
aiven-client
aiven-client (avn) is the official command-line client for Aiven
Stars: 86
Aiven Client is the official command-line client for Aiven, a next-generation managed cloud services platform. It focuses on ease of adoption, high fault resilience, customer's peace of mind, and advanced features at competitive price points. The client allows users to interact with Aiven services through a command-line interface, providing functionalities such as authentication, project management, service exploration, service launching, service integrations, custom files management, team management, OAuth2 client configuration, autocomplete support, and auth helpers for connecting to services. Users can perform various tasks related to managing cloud services efficiently using the Aiven Client.
README:
Aiven Client |BuildStatus|_ ###########################
.. |BuildStatus| image:: https://github.com/aiven/aiven-client/workflows/Build%20Aiven%20Client/badge.svg?branch=main .. _BuildStatus: https://github.com/aiven/aiven-client/actions
Aiven is a next-generation managed cloud services platform. Its focus is in ease of adoption, high fault resilience, customer's peace of mind and advanced features at competitive price points. See https://aiven.io/ for more information about the backend service.
aiven-client (avn) is the official command-line client for Aiven.
.. contents::
.. _platform-requirements:
Requirements:
-
Python 3.8 or later
-
Requests_
-
For Windows and OSX, certifi_ is also needed
.. _Requests: http://www.python-requests.org/
.. _certifi: https://github.com/certifi/python-certifi
.. _installation:
Pypi installation is the recommended route for most users::
$ python3 -m pip install aiven-client
It is also possible to build an RPM::
$ make rpm
To check that the tool is installed and working, run it without arguments::
$ avn
If you see usage output, you're all set.
Note: On Windows you may need to use python3 -m aiven.client instead of avn.
The simplest way to use Aiven CLI is to authenticate with the username and password you use on Aiven::
$ avn user login [email protected]
The command will prompt you for your password.
You can also use an access token generated in the Aiven Console::
$ avn user login [email protected] --token
You will be prompted for your access token as above.
If you are registered on Aiven through the AWS or GCP marketplace, then you need to specify an additional argument --tenant. Currently the supported value are aws and gcp, for example::
$ avn user login [email protected] --tenant aws
.. _help-command: .. _basic-usage:
Some handy hints that work with all commands:
-
The
avn helpcommand shows all commands and can search for a command, so for exampleavn help kafka topicshows commands with kafka and topic in their description. -
Passing
-hor--helpgives help output for any command. Examples:avn --helporavn service --help. -
All commands will output the raw REST API JSON response with
--json, we use this extensively ourselves in conjunction withjq <https://stedolan.github.io/jq/>__.
.. _login-and-users:
Login::
$ avn user login [email protected]
Logout (revokes current access token, other sessions remain valid)::
$ avn user logout
Expire all authentication tokens for your user, logs out all web console sessions, etc. You will need to login again after this::
$ avn user tokens-expire
Manage individual access tokens::
$ avn user access-token list $ avn user access-token create --description <usage_description> [--max-age-seconds ] [--extend-when-used] $ avn user access-token update <token|token_prefix> --description <new_description> $ avn user access-token revoke <token|token_prefix>
Note that the system has hard limits for the number of tokens you can create. If you're
permanently done using a token you should always use user access-token revoke operation
to revoke the token so that it does not count towards the quota.
Alternatively, you can add 2 JSON files, first create a default config in ~/.config/aiven/aiven-credentials.json containing the JSON with an auth_token::
{ "auth_token": "ABC1+123...TOKEN==", "user_email": "[email protected]" }
Second create a default config in ~/.config/aiven/aiven-client.json containing the json with the default_project::
{"default_project": "yourproject-abcd"}
.. _clouds:
List available cloud regions::
$ avn cloud list
.. _projects:
List projects you are a member of::
$ avn project list
Project commands operate on the currently active project or the project
specified with the --project NAME switch. The active project cab be changed
with the project switch command::
$ avn project switch
Show active project's details::
$ avn project details
Create a project and set the default cloud region for it::
$ avn project create myproject --cloud aws-us-east-1
Delete an empty project::
$ avn project delete myproject
List authorized users in a project::
$ avn project user-list
Invite an existing Aiven user to a project::
$ avn project user-invite [email protected]
Remove a user from the project::
$ avn project user-remove [email protected]
View project management event log::
$ avn events
.. _services:
List services (of the active project)::
$ avn service list
List services in a specific project::
$ avn service list --project proj2
List only a specific service::
$ avn service list db1
Verbose list (includes connection information, etc.)::
$ avn service list db1 -v
Full service information in JSON, as it is returned by the Aiven REST API::
$ avn service list db1 --json
Only a specific field in the output, custom formatting::
$ avn service list db1 --format "The service is at {service_uri}"
View service log entries (most recent entries and keep on following logs, other options can be used to get history)::
$ avn service logs db1 -f
.. _launching-services:
View available service plans::
$ avn service plans
Launch a PostgreSQL service::
$ avn service create mydb -t pg --plan hobbyist
View service type specific options, including examples on how to set them::
$ avn service types -v
Launch a PostgreSQL service of a specific version (see above command)::
$ avn service create mydb96 -t pg --plan hobbyist -c pg_version=9.6
Update a service's list of allowed client IP addresses. Note that a list of multiple values is provided as a comma separated list::
$ avn service update mydb96 -c ip_filter=10.0.1.0/24,10.0.2.0/24,1.2.3.4/32
Open psql client and connect to the PostgreSQL service (also available for InfluxDB)::
$ avn service cli mydb96
Update a service to a different plan AND move it to another cloud region::
$ avn service update mydb --plan startup-4 --cloud aws-us-east-1
Power off a service::
$ avn service update mydb --power-off
Power on a service::
$ avn service update mydb --power-on
Terminate a service (all data will be gone!)::
$ avn service terminate mydb
Some service types support multiple users (e.g. PostgreSQL database users).
List, add and delete service users::
$ avn service user-list $ avn service user-create $ avn service user-delete
For Valkey services it's possible to create users with ACLs_::
$ avn service user-create --username new_user --valkey-acl-keys="prefix* another_key" --valkey-acl-commands="+set" --valkey-acl-categories="-@all +@admin" --valkey-acl-channels="prefix* some_chan" my-valkey-service
.. _ACLs: https://valkey.io/docs/topics/acl
Service users are created with strong random passwords.
Service integrations <https://aiven.io/service-integrations>_ allow to link Aiven services to other Aiven services or to services
offered by other companies for example for logging. Some examples for various diffenent integrations:
Google cloud logging, AWS Cloudwatch logging, Remote syslog integration_ and Getting started with Datadog_.
.. _Google cloud logging: https://help.aiven.io/en/articles/4209837-sending-service-logs-to-google-cloud-logging
.. _AWS Cloudwatch logging: https://help.aiven.io/en/articles/4134821-sending-service-logs-to-aws-cloudwatch
.. _Remote syslog integration: https://help.aiven.io/en/articles/2933115-remote-syslog-integration
.. _Getting started with Datadog: https://help.aiven.io/en/articles/1759208-getting-started-with-datadog
List service integration endpoints::
$ avn service integration-endpoint-list
List all available integration endpoint types for given project::
$ avn service integration-endpoint-types-list --project <project>
Create a service integration endpoint::
$ avn service integration-endpoint-create --project <project> --endpoint-type <endpoint type> --endpoint-name <endpoint name> --user-config-json <user configuration as json>
$ avn service integration-endpoint-create --project <project> --endpoint-type <endpoint type> --endpoint-name <endpoint name> -c <KEY=VALUE type user configuration>
Update a service integration endpoint::
$ avn service integration-endpoint-update --project <project> --user-config-json <user configuration as json> <endpoint id>
$ avn service integration-endpoint-update --project <project> -c <KEY=VALUE type user configuration> <endpoint id>
Delete a service integration endpoint::
$ avn service integration-endpoint-delete --project <project> <endpoint_id>
List service integrations::
$ avn service integration-list <service name>
List all available integration types for given project::
$ avn service integration-types-list --project <project>
Create a service integration::
$ avn service integration-create --project <project> -t <integration type> -s <source service> -d <dest service> -S <source endpoint id> -D <destination endpoint id> --user-config-json <user configuration as json>
$ avn service integration-create --project <project> -t <integration type> -s <source service> -d <dest service> -S <source endpoint id> -D <destination endpoint id> -c <KEY=VALUE type user configuration>
Update a service integration::
$ avn service integration-update --project <project> --user-config-json <user configuration as json> <integration_id>
$ avn service integration-update --project <project> -c <KEY=VALUE type user configuration> <integration_id>
Delete a service integration::
$ avn service integration-delete --project <project> <integration_id>
Listing files::
$ avn service custom-file list --project <project> <service_name>
Reading file::
$ avn service custom-file get --project <project> --file_id <file_id> [--target_filepath <file_path>] [--stdout_write] <service_name>
Uploading new files::
$ avn service custom-file upload --project <project> --file_type <file_type> --file_path <file_path> --file_name <file_name> <service_name>
Updating existing files::
$ avn service custom-file update --project <project> --file_path <file_path> --file_id <file_id> <service_name>
.. _teams:
List account teams::
$ avn account team list <account_id>
Create a team::
$ avn account team create --team-name <team_name> <account_id>
Delete a team::
$ avn account team delete --team-id <team_id> <account_id>
Attach team to a project::
$ avn account team project-attach --team-id <team_id> --project <project_name> <account_id> --team-type <admin|developer|operator|read_only>
Detach team from project::
$ avn account team project-detach --team-id <team_id> --project <project_name> <account_id>
List projects associated to the team::
$ avn account team project-list --team-id <team_id> <account_id>
List members of the team::
$ avn account team user-list --team-id <team_id> <account_id>
Invite a new member to the team::
$ avn account team user-invite --team-id <team_id> <account_id> [email protected]
See the list of pending invitations::
$ avn account team user-list-pending --team-id <team_id> <account_id>
Remove user from the team::
$ avn account team user-delete --team-id <team_id> --user-id <user_id> <account_id>
.. _oauth2-clients:
List configured OAuth2 clients::
$ avn account oauth2-client list <account_id>
Get a configured OAuth2 client's configuration::
$ avn account oauth2-client list <account_id> --oauth2-client-id <client_id>
Create a new OAuth2 client information::
$ avn account oauth2-client create <account_id> --name <app_name> -d <app_description> --redirect-uri <redirect_uri>
Delete an OAuth2 client::
$ avn account oauth2-client delete <account_id> --oauth2-client-id <client_id>
List an OAuth2 client's redirect URIs::
$ avn account oauth2-client redirect-list <account_id> --oauth2-client-id <client_id>
Create a new OAuth2 client redirect URI::
$ avn account oauth2-client redirect-create <account_id> --oauth2-client-id <client_id> --redirect-uri <redirect_uri>
Delete an OAuth2 client redirect URI::
$ avn account oauth2-client redirect-delete <account_id> --oauth2-client-id <client_id> --redirect-uri-id <redirect_uri_id>
List an OAuth2 client's secrets::
$ avn account oauth2-client secret-list <account_id> --oauth2-client-id <client_id>
Create a new OAUth2 client secret::
$ avn account oauth2-client secret-create <account_id> --oauth2-client-id <client_id>
Delete an OAuth2 client's secret::
$ avn account oauth2-client secret-delete <account_id> --oauth2-client-id <client_id> --secret-id <secret_id>
.. _shell-completions:
avn supports shell completions. It requires an optional dependency: argcomplete. Install it::
$ python3 -m pip install argcomplete
To use completions in bash, add following line to ~/.bashrc::
eval "$(register-python-argcomplete avn)"
For more information (including completions usage in other shells) see https://kislyuk.github.io/argcomplete/.
When you spin up a new service, you'll want to connect to it. The --json option combined with the jq <https://stedolan.github.io/jq/>_ utility is a good way to grab the fields you need for your specific service. Try this to get the connection string::
$ avn service get --json | jq ".service_uri"
Each project has its own CA cert, and other services (notably Kafka) use mutualTLS so you will also need the service.key and service.cert files too for those. Download all three files to the local directory::
$ avn service user-creds-download --username avnadmin
For working with kcat <https://github.com/edenhill/kcat>_ (see also our help article <https://developer.aiven.io/docs/products/kafka/howto/kcat.html>_ ) or the command-line tools that ship with Kafka itself, a keystore and trustore are needed. By specifying which user's creds to use, and a secret, you can generate these via avn too::
$ avn service user-kafka-java-creds --username avnadmin -p t0pS3cr3t
Check the CONTRIBUTING <https://github.com/aiven/aiven-client/blob/main/.github/CONTRIBUTING.md>_ guide for details on how to contribute to this repository.
We maintain some other resources that you may also find useful:
-
Command Line Magic with avn <https://aiven.io/blog/command-line-magic-with-the-aiven-cli>__ -
Managing Billing Groups via CLI <https://help.aiven.io/en/articles/4720981-using-billing-groups-via-cli>__
For Tasks:
Click tags to check more tools for each tasksFor Jobs:
Alternative AI tools for aiven-client
Similar Open Source Tools

aiven-client
Aiven Client is the official command-line client for Aiven, a next-generation managed cloud services platform. It focuses on ease of adoption, high fault resilience, customer's peace of mind, and advanced features at competitive price points. The client allows users to interact with Aiven services through a command-line interface, providing functionalities such as authentication, project management, service exploration, service launching, service integrations, custom files management, team management, OAuth2 client configuration, autocomplete support, and auth helpers for connecting to services. Users can perform various tasks related to managing cloud services efficiently using the Aiven Client.
airbadge
Airbadge is a Stripe addon for Auth.js that provides an easy way to create a SaaS site without writing any authentication or payment code. It integrates Stripe Checkout into the signup flow, offers over 50 OAuth options for authentication, allows route and UI restriction based on subscription, enables self-service account management, handles all Stripe webhooks, supports trials and free plans, includes subscription and plan data in the session, and is open source with a BSL license. The project also provides components for conditional UI display based on subscription status and helper functions to restrict route access. Additionally, it offers a billing endpoint with various routes for billing operations. Setup involves installing @airbadge/sveltekit, setting up a database provider for Auth.js, adding environment variables, configuring authentication and billing options, and forwarding Stripe events to localhost.
well-architected-iac-analyzer
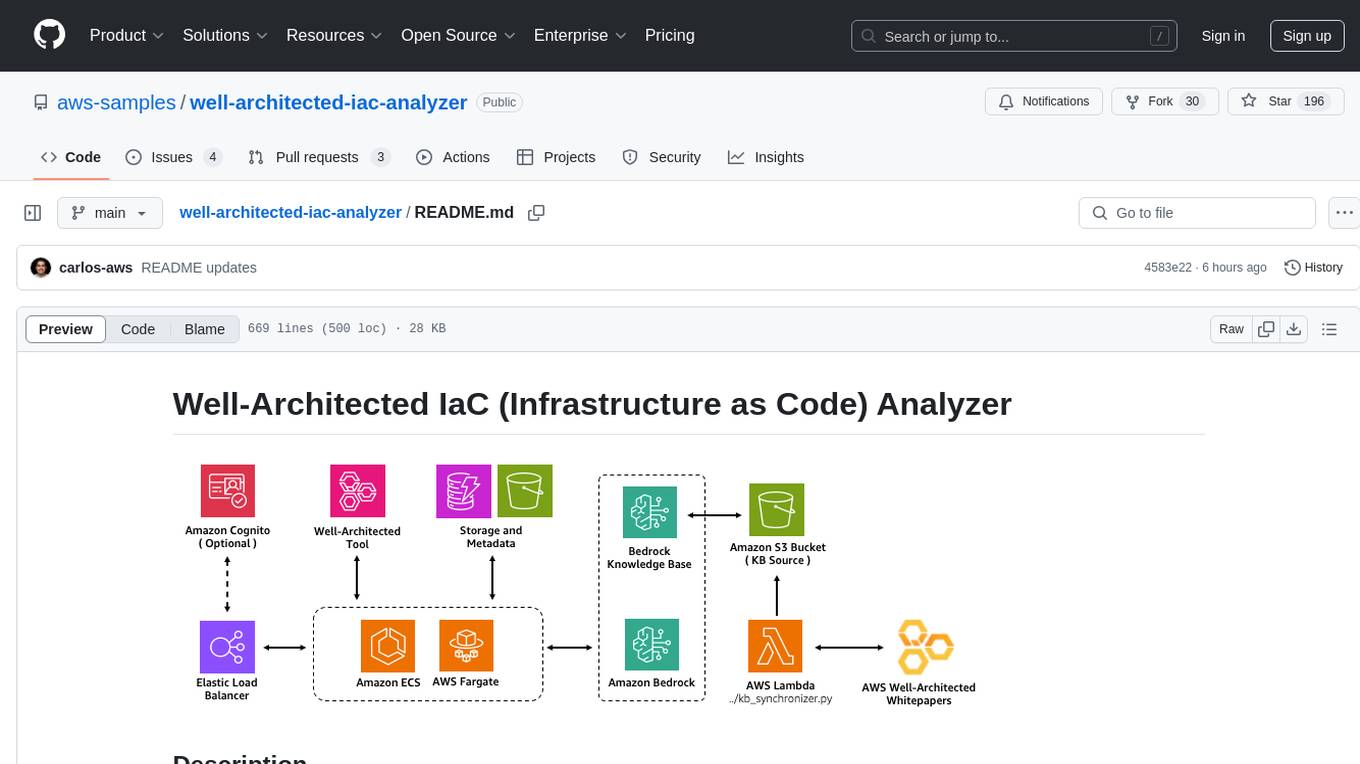
Well-Architected Infrastructure as Code (IaC) Analyzer is a project demonstrating how generative AI can evaluate infrastructure code for alignment with best practices. It features a modern web application allowing users to upload IaC documents, complete IaC projects, or architecture diagrams for assessment. The tool provides insights into infrastructure code alignment with AWS best practices, offers suggestions for improving cloud architecture designs, and can generate IaC templates from architecture diagrams. Users can analyze CloudFormation, Terraform, or AWS CDK templates, architecture diagrams in PNG or JPEG format, and complete IaC projects with supporting documents. Real-time analysis against Well-Architected best practices, integration with AWS Well-Architected Tool, and export of analysis results and recommendations are included.
aimeos-symfony
Aimeos Symfony bundle is a professional, full-featured, and ultra-fast e-commerce package for Symfony. It can be easily installed and customized within an existing Symfony application. The bundle provides comprehensive features for setting up an e-commerce platform, including authentication, routing configuration, database setup, and administration interface setup. It offers flexibility for adapting, extending, overwriting, and customizing various aspects to meet specific business needs. The bundle is designed to streamline the development process and provide a robust foundation for building e-commerce applications with Symfony.
verifywise
VerifyWise is an open-source AI governance platform designed to help businesses harness the power of AI safely and responsibly. The platform ensures compliance and robust AI management without compromising on security. It offers additional products like MaskWise for data redaction, EvalWise for AI model evaluation, and FlagWise for security threat monitoring. VerifyWise simplifies AI governance for organizations, aiding in risk management, regulatory compliance, and promoting responsible AI practices. It features options for on-premises or private cloud hosting, open-source with AGPLv3 license, AI-generated answers for compliance audits, source code transparency, Docker deployment, user registration, role-based access control, and various AI governance tools like risk management, bias & fairness checks, evidence center, AI trust center, and more.

director
Director is a context infrastructure tool for AI agents that simplifies managing MCP servers, prompts, and configurations by packaging them into portable workspaces accessible through a single endpoint. It allows users to define context workspaces once and share them across different AI clients, enabling seamless collaboration, instant context switching, and secure isolation of untrusted servers without cloud dependencies or API keys. Director offers features like workspaces, universal portability, local-first architecture, sandboxing, smart filtering, unified OAuth, observability, multiple interfaces, and compatibility with all MCP clients and servers.
chat-ui
This repository provides a minimalist approach to create a chatbot by constructing the entire front-end UI using a single HTML file. It supports various backend endpoints through custom configurations, multiple response formats, chat history download, and MCP. Users can deploy the chatbot locally, via Docker, Cloudflare pages, Huggingface, or within K8s. The tool also supports image inputs, toggling between different display formats, internationalization, and localization.
shortest
Shortest is a project for local development that helps set up environment variables and services for a web application. It provides a guide for setting up Node.js and pnpm dependencies, configuring services like Clerk, Vercel Postgres, Anthropic, Stripe, and GitHub OAuth, and running the application and tests locally.
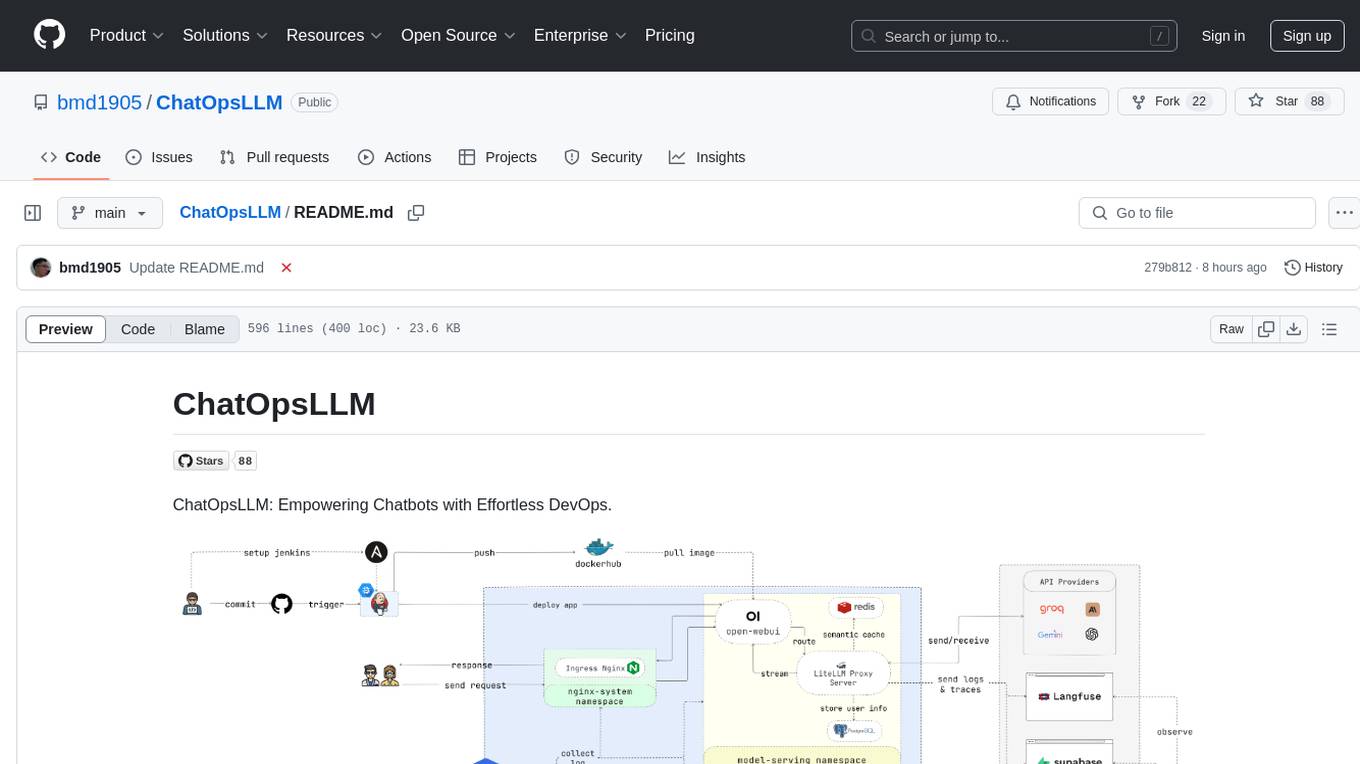
ChatOpsLLM
ChatOpsLLM is a project designed to empower chatbots with effortless DevOps capabilities. It provides an intuitive interface and streamlined workflows for managing and scaling language models. The project incorporates robust MLOps practices, including CI/CD pipelines with Jenkins and Ansible, monitoring with Prometheus and Grafana, and centralized logging with the ELK stack. Developers can find detailed documentation and instructions on the project's website.
backend.ai-webui
Backend.AI Web UI is a user-friendly web and app interface designed to make AI accessible for end-users, DevOps, and SysAdmins. It provides features for session management, inference service management, pipeline management, storage management, node management, statistics, configurations, license checking, plugins, help & manuals, kernel management, user management, keypair management, manager settings, proxy mode support, service information, and integration with the Backend.AI Web Server. The tool supports various devices, offers a built-in websocket proxy feature, and allows for versatile usage across different platforms. Users can easily manage resources, run environment-supported apps, access a web-based terminal, use Visual Studio Code editor, manage experiments, set up autoscaling, manage pipelines, handle storage, monitor nodes, view statistics, configure settings, and more.
stable-diffusion-webui
Stable Diffusion WebUI Docker Image allows users to run Automatic1111 WebUI in a docker container locally or in the cloud. The images do not bundle models or third-party configurations, requiring users to use a provisioning script for container configuration. It supports NVIDIA CUDA, AMD ROCm, and CPU platforms, with additional environment variables for customization and pre-configured templates for Vast.ai and Runpod.io. The service is password protected by default, with options for version pinning, startup flags, and service management using supervisorctl.
odoo-expert
RAG-Powered Odoo Documentation Assistant is a comprehensive documentation processing and chat system that converts Odoo's documentation to a searchable knowledge base with an AI-powered chat interface. It supports multiple Odoo versions (16.0, 17.0, 18.0) and provides semantic search capabilities powered by OpenAI embeddings. The tool automates the conversion of RST to Markdown, offers real-time semantic search, context-aware AI-powered chat responses, and multi-version support. It includes a Streamlit-based web UI, REST API for programmatic access, and a CLI for document processing and chat. The system operates through a pipeline of data processing steps and an interface layer for UI and API access to the knowledge base.
mcpdoc
The MCP LLMS-TXT Documentation Server is an open-source server that provides developers full control over tools used by applications like Cursor, Windsurf, and Claude Code/Desktop. It allows users to create a user-defined list of `llms.txt` files and use a `fetch_docs` tool to read URLs within these files, enabling auditing of tool calls and context returned. The server supports various applications and provides a way to connect to them, configure rules, and test tool calls for tasks related to documentation retrieval and processing.
lightspeed-service
OpenShift LightSpeed (OLS) is an AI powered assistant that runs on OpenShift and provides answers to product questions using backend LLM services. It supports various LLM providers such as OpenAI, Azure OpenAI, OpenShift AI, RHEL AI, and Watsonx. Users can configure the service, manage API keys securely, and deploy it locally or on OpenShift. The project structure includes REST API handlers, configuration loader, LLM providers registry, and more. Additional tools include generating OpenAPI schema, requirements.txt file, and uploading artifacts to an S3 bucket. The project is open source under the Apache 2.0 License.

gemini-ai-code-reviewer
Gemini AI Code Reviewer is a GitHub Action that automatically reviews pull requests using Google's Gemini AI. It analyzes code changes, consults the Gemini model, provides feedback, and delivers review comments directly to pull requests on GitHub. Users need a Gemini API key and can trigger the workflow by commenting '/gemini-review' in the PR. The tool helps improve source code quality by giving suggestions and comments for enhancement.
shortest
Shortest is an AI-powered natural language end-to-end testing framework built on Playwright. It provides a seamless testing experience by allowing users to write tests in natural language and execute them using Anthropic Claude API. The framework also offers GitHub integration with 2FA support, making it suitable for testing web applications with complex authentication flows. Shortest simplifies the testing process by enabling users to run tests locally or in CI/CD pipelines, ensuring the reliability and efficiency of web applications.
For similar tasks

aiven-client
Aiven Client is the official command-line client for Aiven, a next-generation managed cloud services platform. It focuses on ease of adoption, high fault resilience, customer's peace of mind, and advanced features at competitive price points. The client allows users to interact with Aiven services through a command-line interface, providing functionalities such as authentication, project management, service exploration, service launching, service integrations, custom files management, team management, OAuth2 client configuration, autocomplete support, and auth helpers for connecting to services. Users can perform various tasks related to managing cloud services efficiently using the Aiven Client.
For similar jobs
minio
MinIO is a High Performance Object Storage released under GNU Affero General Public License v3.0. It is API compatible with Amazon S3 cloud storage service. Use MinIO to build high performance infrastructure for machine learning, analytics and application data workloads.
ai-on-gke
This repository contains assets related to AI/ML workloads on Google Kubernetes Engine (GKE). Run optimized AI/ML workloads with Google Kubernetes Engine (GKE) platform orchestration capabilities. A robust AI/ML platform considers the following layers: Infrastructure orchestration that support GPUs and TPUs for training and serving workloads at scale Flexible integration with distributed computing and data processing frameworks Support for multiple teams on the same infrastructure to maximize utilization of resources

kong
Kong, or Kong API Gateway, is a cloud-native, platform-agnostic, scalable API Gateway distinguished for its high performance and extensibility via plugins. It also provides advanced AI capabilities with multi-LLM support. By providing functionality for proxying, routing, load balancing, health checking, authentication (and more), Kong serves as the central layer for orchestrating microservices or conventional API traffic with ease. Kong runs natively on Kubernetes thanks to its official Kubernetes Ingress Controller.
AI-in-a-Box
AI-in-a-Box is a curated collection of solution accelerators that can help engineers establish their AI/ML environments and solutions rapidly and with minimal friction, while maintaining the highest standards of quality and efficiency. It provides essential guidance on the responsible use of AI and LLM technologies, specific security guidance for Generative AI (GenAI) applications, and best practices for scaling OpenAI applications within Azure. The available accelerators include: Azure ML Operationalization in-a-box, Edge AI in-a-box, Doc Intelligence in-a-box, Image and Video Analysis in-a-box, Cognitive Services Landing Zone in-a-box, Semantic Kernel Bot in-a-box, NLP to SQL in-a-box, Assistants API in-a-box, and Assistants API Bot in-a-box.
awsome-distributed-training
This repository contains reference architectures and test cases for distributed model training with Amazon SageMaker Hyperpod, AWS ParallelCluster, AWS Batch, and Amazon EKS. The test cases cover different types and sizes of models as well as different frameworks and parallel optimizations (Pytorch DDP/FSDP, MegatronLM, NemoMegatron...).
generative-ai-cdk-constructs
The AWS Generative AI Constructs Library is an open-source extension of the AWS Cloud Development Kit (AWS CDK) that provides multi-service, well-architected patterns for quickly defining solutions in code to create predictable and repeatable infrastructure, called constructs. The goal of AWS Generative AI CDK Constructs is to help developers build generative AI solutions using pattern-based definitions for their architecture. The patterns defined in AWS Generative AI CDK Constructs are high level, multi-service abstractions of AWS CDK constructs that have default configurations based on well-architected best practices. The library is organized into logical modules using object-oriented techniques to create each architectural pattern model.
model_server
OpenVINO™ Model Server (OVMS) is a high-performance system for serving models. Implemented in C++ for scalability and optimized for deployment on Intel architectures, the model server uses the same architecture and API as TensorFlow Serving and KServe while applying OpenVINO for inference execution. Inference service is provided via gRPC or REST API, making deploying new algorithms and AI experiments easy.
dify-helm
Deploy langgenius/dify, an LLM based chat bot app on kubernetes with helm chart.