Best AI tools for< Prevent Security Breaches >
20 - AI tool Sites
icetana
icetana is an AI Security Video Analytics Software that offers Safety and Security Analytics, Forensic Quick Find, Facial Recognition, Licence Plate Recognition, and GPT Event Finder. The core product connects with existing security cameras to detect unusual or interesting events across large surveillance networks. It helps users stay ahead of security incidents with immediate alerts and allows cameras to detect potential security breaches before they happen. icetana AI enhances security and safety through advanced surveillance, covering theft, medical emergencies, routine monitoring, and prevention. The AI continuously evolves, offers real-time event detection, reduces false alarms, and is easy to configure with user-friendly setup.
Concentric AI
Concentric AI is a Managed Data Security Posture Management tool that utilizes Semantic Intelligence to provide comprehensive data security solutions. The platform offers features such as autonomous data discovery, data risk identification, centralized remediation, easy deployment, and data security posture management. Concentric AI helps organizations protect sensitive data, prevent data loss, and ensure compliance with data security regulations. The tool is designed to simplify data governance and enhance data security across various data repositories, both in the cloud and on-premises.
OpenBuckets
OpenBuckets is a web application designed to help users find and secure open buckets in cloud storage systems. The platform scans various cloud storage services to identify publicly accessible buckets, which may contain sensitive data. By detecting these open buckets, OpenBuckets aims to enhance data security and privacy for individuals and organizations. Users can easily search for open buckets and take necessary actions to secure their data, thereby mitigating the risk of unauthorized access and data breaches.
CrowdStrike
CrowdStrike is a cloud-based cybersecurity platform that provides endpoint protection, threat intelligence, and incident response services. It uses artificial intelligence (AI) to detect and prevent cyberattacks. CrowdStrike's platform is designed to be scalable and easy to use, and it can be deployed on-premises or in the cloud. CrowdStrike has a global customer base of over 23,000 organizations, including many Fortune 500 companies.
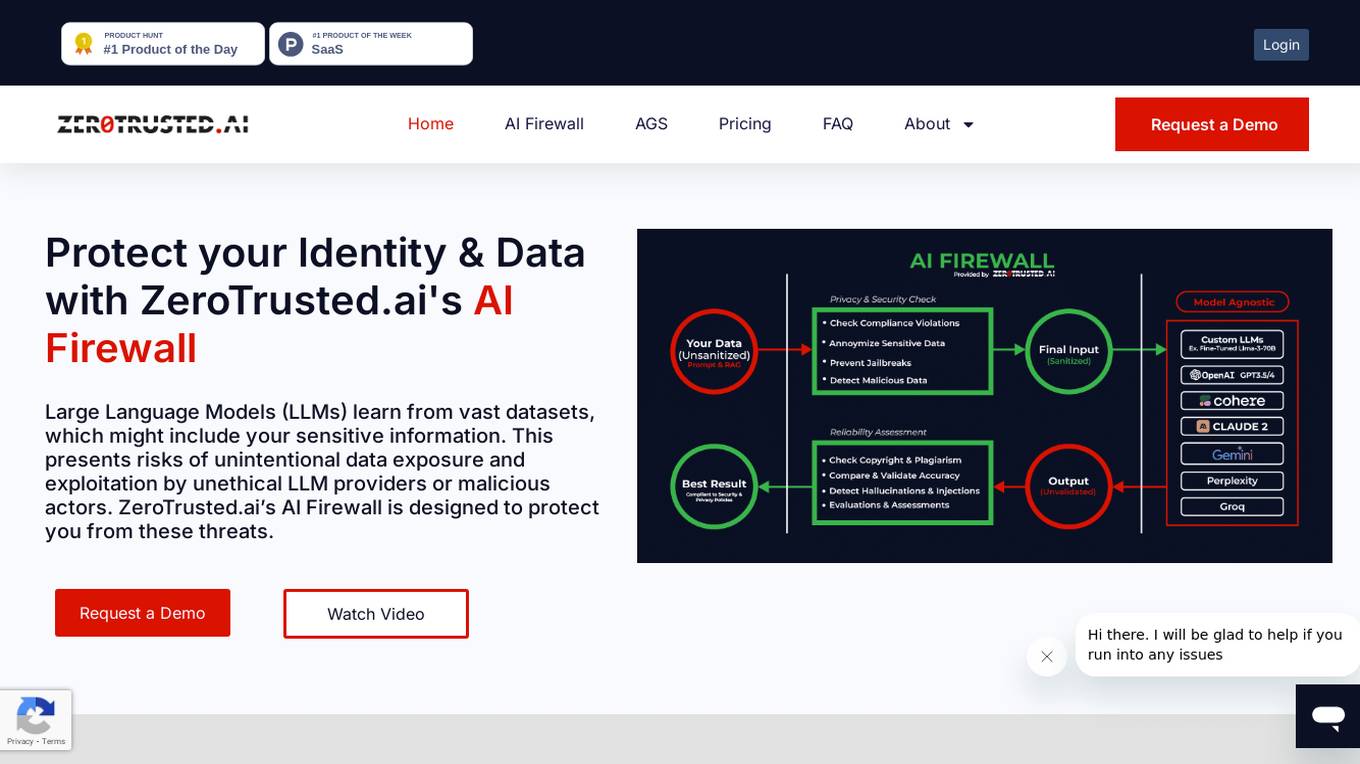
ZeroTrusted.ai
ZeroTrusted.ai is a cybersecurity platform that offers an AI Firewall to protect users from data exposure and exploitation by unethical providers or malicious actors. The platform provides features such as anonymity, security, reliability, integrations, and privacy to safeguard sensitive information. ZeroTrusted.ai empowers organizations with cutting-edge encryption techniques, AI & ML technologies, and decentralized storage capabilities for maximum security and compliance with regulations like PCI, GDPR, and NIST.
Equixly
Equixly is an AI-powered application designed to help secure APIs by identifying vulnerabilities and weaknesses through continuous security testing. The platform offers features such as scalable API PenTesting, rapid remediation, attack simulation, mapping attack surface, compliance simplification, and data exposure minimization. Equixly aims to provide users with a comprehensive solution to enhance API security and reduce the risk of breaches.
Playlab.ai
Playlab.ai is an AI-powered platform that offers a range of tools and applications to enhance online security and protect against cyber attacks. The platform utilizes advanced algorithms to detect and prevent various online threats, such as malicious attacks, SQL injections, and data breaches. Playlab.ai provides users with a secure and reliable online environment by offering real-time monitoring and protection services. With a user-friendly interface and customizable security settings, Playlab.ai is a valuable tool for individuals and businesses looking to safeguard their online presence.
Nametag
Nametag is an identity verification solution designed specifically for IT helpdesks. It helps businesses prevent social engineering attacks, account takeovers, and data breaches by verifying the identity of users at critical moments, such as password resets, MFA resets, and high-risk transactions. Nametag's unique approach to identity verification combines mobile cryptography, device telemetry, and proprietary AI models to provide unmatched security and better user experiences.
DevOps Security Platform
DevOps Security Platform is an AI-native security tool designed to automate security requirements definition, enforcement, risk assessments, and threat modeling. It helps companies secure their applications by identifying risks early in the Software Development Lifecycle and enforcing security controls effectively. The platform offers innovative features, AI-generated questionnaires, and the ability to customize, automate, and integrate security processes. DevOps Security Platform aims to empower security champions and prevent security vulnerabilities through a centralized and automated approach.
LMarena.ai
LMarena.ai is an AI-powered security service that protects websites from online attacks by enabling cookies and blocking malicious activities. It uses advanced algorithms to detect and prevent security threats, ensuring a safe browsing experience for users. The service is designed to safeguard websites from various types of attacks, such as SQL injections and data manipulation. LMarena.ai offers a reliable and efficient security solution for website owners to maintain the integrity and performance of their online platforms.

Facia.ai
Facia.ai is a cutting-edge AI tool that offers the fastest and most accurate liveness detection and deepfake detection solutions. It empowers businesses globally with advanced facial recognition technology, providing services for industries such as retail, government, dating apps, event management, and more. The platform ensures security, prevents identity fraud, and enhances customer authentication processes through innovative AI-powered features.
Vercel Security Checkpoint
Vercel Security Checkpoint is a web application that provides a security verification process for users accessing the Vercel platform. It ensures the safety and integrity of the platform by verifying the user's browser and enabling JavaScript before proceeding. The checkpoint serves as a protective measure to prevent unauthorized access and potential security threats.
Wing Security
Wing Security is a SaaS Security Posture Management (SSPM) solution that helps businesses protect their data by providing full visibility and control over applications, users, and data. The platform offers features such as automated remediation, AI discovery, real-time SaaS visibility, vendor risk management, insider risk management, and more. Wing Security enables organizations to eliminate risky applications, manage user behavior, and protect sensitive data from unauthorized access. With a focus on security first, Wing Security helps businesses leverage the benefits of SaaS while staying protected.
EchoMark
EchoMark is a cloud-based data leak prevention solution that uses invisible forensic watermarks to protect sensitive information from unauthorized access and exfiltration. It allows organizations to securely share and collaborate on documents and emails without compromising privacy and security. EchoMark's advanced investigation tools can trace the source of a leaked document or email, even if it has been shared via printout or photo.
Abnormal AI
Abnormal AI is an email security platform that provides comprehensive protection against email attacks exploiting human behavior, such as phishing and social engineering. The platform deeply understands human behavior through AI-native solutions and API-based architecture. Abnormal Security offers products to secure cloud email, increase productivity with AI, prevent SaaS application attacks, and protect cloud infrastructure. The platform leverages behavioral AI detection, multi-dimensional defense, and human behavior modeling to deliver uniform protection across various communication channels and cloud ecosystems.
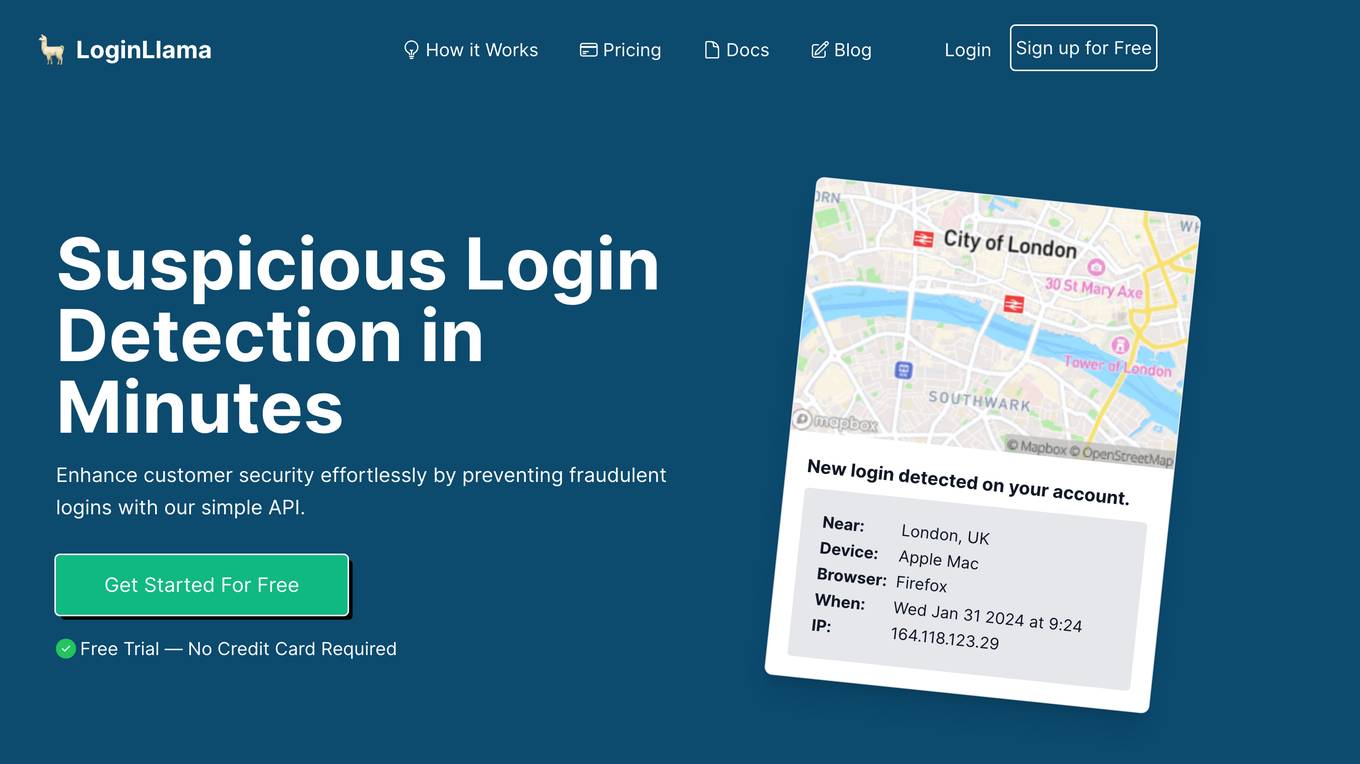
LoginLlama
LoginLlama is an AI-powered suspicious login detection tool designed for developers to enhance customer security effortlessly by preventing fraudulent logins. It provides real-time fraud detection, AI-powered login behavior insights, and easy integration through SDK and API. By evaluating login attempts based on multiple ranking factors and historic behavior analysis, LoginLlama helps protect against unauthorized access, account takeover, credential stuffing, phishing attacks, and insider threats. The tool is user-friendly, offering a simple API for developers to add security checks to their apps with just a few lines of code.
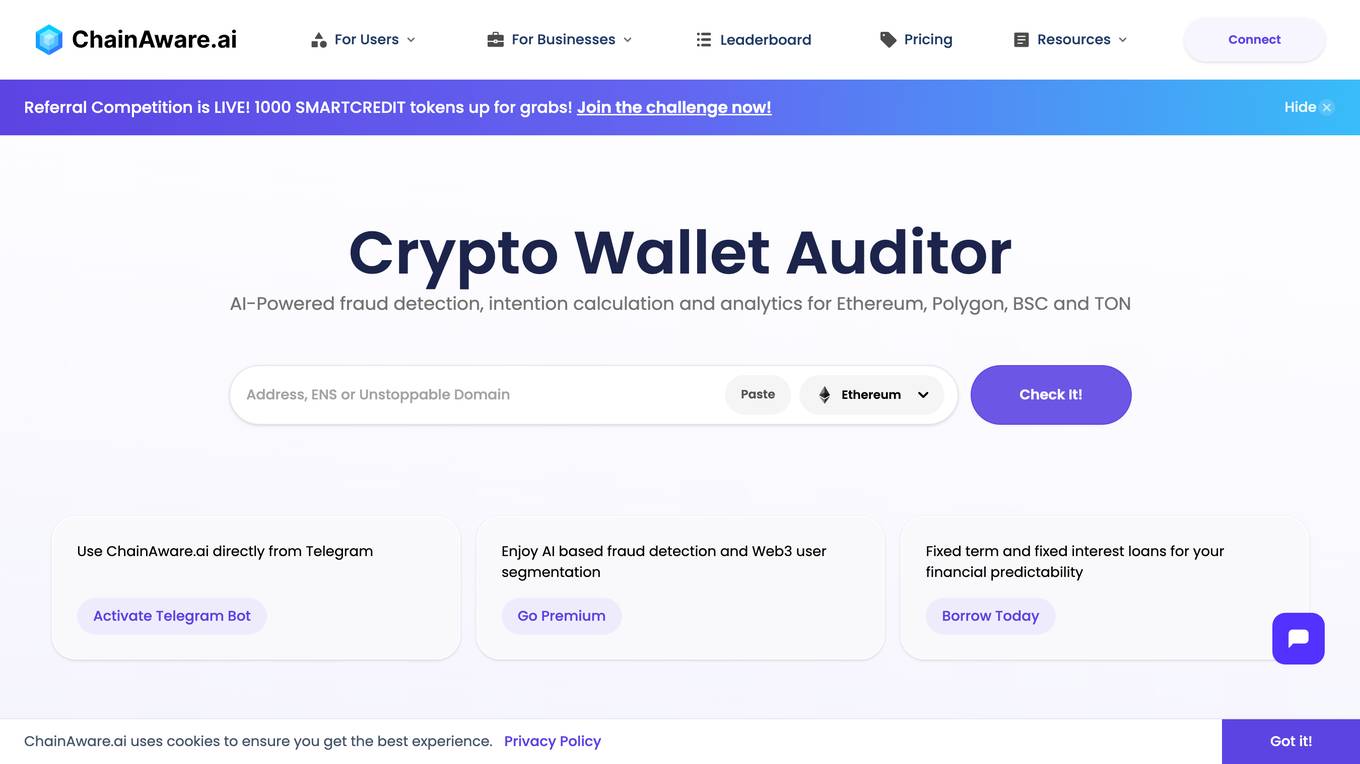
ChainAware.ai
ChainAware.ai is an AI-powered blockchain super tool designed for both users and businesses. It offers a range of features such as Wallet Auditor, Fraud Detector, and Rug Pull Detector to enhance security and trust in blockchain transactions. The tool provides predictive AI capabilities to prevent fraud and identify potential risks before they occur. Additionally, it offers business solutions including account-based user acquisition, web3 user analytics, and crypto fraud detection with AI. ChainAware.ai aims to revolutionize the way users interact with blockchain technology by providing advanced tools and services powered by artificial intelligence.
Mimecast
Mimecast is an AI-powered email and collaboration security application that offers advanced threat protection, cloud archiving, security awareness training, and more. With a focus on protecting communications, data, and people, Mimecast leverages AI technology to provide industry-leading security solutions to organizations globally. The application is designed to defend against sophisticated email attacks, enhance human risk management, and streamline compliance processes.
Magicbookifier.ai
Magicbookifier.ai is an AI tool designed to enhance the security of online connections by verifying the user's identity. It ensures a secure browsing experience by reviewing the security aspects before allowing access to the website. The tool aims to protect users from potential threats and ensure a safe online environment. Magicbookifier.ai utilizes advanced technologies to verify human users and prevent unauthorized access.
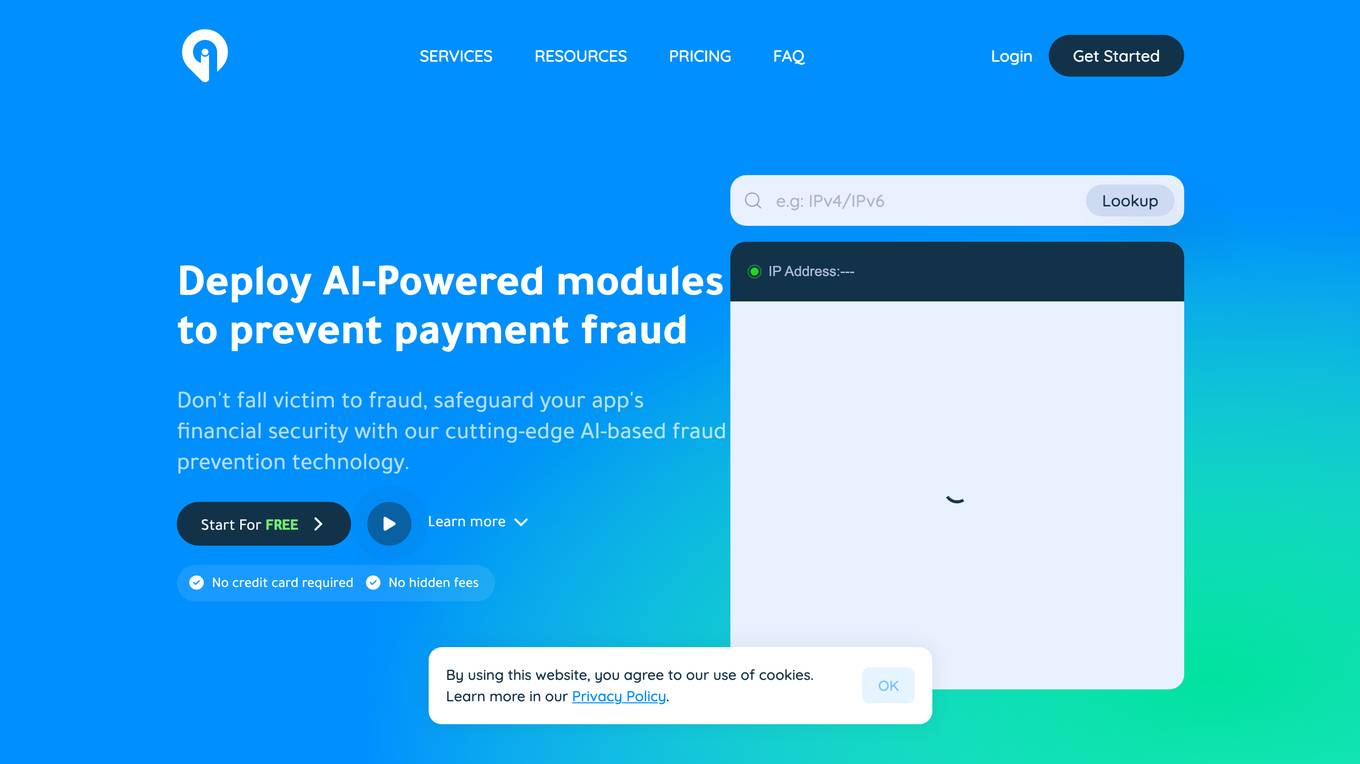
Greip
Greip is an AI-powered fraud prevention tool that offers a range of services to detect and prevent fraudulent activities in payments, validate card and IBAN details, detect profanity in text, identify VPN/proxy connections, provide IP location intelligence, and more. It combines AI-driven transaction analysis with advanced technology to safeguard financial security and enhance data integrity. Greip's services are trusted by businesses worldwide for secure and reliable protection against fraud.
20 - Open Source AI Tools
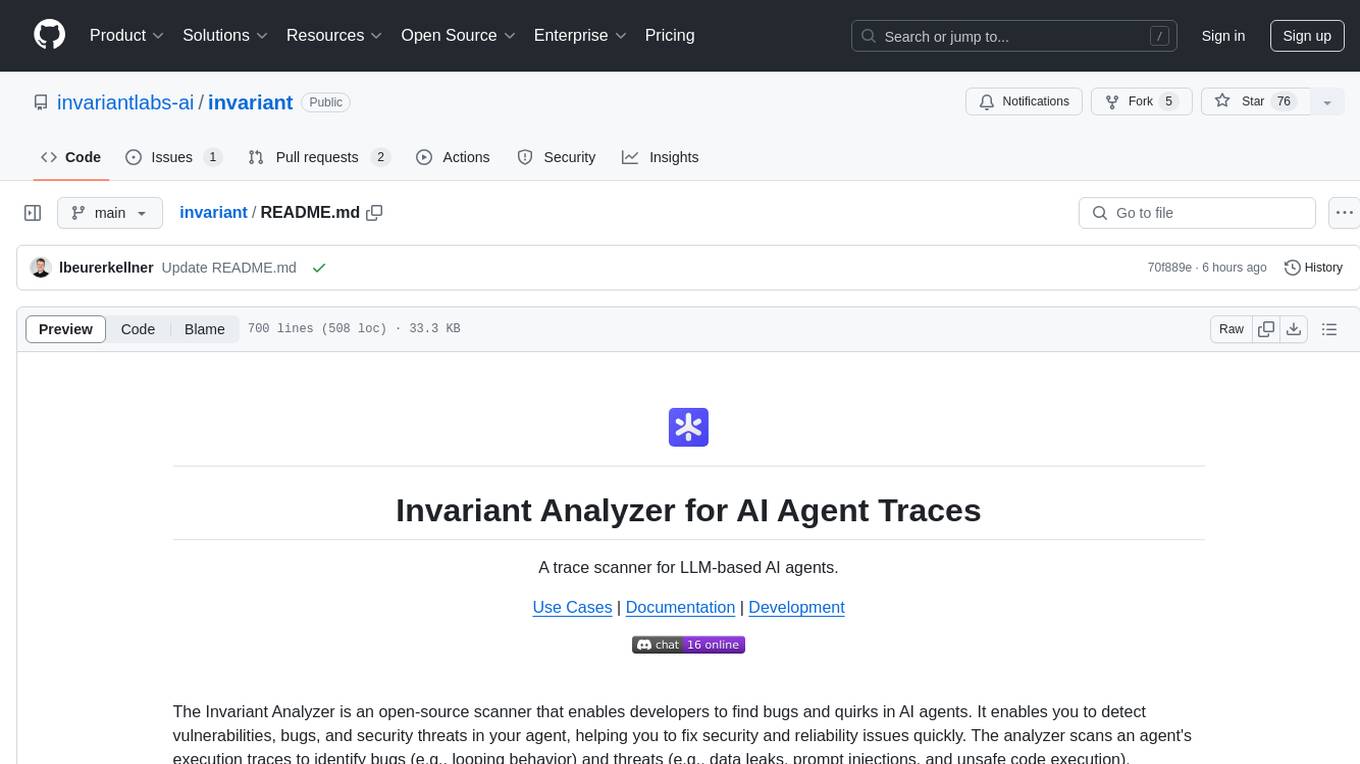
invariant
Invariant Analyzer is an open-source scanner designed for LLM-based AI agents to find bugs, vulnerabilities, and security threats. It scans agent execution traces to identify issues like looping behavior, data leaks, prompt injections, and unsafe code execution. The tool offers a library of built-in checkers, an expressive policy language, data flow analysis, real-time monitoring, and extensible architecture for custom checkers. It helps developers debug AI agents, scan for security violations, and prevent security issues and data breaches during runtime. The analyzer leverages deep contextual understanding and a purpose-built rule matching engine for security policy enforcement.

Chinese-Tiny-LLM
Chinese-Tiny-LLM is a repository containing procedures for cleaning Chinese web corpora and pre-training code. It introduces CT-LLM, a 2B parameter language model focused on the Chinese language. The model primarily uses Chinese data from a 1,200 billion token corpus, showing excellent performance in Chinese language tasks. The repository includes tools for filtering, deduplication, and pre-training, aiming to encourage further research and innovation in language model development.
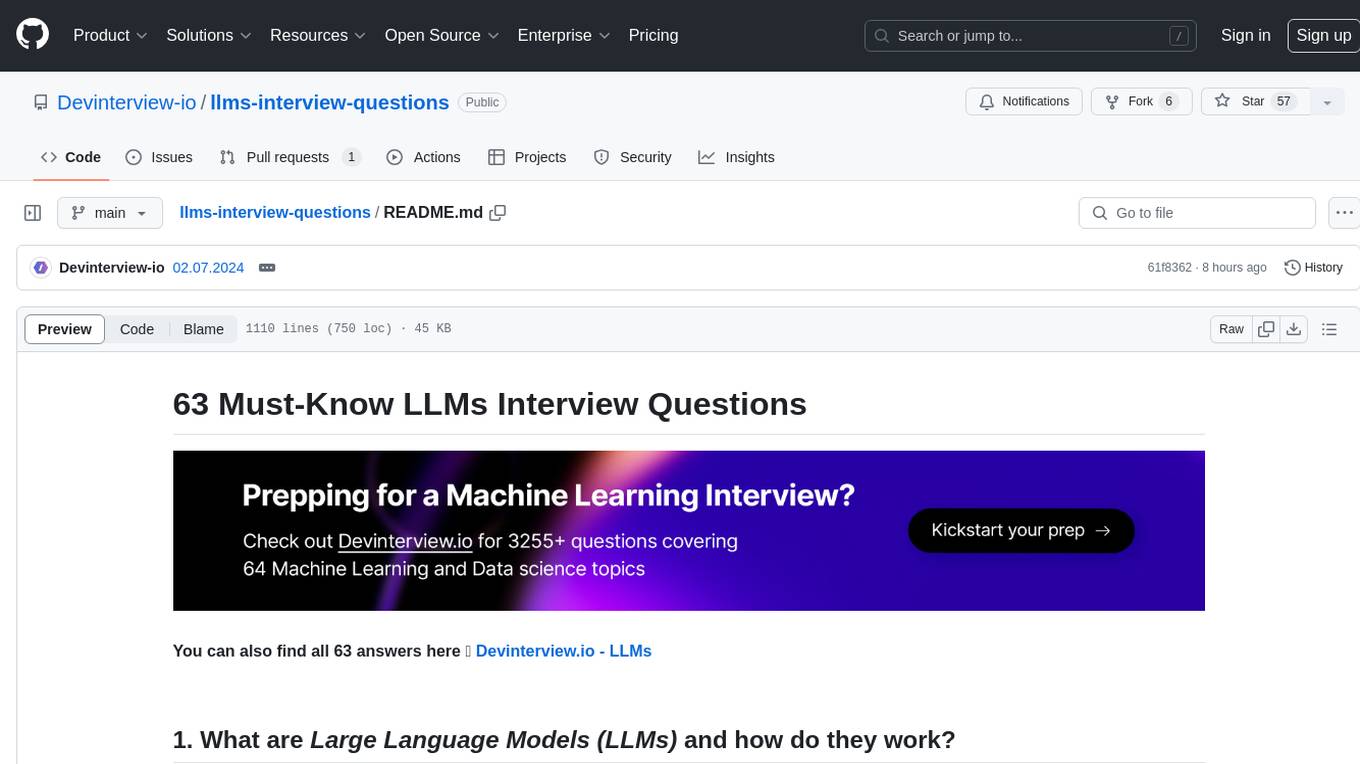
llms-interview-questions
This repository contains a comprehensive collection of 63 must-know Large Language Models (LLMs) interview questions. It covers topics such as the architecture of LLMs, transformer models, attention mechanisms, training processes, encoder-decoder frameworks, differences between LLMs and traditional statistical language models, handling context and long-term dependencies, transformers for parallelization, applications of LLMs, sentiment analysis, language translation, conversation AI, chatbots, and more. The readme provides detailed explanations, code examples, and insights into utilizing LLMs for various tasks.
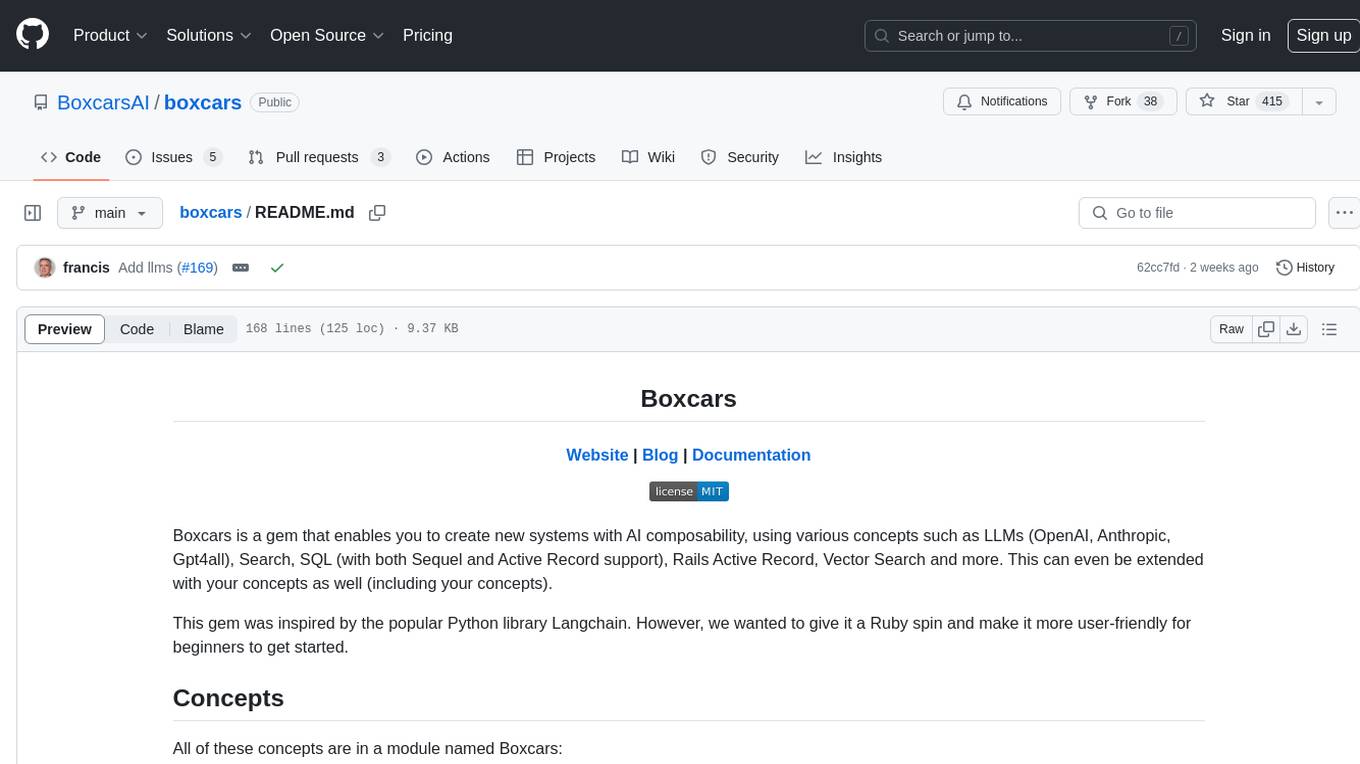
boxcars
Boxcars is a Ruby gem that enables users to create new systems with AI composability, incorporating concepts such as LLMs, Search, SQL, Rails Active Record, Vector Search, and more. It allows users to work with Boxcars, Trains, Prompts, Engines, and VectorStores to solve problems and generate text results. The gem is designed to be user-friendly for beginners and can be extended with custom concepts. Boxcars is actively seeking ways to enhance security measures to prevent malicious actions. Users can use Boxcars for tasks like running calculations, performing searches, generating Ruby code for math operations, and interacting with APIs like OpenAI, Anthropic, and Google SERP.

ciso-assistant-community
CISO Assistant is a tool that helps organizations manage their cybersecurity posture and compliance. It provides a centralized platform for managing security controls, threats, and risks. CISO Assistant also includes a library of pre-built frameworks and tools to help organizations quickly and easily implement best practices.

hackingBuddyGPT
hackingBuddyGPT is a framework for testing LLM-based agents for security testing. It aims to create common ground truth by creating common security testbeds and benchmarks, evaluating multiple LLMs and techniques against those, and publishing prototypes and findings as open-source/open-access reports. The initial focus is on evaluating the efficiency of LLMs for Linux privilege escalation attacks, but the framework is being expanded to evaluate the use of LLMs for web penetration-testing and web API testing. hackingBuddyGPT is released as open-source to level the playing field for blue teams against APTs that have access to more sophisticated resources.

AutoAudit
AutoAudit is an open-source large language model specifically designed for the field of network security. It aims to provide powerful natural language processing capabilities for security auditing and network defense, including analyzing malicious code, detecting network attacks, and predicting security vulnerabilities. By coupling AutoAudit with ClamAV, a security scanning platform has been created for practical security audit applications. The tool is intended to assist security professionals with accurate and fast analysis and predictions to combat evolving network threats.

watchtower
AIShield Watchtower is a tool designed to fortify the security of AI/ML models and Jupyter notebooks by automating model and notebook discoveries, conducting vulnerability scans, and categorizing risks into 'low,' 'medium,' 'high,' and 'critical' levels. It supports scanning of public GitHub repositories, Hugging Face repositories, AWS S3 buckets, and local systems. The tool generates comprehensive reports, offers a user-friendly interface, and aligns with industry standards like OWASP, MITRE, and CWE. It aims to address the security blind spots surrounding Jupyter notebooks and AI models, providing organizations with a tailored approach to enhancing their security efforts.
awesome-MLSecOps
Awesome MLSecOps is a curated list of open-source tools, resources, and tutorials for MLSecOps (Machine Learning Security Operations). It includes a wide range of security tools and libraries for protecting machine learning models against adversarial attacks, as well as resources for AI security, data anonymization, model security, and more. The repository aims to provide a comprehensive collection of tools and information to help users secure their machine learning systems and infrastructure.
ai_automation_suggester
An integration for Home Assistant that leverages AI models to understand your unique home environment and propose intelligent automations. By analyzing your entities, devices, areas, and existing automations, the AI Automation Suggester helps you discover new, context-aware use cases you might not have considered, ultimately streamlining your home management and improving efficiency, comfort, and convenience. The tool acts as a personal automation consultant, providing actionable YAML-based automations that can save energy, improve security, enhance comfort, and reduce manual intervention. It turns the complexity of a large Home Assistant environment into actionable insights and tangible benefits.
0chain
Züs is a high-performance cloud on a fast blockchain offering privacy and configurable uptime. It uses erasure code to distribute data between data and parity servers, allowing flexibility for IT managers to design for security and uptime. Users can easily share encrypted data with business partners through a proxy key sharing protocol. The ecosystem includes apps like Blimp for cloud migration, Vult for personal cloud storage, and Chalk for NFT artists. Other apps include Bolt for secure wallet and staking, Atlus for blockchain explorer, and Chimney for network participation. The QoS protocol challenges providers based on response time, while the privacy protocol enables secure data sharing. Züs supports hybrid and multi-cloud architectures, allowing users to improve regulatory compliance and security requirements.
repopack
Repopack is a powerful tool that packs your entire repository into a single, AI-friendly file. It optimizes your codebase for AI comprehension, is simple to use with customizable options, and respects Gitignore files for security. The tool generates a packed file with clear separators and AI-oriented explanations, making it ideal for use with Generative AI tools like Claude or ChatGPT. Repopack offers command line options, configuration settings, and multiple methods for setting ignore patterns to exclude specific files or directories during the packing process. It includes features like comment removal for supported file types and a security check using Secretlint to detect sensitive information in files.
repomix
Repomix is a powerful tool that packs your entire repository into a single, AI-friendly file. It is designed to format your codebase for easy understanding by AI tools like Large Language Models (LLMs), Claude, ChatGPT, and Gemini. Repomix offers features such as AI optimization, token counting, simplicity in usage, customization options, Git awareness, and security-focused checks using Secretlint. It allows users to pack their entire repository or specific directories/files using glob patterns, and even supports processing remote Git repositories. The tool generates output in plain text, XML, or Markdown formats, with options for including/excluding files, removing comments, and performing security checks. Repomix also provides a global configuration option, custom instructions for AI context, and a security check feature to detect sensitive information in files.
gateway
Gateway is a tool that streamlines requests to 100+ open & closed source models with a unified API. It is production-ready with support for caching, fallbacks, retries, timeouts, load balancing, and can be edge-deployed for minimum latency. It is blazing fast with a tiny footprint, supports load balancing across multiple models, providers, and keys, ensures app resilience with fallbacks, offers automatic retries with exponential fallbacks, allows configurable request timeouts, supports multimodal routing, and can be extended with plug-in middleware. It is battle-tested over 300B tokens and enterprise-ready for enhanced security, scale, and custom deployments.
airunner
AI Runner is a multi-modal AI interface that allows users to run open-source large language models and AI image generators on their own hardware. The tool provides features such as voice-based chatbot conversations, text-to-speech, speech-to-text, vision-to-text, text generation with large language models, image generation capabilities, image manipulation tools, utility functions, and more. It aims to provide a stable and user-friendly experience with security updates, a new UI, and a streamlined installation process. The application is designed to run offline on users' hardware without relying on a web server, offering a smooth and responsive user experience.
MiniCPM-V
MiniCPM-V is a series of end-side multimodal LLMs designed for vision-language understanding. The models take image and text inputs to provide high-quality text outputs. The series includes models like MiniCPM-Llama3-V 2.5 with 8B parameters surpassing proprietary models, and MiniCPM-V 2.0, a lighter model with 2B parameters. The models support over 30 languages, efficient deployment on end-side devices, and have strong OCR capabilities. They achieve state-of-the-art performance on various benchmarks and prevent hallucinations in text generation. The models can process high-resolution images efficiently and support multilingual capabilities.
arch
Arch is an intelligent Layer 7 gateway designed to protect, observe, and personalize LLM applications with APIs. It handles tasks like detecting and rejecting jailbreak attempts, calling backend APIs, disaster recovery, and observability. Built on Envoy Proxy, it offers features like function calling, prompt guardrails, traffic management, and standards-based observability. Arch aims to improve the speed, security, and personalization of generative AI applications.
archgw
Arch is an intelligent Layer 7 gateway designed to protect, observe, and personalize AI agents with APIs. It handles tasks related to prompts, including detecting jailbreak attempts, calling backend APIs, routing between LLMs, and managing observability. Built on Envoy Proxy, it offers features like function calling, prompt guardrails, traffic management, and observability. Users can build fast, observable, and personalized AI agents using Arch to improve speed, security, and personalization of GenAI apps.

Equivariant-Encryption-for-AI
At Nesa, privacy is a critical objective. Equivariant Encryption (EE) is a solution developed to perform inference on neural networks without exposing input and output data. EE integrates specialized transformations for neural networks, maintaining data privacy while ensuring inference operates correctly on encrypted inputs. It provides the same latency as plaintext inference with no slowdowns and offers strong security guarantees. EE avoids the computational costs of traditional Homomorphic Encryption (HE) by preserving non-linear neural functions. The tool is designed for modern neural architectures, ensuring accuracy, scalability, and compatibility with existing pipelines.
20 - OpenAI Gpts

Phish or No Phish Trainer
Hone your phishing detection skills! Analyze emails, texts, and calls to spot deception. Become a security pro!
GPT Auth™
This is a demonstration of GPT Auth™, an authentication system designed to protect your customized GPT.
Auth Guide - Authentication & Authorization Expert
Detailed, step-by-step authentication & authorization guide for programmers, with code examples.
MITRE Interpreter
This GPT helps you understand and apply the MITRE ATT&CK Framework, whether you are familiar with the concepts or not.
Online Doc
You are a virtual general practitioner who makes a basic diagnosis based on the consultant's description and gives advice on treatment and how to prevent such diseases.
Plagiarism Checker
Plagiarism Checker GPT is powered by Winston AI and created to help identify plagiarized content. It is designed to help you detect instances of plagiarism and maintain integrity in academia and publishing. Winston AI is the most trusted AI and Plagiarism Checker.
Punaises de Lit
Expert sur les punaises de lit, conseils d'identification et mesures à prendre en cas d'infestation.