkg_extracted/— NPM package extraction (JavaScript bundles). -
decompiled_jsc/— V8 / JSC bytecode objects and decompiled artifacts. -
obfuscar/— .NET assemblies obfuscated with Obfuscar. -
de4dot_extracted/— .NET files deobfuscated using de4dot. -
net_reactor_extracted/— .NET Reactor Slayer outputs. -
un_confuser_ex_extracted/— UnConfuserEx deobfuscation outputs. -
pyinstaller_extracted/— PyInstaller onefile extraction results. -
pyarmor8_and_9_extracted/— PyArmor 8/9 unpacked outputs. -
pyarmor7_extracted/— PyArmor 7-specific unpacking outputs. -
cx_freeze_extracted/— cx_Freezelibrary.zipcontents extracted. -
pe_extracted/— PE file internals and extracted sections/resources. -
zip_extracted/— ZIP archive contents. -
seven_zip_extracted/— 7-Zip archive contents. -
general_extracted_with_7z/— General extraction area for 7-Zip operations. -
nuitka_extracted/— Nuitka binary outputs and support files. -
advanced_installer_extracted/— Advanced Installer extraction outputs. -
tar_extracted/— TAR archive contents. -
memory/— Dynamic analysis memory dump files (.dmp / raw memory dumps). -
resource_extractor/— RCData and embedded resources extracted by resource extractor. -
ungarbler/— Deobfuscated Go (garble) binaries and output. -
ungarbler_string/— Deobfuscated strings from Go Garble outputs. -
debloat/— Debloated files directory (trimmed installers/binaries). -
jar_extracted/— Extracted contents of JAR files. -
FernFlower_decompiled/— JARs decompiled with FernFlower. -
pylingual_extracted/— pylingual-reversed Python sources (.pyc -> .py). -
vmprotect_unpacked/— VMProtect unpacked directories. -
python_deobfuscated/— Deobfuscated Python sources. -
python_deobfuscated_marshal_pyc/— Deobfuscated .pyc from marshal blobs. -
pycdas_extracted/— pycdas / Decompyle++ extracted Python sources. ( 21-Oct-2025) -
python_source_code/— Extracted and organized Python project sources. -
nuitka_source_code/— Nuitka reversed-engineered source tree. -
html_extracted/— HTML and web page resources captured during analysis. -
installshield_extracted/— InstallShield unpack outputs. -
autoit_extracted/— AutoIt script extraction results.
- Inspect each extraction directory after the run to locate configuration blobs, embedded resources, strings, and suspicious binaries.
- If you need to regenerate extracted outputs, run the relevant extractor again; numbered subfolders prevent accidental overwrites.
- If a directory is empty, check the corresponding extraction log for errors. Tools may fail silently if binaries are corrupted.
- If references look malformed (e.g.
Unknown.0,Unknown), run the providedreference_fix_and_rebuild.pyto normalize and rebuild references. - If the loader is slow, enable shard caching or batch queries (see loader docs) rather than re-loading every shard for each lookup.
For changes to this README or to add new extractor directories, update this file and check it into your repo so everyone can see the mapping.
For Tasks:
Click tags to check more tools for each tasksFor Jobs:
Alternative AI tools for HydraDragonPlatform
Similar Open Source Tools

HydraDragonPlatform
Hydra Dragon Automatic Malware/Executable Analysis Platform offers dynamic and static analysis for Windows, including open-source XDR projects, ClamAV, YARA-X, machine learning AI, behavioral analysis, Unpacker, Deobfuscator, Decompiler, website signatures, Ghidra, Suricata, Sigma, Kernel based protection, and more. It is a Unified Executable Analysis & Detection Framework.
PentestGPT
PentestGPT is a penetration testing tool empowered by ChatGPT, designed to automate the penetration testing process. It operates interactively to guide penetration testers in overall progress and specific operations. The tool supports solving easy to medium HackTheBox machines and other CTF challenges. Users can use PentestGPT to perform tasks like testing connections, using different reasoning models, discussing with the tool, searching on Google, and generating reports. It also supports local LLMs with custom parsers for advanced users.
testzeus-hercules
Hercules is the world’s first open-source testing agent designed to handle the toughest testing tasks for modern web applications. It turns simple Gherkin steps into fully automated end-to-end tests, making testing simple, reliable, and efficient. Hercules adapts to various platforms like Salesforce and is suitable for CI/CD pipelines. It aims to democratize and disrupt test automation, making top-tier testing accessible to everyone. The tool is transparent, reliable, and community-driven, empowering teams to deliver better software. Hercules offers multiple ways to get started, including using PyPI package, Docker, or building and running from source code. It supports various AI models, provides detailed installation and usage instructions, and integrates with Nuclei for security testing and WCAG for accessibility testing. The tool is production-ready, open core, and open source, with plans for enhanced LLM support, advanced tooling, improved DOM distillation, community contributions, extensive documentation, and a bounty program.
restai
RestAI is an AIaaS (AI as a Service) platform that allows users to create and consume AI agents (projects) using a simple REST API. It supports various types of agents, including RAG (Retrieval-Augmented Generation), RAGSQL (RAG for SQL), inference, vision, and router. RestAI features automatic VRAM management, support for any public LLM supported by LlamaIndex or any local LLM supported by Ollama, a user-friendly API with Swagger documentation, and a frontend for easy access. It also provides evaluation capabilities for RAG agents using deepeval.
horde-worker-reGen
This repository provides the latest implementation for the AI Horde Worker, allowing users to utilize their graphics card(s) to generate, post-process, or analyze images for others. It offers a platform where users can create images and earn 'kudos' in return, granting priority for their own image generations. The repository includes important details for setup, recommendations for system configurations, instructions for installation on Windows and Linux, basic usage guidelines, and information on updating the AI Horde Worker. Users can also run the worker with multiple GPUs and receive notifications for updates through Discord. Additionally, the repository contains models that are licensed under the CreativeML OpenRAIL License.
wcgw
wcgw is a shell and coding agent designed for Claude and Chatgpt. It provides full shell access with no restrictions, desktop control on Claude for screen capture and control, interactive command handling, large file editing, and REPL support. Users can use wcgw to create, execute, and iterate on tasks, such as solving problems with Python, finding code instances, setting up projects, creating web apps, editing large files, and running server commands. Additionally, wcgw supports computer use on Docker containers for desktop control. The tool can be extended with a VS Code extension for pasting context on Claude app and integrates with Chatgpt for custom GPT interactions.
llm-autoeval
LLM AutoEval is a tool that simplifies the process of evaluating Large Language Models (LLMs) using a convenient Colab notebook. It automates the setup and execution of evaluations using RunPod, allowing users to customize evaluation parameters and generate summaries that can be uploaded to GitHub Gist for easy sharing and reference. LLM AutoEval supports various benchmark suites, including Nous, Lighteval, and Open LLM, enabling users to compare their results with existing models and leaderboards.
app-agent
AppAgent is an open-source AI-first platform designed to streamline the app release process, from autonomous keyword research to ASO content generation. It offers features like autonomous keyword research, AI-powered store optimization, store synchronization with App Store Connect, and upcoming keyword tracking with self-healing. The tech stack includes Next.js, TypeScript, Tailwind CSS, Prisma ORM, PostgreSQL, NextAuth.js, PostHog, Resend, Stripe, and Vercel for hosting. Users can clone the repository, set up environment variables, install dependencies, set up the database, and run the development server to start using the tool.
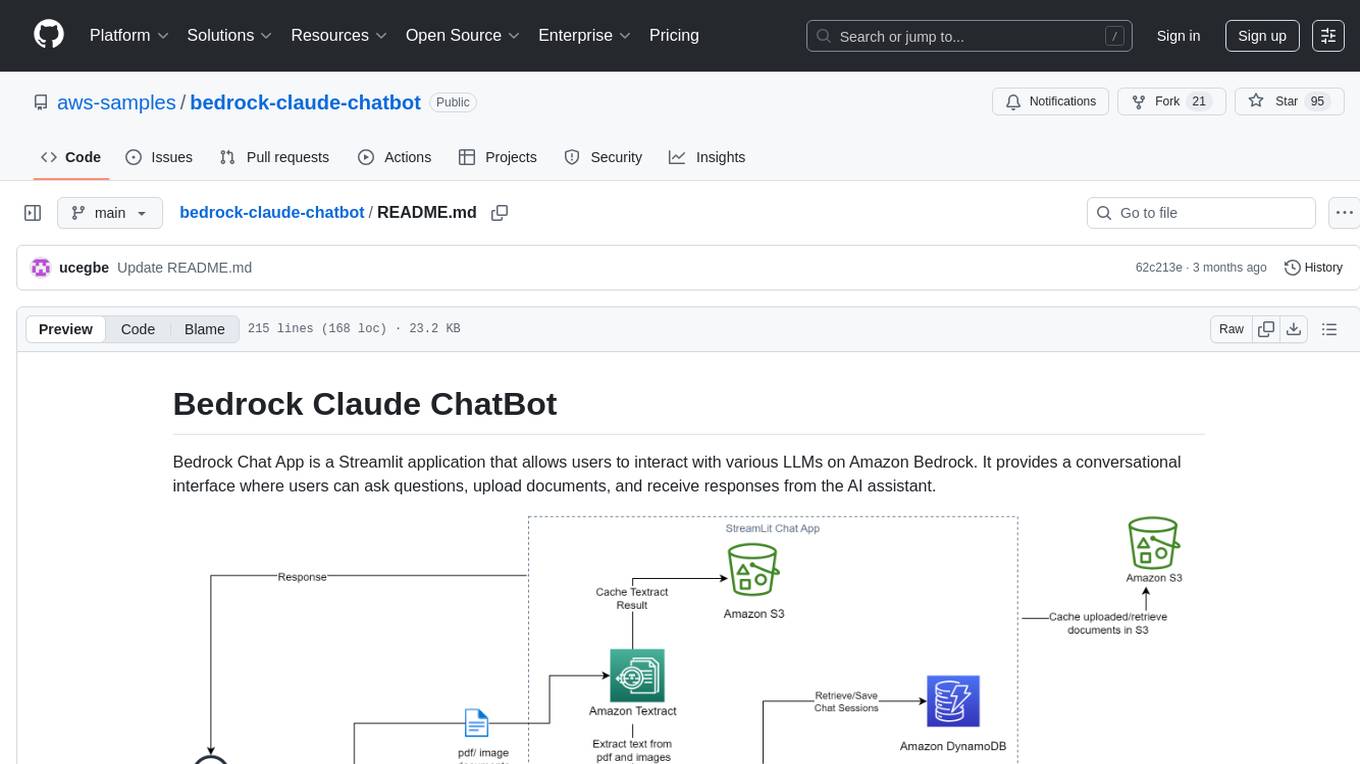
bedrock-claude-chatbot
Bedrock Claude ChatBot is a Streamlit application that provides a conversational interface for users to interact with various Large Language Models (LLMs) on Amazon Bedrock. Users can ask questions, upload documents, and receive responses from the AI assistant. The app features conversational UI, document upload, caching, chat history storage, session management, model selection, cost tracking, logging, and advanced data analytics tool integration. It can be customized using a config file and is extensible for implementing specialized tools using Docker containers and AWS Lambda. The app requires access to Amazon Bedrock Anthropic Claude Model, S3 bucket, Amazon DynamoDB, Amazon Textract, and optionally Amazon Elastic Container Registry and Amazon Athena for advanced analytics features.
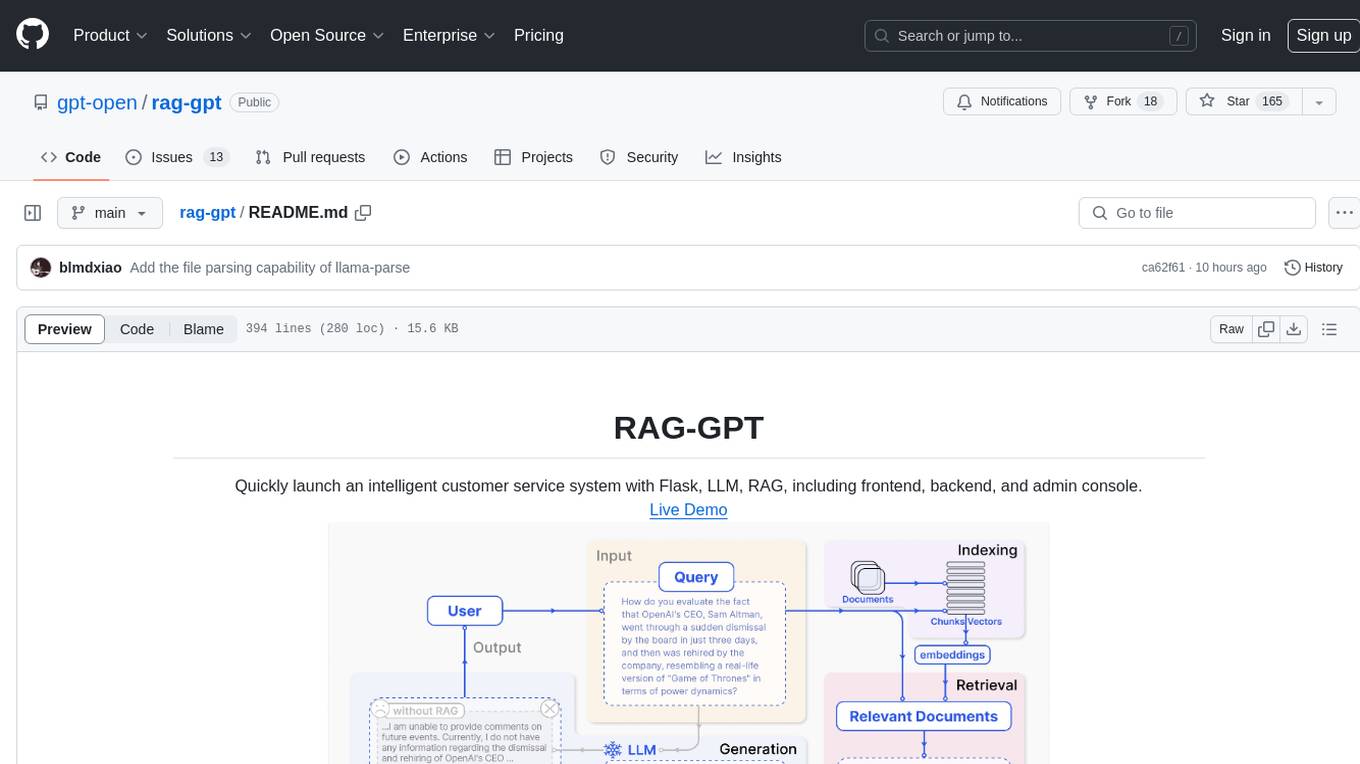
rag-gpt
RAG-GPT is a tool that allows users to quickly launch an intelligent customer service system with Flask, LLM, and RAG. It includes frontend, backend, and admin console components. The tool supports cloud-based and local LLMs, offers quick setup for conversational service robots, integrates diverse knowledge bases, provides flexible configuration options, and features an attractive user interface.
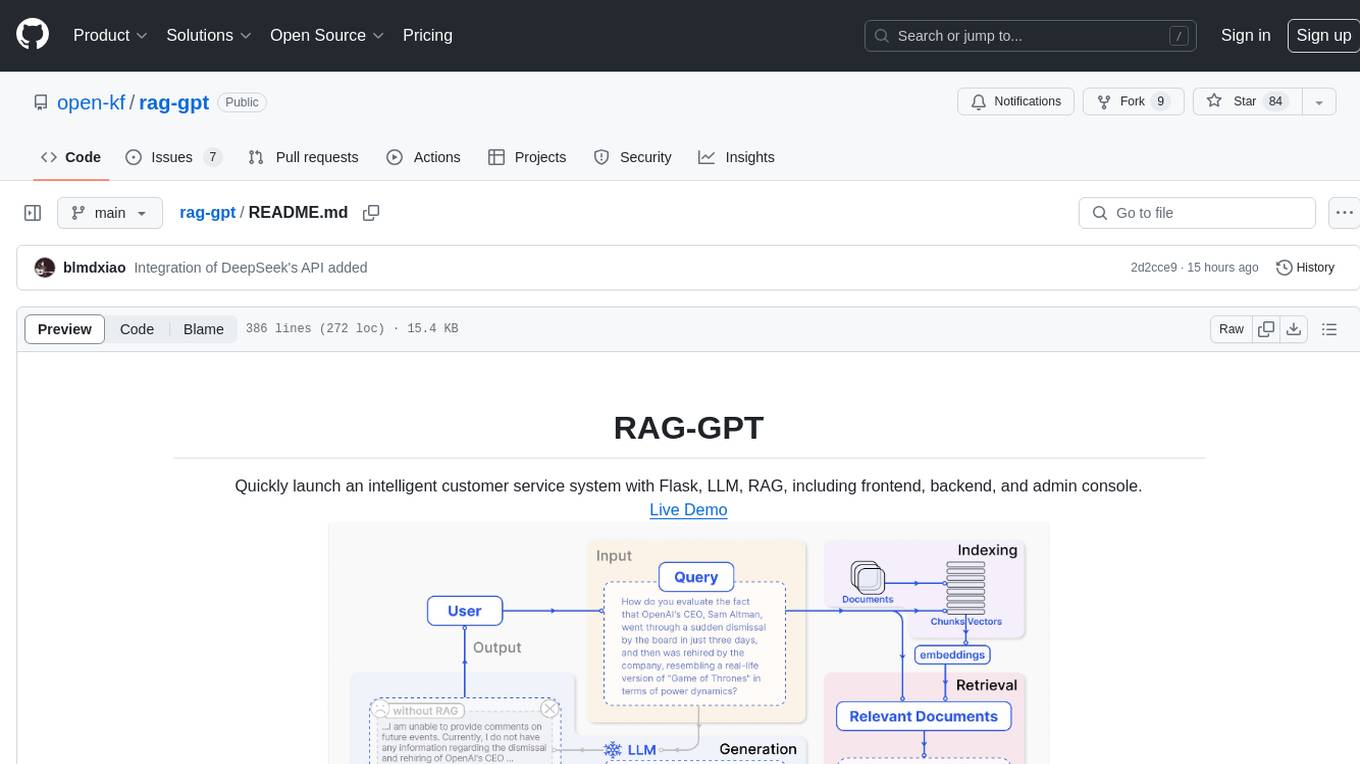
rag-gpt
RAG-GPT is a tool that allows users to quickly launch an intelligent customer service system with Flask, LLM, and RAG. It includes frontend, backend, and admin console components. The tool supports cloud-based and local LLMs, enables deployment of conversational service robots in minutes, integrates diverse knowledge bases, offers flexible configuration options, and features an attractive user interface.
bittensor
Bittensor is an internet-scale neural network that incentivizes computers to provide access to machine learning models in a decentralized and censorship-resistant manner. It operates through a token-based mechanism where miners host, train, and procure machine learning systems to fulfill verification problems defined by validators. The network rewards miners and validators for their contributions, ensuring continuous improvement in knowledge output. Bittensor allows anyone to participate, extract value, and govern the network without centralized control. It supports tasks such as generating text, audio, images, and extracting numerical representations.

nlux
nlux is an open-source Javascript and React JS library that makes it super simple to integrate powerful large language models (LLMs) like ChatGPT into your web app or website. With just a few lines of code, you can add conversational AI capabilities and interact with your favourite LLM.
mandark
Mandark is a lightweight AI tool that can perform various tasks, such as answering questions about codebases, editing files, verifying diffs, estimating token and cost before execution, and working with any codebase. It supports multiple AI models like Claude-3.5 Sonnet, Haiku, GPT-4o-mini, and GPT-4-turbo. Users can run Mandark without installation and easily interact with it through command line options. It offers flexibility in processing individual files or folders and allows for customization with optional AI model selection and output preferences.

Fabric
Fabric is an open-source framework designed to augment humans using AI by organizing prompts by real-world tasks. It addresses the integration problem of AI by creating and organizing prompts for various tasks. Users can create, collect, and organize AI solutions in a single place for use in their favorite tools. Fabric also serves as a command-line interface for those focused on the terminal. It offers a wide range of features and capabilities, including support for multiple AI providers, internationalization, speech-to-text, AI reasoning, model management, web search, text-to-speech, desktop notifications, and more. The project aims to help humans flourish by leveraging AI technology to solve human problems and enhance creativity.
Easy-Translate
Easy-Translate is a script designed for translating large text files with a single command. It supports various models like M2M100, NLLB200, SeamlessM4T, LLaMA, and Bloom. The tool is beginner-friendly and offers seamless and customizable features for advanced users. It allows acceleration on CPU, multi-CPU, GPU, multi-GPU, and TPU, with support for different precisions and decoding strategies. Easy-Translate also provides an evaluation script for translations. Built on HuggingFace's Transformers and Accelerate library, it supports prompt usage and loading huge models efficiently.
For similar tasks
nebula
Nebula is an advanced, AI-powered penetration testing tool designed for cybersecurity professionals, ethical hackers, and developers. It integrates state-of-the-art AI models into the command-line interface, automating vulnerability assessments and enhancing security workflows with real-time insights and automated note-taking. Nebula revolutionizes penetration testing by providing AI-driven insights, enhanced tool integration, AI-assisted note-taking, and manual note-taking features. It also supports any tool that can be invoked from the CLI, making it a versatile and powerful tool for cybersecurity tasks.
binary_ninja_mcp
This repository contains a Binary Ninja plugin, MCP server, and bridge that enables seamless integration of Binary Ninja's capabilities with your favorite LLM client. It provides real-time integration, AI assistance for reverse engineering, multi-binary support, and various MCP tools for tasks like decompiling functions, getting IL code, managing comments, renaming variables, and more.

HydraDragonPlatform
Hydra Dragon Automatic Malware/Executable Analysis Platform offers dynamic and static analysis for Windows, including open-source XDR projects, ClamAV, YARA-X, machine learning AI, behavioral analysis, Unpacker, Deobfuscator, Decompiler, website signatures, Ghidra, Suricata, Sigma, Kernel based protection, and more. It is a Unified Executable Analysis & Detection Framework.

last_layer
last_layer is a security library designed to protect LLM applications from prompt injection attacks, jailbreaks, and exploits. It acts as a robust filtering layer to scrutinize prompts before they are processed by LLMs, ensuring that only safe and appropriate content is allowed through. The tool offers ultra-fast scanning with low latency, privacy-focused operation without tracking or network calls, compatibility with serverless platforms, advanced threat detection mechanisms, and regular updates to adapt to evolving security challenges. It significantly reduces the risk of prompt-based attacks and exploits but cannot guarantee complete protection against all possible threats.
Cyberion-Spark-X
Cyberion-Spark-X is a powerful open-source tool designed for cybersecurity professionals and data analysts. It provides advanced capabilities for analyzing and visualizing large datasets to detect security threats and anomalies. The tool integrates with popular data sources and supports various machine learning algorithms for predictive analytics and anomaly detection. Cyberion-Spark-X is user-friendly and highly customizable, making it suitable for both beginners and experienced professionals in the field of cybersecurity and data analysis.
Here-Comes-the-AI-Worm
Large Language Models (LLMs) are now embedded in everyday tools like email assistants, chat apps, and productivity software. This project introduces DonkeyRail, a lightweight guardrail that detects and blocks malicious self-replicating prompts known as RAGworm within GenAI-powered applications. The guardrail is fast, accurate, and practical for real-world GenAI systems, preventing activities like spam, phishing campaigns, and data leaks.

sec-gemini
Sec-Gemini is an experimental cybersecurity-focused AI tool developed by Google. This repository contains SDKs and a CLI for Sec-Gemini, with SDKs available for Python and TypeScript. Additionally, there is a web component provided to facilitate integration on websites.
For similar jobs
Copilot-For-Security
Microsoft Copilot for Security is a generative AI-powered assistant for daily operations in security and IT that empowers teams to protect at the speed and scale of AI.

AIL-framework
AIL framework is a modular framework to analyze potential information leaks from unstructured data sources like pastes from Pastebin or similar services or unstructured data streams. AIL framework is flexible and can be extended to support other functionalities to mine or process sensitive information (e.g. data leak prevention).
beelzebub
Beelzebub is an advanced honeypot framework designed to provide a highly secure environment for detecting and analyzing cyber attacks. It offers a low code approach for easy implementation and utilizes virtualization techniques powered by OpenAI Generative Pre-trained Transformer. Key features include OpenAI Generative Pre-trained Transformer acting as Linux virtualization, SSH Honeypot, HTTP Honeypot, TCP Honeypot, Prometheus openmetrics integration, Docker integration, RabbitMQ integration, and kubernetes support. Beelzebub allows easy configuration for different services and ports, enabling users to create custom honeypot scenarios. The roadmap includes developing Beelzebub into a robust PaaS platform. The project welcomes contributions and encourages adherence to the Code of Conduct for a supportive and respectful community.

hackingBuddyGPT
hackingBuddyGPT is a framework for testing LLM-based agents for security testing. It aims to create common ground truth by creating common security testbeds and benchmarks, evaluating multiple LLMs and techniques against those, and publishing prototypes and findings as open-source/open-access reports. The initial focus is on evaluating the efficiency of LLMs for Linux privilege escalation attacks, but the framework is being expanded to evaluate the use of LLMs for web penetration-testing and web API testing. hackingBuddyGPT is released as open-source to level the playing field for blue teams against APTs that have access to more sophisticated resources.
awesome-business-of-cybersecurity
The 'Awesome Business of Cybersecurity' repository is a comprehensive resource exploring the cybersecurity market, focusing on publicly traded companies, industry strategy, and AI capabilities. It provides insights into how cybersecurity companies operate, compete, and evolve across 18 solution categories and beyond. The repository offers structured information on the cybersecurity market snapshot, specialists vs. multiservice cybersecurity companies, cybersecurity stock lists, endpoint protection and threat detection, network security, identity and access management, cloud and application security, data protection and governance, security analytics and threat intelligence, non-US traded cybersecurity companies, cybersecurity ETFs, blogs and newsletters, podcasts, market insights and research, and cybersecurity solutions categories.
mcp-scan
MCP-Scan is a security scanning tool designed to detect common security vulnerabilities in Model Context Protocol (MCP) servers. It can auto-discover various MCP configurations, scan both local and remote servers for security issues like prompt injection attacks, tool poisoning attacks, and toxic flows. The tool operates in two main modes - 'scan' for static scanning of installed servers and 'proxy' for real-time monitoring and guardrailing of MCP connections. It offers features like scanning for specific attacks, enforcing guardrailing policies, auditing MCP traffic, and detecting changes to MCP tools. MCP-Scan does not store or log usage data and can be used to enhance the security of MCP environments.
AI-Infra-Guard
A.I.G (AI-Infra-Guard) is an AI red teaming platform by Tencent Zhuque Lab that integrates capabilities such as AI infra vulnerability scan, MCP Server risk scan, and Jailbreak Evaluation. It aims to provide users with a comprehensive, intelligent, and user-friendly solution for AI security risk self-examination. The platform offers features like AI Infra Scan, AI Tool Protocol Scan, and Jailbreak Evaluation, along with a modern web interface, complete API, multi-language support, cross-platform deployment, and being free and open-source under the MIT license.

HydraDragonPlatform
Hydra Dragon Automatic Malware/Executable Analysis Platform offers dynamic and static analysis for Windows, including open-source XDR projects, ClamAV, YARA-X, machine learning AI, behavioral analysis, Unpacker, Deobfuscator, Decompiler, website signatures, Ghidra, Suricata, Sigma, Kernel based protection, and more. It is a Unified Executable Analysis & Detection Framework.


