Best AI tools for< Identify Security Issues >
20 - AI tool Sites
Giskard
Giskard is a testing platform for AI systems that helps companies protect against biases, performance, and security issues in AI models. It offers automated detection of issues, compliance with the EU AI Act, and standard methodologies for optimal model deployment. The platform streamlines testing processes, collaboration between data scientists and business stakeholders, and identification of biases in AI models. Giskard is trusted by Enterprise AI teams and aims to ensure the quality, security, and compliance of AI systems.

DevSecCops
DevSecCops is an AI-driven automation platform designed to revolutionize DevSecOps processes. The platform offers solutions for cloud optimization, machine learning operations, data engineering, application modernization, infrastructure monitoring, security, compliance, and more. With features like one-click infrastructure security scan, AI engine security fixes, compliance readiness using AI engine, and observability, DevSecCops aims to enhance developer productivity, reduce cloud costs, and ensure secure and compliant infrastructure management. The platform leverages AI technology to identify and resolve security issues swiftly, optimize AI workflows, and provide cost-saving techniques for cloud architecture.
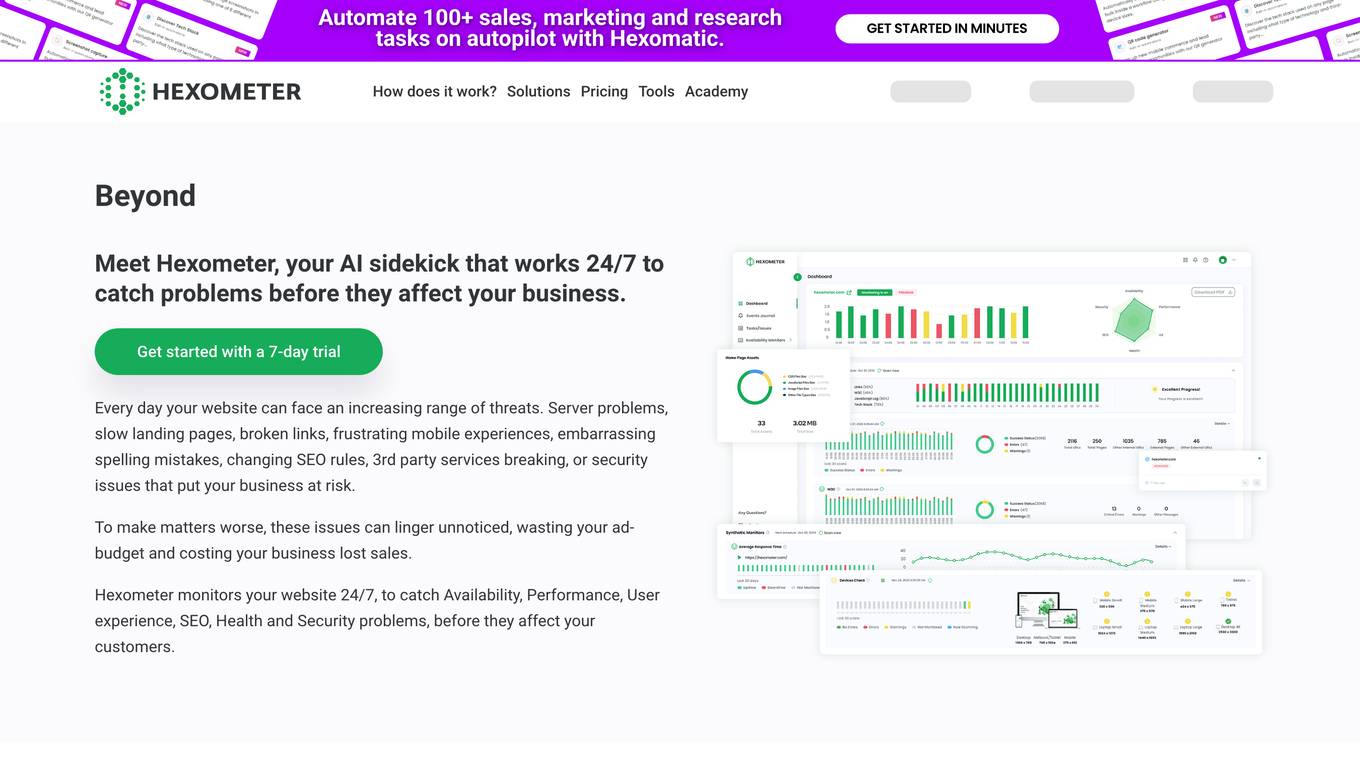
Hexometer
Hexometer is an AI-powered website monitoring tool that helps businesses protect and grow their online presence. It continuously monitors websites for availability, performance, user experience, SEO, health, and security issues, and alerts businesses when problems are detected. Hexometer also provides businesses with insights into their website's performance and helps them identify opportunities for improvement.
403 Forbidden
The website seems to be experiencing a 403 Forbidden error, which indicates that the server is refusing to respond to the request. This error message is often encountered when the user is trying to access a webpage or resource that they are not authorized to view. The '403 Forbidden' error is a standard HTTP status code that communicates that the server understands the request but refuses to authorize it. This could be due to insufficient permissions, incorrect authentication credentials, or other security-related issues. It is important to troubleshoot the cause of the error and ensure that proper access permissions are in place to resolve the issue.
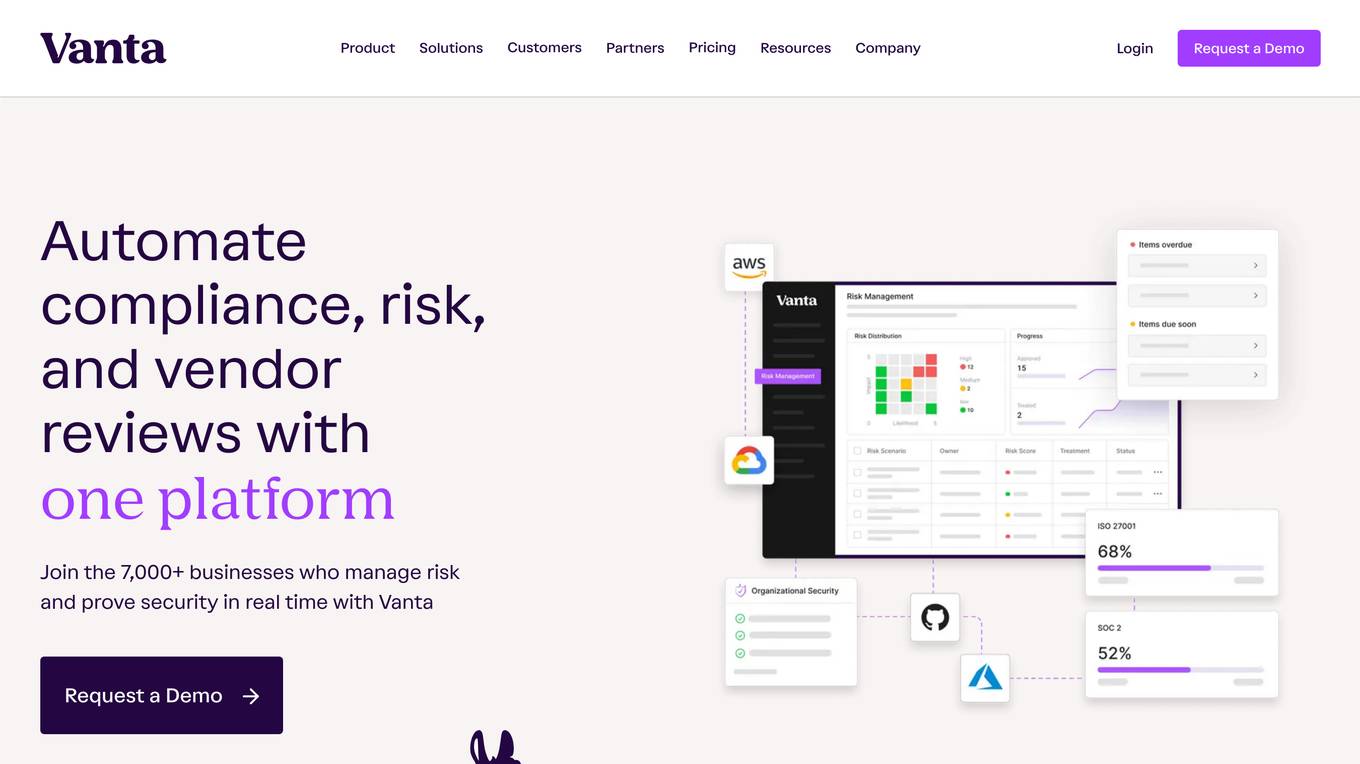
Vanta
Vanta is a trust management platform that helps businesses automate compliance, streamline security reviews, and build trust with customers. It offers a range of features to help businesses manage risk and prove security in real time, including: * **Compliance automation:** Vanta automates up to 90% of the work for security and privacy frameworks, making it easy for businesses to achieve and maintain compliance. * **Real-time monitoring:** Vanta provides real-time visibility into the state of a business's security posture, with hourly tests and alerts for any issues. * **Holistic risk visibility:** Vanta offers a single view across key risk surfaces in a business, including employees, assets, and vendors, to help businesses identify and mitigate risks. * **Efficient audits:** Vanta streamlines the audit process, making it easier for businesses to prepare for and complete audits. * **Integrations:** Vanta integrates with a range of tools and platforms to help businesses automate security and compliance tasks.
403 Forbidden
The website is currently displaying a '403 Forbidden' error message, which indicates that the server is refusing to respond to the request. This error is often caused by incorrect permissions on the server or a misconfiguration in the server software. The 'openresty' message suggests that the server is using the OpenResty web platform. Users encountering this error should contact the website administrator for assistance in resolving the issue.

403 Forbidden
The website displays a '403 Forbidden' error message, indicating that the server understood the request but refuses to authorize it. This error is typically due to insufficient permissions or server misconfiguration. The 'openresty' mentioned in the text refers to a web platform based on NGINX and LuaJIT, often used for building dynamic web applications. The website seems to be experiencing server-side issues preventing access to the requested resource.
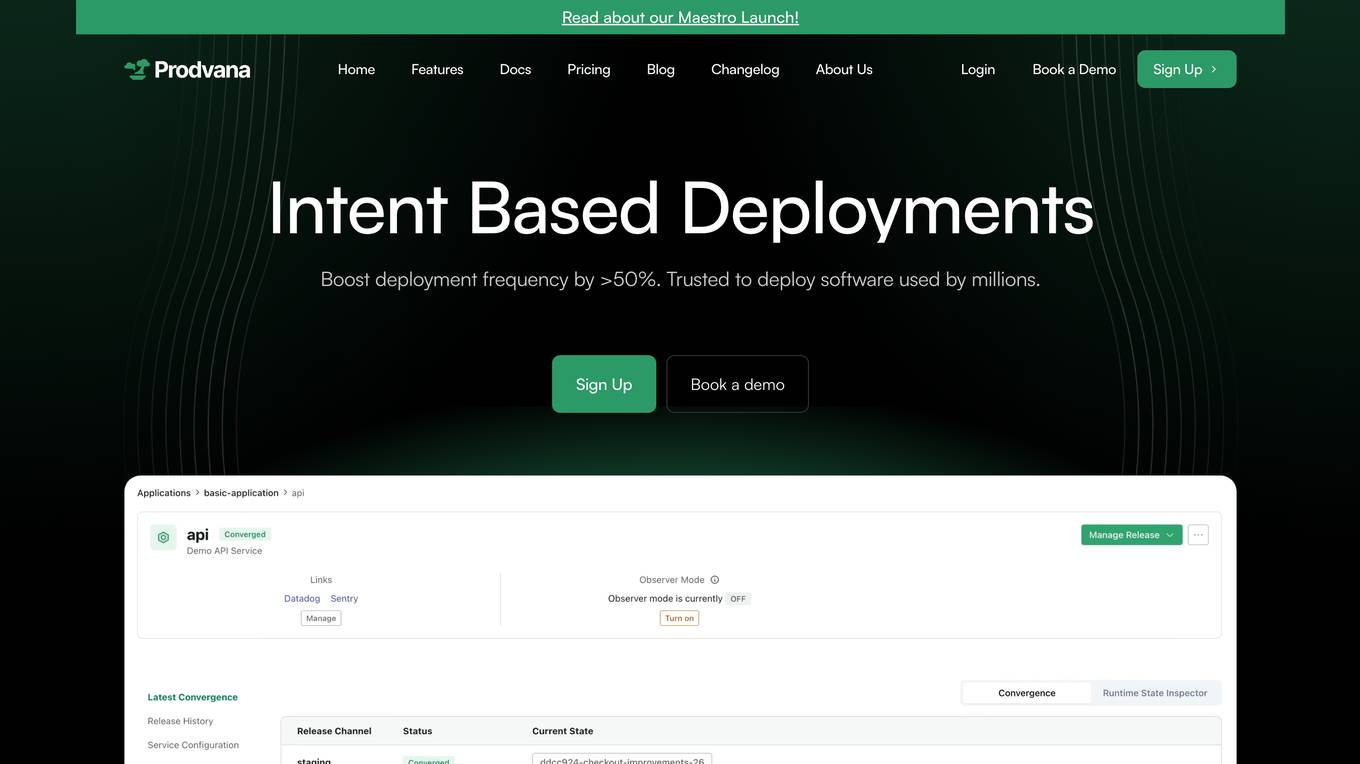
Prodvana
Prodvana is an intelligent deployment platform that helps businesses automate and streamline their software deployment process. It provides a variety of features to help businesses improve the speed, reliability, and security of their deployments. Prodvana is a cloud-based platform that can be used with any type of infrastructure, including on-premises, hybrid, and multi-cloud environments. It is also compatible with a wide range of DevOps tools and technologies. Prodvana's key features include: Intent-based deployments: Prodvana uses intent-based deployment technology to automate the deployment process. This means that businesses can simply specify their deployment goals, and Prodvana will automatically generate and execute the necessary steps to achieve those goals. This can save businesses a significant amount of time and effort. Guardrails for deployments: Prodvana provides a variety of guardrails to help businesses ensure the security and reliability of their deployments. These guardrails include approvals, database validations, automatic deployment validation, and simple interfaces to add custom guardrails. This helps businesses to prevent errors and reduce the risk of outages. Frictionless DevEx: Prodvana provides a frictionless developer experience by tracking commits through the infrastructure, ensuring complete visibility beyond just Docker images. This helps developers to quickly identify and resolve issues, and it also makes it easier to collaborate with other team members. Intelligence with Clairvoyance: Prodvana's Clairvoyance feature provides businesses with insights into the impact of their deployments before they are executed. This helps businesses to make more informed decisions about their deployments and to avoid potential problems. Easy integrations: Prodvana integrates seamlessly with a variety of DevOps tools and technologies. This makes it easy for businesses to use Prodvana with their existing workflows and processes.
TripleWhale
TripleWhale is a website that provides security services to protect itself from online attacks. It uses Cloudflare to block unauthorized access and ensure the safety of the website. Users may encounter blocks due to various triggers such as submitting specific words or phrases, SQL commands, or malformed data. In such cases, users can contact the site owner to resolve the issue by providing details of the blocked action and the Cloudflare Ray ID.

MLSecOps
MLSecOps is an AI tool designed to drive the field of MLSecOps forward through high-quality educational resources and tools. It focuses on traditional cybersecurity principles, emphasizing people, processes, and technology. The MLSecOps Community educates and promotes the integration of security practices throughout the AI & machine learning lifecycle, empowering members to identify, understand, and manage risks associated with their AI systems.
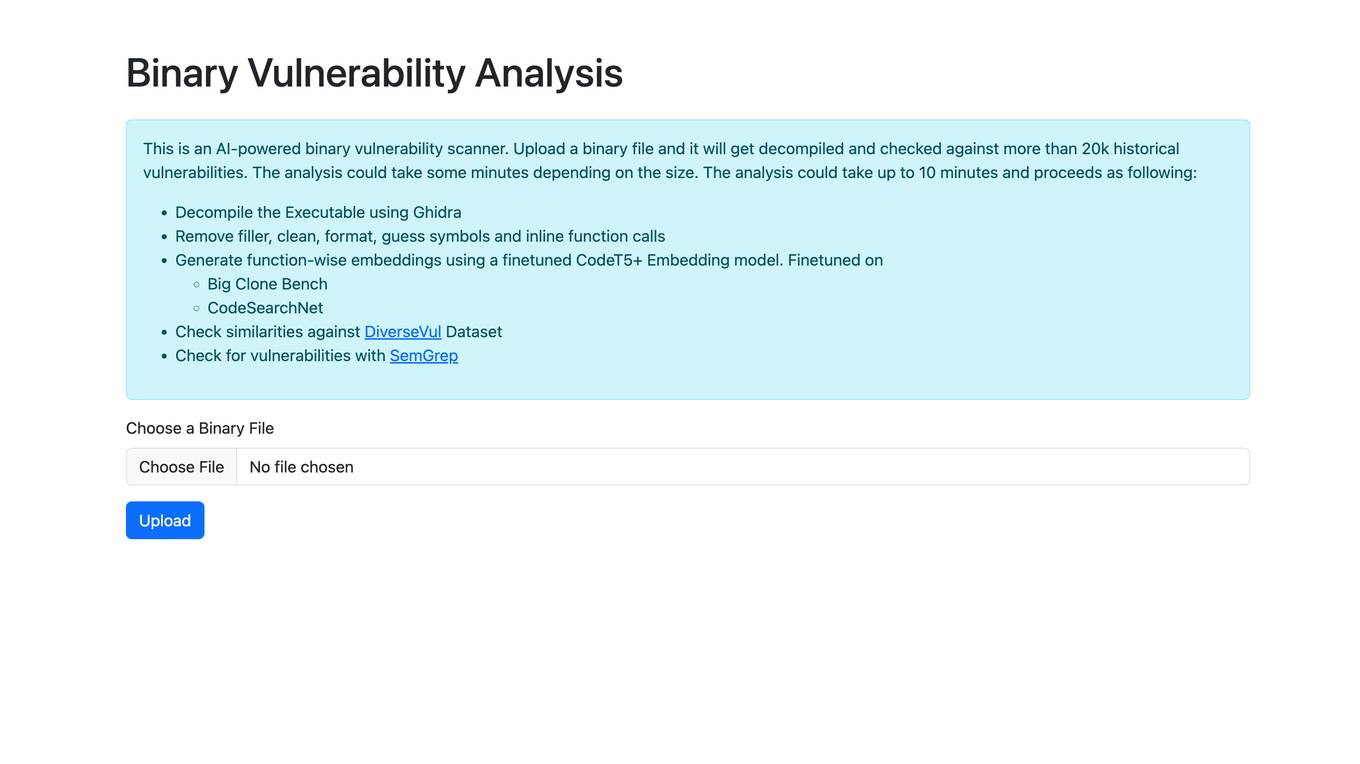
Binary Vulnerability Analysis
The website offers an AI-powered binary vulnerability scanner that allows users to upload a binary file for analysis. The tool decompiles the executable, removes filler, cleans, formats, and checks for historical vulnerabilities. It generates function-wise embeddings using a finetuned CodeT5+ Embedding model and checks for similarities against the DiverseVul Dataset. The tool also checks for vulnerabilities using SemGrep. The analysis process may take up to 10 minutes depending on the file size.
DryRun Security
DryRun Security is a contextual security analysis tool designed to help organizations uncover risks in their codebase that traditional pattern-matching tools may miss. By providing real-time feedback, clear guidance, and customizable code policies, DryRun Security empowers security leaders, AppSec engineers, and developers to enhance code security, streamline compliance, and increase developer engagement. The tool supports various languages and frameworks, offers natural language code policies, and integrates with GitHub and Slack for notifications and reporting.
Concentric AI
Concentric AI is a Managed Data Security Posture Management tool that utilizes Semantic Intelligence to provide comprehensive data security solutions. The platform offers features such as autonomous data discovery, data risk identification, centralized remediation, easy deployment, and data security posture management. Concentric AI helps organizations protect sensitive data, prevent data loss, and ensure compliance with data security regulations. The tool is designed to simplify data governance and enhance data security across various data repositories, both in the cloud and on-premises.
Link Shield
Link Shield is an AI-powered malicious URL detection API platform that helps protect online security. It utilizes advanced machine learning algorithms to analyze URLs and identify suspicious activity, safeguarding users from phishing scams, malware, and other harmful threats. The API is designed for ease of integration, affordability, and flexibility, making it accessible to developers of all levels. Link Shield empowers businesses to ensure the safety and security of their applications and online communities.
Immunifai
Immunifai is a cybersecurity company that provides AI-powered threat detection and response solutions. The company's mission is to make the world a safer place by protecting organizations from cyberattacks. Immunifai's platform uses machine learning and artificial intelligence to identify and respond to threats in real time. The company's solutions are used by a variety of organizations, including Fortune 500 companies, government agencies, and financial institutions.
KBY-AI Identity Verification SDK
KBY-AI is an advanced Identity Verification SDK provider offering powerful solutions for Face Recognition, Face Liveness Detection, and ID Card Recognition. Their cutting-edge AI technology ensures foolproof protection without disrupting the user's flow. The SDKs are designed to be lightweight, highly effective, and ideal for commercial applications like KYC automation, time and attendance systems, and video surveillance. KBY-AI's solutions support various ID documents from 200+ countries and are compatible with Android, iOS, and web platforms.
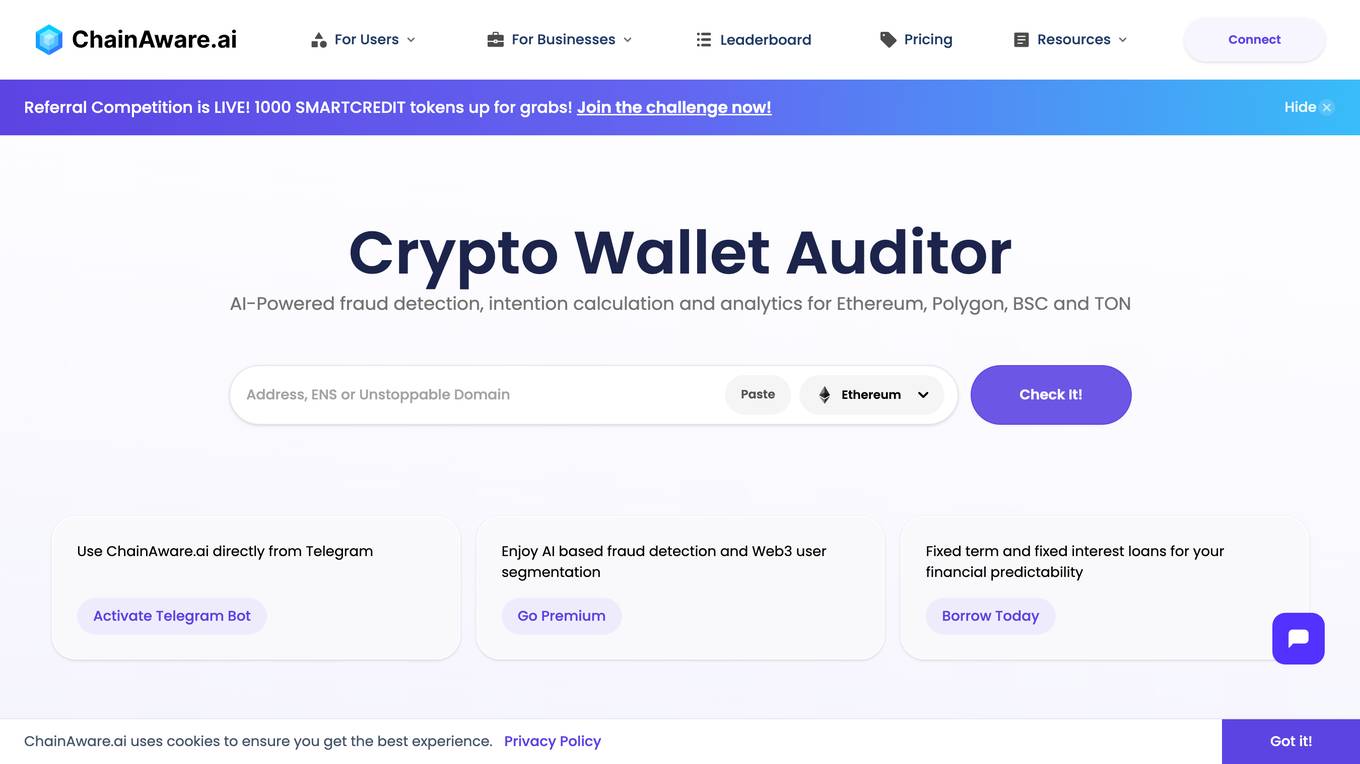
ChainAware.ai
ChainAware.ai is an AI-powered blockchain super tool designed for both users and businesses. It offers a range of features such as Wallet Auditor, Fraud Detector, and Rug Pull Detector to enhance security and trust in blockchain transactions. The tool provides predictive AI capabilities to prevent fraud and identify potential risks before they occur. Additionally, it offers business solutions including account-based user acquisition, web3 user analytics, and crypto fraud detection with AI. ChainAware.ai aims to revolutionize the way users interact with blockchain technology by providing advanced tools and services powered by artificial intelligence.

Smaty.xyz
Smaty.xyz is a comprehensive platform that provides a suite of tools for code generation and security auditing. With Smaty.xyz, developers can quickly and easily generate high-quality code in multiple programming languages, ensuring consistency and reducing development time. Additionally, Smaty.xyz offers robust security auditing capabilities, enabling developers to identify and address vulnerabilities in their code, mitigating risks and enhancing the overall security of their applications.
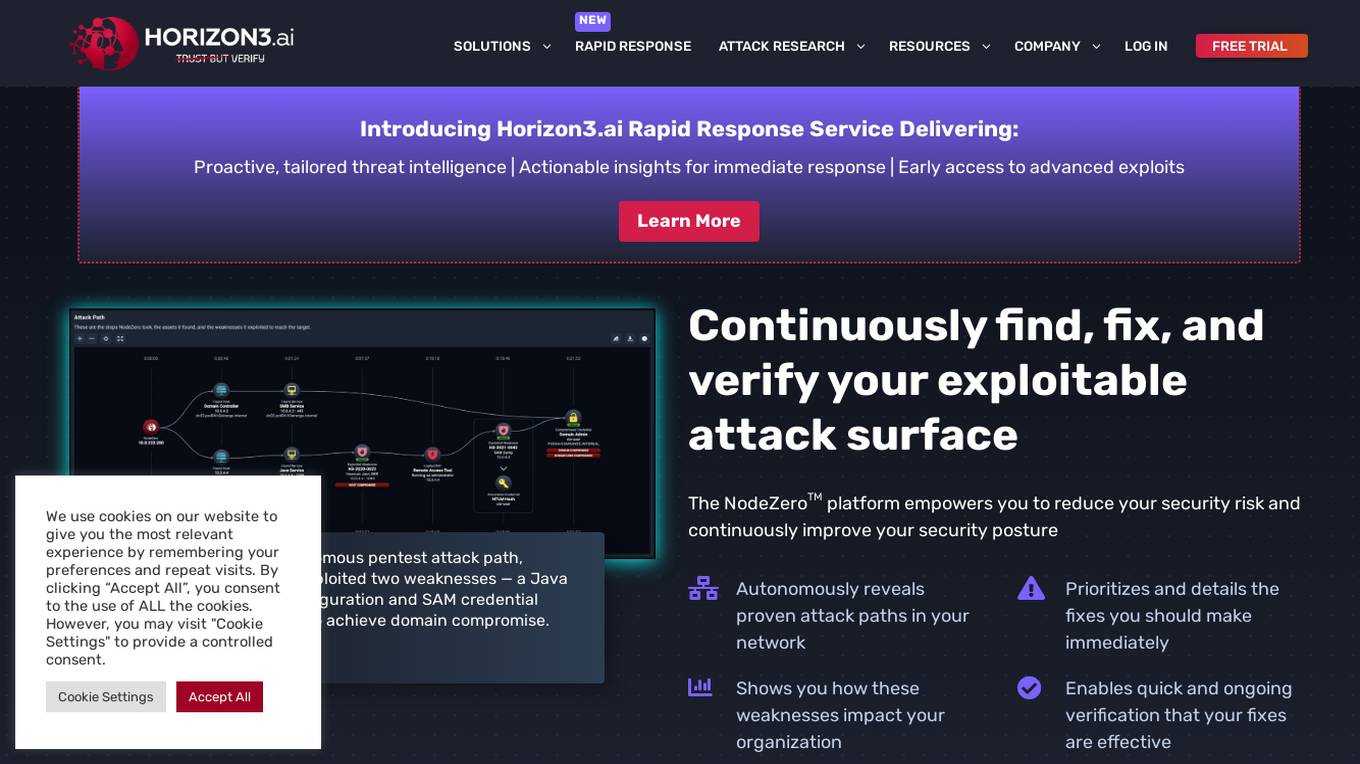
NodeZero™ Platform
Horizon3.ai Solutions offers the NodeZero™ Platform, an AI-powered autonomous penetration testing tool designed to enhance cybersecurity measures. The platform combines expert human analysis by Offensive Security Certified Professionals with automated testing capabilities to streamline compliance processes and proactively identify vulnerabilities. NodeZero empowers organizations to continuously assess their security posture, prioritize fixes, and verify the effectiveness of remediation efforts. With features like internal and external pentesting, rapid response capabilities, AD password audits, phishing impact testing, and attack research, NodeZero is a comprehensive solution for large organizations, ITOps, SecOps, security teams, pentesters, and MSSPs. The platform provides real-time reporting, integrates with existing security tools, reduces operational costs, and helps organizations make data-driven security decisions.
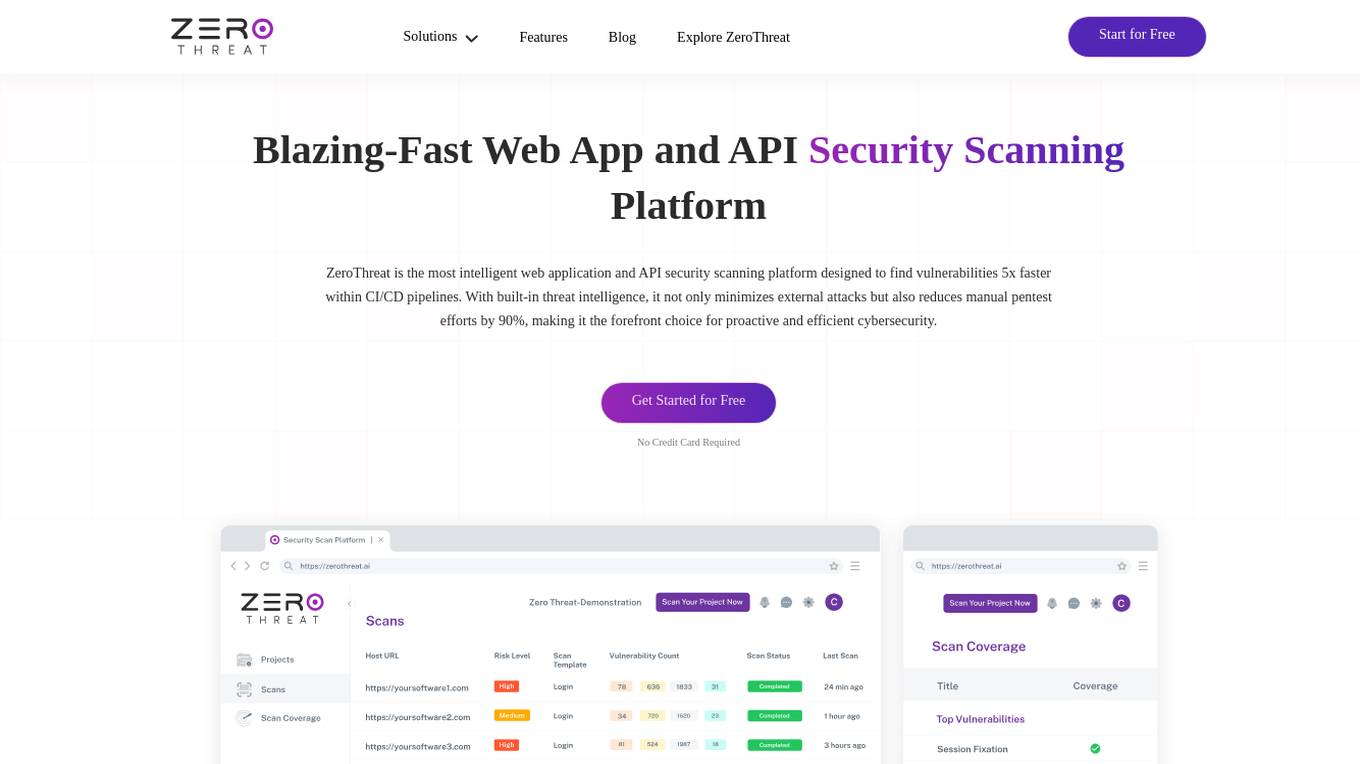
ZeroThreat
ZeroThreat is a web app and API security scanner that helps businesses identify and fix vulnerabilities in their web applications and APIs. It uses a combination of static and dynamic analysis techniques to scan for a wide range of vulnerabilities, including OWASP Top 10, CWE Top 25, and SANS Top 25. ZeroThreat also provides continuous monitoring and alerting, so businesses can stay on top of new vulnerabilities as they emerge.
20 - Open Source AI Tools
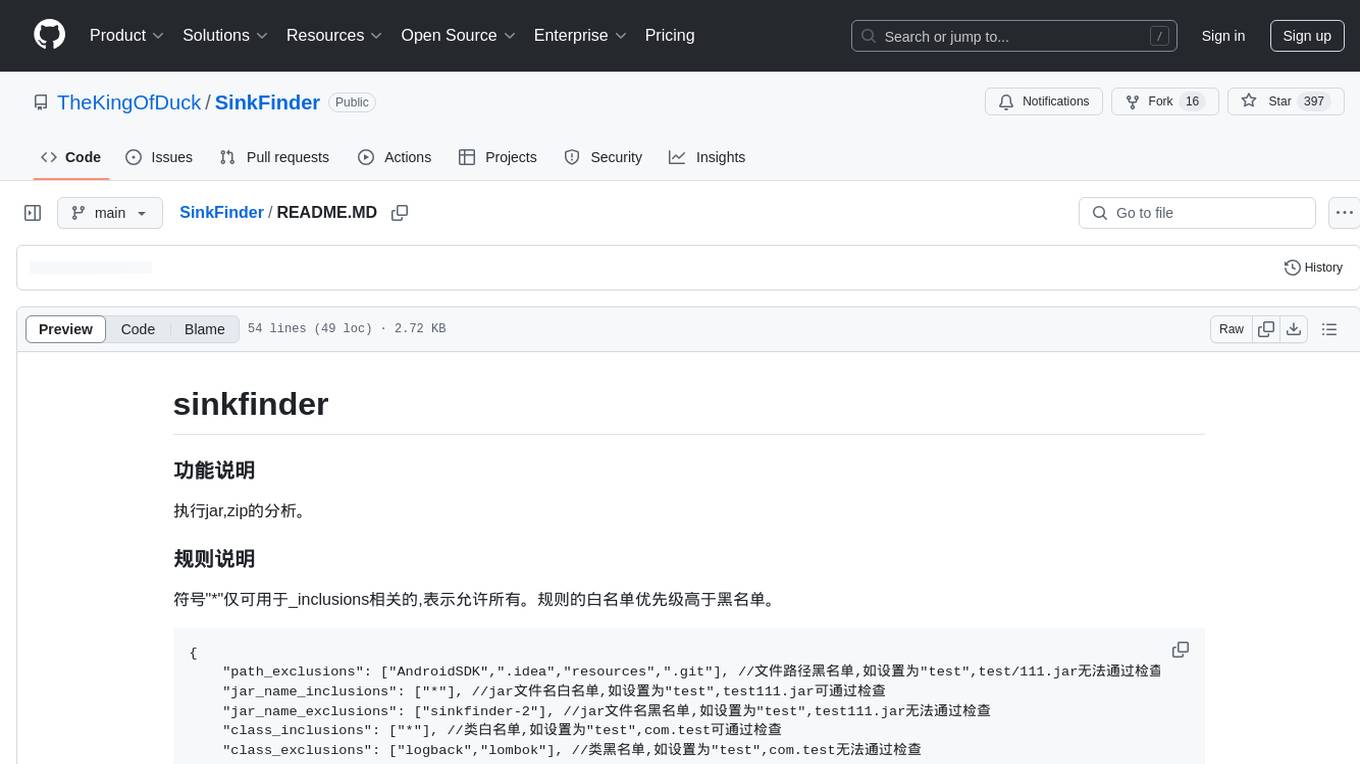
SinkFinder
SinkFinder is a tool designed to analyze jar and zip files for security vulnerabilities. It allows users to define rules for white and blacklisting specific classes and methods that may pose a risk. The tool provides a list of common security sink names along with severity levels and associated vulnerable methods. Users can use SinkFinder to quickly identify potential security issues in their Java applications by scanning for known sink patterns and configurations.
invariant
Invariant Analyzer is an open-source scanner designed for LLM-based AI agents to find bugs, vulnerabilities, and security threats. It scans agent execution traces to identify issues like looping behavior, data leaks, prompt injections, and unsafe code execution. The tool offers a library of built-in checkers, an expressive policy language, data flow analysis, real-time monitoring, and extensible architecture for custom checkers. It helps developers debug AI agents, scan for security violations, and prevent security issues and data breaches during runtime. The analyzer leverages deep contextual understanding and a purpose-built rule matching engine for security policy enforcement.
fairlearn
Fairlearn is a Python package designed to help developers assess and mitigate fairness issues in artificial intelligence (AI) systems. It provides mitigation algorithms and metrics for model assessment. Fairlearn focuses on two types of harms: allocation harms and quality-of-service harms. The package follows the group fairness approach, aiming to identify groups at risk of experiencing harms and ensuring comparable behavior across these groups. Fairlearn consists of metrics for assessing model impacts and algorithms for mitigating unfairness in various AI tasks under different fairness definitions.
AwesomeLLM4APR
Awesome LLM for APR is a repository dedicated to exploring the capabilities of Large Language Models (LLMs) in Automated Program Repair (APR). It provides a comprehensive collection of research papers, tools, and resources related to using LLMs for various scenarios such as repairing semantic bugs, security vulnerabilities, syntax errors, programming problems, static warnings, self-debugging, type errors, web UI tests, smart contracts, hardware bugs, performance bugs, API misuses, crash bugs, test case repairs, formal proofs, GitHub issues, code reviews, motion planners, human studies, and patch correctness assessments. The repository serves as a valuable reference for researchers and practitioners interested in leveraging LLMs for automated program repair.

Awesome-LLM4Cybersecurity
The repository 'Awesome-LLM4Cybersecurity' provides a comprehensive overview of the applications of Large Language Models (LLMs) in cybersecurity. It includes a systematic literature review covering topics such as constructing cybersecurity-oriented domain LLMs, potential applications of LLMs in cybersecurity, and research directions in the field. The repository analyzes various benchmarks, datasets, and applications of LLMs in cybersecurity tasks like threat intelligence, fuzzing, vulnerabilities detection, insecure code generation, program repair, anomaly detection, and LLM-assisted attacks.
awesome-ai-devtools
Awesome AI-Powered Developer Tools is a curated list of AI-powered developer tools that leverage AI to assist developers in tasks such as code completion, refactoring, debugging, documentation, and more. The repository includes a wide range of tools, from IDEs and Git clients to assistants, agents, app generators, UI generators, snippet generators, documentation tools, code generation tools, agent platforms, OpenAI plugins, search tools, and testing tools. These tools are designed to enhance developer productivity and streamline various development tasks by integrating AI capabilities.
LLM-FuzzX
LLM-FuzzX is an open-source user-friendly fuzz testing tool for large language models (e.g., GPT, Claude, LLaMA), equipped with advanced task-aware mutation strategies, fine-grained evaluation, and jailbreak detection capabilities. It helps researchers and developers quickly discover potential security vulnerabilities and enhance model robustness. The tool features a user-friendly web interface for visual configuration and real-time monitoring, supports various advanced mutation methods, integrates RoBERTa model for real-time jailbreak detection and evaluation, supports multiple language models like GPT, Claude, LLaMA, provides visualization analysis with seed flowcharts and experiment data statistics, and offers detailed logging support for main, mutation, and jailbreak logs.
llms-interview-questions
This repository contains a comprehensive collection of 63 must-know Large Language Models (LLMs) interview questions. It covers topics such as the architecture of LLMs, transformer models, attention mechanisms, training processes, encoder-decoder frameworks, differences between LLMs and traditional statistical language models, handling context and long-term dependencies, transformers for parallelization, applications of LLMs, sentiment analysis, language translation, conversation AI, chatbots, and more. The readme provides detailed explanations, code examples, and insights into utilizing LLMs for various tasks.

MAVIS
MAVIS (Math Visual Intelligent System) is an AI-driven application that allows users to analyze visual data such as images and generate interactive answers based on them. It can perform complex mathematical calculations, solve programming tasks, and create professional graphics. MAVIS supports Python for coding and frameworks like Matplotlib, Plotly, Seaborn, Altair, NumPy, Math, SymPy, and Pandas. It is designed to make projects more efficient and professional.
www-project-ai-security-and-privacy-guide
The OWASP AI Exchange and OWASP AI security and privacy guide are initiatives to collect and present the state of the art on AI threats, controls, security, and privacy through community collaboration. The AI Exchange is a living set of documents that collect AI threats and controls from collaboration between experts worldwide. The AI Security and Privacy Guide project has a security part that links directly to the AI Exchange, and a privacy part.
radicalbit-ai-monitoring
The Radicalbit AI Monitoring Platform provides a comprehensive solution for monitoring Machine Learning and Large Language models in production. It helps proactively identify and address potential performance issues by analyzing data quality, model quality, and model drift. The repository contains files and projects for running the platform, including UI, API, SDK, and Spark components. Installation using Docker compose is provided, allowing deployment with a K3s cluster and interaction with a k9s container. The platform documentation includes a step-by-step guide for installation and creating dashboards. Community engagement is encouraged through a Discord server. The roadmap includes adding functionalities for batch and real-time workloads, covering various model types and tasks.
bugbug
Bugbug is a tool developed by Mozilla that leverages machine learning techniques to assist with bug and quality management, as well as other software engineering tasks like test selection and defect prediction. It provides various classifiers to suggest assignees, detect patches likely to be backed-out, classify bugs, assign product/components, distinguish between bugs and feature requests, detect bugs needing documentation, identify invalid issues, verify bugs needing QA, detect regressions, select relevant tests, track bugs, and more. Bugbug can be trained and tested using Python scripts, and it offers the ability to run model training tasks on Taskcluster. The project structure includes modules for data mining, bug/commit feature extraction, model implementations, NLP utilities, label handling, bug history playback, and GitHub issue retrieval.
moonpalace
MoonPalace is a debugging tool for API provided by Moonshot AI. It supports all platforms (Mac, Windows, Linux) and is simple to use by replacing 'base_url' with 'http://localhost:9988'. It captures complete requests, including 'accident scenes' during network errors, and allows quick retrieval and viewing of request information using 'request_id' and 'chatcmpl_id'. It also enables one-click export of BadCase structured reporting data to help improve Kimi model capabilities. MoonPalace is recommended for use as an API 'supplier' during code writing and debugging stages to quickly identify and locate various issues related to API calls and code writing processes, and to export request details for submission to Moonshot AI to improve Kimi model.

last_layer
last_layer is a security library designed to protect LLM applications from prompt injection attacks, jailbreaks, and exploits. It acts as a robust filtering layer to scrutinize prompts before they are processed by LLMs, ensuring that only safe and appropriate content is allowed through. The tool offers ultra-fast scanning with low latency, privacy-focused operation without tracking or network calls, compatibility with serverless platforms, advanced threat detection mechanisms, and regular updates to adapt to evolving security challenges. It significantly reduces the risk of prompt-based attacks and exploits but cannot guarantee complete protection against all possible threats.

air-script
Air Script is a versatile tool designed for Wi-Fi penetration testing, offering automated and user-friendly features to streamline the hacking process. It allows users to easily capture handshakes from nearby networks, automate attacks, and even send email notifications upon completion. The tool is ideal for individuals looking to efficiently pwn Wi-Fi networks without extensive manual input. With additional tools and options available, Air Script caters to a wide range of users, including script kiddies, hackers, pentesters, and security researchers. Whether on the go or using a Raspberry Pi, Air Script provides a convenient solution for network penetration testing and password cracking.

watchtower
AIShield Watchtower is a tool designed to fortify the security of AI/ML models and Jupyter notebooks by automating model and notebook discoveries, conducting vulnerability scans, and categorizing risks into 'low,' 'medium,' 'high,' and 'critical' levels. It supports scanning of public GitHub repositories, Hugging Face repositories, AWS S3 buckets, and local systems. The tool generates comprehensive reports, offers a user-friendly interface, and aligns with industry standards like OWASP, MITRE, and CWE. It aims to address the security blind spots surrounding Jupyter notebooks and AI models, providing organizations with a tailored approach to enhancing their security efforts.

patchwork
PatchWork is an open-source framework designed for automating development tasks using large language models. It enables users to automate workflows such as PR reviews, bug fixing, security patching, and more through a self-hosted CLI agent and preferred LLMs. The framework consists of reusable atomic actions called Steps, customizable LLM prompts known as Prompt Templates, and LLM-assisted automations called Patchflows. Users can run Patchflows locally in their CLI/IDE or as part of CI/CD pipelines. PatchWork offers predefined patchflows like AutoFix, PRReview, GenerateREADME, DependencyUpgrade, and ResolveIssue, with the flexibility to create custom patchflows. Prompt templates are used to pass queries to LLMs and can be customized. Contributions to new patchflows, steps, and the core framework are encouraged, with chat assistants available to aid in the process. The roadmap includes expanding the patchflow library, introducing a debugger and validation module, supporting large-scale code embeddings, parallelization, fine-tuned models, and an open-source GUI. PatchWork is licensed under AGPL-3.0 terms, while custom patchflows and steps can be shared using the Apache-2.0 licensed patchwork template repository.
aiogram-django-template
Aiogram & Django API Template is a robust and secure Django template with advanced features like Docker integration, Celery for asynchronous tasks, Sentry for error tracking, Django Rest Framework for building APIs, and more. It provides scalability options, up-to-date dependencies, and integration with AWS S3 for storage. The template includes configuration guides for secrets, ports, performance tuning, application settings, CORS and CSRF settings, and database configuration. Security, scalability, and monitoring are emphasized for efficient Django API development.
ai_automation_suggester
An integration for Home Assistant that leverages AI models to understand your unique home environment and propose intelligent automations. By analyzing your entities, devices, areas, and existing automations, the AI Automation Suggester helps you discover new, context-aware use cases you might not have considered, ultimately streamlining your home management and improving efficiency, comfort, and convenience. The tool acts as a personal automation consultant, providing actionable YAML-based automations that can save energy, improve security, enhance comfort, and reduce manual intervention. It turns the complexity of a large Home Assistant environment into actionable insights and tangible benefits.
eulers-shield
Euler's Shield is a decentralized, AI-powered financial system designed to stabilize the value of Pi Coin at $314.159. It combines blockchain, machine learning, and cybersecurity to ensure the security, scalability, and decentralization of the Pi Coin ecosystem.
20 - OpenAI Gpts
Java Security Expert
Java Security Expert offering advice on best practices and resolving security issues.
Security Testing Advisor
Ensures software security through comprehensive testing techniques.
Securia
AI-powered audit ally. Enhance cybersecurity effortlessly with intelligent, automated security analysis. Safe, swift, and smart.
HackMeIfYouCan
Hack Me if you can - I can only talk to you about computer security, software security and LLM security @JacquesGariepy
SSLLMs Advisor
Helps you build logic security into your GPTs custom instructions. Documentation: https://github.com/infotrix/SSLLMs---Semantic-Secuirty-for-LLM-GPTs
CyberNews GPT
CyberNews GPT is an assistant that provides the latest security news about cyber threats, hackings and breaches, malware, zero-day vulnerabilities, phishing, scams and so on.
🛡️ CodeGuardian Pro+ 🛡️
Your AI-powered sentinel for code! Scans for vulnerabilities, offers security tips, and educates on best practices in cybersecurity. 🔍🔐
RobotGPT
Expert in ethical hacking, leveraging https://pentestbook.six2dez.com/ and https://book.hacktricks.xyz resources for CTFs and challenges.
Bug Insider
Analyzes bug bounty writeups and cybersecurity reports, providing structured insights and tips.