Best AI tools for< Security Consultant >
Infographic
52 - AI tool Sites

StudentMate
The website studentmate.shuchir.dev is a platform that focuses on enhancing security and privacy for users while browsing the web. It provides information about potential privacy errors, such as insecure connections and invalid certificates, and offers guidance on how to protect personal data. The site educates users on common security threats and how to identify and mitigate them, ultimately aiming to create a safer online environment for everyone.
icetana AI
icetana AI is a self-learning AI tool designed for real-time event detection in security surveillance systems. It seamlessly connects to existing security cameras, learns normal patterns, and highlights unusual events without compromising privacy. The system continuously evolves to improve security team decision-making. icetana AI offers a suite of products for safety and security, analytics, forensics, license plate recognition, facial recognition, and automating security workflows. It is ideal for industries like mall management, education, guarding services, safe cities, and more.
SMshrimant
SMshrimant is a personal website belonging to a Bug Bounty Hunter, Security Researcher, Penetration Tester, and Ethical Hacker. The website showcases the creator's skills and experiences in the field of cybersecurity, including bug hunting, security vulnerability reporting, open-source tool development, and participation in Capture The Flag competitions. Visitors can learn about the creator's projects, achievements, and contact information for inquiries or collaborations.

Facia.ai
Facia.ai is an AI-powered platform that specializes in liveness detection and deepfake detection solutions for businesses and governments. It offers cutting-edge technology to prevent identity fraud, verify authenticity, and enhance security measures. The platform provides accurate face matching, facial recognition, and age verification services, along with customizable integration options and reliable support. Facia.ai aims to combat misinformation, identity fraud, and evolving threats in various industries by leveraging AI algorithms and real-time detection capabilities.
DevOps Security Platform
DevOps Security Platform is an AI-native security tool designed to automate security requirements definition, enforcement, risk assessments, and threat modeling. It helps companies secure their applications by identifying risks early in the Software Development Lifecycle and enforcing security measures before go-live. The platform offers innovative features, customization options, and integrations with existing tools to streamline security processes.
Ambient.ai
Ambient.ai is an AI-powered physical security software that helps prevent security incidents by detecting threats in real-time, auto-clearing false alarms, and accelerating investigations. The platform uses computer vision intelligence to monitor cameras for suspicious activities, decrease alarms, and enable rapid investigations. Ambient.ai offers rich integration ecosystem, detections for a spectrum of threats, unparalleled operational efficiency, and enterprise-grade privacy to ensure maximum security and efficiency for its users.
Abnormal
Abnormal is an AI-powered platform that leverages superhuman understanding of human behavior to protect against email attacks such as phishing, social engineering, and account takeovers. The platform offers unified protection across email and cloud applications, behavioral anomaly detection, account compromise detection, data security, and autonomous AI agents for security operations. Abnormal is recognized as a leader in email security and AI-native security, trusted by over 3,000 customers, including 20% of the Fortune 500. The platform aims to autonomously protect humans, reduce risks, save costs, accelerate AI adoption, and provide industry-leading security solutions.
Ascento
Ascento is an AI-powered security solution that combines robotics and artificial intelligence to secure assets and provide quantitative insights of premises. The application offers features such as detecting people on premises, verifying perimeter integrity, recording property lights, scanning for thermal anomalies, controlling parking lots, and checking doors and windows. Ascento provides advantages like faster threat detection with greater accuracy, cost reduction, autonomous all-terrain robot capabilities, encrypted live communication, and integration with existing video management systems. However, some disadvantages include the need for immediate cost-benefits, training and onboarding requirements, and limited battery life for autonomous charging. The application is suitable for various industries and offers a turnkey solution with 24/7 support and fast replacements.
Greip
Greip is an AI-powered fraud prevention tool that offers a range of services to detect and prevent fraudulent activities in payments, validate card and IBAN details, detect profanity in text, identify VPN/proxy connections, provide IP location intelligence, and more. It combines AI-driven transaction analysis with advanced technology to safeguard financial security and enhance data integrity. Greip's services are trusted by businesses worldwide for secure and reliable protection against fraud.
Lakera
Lakera is the world's most advanced AI security platform that offers cutting-edge solutions to safeguard GenAI applications against various security threats. Lakera provides real-time security controls, stress-testing for AI systems, and protection against prompt attacks, data loss, and insecure content. The platform is powered by a proprietary AI threat database and aligns with global AI security frameworks to ensure top-notch security standards. Lakera is suitable for security teams, product teams, and LLM builders looking to secure their AI applications effectively and efficiently.
Vercel Security Checkpoint
Vercel Security Checkpoint is a web application that provides a security verification process for users accessing the Vercel platform. It ensures the safety and integrity of the platform by verifying the user's browser and enabling JavaScript before proceeding. The checkpoint serves as a protective measure to prevent unauthorized access and potential security threats.
PROTECTSTAR
PROTECTSTAR is an AI-powered cybersecurity application that offers Secure Erasure, Anti Spy, Antivirus AI, and Firewall AI features to protect users from cyber threats. With a focus on privacy and security, PROTECTSTAR aims to provide innovative products using Artificial Intelligence technology. The application has been trusted by over 7 million satisfied users globally and is known for its outstanding detection rate of 99.956%. PROTECTSTAR is committed to environmental sustainability and energy efficiency, as evidenced by its dark mode feature to reduce energy consumption and become CO2-neutral.
Kami Home
Kami Home is an AI-powered security application that provides effortless safety and security for homes. It offers smart alerts, secure cloud video storage, and a Pro Security Alarm system with 24/7 emergency response. The application uses AI-vision to detect humans, vehicles, and animals, ensuring that users receive custom alerts for relevant activities. With features like Fall Detect for seniors living at home, Kami Home aims to protect families and provide peace of mind through advanced technology.
Immunifai
Immunifai is a cybersecurity company that provides AI-powered threat detection and response solutions. The company's mission is to make the world a safer place by protecting organizations from cyberattacks. Immunifai's platform uses machine learning and artificial intelligence to identify and respond to threats in real time. The company's solutions are used by a variety of organizations, including Fortune 500 companies, government agencies, and financial institutions.
moderation.dev
moderation.dev is an AI tool that offers domain-specific guardrails to help organizations identify and manage risks efficiently. By leveraging AI technology, the tool provides custom guardrail models in just one click. It specializes in predicting risks associated with AI chatbots and creating models to intercept queries that a traditional chatbot might struggle to answer accurately.
Blackbird.AI
Blackbird.AI is a narrative and risk intelligence platform that helps organizations identify and protect against narrative attacks created by misinformation and disinformation. The platform offers a range of solutions tailored to different industries and roles, enabling users to analyze threats in text, images, and memes across various sources such as social media, news, and the dark web. By providing context and clarity for strategic decision-making, Blackbird.AI empowers organizations to proactively manage and mitigate the impact of narrative attacks on their reputation and financial stability.
Elie Bursztein AI Cybersecurity Platform
The website is a platform managed by Dr. Elie Bursztein, the Google & DeepMind AI Cybersecurity technical and research lead. It features a collection of publications, blog posts, talks, and press releases related to cybersecurity, artificial intelligence, and technology. Dr. Bursztein shares insights and research findings on various topics such as secure AI workflows, language models in cybersecurity, hate and harassment online, and more. Visitors can explore recent content and subscribe to receive cutting-edge research directly in their inbox.
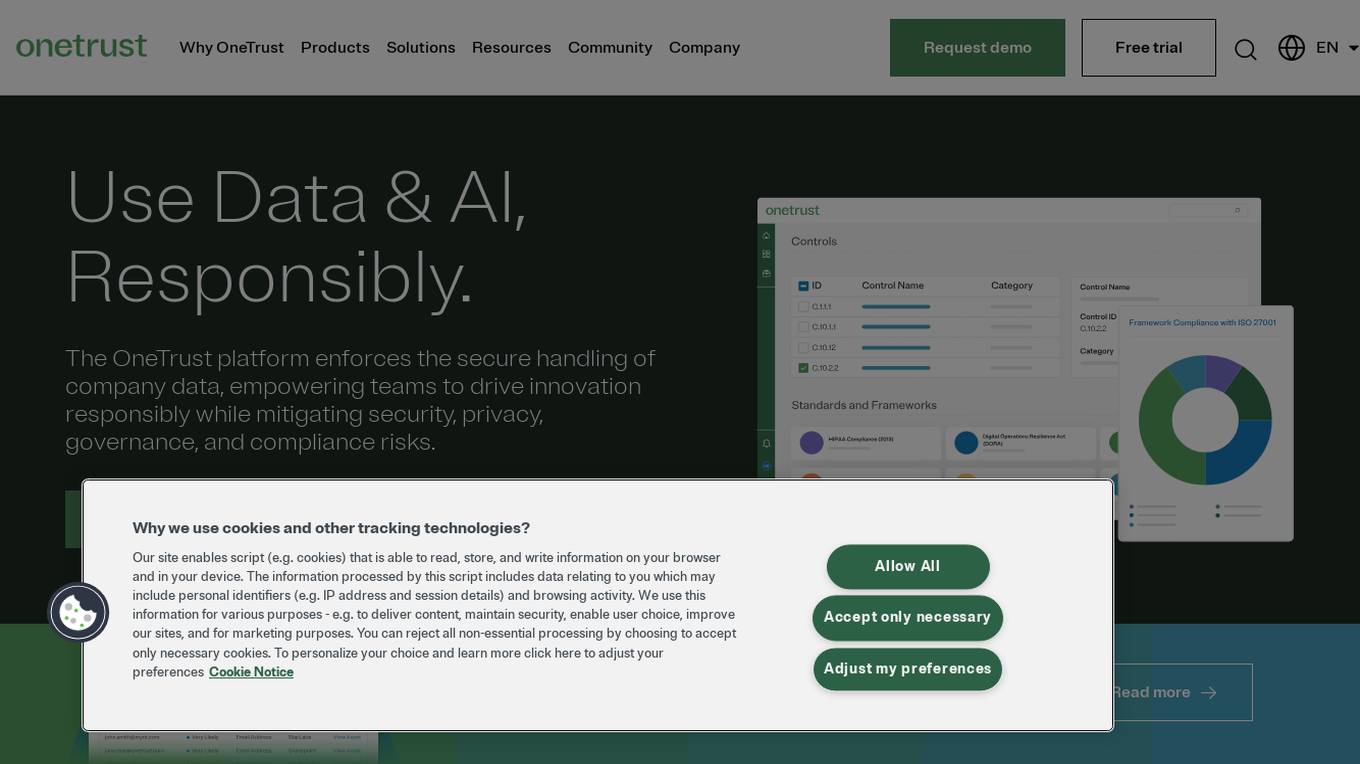
OneTrust
OneTrust is a Trust Intelligence Cloud Solutions platform that leverages data and artificial intelligence to drive trusted innovation across privacy, security, and ethics initiatives. It offers a comprehensive suite of solutions for privacy management, data discovery, security, consent and preferences, AI governance, technology risk and compliance, compliance automation, third-party risk, and ethics program management. With over 14,000 customers worldwide, OneTrust helps organizations manage risk, ensure compliance, and build trust through responsible data and AI usage.
Helsing
Helsing is an AI tool designed to serve and protect democracies by leveraging artificial intelligence technology. The company focuses on developing software-first solutions that enhance defense capabilities and safeguard democratic values. Helsing collaborates with industry and governments to integrate advanced AI with hardware platforms, aiming to achieve technological leadership in the defense sector. The team at Helsing comprises experts with diverse backgrounds in software, defense, intelligence, and artificial intelligence, united by a shared commitment to upholding democratic principles.
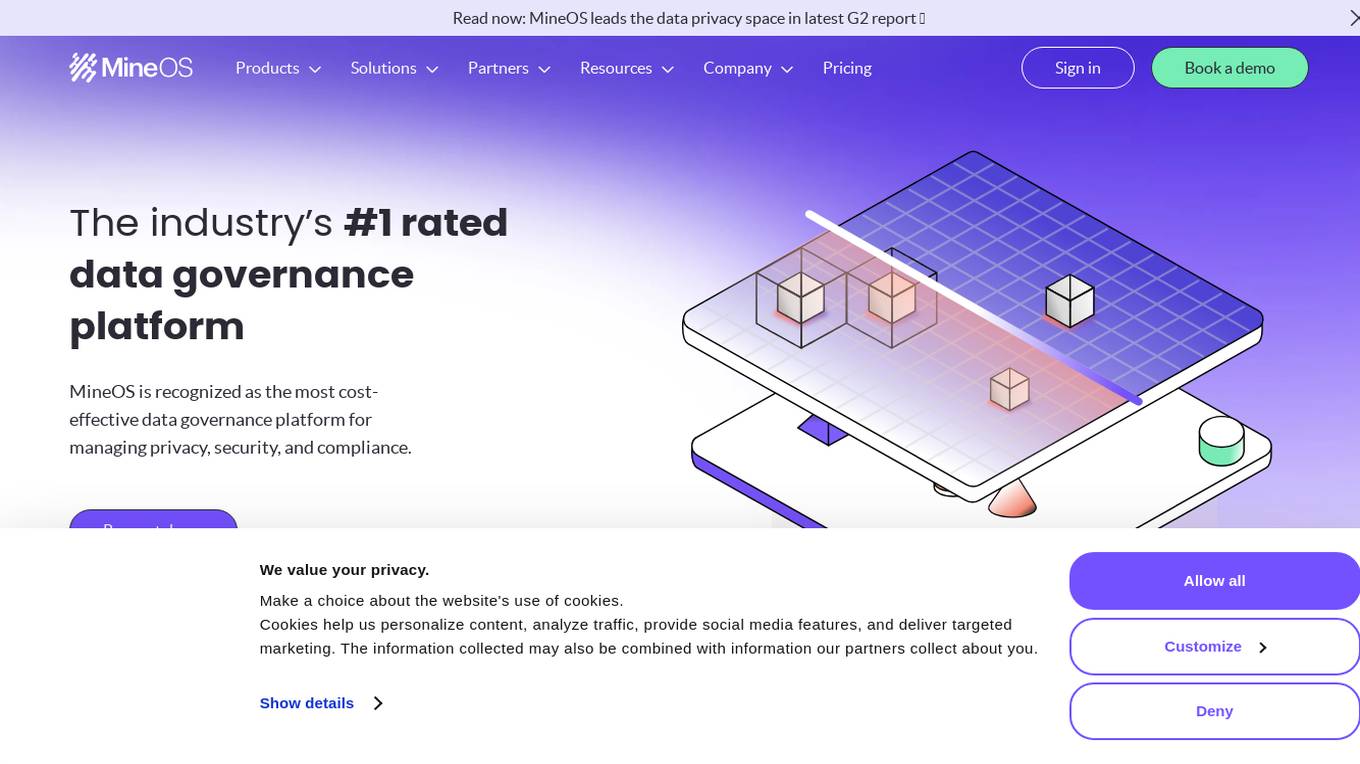
MineOS
MineOS is an automation-driven platform that focuses on privacy, security, and compliance. It offers a comprehensive suite of tools and solutions to help businesses manage their data privacy needs efficiently. By leveraging AI and special discovery methods, MineOS adapts unique data processes to universal privacy standards seamlessly. The platform provides features such as data mapping, AI governance, DSR automations, consent management, and security & compliance solutions to ensure data visibility and governance. MineOS is recognized as the industry's #1 rated data governance platform, offering cost-effective control of data systems and centralizing data subject request handling.
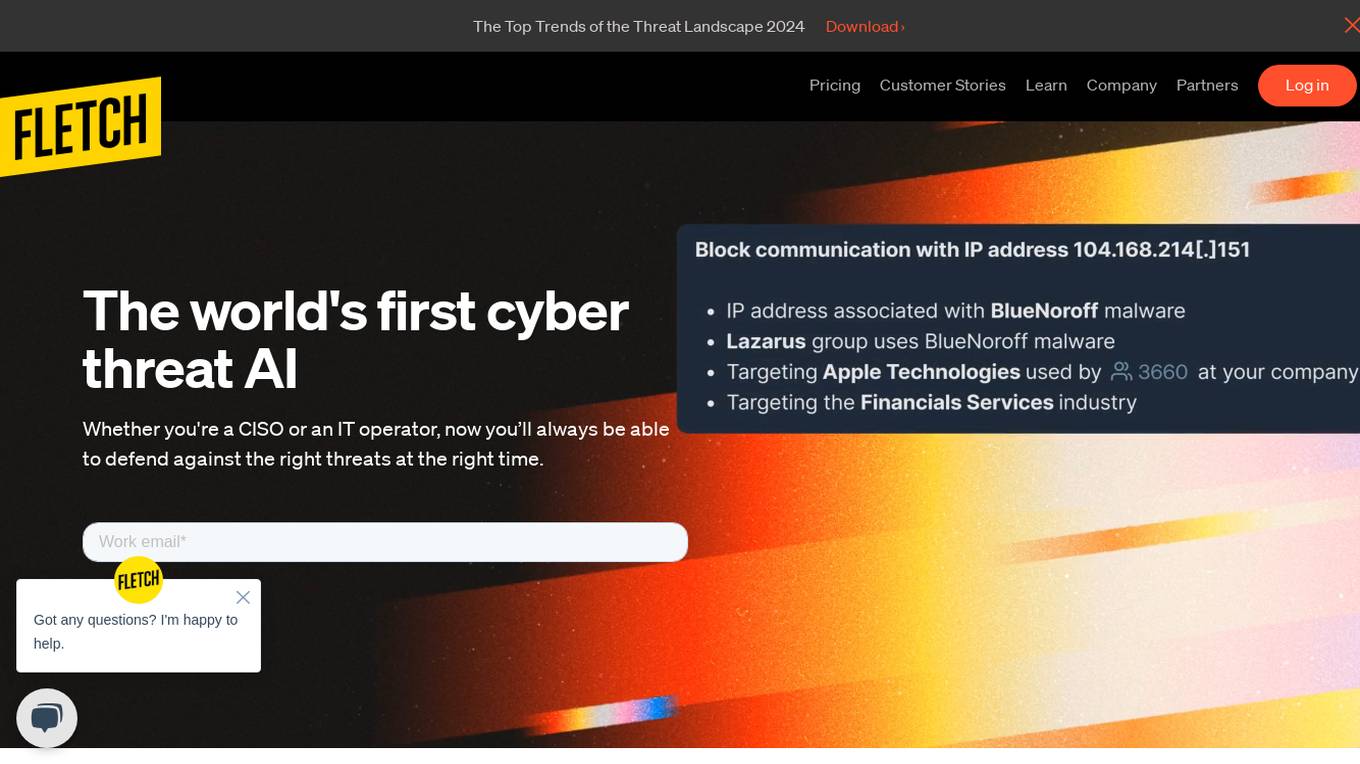
Fletch
Fletch is the world's first cyber threat AI application that helps users stay ahead of cyber threats by automating busywork with AI agents. It continuously trends the threat landscape, forecasts impact, prioritizes alerts, generates tailored advice, and provides daily proactive insights to guide users in defending against threats. Fletch filters and prioritizes alerts, uncovers weaknesses in SaaS supply chains, and offers timely tactical advice to act fast in critical moments. The application also assists in articulating threat messages and provides instant answers through AskFletch chat. Fletch integrates with existing tools, simplifying users' lives and offering hands-on guidance for businesses of all sizes.
CUBE3.AI
CUBE3.AI is a real-time crypto fraud prevention tool that utilizes AI technology to identify and prevent various types of fraudulent activities in the blockchain ecosystem. It offers features such as risk assessment, real-time transaction security, automated protection, instant alerts, and seamless compliance management. The tool helps users protect their assets, customers, and reputation by proactively detecting and blocking fraud in real-time.
Censornet
The website is an AI-powered cybersecurity platform that aims to empower and secure every user and every action. It provides total protection through an integrated cloud platform, offering features such as secure access to web and cloud apps, threat detection and mitigation, advanced data protection, secure remote worker solutions, and AI-powered security leveraging intelligence about user activity and devices. The platform helps businesses anticipate threats, manage vulnerabilities, and protect users worldwide.
Logically
Logically is an AI-powered platform that helps governments, NGOs, and enterprise organizations detect and address harmful and deliberately inaccurate information online. The platform combines artificial intelligence with human expertise to deliver actionable insights and reduce the harms associated with misleading or deceptive information. Logically offers services such as Analyst Services, Logically Intelligence, Point Solutions, and Trust and Safety, focusing on threat detection, online narrative detection, intelligence reports, and harm reduction. The platform is known for its expertise in analysis, data science, and government affairs, providing solutions for various sectors including Corporate, Defense, Digital Platforms, Elections, National Security, and NGO Solutions.
SentinelOne
SentinelOne is an advanced enterprise cybersecurity AI platform that offers a comprehensive suite of AI-powered security solutions for endpoint, cloud, and identity protection. The platform leverages artificial intelligence to anticipate threats, manage vulnerabilities, and protect resources across the entire enterprise ecosystem. With features such as Singularity XDR, Purple AI, and AI-SIEM, SentinelOne empowers security teams to detect and respond to cyber threats in real-time. The platform is trusted by leading enterprises worldwide and has received industry recognition for its innovative approach to cybersecurity.
Control Audits
Control Audits is an AI-powered platform that helps organizations comply with AI & Cyber Security standards. It provides a comprehensive solution for AI and Cyber Security Governance, Risk, and Compliance, offering features such as single pane view, teamwork integration, effortless implementation, seamless task management, and more. The platform is designed to simplify the implementation and compliance process, ensuring that organizations meet standards like ISO 42001, NIST AI RMF, ISO 27001, and others. Control Audits aims to make AI and Cyber Security management efficient and effective for businesses of all sizes.
SentinelOne
SentinelOne is an advanced enterprise cybersecurity AI platform that offers a comprehensive suite of AI-powered security solutions for endpoint, cloud, and identity protection. The platform leverages AI technology to anticipate threats, manage vulnerabilities, and protect resources across the enterprise ecosystem. SentinelOne provides real-time threat hunting, managed services, and actionable insights through its unified data lake, empowering security teams to respond effectively to cyber threats. With a focus on automation, efficiency, and value maximization, SentinelOne is a trusted cybersecurity solution for leading enterprises worldwide.
Vultron Solution
Vultron Solution is an AI tool designed for Federal Proposal Development, offering unparalleled AI capabilities to compress proposal production timeframes, increase revenue, and enhance proposal quality. The tool utilizes proprietary multi-domain models to deliver unique and high-quality content tailored to each organization's needs. With a focus on security and efficiency, Vultron is trusted by leading government contractors to streamline the proposal development process and drive business growth.

Relyance AI
Relyance AI is a platform that offers 360 Data Governance and Trust solutions. It helps businesses safeguard against fines and reputation damage while enhancing customer trust to drive business growth. The platform provides visibility into enterprise-wide data processing, ensuring compliance with regulatory and customer obligations. Relyance AI uses AI-powered risk insights to proactively identify and address risks, offering a unified trust and governance infrastructure. It offers features such as data inventory and mapping, automated assessments, security posture management, and vendor risk management. The platform is designed to streamline data governance processes, reduce costs, and improve operational efficiency.
AI Bot Eye
AI Bot Eye is an AI-based security system that seamlessly integrates with existing CCTV systems to deliver intelligent insights. From AI-powered Fire Detection to Real-Time Intrusion Alerts, AI Bot Eye elevates security systems with cutting-edge AI technology. The application offers features such as Intrusion Detection, Face Recognition, Fire and Smoke Detection, Speed Cam Mode, Safety Kit Detection, HeatMaps Insights, Foot Traffic Analysis, and Numberplate recognition. AI Bot Eye provides advantages like real-time alerts, enhanced security, efficient traffic monitoring, worker compliance monitoring, and optimized operational efficiency. However, the application has disadvantages such as potential false alarms, initial setup complexity, and dependency on existing CCTV infrastructure. The FAQ section addresses common queries about the application, including integration, customization, and compatibility. AI Bot Eye is suitable for jobs such as security guard, surveillance analyst, system integrator, security consultant, and safety officer. The AI keywords associated with the application include AI-based security system, CCTV integration, intrusion detection, and video analytics. Users can utilize AI Bot Eye for tasks like monitor intrusion, analyze foot traffic, detect fire, recognize faces, and manage vehicle entry.

Start Left® Security
Start Left® Security is an AI-driven application security posture management platform that empowers product teams to automate secure-by-design software from people to cloud. The platform integrates security into every facet of the organization, offering a unified solution that aligns with business goals, fosters continuous improvement, and drives innovation. Start Left® Security provides a gamified DevSecOps experience with comprehensive security capabilities like SCA, SBOM, SAST, DAST, Container Security, IaC security, ASPM, and more.
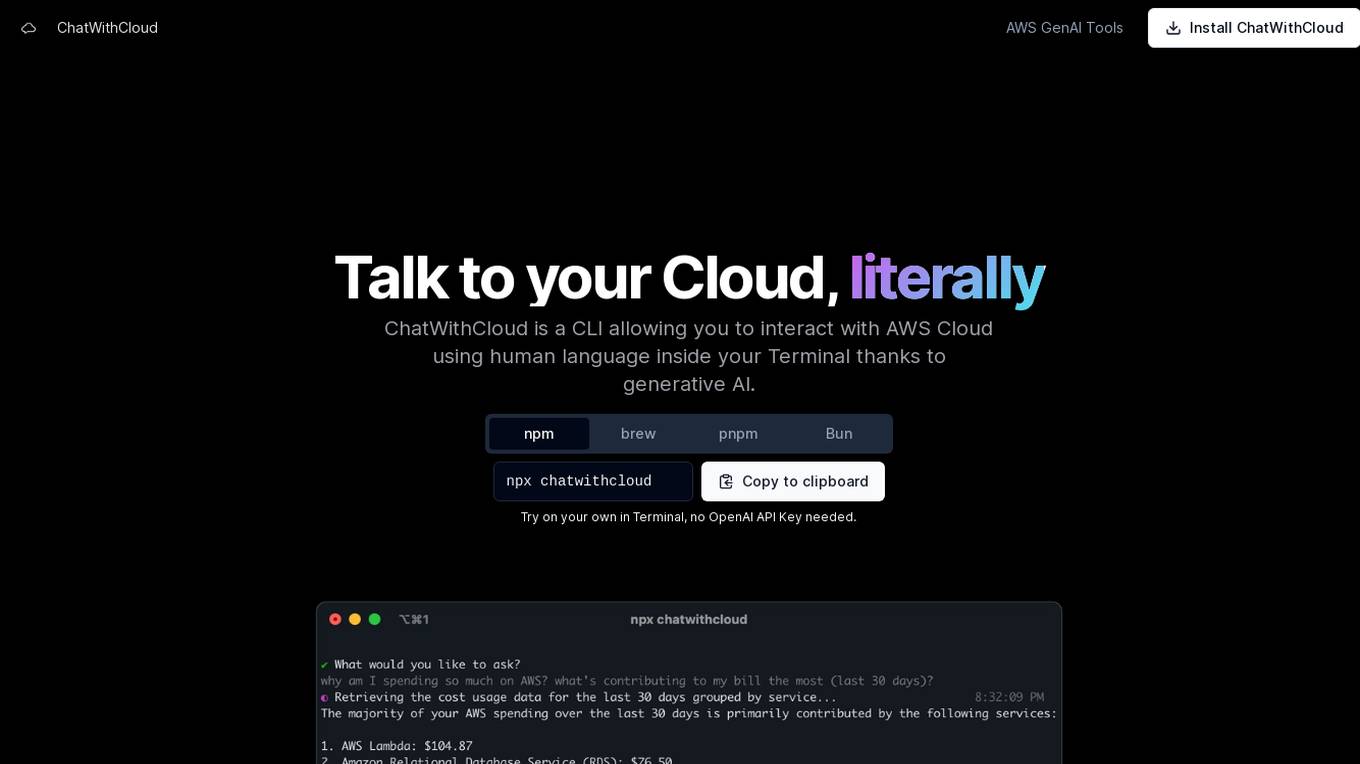
ChatWithCloud
ChatWithCloud is a command-line interface (CLI) tool that enables users to interact with AWS Cloud using natural language within the Terminal, powered by generative AI. It allows users to perform various tasks such as cost analysis, security analysis, troubleshooting, and fixing infrastructure issues without the need for an OpenAI API Key. The tool offers both a lifetime license option and a managed subscription model for users' convenience.
ArcadianAI
ArcadianAI is a modern security monitoring platform that offers easy and affordable solutions for businesses and individuals. The platform provides security cameras, crime maps, and a 30-day free trial for users to experience its features. ArcadianAI uses AI technology for intrusion detection, smart alerts analytics, AI heatmaps search, and AI detection of people. The platform aims to enhance security measures by intelligently contextualizing, analyzing, and safeguarding premises in real-time using existing CCTV footage.
VOLT AI
VOLT AI is a cloud-based enterprise security application that utilizes advanced AI technology to intercept threats in real-time. The application offers solutions for various industries such as education, corporate, and cities, focusing on perimeter security, medical emergencies, and weapons detection. VOLT AI provides features like unified cameras, video intelligence, real-time notifications, automated escalations, and digital twin creation for advanced situational awareness. The application aims to enhance safety and security by detecting security risks and notifying users promptly.

Bagel
Bagel is an AI & Cryptography Research Lab that focuses on making open source AI monetizable by leveraging novel cryptography techniques. Their innovative fine-tuning technology tracks the evolution of AI models, ensuring every contribution is rewarded. Bagel is built for autonomous AIs with large resource requirements and offers permissionless infrastructure for seamless information flow between machines and humans. The lab is dedicated to privacy-preserving machine learning through advanced cryptography schemes.
Masterhackers
Masterhackers is an all-in-one cybersecurity application designed to help cybersecurity professionals and students prepare for certifications and interviews. The platform offers a comprehensive set of tools and resources, including practice tests, flashcards, mock interviews, and personalized feedback with AI. Trusted by students worldwide, Masterhackers aims to enhance users' cybersecurity skills and knowledge through interactive learning experiences.
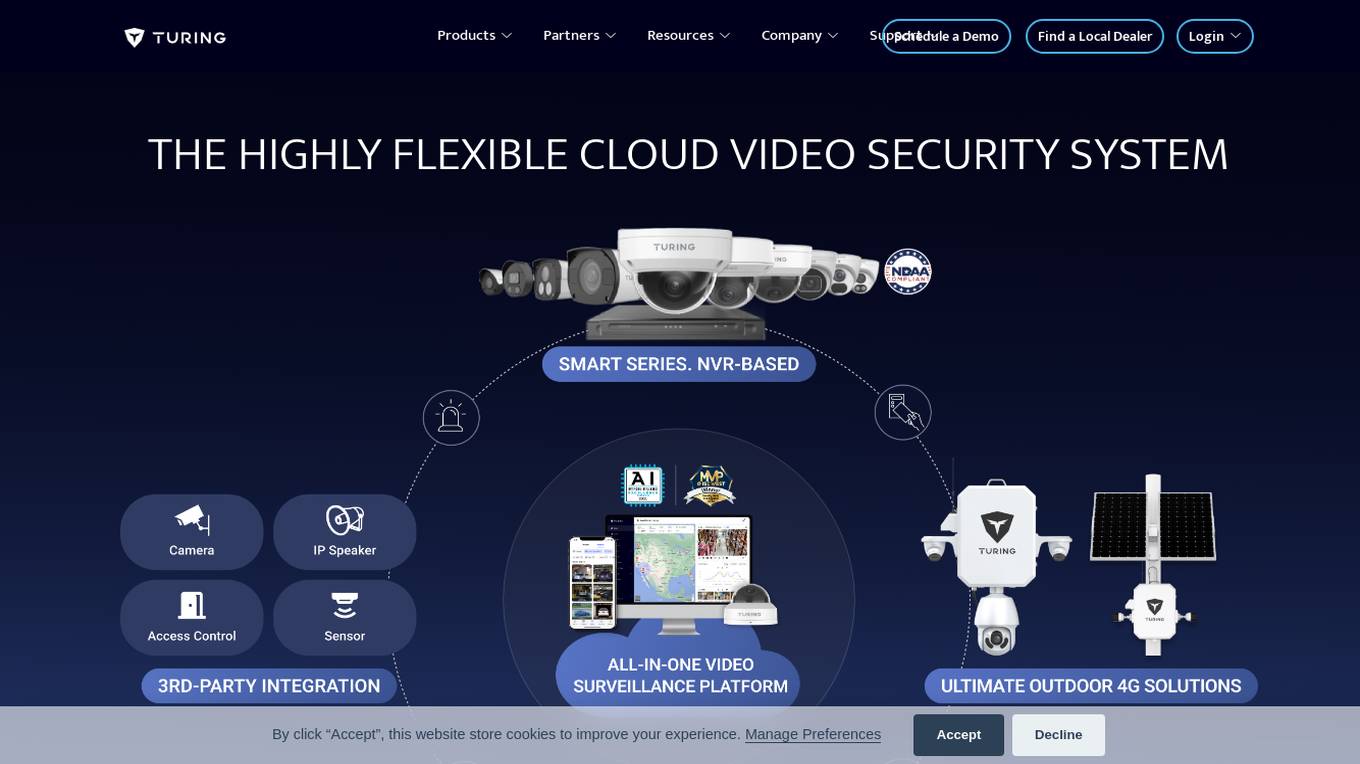
Turing AI
Turing AI is a cloud-based video security system powered by artificial intelligence. It offers a range of AI-powered video surveillance products and solutions to enhance safety, security, and operations. The platform provides smart video search capabilities, real-time alerts, instant video sharing, and hardware offerings compatible with various cameras. With flexible licensing options and integration with third-party devices, Turing AI is trusted by customers across industries for its robust and innovative approach to cloud video security.
Sexy.ai
Sexy.ai is an AI-powered security service provided by Cloudflare to protect websites from online attacks. It helps in identifying and blocking malicious activities such as submitting certain words or phrases, SQL commands, or malformed data. The tool uses advanced algorithms to detect potential threats and prevent unauthorized access to websites. Sexy.ai ensures the safety and integrity of online platforms by offering robust security solutions.
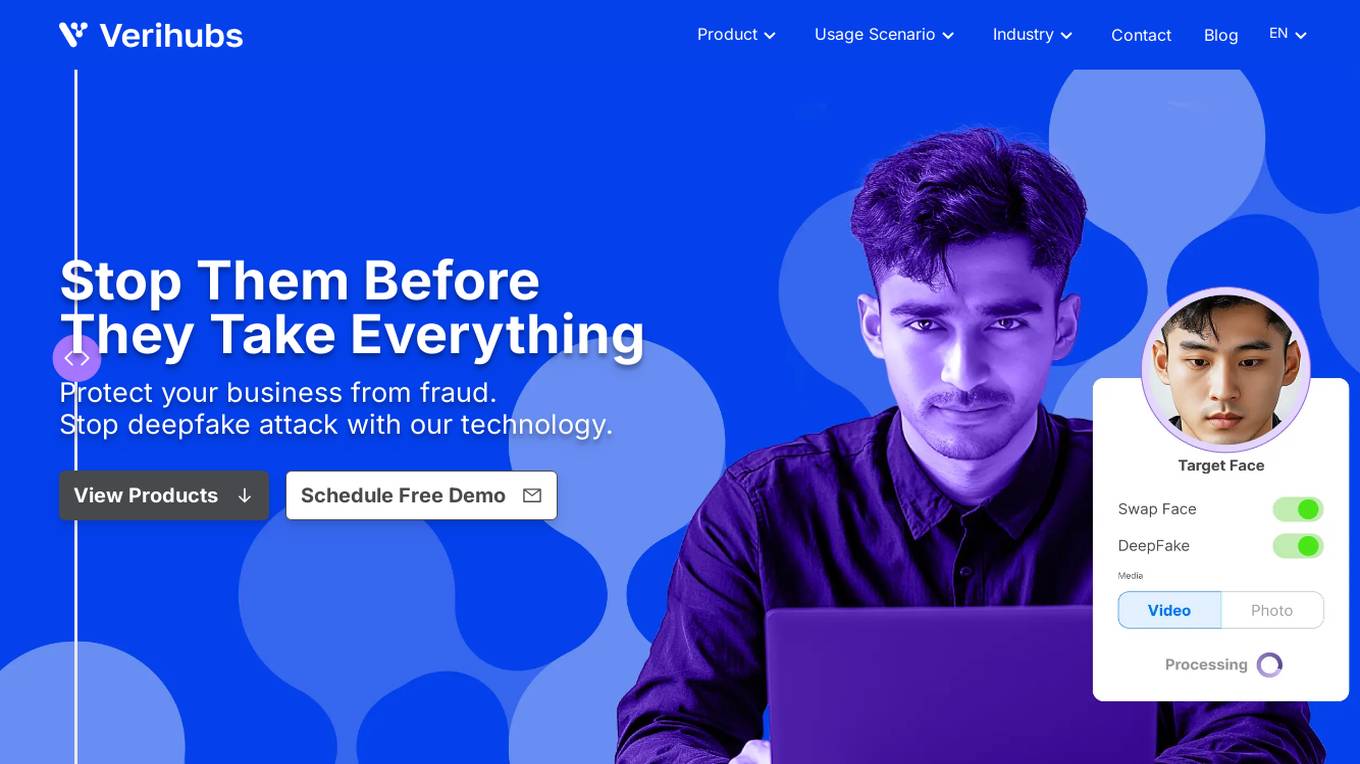
Verihubs
Verihubs is an AI-based verification system that offers backend infrastructure solutions for digital businesses. It provides services such as deepfake detection, face recognition, liveness detection, data extraction, identity verification, phone number verification, and watchlist screening. The platform helps protect businesses from fraud by verifying user identities and preventing AI-based video and image identity fraud. Verihubs is trusted by over 400 clients worldwide for its secure and reliable services.
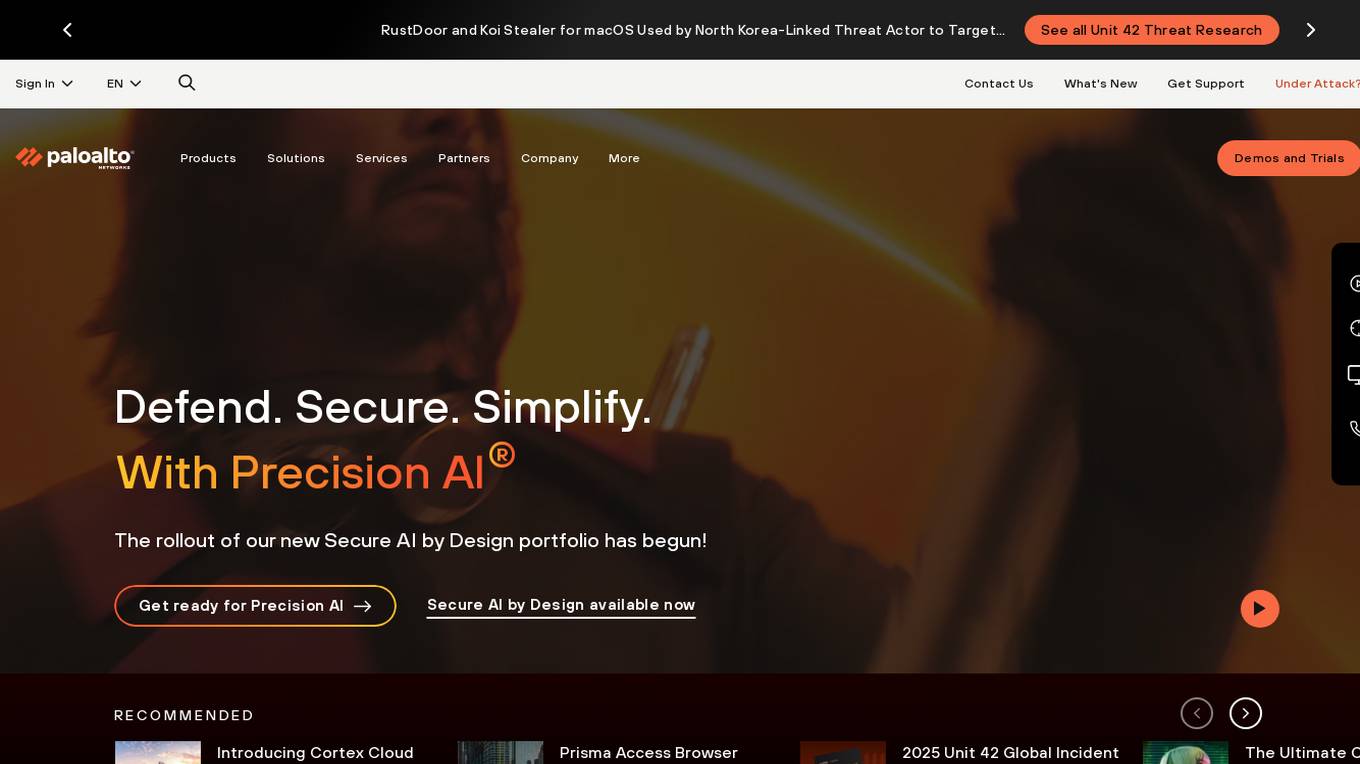
Palo Alto Networks
Palo Alto Networks is a cybersecurity company offering advanced security solutions powered by Precision AI to protect modern enterprises from cyber threats. The company provides network security, cloud security, and AI-driven security operations to defend against AI-generated threats in real time. Palo Alto Networks aims to simplify security and achieve better security outcomes through platformization, intelligence-driven expertise, and proactive monitoring of sophisticated threats.
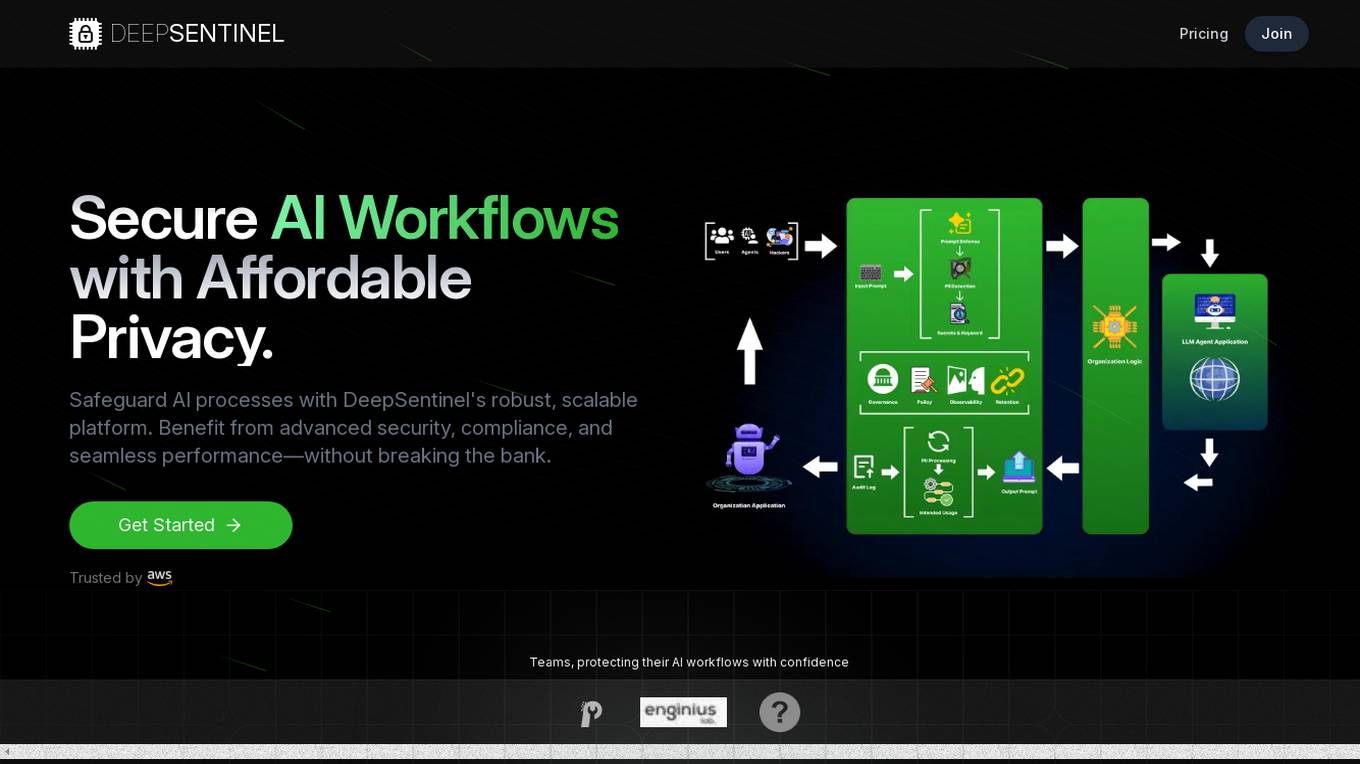
DeepSentinel
DeepSentinel is an AI application that provides secure AI workflows with affordable deep data privacy. It offers a robust, scalable platform for safeguarding AI processes with advanced security, compliance, and seamless performance. The platform allows users to track, protect, and control their AI workflows, ensuring secure and efficient operations. DeepSentinel also provides real-time threat monitoring, granular control, and global trust for securing sensitive data and ensuring compliance with international regulations.
SANS AI Cybersecurity Hackathon
SANS AI Cybersecurity Hackathon is a global virtual competition that challenges participants to design and build AI-driven solutions to secure systems, protect data, and counter emerging cyber threats. The hackathon offers a platform for cybersecurity professionals and students to showcase their creativity and technical expertise, connect with a global community, and make a real-world impact through AI innovation. Participants are required to create open-source solutions addressing pressing cybersecurity challenges by integrating AI, with a focus on areas like threat detection, incident response, vulnerability scanning, security dashboards, digital forensics, and more.
Semgrep
Semgrep is an AI-powered application designed for static analysis and security testing of code. It helps developers find and fix issues in their code, detect vulnerabilities in the software supply chain, and identify hardcoded secrets. Semgrep offers features such as AI-powered noise filtering, dataflow analysis, and tailored remediation guidance. It is known for its speed, transparency, and extensibility, making it a valuable tool for AppSec teams of all sizes.
Kount
Kount is a comprehensive trust and safety platform that offers solutions for fraud detection, chargeback management, identity verification, and compliance. With advanced artificial intelligence and machine learning capabilities, Kount provides businesses with robust data and customizable policies to protect against various threats. The platform is suitable for industries such as ecommerce, health care, online learning, gaming, and more, offering personalized solutions to meet individual business needs.
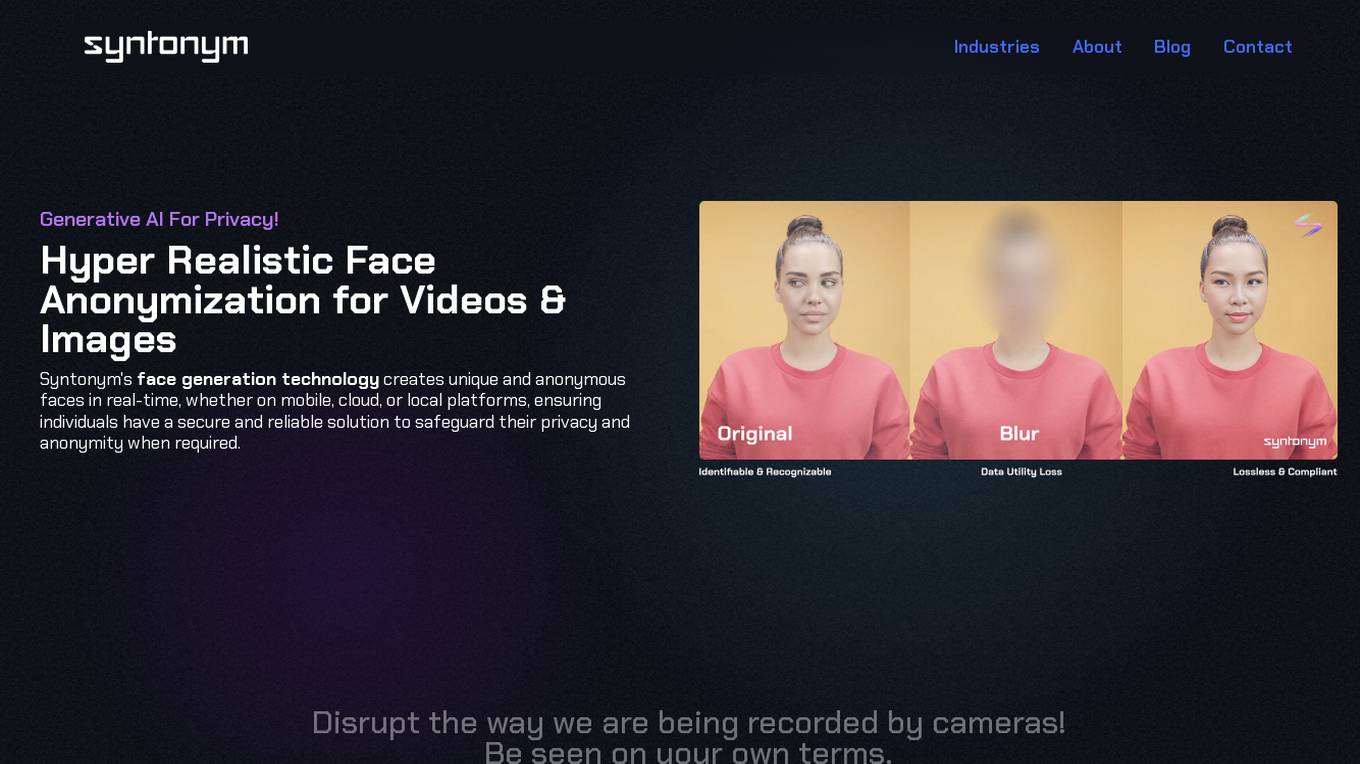
Syntonym
Syntonym is a generative AI tool focused on privacy, specifically offering hyper-realistic face anonymization for videos and images. The technology creates unique and anonymous faces in real-time, ensuring individuals have a secure and reliable solution to safeguard their privacy and anonymity. Syntonym disrupts the way individuals are recorded by cameras, allowing them to be seen on their own terms and integrating privacy layers into video platforms for interactive communication. The tool removes biometrics to unlock unique video processing potential with real-time, lossless anonymization in compliance with privacy regulations.
MegaMatcher ABIS Online
MegaMatcher ABIS Online is an automated biometric identification system developed by Neurotechnology. It offers a turnkey multi-biometric solution for government and enterprise applications worldwide. The system includes features such as enrollment, biometric matching, identity management, data analysis, and deployment options for cloud services or on-premise solutions. With support for fingerprint, face, iris, and palmprint biometric modalities, the system ensures high accuracy, reliability, and unlimited storage of biometric and demographic information. It also provides easy integration through RESTful API and SDK libraries, along with security features like role-based access control and auditability.
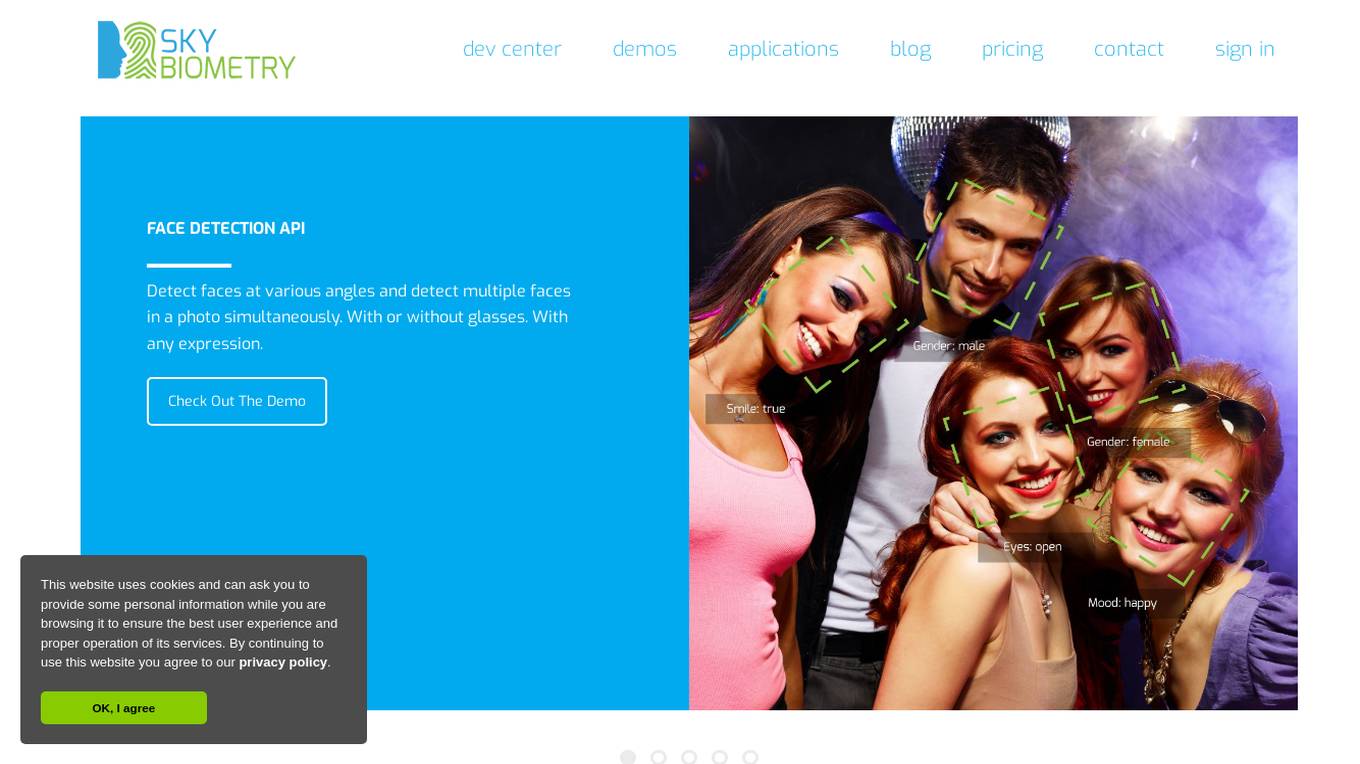
SkyBiometry
Skybiometry is a cloud-based face recognition API service that offers advanced features such as face detection, face recognition, face grouping, and attributes determination. It provides high-quality face recognition algorithms and the ability to detect faces at various angles with or without glasses, expressions, and other attributes. The service is suitable for applications in advertising campaigns, photo management, user authentication, community moderation, and specific projects. Skybiometry allows developers and marketers to integrate face recognition technology into their projects easily, enhancing customization and execution capabilities.
Sprinto
Sprinto is a Continuous Security & Compliance Platform that helps organizations manage and maintain compliance with various frameworks such as SOC 2, ISO 27001, NIST, GDPR, HIPAA, and more. It offers features like Vendor Risk Management, Vulnerability Assessment, Access Control Policies, Security Questionnaire, and Change Management. Sprinto automates evidence collection, streamlines workflows, and provides expert support to ensure organizations stay audit-ready and compliant. The platform is AI-powered, scalable, and supports over 40 compliance frameworks, making it a comprehensive solution for security and compliance needs.

datasurfr
datasurfr is an AI-driven risk monitoring and analysis platform augmented by human intelligence. It provides operational risk data and intelligence that is curated, customized, and comprehensive. The platform offers tailored alerts detected by AI, curated by surfers, and analyzed by subject matter experts for global security teams. datasurfr also offers predictive risk analytics, proactive alert risk assessment, resilience strategy, data-driven decision-making, supply chain resilience, dynamic incident response, regulatory compliance, and future-proofing strategies. The platform's algorithm works on AI detection and structuring, while human-based smart curation eliminates irrelevant data. Subject matter experts provide event summaries with insights and recommendations. datasurfr offers multi-modal communication through intuitive dashboards, mobile apps, emails, WhatsApp, and seamless APIs for versatile consumption.
Nelson
The website is an AI-powered research companion called Nelson, designed to provide rapid and comprehensive answers to complex intelligence, diligence, and geopolitical risk questions. It offers a natural language interface for research queries, hand-selected sources by veteran analysts, and deep regional knowledge. Nelson is trusted by professionals for its reliable and accurate analysis, supporting professional-level research workflows.
GeoInfer
GeoInfer is a professional AI-powered geolocation platform that analyzes photographs to determine where they were taken. It uses visual-only inference technology to examine visual elements like architecture, terrain, vegetation, and environmental markers to identify geographic locations without requiring GPS metadata or EXIF data. The platform offers transparent accuracy levels for different use cases, including a Global Model with 1km-100km accuracy ideal for regional and city-level identification. Additionally, GeoInfer provides custom regional models for organizations requiring higher precision, such as meter-level accuracy for specific geographic areas. The platform is designed for professionals in various industries, including law enforcement, insurance fraud investigation, digital forensics, and security research.
Dreamervision.ai
Dreamervision.ai is an innovative AI tool that utilizes advanced machine learning algorithms to analyze and interpret images and videos. The tool is designed to provide users with valuable insights and information based on visual content, enabling them to make informed decisions and enhance their understanding of the world around them. With its cutting-edge technology, Dreamervision.ai offers a seamless and efficient way to extract meaningful data from visual media, making it a valuable asset for professionals in various industries.
50 - Open Source Tools
Awesome_GPT_Super_Prompting
Awesome_GPT_Super_Prompting is a repository that provides resources related to Jailbreaks, Leaks, Injections, Libraries, Attack, Defense, and Prompt Engineering. It includes information on ChatGPT Jailbreaks, GPT Assistants Prompt Leaks, GPTs Prompt Injection, LLM Prompt Security, Super Prompts, Prompt Hack, Prompt Security, Ai Prompt Engineering, and Adversarial Machine Learning. The repository contains curated lists of repositories, tools, and resources related to GPTs, prompt engineering, prompt libraries, and secure prompting. It also offers insights into Cyber-Albsecop GPT Agents and Super Prompts for custom GPT usage.
specification
OWASP CycloneDX is a full-stack Bill of Materials (BOM) standard that provides advanced supply chain capabilities for cyber risk reduction. The specification supports various types of Bill of Materials including Software, Hardware, Machine Learning, Cryptography, Manufacturing, and Operations. It also includes support for Vulnerability Disclosure Reports, Vulnerability Exploitability eXchange, and CycloneDX Attestations. CycloneDX helps organizations accurately inventory all components used in software development to identify risks, enhance transparency, and enable rapid impact analysis. The project is managed by the CycloneDX Core Working Group under the OWASP Foundation and is supported by the global information security community.
airgeddon
Airgeddon is a versatile bash script designed for Linux systems to conduct wireless network audits. It provides a comprehensive set of features and tools for auditing and securing wireless networks. The script is user-friendly and offers functionalities such as scanning, capturing handshakes, deauth attacks, and more. Airgeddon is regularly updated and supported, making it a valuable tool for both security professionals and enthusiasts.
trickPrompt-engine
This repository contains a vulnerability mining engine based on GPT technology. The engine is designed to identify logic vulnerabilities in code by utilizing task-driven prompts. It does not require prior knowledge or fine-tuning and focuses on prompt design rather than model design. The tool is effective in real-world projects and should not be used for academic vulnerability testing. It supports scanning projects in various languages, with current support for Solidity. The engine is configured through prompts and environment settings, enabling users to scan for vulnerabilities in their codebase. Future updates aim to optimize code structure, add more language support, and enhance usability through command line mode. The tool has received a significant audit bounty of $50,000+ as of May 2024.
PentestGPT
PentestGPT is a penetration testing tool empowered by ChatGPT, designed to automate the penetration testing process. It operates interactively to guide penetration testers in overall progress and specific operations. The tool supports solving easy to medium HackTheBox machines and other CTF challenges. Users can use PentestGPT to perform tasks like testing connections, using different reasoning models, discussing with the tool, searching on Google, and generating reports. It also supports local LLMs with custom parsers for advanced users.
AIRAVAT
AIRAVAT is a multifunctional Android Remote Access Tool (RAT) with a GUI-based Web Panel that does not require port forwarding. It allows users to access various features on the victim's device, such as reading files, downloading media, retrieving system information, managing applications, SMS, call logs, contacts, notifications, keylogging, admin permissions, phishing, audio recording, music playback, device control (vibration, torch light, wallpaper), executing shell commands, clipboard text retrieval, URL launching, and background operation. The tool requires a Firebase account and tools like ApkEasy Tool or ApkTool M for building. Users can set up Firebase, host the web panel, modify Instagram.apk for RAT functionality, and connect the victim's device to the web panel. The tool is intended for educational purposes only, and users are solely responsible for its use.

airgorah
Airgorah is a WiFi security auditing software written in Rust that utilizes the aircrack-ng tools suite. It allows users to capture WiFi traffic, discover connected clients, perform deauthentication attacks, capture handshakes, and crack access point passwords. The software is designed for testing and discovering flaws in networks owned by the user, and requires root privileges to run on Linux systems with a wireless network card supporting monitor mode and packet injection. Airgorah is not responsible for any illegal activities conducted with the software.
galah
Galah is an LLM-powered web honeypot designed to mimic various applications and dynamically respond to arbitrary HTTP requests. It supports multiple LLM providers, including OpenAI. Unlike traditional web honeypots, Galah dynamically crafts responses for any HTTP request, caching them to reduce repetitive generation and API costs. The honeypot's configuration is crucial, directing the LLM to produce responses in a specified JSON format. Note that Galah is a weekend project exploring LLM capabilities and not intended for production use, as it may be identifiable through network fingerprinting and non-standard responses.
stride-gpt
STRIDE GPT is an AI-powered threat modelling tool that leverages Large Language Models (LLMs) to generate threat models and attack trees for a given application based on the STRIDE methodology. Users provide application details, such as the application type, authentication methods, and whether the application is internet-facing or processes sensitive data. The model then generates its output based on the provided information. It features a simple and user-friendly interface, supports multi-modal threat modelling, generates attack trees, suggests possible mitigations for identified threats, and does not store application details. STRIDE GPT can be accessed via OpenAI API, Azure OpenAI Service, Google AI API, or Mistral API. It is available as a Docker container image for easy deployment.
Evilginx3-Phishlets
This repository contains custom Evilginx phishlets that are meticulously crafted and updated for real-world applications. It also offers an advanced course, EvilGoPhish Mastery, focusing on phishing and smishing techniques using EvilGoPhish 3.0. The course complements the repository by providing in-depth guidance on deploying these scripts for red team phishing and smishing campaigns.
agentic_security
Agentic Security is an open-source vulnerability scanner designed for safety scanning, offering customizable rule sets and agent-based attacks. It provides comprehensive fuzzing for any LLMs, LLM API integration, and stress testing with a wide range of fuzzing and attack techniques. The tool is not a foolproof solution but aims to enhance security measures against potential threats. It offers installation via pip and supports quick start commands for easy setup. Users can utilize the tool for LLM integration, adding custom datasets, running CI checks, extending dataset collections, and dynamic datasets with mutations. The tool also includes a probe endpoint for integration testing. The roadmap includes expanding dataset variety, introducing new attack vectors, developing an attacker LLM, and integrating OWASP Top 10 classification.
pwnagotchi
Pwnagotchi is an AI tool leveraging bettercap to learn from WiFi environments and maximize crackable WPA key material. It uses LSTM with MLP feature extractor for A2C agent, learning over epochs to improve performance in various WiFi environments. Units can cooperate using a custom parasite protocol. Visit https://www.pwnagotchi.ai for documentation and community links.
HaE
HaE is a framework project in the field of network security (data security) that combines artificial intelligence (AI) large models to achieve highlighting and information extraction of HTTP messages (including WebSocket). It aims to reduce testing time, focus on valuable and meaningful messages, and improve vulnerability discovery efficiency. The project provides a clear and visual interface design, simple interface interaction, and centralized data panel for querying and extracting information. It also features built-in color upgrade algorithm, one-click export/import of data, and integration of AI large models API for optimized data processing.
sploitcraft
SploitCraft is a curated collection of security exploits, penetration testing techniques, and vulnerability demonstrations intended to help professionals and enthusiasts understand and demonstrate the latest in cybersecurity threats and offensive techniques. The repository is organized into folders based on specific topics, each containing directories and detailed READMEs with step-by-step instructions. Contributions from the community are welcome, with a focus on adding new proof of concepts or expanding existing ones while adhering to the current structure and format of the repository.
CJA_Comprehensive_Jailbreak_Assessment
This public repository contains the paper 'Comprehensive Assessment of Jailbreak Attacks Against LLMs'. It provides a labeling method to label results using Python and offers the opportunity to submit evaluation results to the leaderboard. Full codes will be released after the paper is accepted.
PyWxDump
PyWxDump is a Python tool designed for obtaining WeChat account information, decrypting databases, viewing WeChat chats, and exporting chats as HTML backups. It provides core features such as extracting base address offsets of various WeChat data, decrypting databases, and combining multiple database types for unified viewing. Additionally, it offers extended functions like viewing chat history through the web, exporting chat logs in different formats, and remote viewing of WeChat chat history. The tool also includes document classes for database field descriptions, base address offset methods, and decryption methods for MAC databases. PyWxDump is suitable for network security, daily backup archiving, remote chat history viewing, and more.
aiosmb
aiosmb is a fully asynchronous SMB library written in pure Python, supporting Python 3.7 and above. It offers various authentication methods such as Kerberos, NTLM, SSPI, and NEGOEX. The library supports connections over TCP and QUIC protocols, with proxy support for SOCKS4 and SOCKS5. Users can specify an SMB connection using a URL format, making it easier to authenticate and connect to SMB hosts. The project aims to implement DCERPC features, VSS mountpoint operations, and other enhancements in the future. It is inspired by Impacket and AzureADJoinedMachinePTC projects.
SecReport
SecReport is a platform for collaborative information security penetration testing report writing and exporting, powered by ChatGPT. It standardizes penetration testing processes, allows multiple users to edit reports, offers custom export templates, generates vulnerability summaries and fix suggestions using ChatGPT, and provides APP security compliance testing reports. The tool aims to streamline the process of creating and managing security reports for penetration testing and compliance purposes.
Geolocation-OSINT
Geolocation-OSINT is a repository that provides a comprehensive list of resources, tools, and platforms for geolocation challenges and open-source intelligence. It includes a wide range of mapping services, image search tools, AI-powered geolocation estimators, and satellite imagery archives. The repository covers various aspects of geolocation, from finding GPS coordinates to estimating the size of objects in images. Users can access tools for social media monitoring, street-level imagery, and geospatial analysis. Geolocation-OSINT is a valuable resource for individuals interested in geolocation, mapping, and intelligence gathering.
FlipAttack
FlipAttack is a jailbreak attack tool designed to exploit black-box Language Model Models (LLMs) by manipulating text inputs. It leverages insights into LLMs' autoregressive nature to construct noise on the left side of the input text, deceiving the model and enabling harmful behaviors. The tool offers four flipping modes to guide LLMs in denoising and executing malicious prompts effectively. FlipAttack is characterized by its universality, stealthiness, and simplicity, allowing users to compromise black-box LLMs with just one query. Experimental results demonstrate its high success rates against various LLMs, including GPT-4o and guardrail models.
AgentPoison
AgentPoison is a repository that provides the official PyTorch implementation of the paper 'AgentPoison: Red-teaming LLM Agents via Memory or Knowledge Base Backdoor Poisoning'. It offers tools for red-teaming LLM agents by poisoning memory or knowledge bases. The repository includes trigger optimization algorithms, agent experiments, and evaluation scripts for Agent-Driver, ReAct-StrategyQA, and EHRAgent. Users can fine-tune motion planners, inject queries with triggers, and evaluate red-teaming performance. The codebase supports multiple RAG embedders and provides a unified dataset access for all three agents.
SinkFinder
SinkFinder + LLM is a closed-source semi-automatic vulnerability discovery tool that performs static code analysis on jar/war/zip files. It enhances the capability of LLM large models to verify path reachability and assess the trustworthiness score of the path based on the contextual code environment. Users can customize class and jar exclusions, depth of recursive search, and other parameters through command-line arguments. The tool generates rule.json configuration file after each run and requires configuration of the DASHSCOPE_API_KEY for LLM capabilities. The tool provides detailed logs on high-risk paths, LLM results, and other findings. Rules.json file contains sink rules for various vulnerability types with severity levels and corresponding sink methods.
SinkFinder
SinkFinder is a tool designed to analyze jar and zip files for security vulnerabilities. It allows users to define rules for white and blacklisting specific classes and methods that may pose a risk. The tool provides a list of common security sink names along with severity levels and associated vulnerable methods. Users can use SinkFinder to quickly identify potential security issues in their Java applications by scanning for known sink patterns and configurations.
AutoDAN-Turbo
AutoDAN-Turbo is the official implementation of the ICLR2025 paper 'AutoDAN-Turbo: A Lifelong Agent for Strategy Self-Exploration to Jailbreak LLMs'. It is a black-box jailbreak method that automatically discovers jailbreak strategies without human intervention, achieving high attack success rates on public benchmarks. The tool can incorporate existing human-designed strategies and outperform baseline methods.
finite-monkey-engine
FiniteMonkey is an advanced vulnerability mining engine powered purely by GPT, requiring no prior knowledge base or fine-tuning. Its effectiveness significantly surpasses most current related research approaches. The tool is task-driven, prompt-driven, and focuses on prompt design, leveraging 'deception' and hallucination as key mechanics. It has helped identify vulnerabilities worth over $60,000 in bounties. The tool requires PostgreSQL database, OpenAI API access, and Python environment for setup. It supports various languages like Solidity, Rust, Python, Move, Cairo, Tact, Func, Java, and Fake Solidity for scanning. FiniteMonkey is best suited for logic vulnerability mining in real projects, not recommended for academic vulnerability testing. GPT-4-turbo is recommended for optimal results with an average scan time of 2-3 hours for medium projects. The tool provides detailed scanning results guide and implementation tips for users.
nebula
Nebula is an advanced, AI-powered penetration testing tool designed for cybersecurity professionals, ethical hackers, and developers. It integrates state-of-the-art AI models into the command-line interface, automating vulnerability assessments and enhancing security workflows with real-time insights and automated note-taking. Nebula revolutionizes penetration testing by providing AI-driven insights, enhanced tool integration, AI-assisted note-taking, and manual note-taking features. It also supports any tool that can be invoked from the CLI, making it a versatile and powerful tool for cybersecurity tasks.

HydraDragonAntivirus
Hydra Dragon Antivirus is a comprehensive tool that combines dynamic and static analysis using Sandboxie for Windows with ClamAV, YARA-X, machine learning AI, behavior analysis, NLP-based detection, website signatures, Ghidra, and Snort. The tool provides a Machine Learning Malware and Benign Database for training, along with a guide for compiling from source. It offers features like Ghidra source code analysis, Java Development Kit setup, and detailed logs for malware detections. Users can join the Discord community server for support and follow specific guidelines for preparing the analysis environment. The tool emphasizes security measures such as cleaning up directories, avoiding sharing IP addresses, and ensuring ClamAV database installation. It also includes tips for effective analysis and troubleshooting common issues.
Cyberion-Spark-X
Cyberion-Spark-X is a powerful open-source tool designed for cybersecurity professionals and data analysts. It provides advanced capabilities for analyzing and visualizing large datasets to detect security threats and anomalies. The tool integrates with popular data sources and supports various machine learning algorithms for predictive analytics and anomaly detection. Cyberion-Spark-X is user-friendly and highly customizable, making it suitable for both beginners and experienced professionals in the field of cybersecurity and data analysis.

agentic-radar
The Agentic Radar is a security scanner designed to analyze and assess agentic systems for security and operational insights. It helps users understand how agentic systems function, identify potential vulnerabilities, and create security reports. The tool includes workflow visualization, tool identification, and vulnerability mapping, providing a comprehensive HTML report for easy reviewing and sharing. It simplifies the process of assessing complex workflows and multiple tools used in agentic systems, offering a structured view of potential risks and security frameworks.
Security-Copilot
Microsoft Security Copilot is a generative AI-powered assistant for daily operations in security and IT that empowers teams to protect at the speed and scale of AI. It provides a platform for contributors to enhance and expand the capabilities of the tool through collaborative development. Users can contribute by forking the repository, making changes locally, and submitting pull requests to merge their contributions back into the main repository. The tool is designed to streamline security and IT tasks, automate processes, and enable teams to work more efficiently in managing security operations.
awsome_kali_MCPServers
awsome-kali-MCPServers is a repository containing Model Context Protocol (MCP) servers tailored for Kali Linux environments. It aims to optimize reverse engineering, security testing, and automation tasks by incorporating powerful tools and flexible features. The collection includes network analysis tools, support for binary understanding, and automation scripts to streamline repetitive tasks. The repository is continuously evolving with new features and integrations based on the FastMCP framework, such as network scanning, symbol analysis, binary analysis, string extraction, network traffic analysis, and sandbox support using Docker containers.

mcp
Semgrep MCP Server is a beta server under active development for using Semgrep to scan code for security vulnerabilities. It provides a Model Context Protocol (MCP) for various coding tools to get specialized help in tasks. Users can connect to Semgrep AppSec Platform, scan code for vulnerabilities, customize Semgrep rules, analyze and filter scan results, and compare results. The tool is published on PyPI as semgrep-mcp and can be installed using pip, pipx, uv, poetry, or other methods. It supports CLI and Docker environments for running the server. Integration with VS Code is also available for quick installation. The project welcomes contributions and is inspired by core technologies like Semgrep and MCP, as well as related community projects and tools.
PyInstaCrack
PyInstaCrack is an all-in-one Instagram hacking suite powered by Python. Launched on July 31, 2021, as a beta project, this Python-based tool combines cutting-edge artificial intelligence (AI) with brutal brute-force techniques. It gathers followers and followings data, creates a smart wordlist that automatically filters vulnerable passwords, ignores invalid combinations like emojis or >255 characters, for efficient and deadly attacks. With manipulation of headers and random parameters, PyInstaCrack operates in stealth mode for anti-detection, sneaking like a digital ghost through security loopholes. Designed for elite pentesters, this tool ensures maximum precision with minimal footprint. Each attack is optimized to crush standard defenses without being traced, making it the top choice in the cybersecurity world. PyInstaCrack is a revolution in ethical hacking. Use responsibly to protect, not to harm. Join the top hackers and master the digital realm!
hound
Hound is a security audit automation pipeline for AI-assisted code review that mirrors how expert auditors think, learn, and collaborate. It features graph-driven analysis, sessionized audits, provider-agnostic models, belief system and hypotheses, precise code grounding, and adaptive planning. The system employs a senior/junior auditor pattern where the Scout actively navigates the codebase and annotates knowledge graphs while the Strategist handles high-level planning and vulnerability analysis. Hound is optimized for small-to-medium sized projects like smart contract applications and is language-agnostic.
nexent
Nexent is a powerful tool for analyzing and visualizing network traffic data. It provides comprehensive insights into network behavior, helping users to identify patterns, anomalies, and potential security threats. With its user-friendly interface and advanced features, Nexent is suitable for network administrators, cybersecurity professionals, and anyone looking to gain a deeper understanding of their network infrastructure.
hexstrike-ai
HexStrike AI is an advanced AI-powered penetration testing MCP framework with 150+ security tools and 12+ autonomous AI agents. It features a multi-agent architecture with intelligent decision-making, vulnerability intelligence, and modern visual engine. The platform allows for AI agent connection, intelligent analysis, autonomous execution, real-time adaptation, and advanced reporting. HexStrike AI offers a streamlined installation process, Docker container support, 250+ specialized AI agents/tools, native desktop client, advanced web automation, memory optimization, enhanced error handling, and bypassing limitations.
mcp-scan
MCP-Scan is a security scanning tool designed to detect common security vulnerabilities in Model Context Protocol (MCP) servers. It can auto-discover various MCP configurations, scan both local and remote servers for security issues like prompt injection attacks, tool poisoning attacks, and toxic flows. The tool operates in two main modes - 'scan' for static scanning of installed servers and 'proxy' for real-time monitoring and guardrailing of MCP connections. It offers features like scanning for specific attacks, enforcing guardrailing policies, auditing MCP traffic, and detecting changes to MCP tools. MCP-Scan does not store or log usage data and can be used to enhance the security of MCP environments.
fraim
Fraim is an AI-powered toolkit designed for security engineers to enhance their workflows by leveraging AI capabilities. It offers solutions to find, detect, fix, and flag vulnerabilities throughout the development lifecycle. The toolkit includes features like Risk Flagger for identifying risks in code changes, Code Security Analysis for context-aware vulnerability detection, and Infrastructure as Code Analysis for spotting misconfigurations in cloud environments. Fraim can be run as a CLI tool or integrated into Github Actions, making it a versatile solution for security teams and organizations looking to enhance their security practices with AI technology.
rag-security-scanner
RAG/LLM Security Scanner is a professional security testing tool designed for Retrieval-Augmented Generation (RAG) systems and LLM applications. It identifies critical vulnerabilities in AI-powered applications such as chatbots, virtual assistants, and knowledge retrieval systems. The tool offers features like prompt injection detection, data leakage assessment, function abuse testing, context manipulation identification, professional reporting with JSON/HTML formats, and easy integration with OpenAI, HuggingFace, and custom RAG systems.
mcp-for-security
MCP for Security is a repository that contains Model Context Protocol (MCP) server implementations for various security testing tools, making them accessible through a standardized interface. It aims to provide automated threat detection and reduce human latency in cybersecurity by combining artificial intelligence and security tools. Users can access a variety of tools for subdomain enumeration, reconnaissance, vulnerability scanning, web crawling, HTTP security analysis, mobile application security testing, network scanning, SSL/TLS configuration analysis, DNS brute-forcing, HTTP request smuggling detection, SQL injection testing, historical URL retrieval, and WordPress vulnerability scanning. The repository encourages collaboration and rapid evolution through open-source projects.
Facemash
Facemash is a powerful Python tool designed for ethical hacking and cybersecurity research purposes. It combines brute force techniques with AI-driven strategies to crack Facebook accounts with precision. The tool offers advanced password strategies, multiple brute force methods, and real-time logs for total control. Facemash is not open-source and is intended for responsible use only.
Guardrails
Guardrails is a security tool designed to help developers identify and fix security vulnerabilities in their code. It provides automated scanning and analysis of code repositories to detect potential security issues, such as sensitive data exposure, injection attacks, and insecure configurations. By integrating Guardrails into the development workflow, teams can proactively address security concerns and reduce the risk of security breaches. The tool offers detailed reports and actionable recommendations to guide developers in remediation efforts, ultimately improving the overall security posture of the codebase. Guardrails supports multiple programming languages and frameworks, making it versatile and adaptable to different development environments. With its user-friendly interface and seamless integration with popular version control systems, Guardrails empowers developers to prioritize security without compromising productivity.

Sec-Interview
Sec-Interview is a comprehensive collection of cybersecurity interview questions with reference answers, covering network security, red team, reverse engineering, cryptography, and binary. It is suitable for all cybersecurity positions. The repository contains thousands of security interview questions categorized for easy access. Contributors are welcome to submit interview questions or provide feedback for future versions. Special thanks to various individuals and teams for their valuable contributions and support during the project's organization and improvement.

DeepAudit
DeepAudit is an AI audit team accessible to everyone, making vulnerability discovery within reach. It is a next-generation code security audit platform based on Multi-Agent collaborative architecture. It simulates the thinking mode of security experts, achieving deep code understanding, vulnerability discovery, and automated sandbox PoC verification through multiple intelligent agents (Orchestrator, Recon, Analysis, Verification). DeepAudit aims to address the three major pain points of traditional SAST tools: high false positive rate, blind spots in business logic, and lack of verification means. Users only need to import the project, and DeepAudit automatically starts working: identifying the technology stack, analyzing potential risks, generating scripts, sandbox verification, and generating reports, ultimately outputting a professional audit report. The core concept is to let AI attack like a hacker and defend like an expert.
AI-Infra-Guard
A.I.G (AI-Infra-Guard) is an AI red teaming platform by Tencent Zhuque Lab that integrates capabilities such as AI infra vulnerability scan, MCP Server risk scan, and Jailbreak Evaluation. It aims to provide users with a comprehensive, intelligent, and user-friendly solution for AI security risk self-examination. The platform offers features like AI Infra Scan, AI Tool Protocol Scan, and Jailbreak Evaluation, along with a modern web interface, complete API, multi-language support, cross-platform deployment, and being free and open-source under the MIT license.
augustus
Augustus is a Go-based LLM vulnerability scanner designed for security professionals to test large language models against a wide range of adversarial attacks. It integrates with 28 LLM providers, covers 210+ adversarial attacks including prompt injection, jailbreaks, encoding exploits, and data extraction, and produces actionable vulnerability reports. The tool is built for production security testing with features like concurrent scanning, rate limiting, retry logic, and timeout handling out of the box.
BoxPwnr
BoxPwnr is a tool designed to test the performance of different agentic architectures using Large Language Models (LLMs) to autonomously solve HackTheBox machines. It provides a plug and play system with various strategies and platforms supported. BoxPwnr uses an iterative process where LLMs receive system prompts, suggest commands, execute them in a Docker container, analyze outputs, and repeat until the flag is found. The tool automates commands, saves conversations and commands for analysis, and tracks usage statistics. With recent advancements in LLM technology, BoxPwnr aims to evaluate AI systems' reasoning capabilities, creative thinking, security understanding, problem-solving skills, and code generation abilities.
CTFCrackTools
CTFCrackTools X is the next generation of CTFCrackTools, featuring extreme performance and experience, extensible node-based architecture, and future-oriented technology stack. It offers a visual node-based workflow for encoding and decoding processes, with 43+ built-in algorithms covering common CTF needs like encoding, classical ciphers, modern encryption, hashing, and text processing. The tool is lightweight (< 15MB), high-performance, and cross-platform, supporting Windows, macOS, and Linux without the need for a runtime environment. It aims to provide a beginner-friendly tool for CTF enthusiasts to easily work on challenges and improve their skills.
CyberStrikeAI
CyberStrikeAI is an AI-native security testing platform built in Go that integrates 100+ security tools, an intelligent orchestration engine, role-based testing with predefined security roles, a skills system with specialized testing skills, and comprehensive lifecycle management capabilities. It enables end-to-end automation from conversational commands to vulnerability discovery, attack-chain analysis, knowledge retrieval, and result visualization, delivering an auditable, traceable, and collaborative testing environment for security teams. The platform features an AI decision engine with OpenAI-compatible models, native MCP implementation with various transports, prebuilt tool recipes, large-result pagination, attack-chain graph, password-protected web UI, knowledge base with vector search, vulnerability management, batch task management, role-based testing, and skills system.
shannon
Shannon is an AI pentester that delivers actual exploits, not just alerts. It autonomously hunts for attack vectors in your code, then uses its built-in browser to execute real exploits, such as injection attacks, and auth bypass, to prove the vulnerability is actually exploitable. Shannon closes the security gap by acting as your on-demand whitebox pentester, providing concrete proof of vulnerabilities to let you ship with confidence. It is a core component of the Keygraph Security and Compliance Platform, automating penetration testing and compliance journey. Shannon Lite achieves a 96.15% success rate on a hint-free, source-aware XBOW benchmark.
65 - OpenAI Gpts
Detective Sherlock
Your AI Detective for piecing together puzzles and solving any mystery.
Crime and Mystery Solver
Expert in solving crimes and mysteries, adept at handling extensive data.
Cyber Test & CareerPrep
Helping you study for cybersecurity certifications and get the job you want!
Cyber Threat Intelligence
An automated cyber threat intelligence expert configured and trained by Bob Gourley. Pls provide feedback. Find Bob on X at @bobgourley
Prepper Survival Guide
... A Guide for Prepping and Survival Strategies ... Life is unpredictable, and while we often hope for the best ... prepare for the worst.
Cyber Audit and Pentest RFP Builder
Generates cybersecurity audit and penetration test specifications.
Blue Team Guide
it is a meticulously crafted arsenal of knowledge, insights, and guidelines that is shaped to empower organizations in crafting, enhancing, and refining their cybersecurity defenses
Cyber Guardian
I'm your personal cybersecurity advisor, here to help you stay safe online.

InfoSec Advisor
An expert in the technical, organizational, infrastructural and personnel aspects of information security management systems (ISMS)

CISO GPT
Specialized LLM in computer security, acting as a CISO with 20 years of experience, providing precise, data-driven technical responses to enhance organizational security.
👑 Data Privacy for PI & Security Firms 👑
Private Investigators and Security Firms, given the nature of their work, handle highly sensitive information and must maintain strict confidentiality and data privacy standards.
Website Security with Jim Walker | HackRepair.com
Jim Walker "The Hack Repair Guy" is a WordPress Security Expert. He Manages HackRepair.com and HackGuard.com, a Malware Cleanup and WordPress Management Service.
ethicallyHackingspace (eHs)® (Full Spectrum)™
Full Spectrum Space Cybersecurity Professional ™ AI-copilot (BETA)
The Sabotage Strategist
Playful strategist using humor and proximity to offer 'sabotage' tactics from a 1944 OSS Manual.
Mónica
CSIRT que lidera un equipo especializado en detectar y responder a incidentes de seguridad, maneja la contención y recuperación, organiza entrenamientos y simulacros, elabora reportes para optimizar estrategias de seguridad y coordina con entidades legales cuando es necesario
Java Security Expert
Java Security Expert offering advice on best practices and resolving security issues.
CyberNews GPT
CyberNews GPT is an assistant that provides the latest security news about cyber threats, hackings and breaches, malware, zero-day vulnerabilities, phishing, scams and so on.
Incident Response Forensic Techniques
help organizations in investigating computer security incidents and troubleshooting some information technology (IT) operational problems by providing practical guidance on performing computer and network forensics.
API Content Warehouse Leak Help
Comprehensive analysis of Google API Content Warehouse Leak
Detective
Dedicated investigator resolving diverse crimes, ensuring justice and community safety.
Aegis ⛨
Interactive Cybersecurity Tutor capable of autonomous management of your knowledge.

Sikich CMMC Coach
CMMC Coach: Guiding through CMMC processes with tailored strategies, interactive training, and regulatory compliance. https://www.sikich.com/technology/contact-us/ 877.403.5227 | [email protected]