Best AI tools for< Security Tester >
Infographic
20 - AI tool Sites
Senior AI
Senior AI is a platform that leverages Artificial Intelligence to help individuals and companies develop and manage software products more efficiently and securely. It offers codebase awareness, bug analysis, security optimization, and productivity enhancements, making software development faster and more reliable. The platform provides different pricing tiers suitable for individuals, power users, small teams, growing teams, and large teams, with the option for enterprise solutions. Senior AI aims to supercharge software development with an AI-first approach, guiding users through the development process and providing tailored code suggestions and security insights.
CensysGPT Beta
CensysGPT Beta is a tool that simplifies building queries and empowers users to conduct efficient and effective reconnaissance operations. It enables users to quickly and easily gain insights into hosts on the internet, streamlining the process and allowing for more proactive threat hunting and exposure management.
Masterhackers
Masterhackers is an all-in-one cybersecurity application designed to help cybersecurity professionals and students prepare for certifications and interviews. The platform offers a comprehensive set of tools and resources, including practice tests, flashcards, mock interviews, and personalized feedback with AI. Trusted by students worldwide, Masterhackers aims to enhance users' cybersecurity skills and knowledge through interactive learning experiences.
Giskard
Giskard is an AI Red Teaming & LLM Security Platform designed to continuously secure LLM agents by preventing hallucinations and security issues in production. It offers automated testing to catch vulnerabilities before they happen, trusted by enterprise AI leaders to ensure data and reputation protection. The platform provides comprehensive protection against various security attacks and vulnerabilities, offering end-to-end encryption, data residency & isolation, and compliance with GDPR, SOC 2 Type II, and HIPAA. Giskard helps in uncovering AI vulnerabilities, stopping business failures at the source, unifying testing across teams, and saving time with continuous testing to prevent regressions.
Qwiet AI
Qwiet AI is a code vulnerability detection platform that accelerates secure coding by uncovering, prioritizing, and generating fixes for top vulnerabilities with a single scan. It offers features such as AI-enhanced SAST, contextual SCA, AI AutoFix, Container Security, SBOM, and Secrets detection. Qwiet AI helps InfoSec teams in companies to accurately pinpoint and autofix risks in their code, reducing false positives and remediation time. The platform provides a unified vulnerability dashboard, prioritizes risks, and offers tailored fix suggestions based on the full context of the code.
Equixly
Equixly is an AI-powered application designed to help users secure their APIs by identifying vulnerabilities and weaknesses through continuous security testing. The platform offers features such as scalable API PenTesting, attack simulation, mapping of attack surfaces, compliance simplification, and data exposure minimization. Equixly aims to streamline the process of identifying and fixing API security risks, ultimately enabling users to release secure code faster and reduce their attack surface.
Huntr
Huntr is the world's first bug bounty platform for AI/ML. It provides a single place for security researchers to submit vulnerabilities, ensuring the security and stability of AI/ML applications, including those powered by Open Source Software (OSS).
SMshrimant
SMshrimant is a personal website belonging to a Bug Bounty Hunter, Security Researcher, Penetration Tester, and Ethical Hacker. The website showcases the creator's skills and experiences in the field of cybersecurity, including bug hunting, security vulnerability reporting, open-source tool development, and participation in Capture The Flag competitions. Visitors can learn about the creator's projects, achievements, and contact information for inquiries or collaborations.
Pentest Copilot
Pentest Copilot by BugBase is an ultimate ethical hacking assistant that guides users through each step of the hacking journey, from analyzing web apps to root shells. It eliminates redundant research, automates payload and command generation, and provides intelligent contextual analysis to save time. The application excels at data extraction, privilege escalation, lateral movement, and leaving no trace behind. With features like secure VPN integration, total control over sessions, parallel command processing, and flexibility to choose between local or cloud execution, Pentest Copilot offers a seamless and efficient hacking experience without the need for Kali Linux installation.
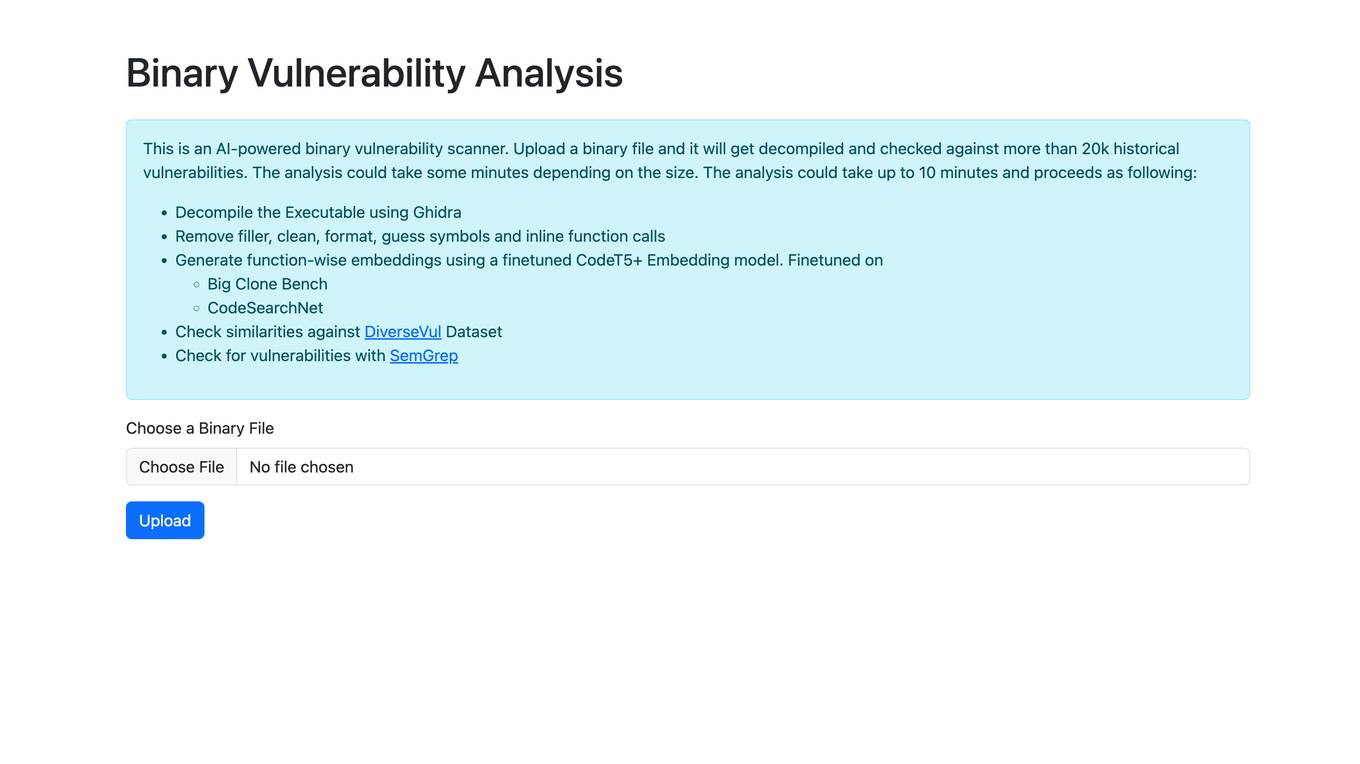
Binary Vulnerability Analysis
The website offers an AI-powered binary vulnerability scanner that allows users to upload a binary file for analysis. The tool decompiles the executable, removes filler, cleans, formats, and checks for historical vulnerabilities. It generates function-wise embeddings using a finetuned CodeT5+ Embedding model and checks for similarities against the DiverseVul Dataset. The tool also utilizes SemGrep to check for vulnerabilities in the binary file.
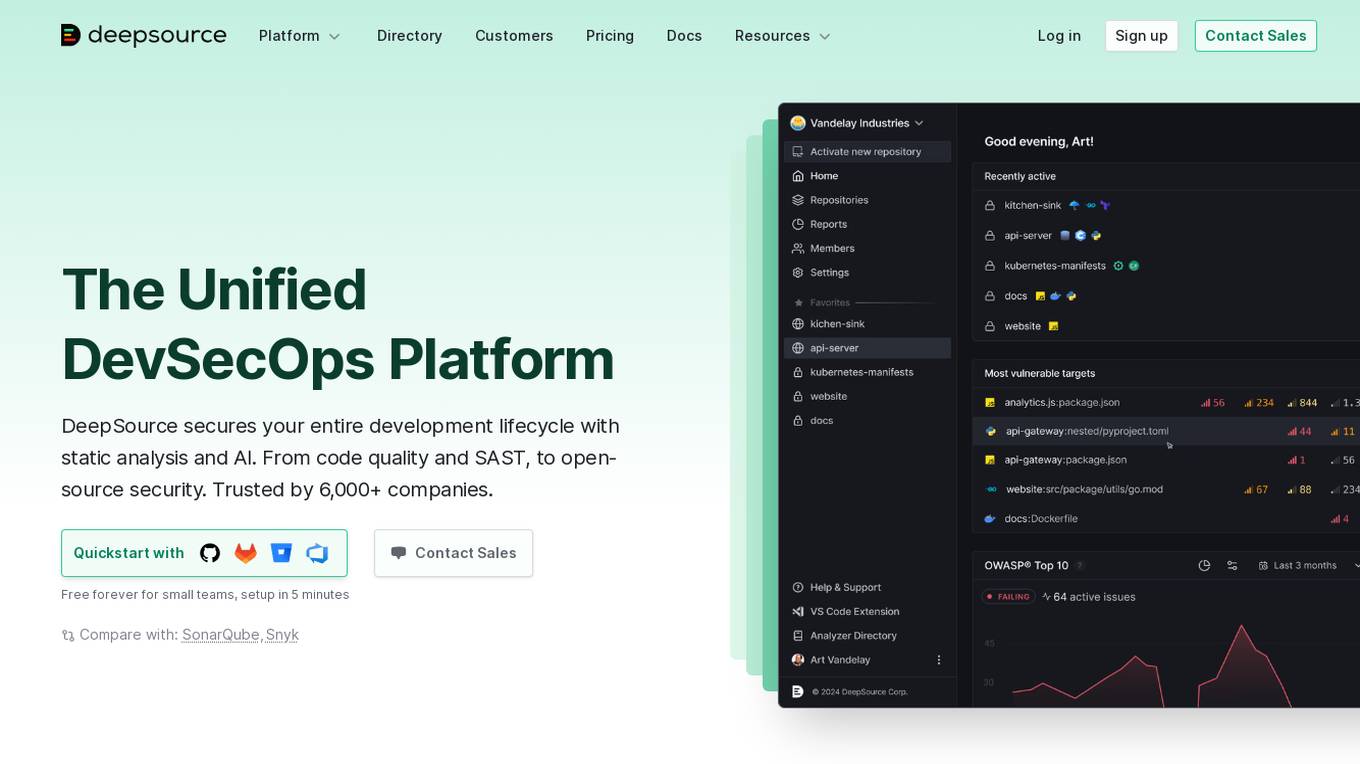
DeepSource
DeepSource is a Unified DevSecOps Platform that secures the entire development lifecycle with static analysis and AI. It offers code quality and SAST, open-source security, and is trusted by over 6,000 companies. The platform helps in finding and fixing security vulnerabilities before code is merged, with a low false-positive rate and customizable security gates for pull requests. DeepSource is built for modern software development, providing features like Autofix™ AI, code coverage, and integrations with popular tools like Jira and GitHub Issues. It offers detailed reports, issue suppression, and metric thresholds to ensure clean and secure code shipping.
nunu.ai
nunu.ai is an AI-powered platform designed to revolutionize game testing by leveraging AI agents to conduct end-to-end tests at scale. By automating repetitive tasks, the platform significantly reduces manual QA costs for game studios. With features like human-like testing, multi-platform support, and enterprise-grade security, nunu.ai offers a comprehensive solution for game developers seeking efficient and reliable testing processes.
Abstracta Solutions
Abstracta Solutions is an AI software development company that provides holistic solutions for software quality. They offer services such as AI software development, testing strategy, functional testing, test automation, performance testing, tool development, accessibility testing, security testing, and DevOps services. Abstracta Solutions empowers organizations with AI-driven solutions to streamline software development processes and enhance customer experiences. They focus on continuously delivering high-quality software by co-creating quality strategies and leveraging expertise in different areas of software development.
World of Tanks
World of Tanks is a popular strategic shooter game with over 160 million players worldwide. Players can enjoy the game for free and claim a starter pack including a Tier II Premium Tank, 7 Days of Premium Account, 1 Garage Slot, 100% Trained Crew, and 200,000 credits. The game offers an immersive gaming experience with various in-game purchases and interactions. Players can create an account using social media, choose a unique in-game name, and enjoy gameplay in multiple languages. Wargaming.net, the developer of World of Tanks, ensures user privacy and data security through an End User License Agreement and Privacy Policy.
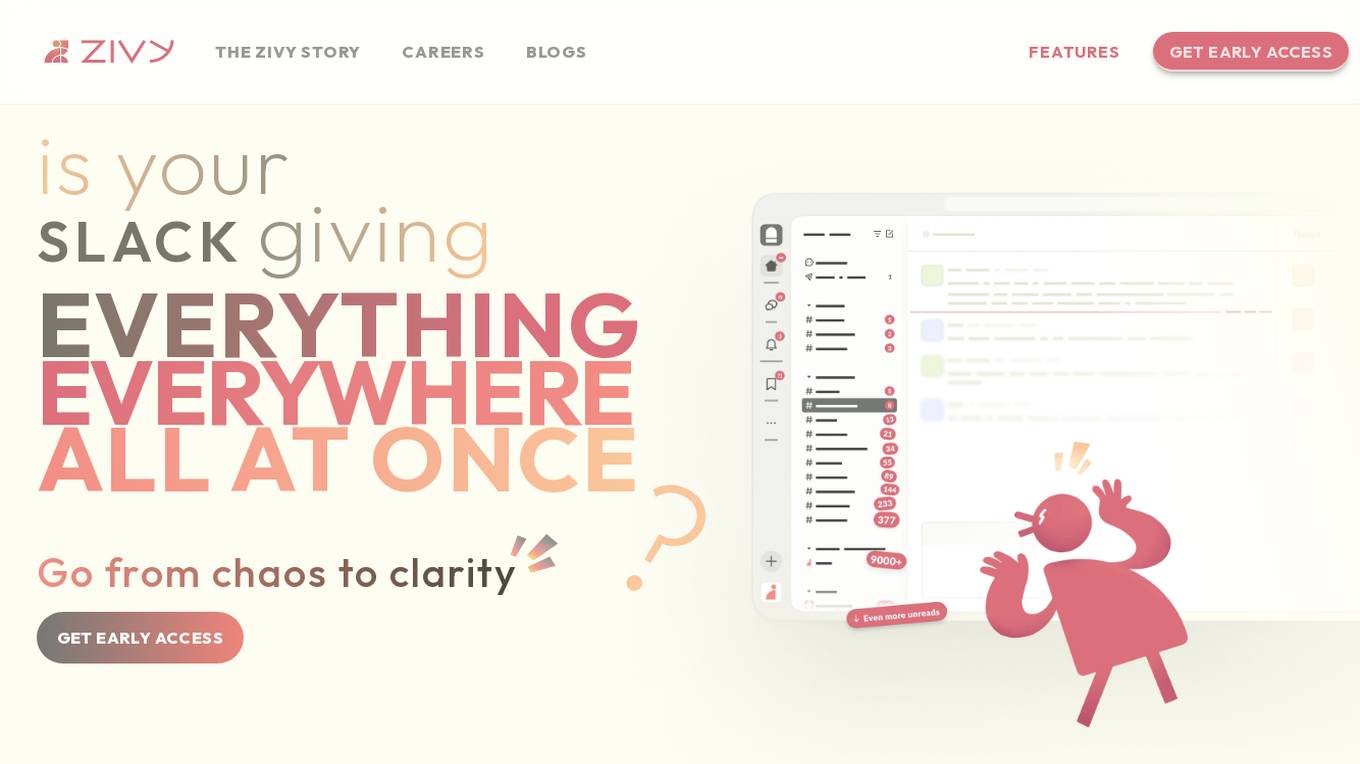
Zivy
Zivy is an AI-powered communication tool designed to help Engineering and Product Leads manage and prioritize messages effectively. It transforms the chaotic Slack environment into organized stacks of cards, ensuring that users focus on what truly matters. Zivy's AI capabilities learn user preferences, prioritize important messages, and continuously improve efficiency. The application also emphasizes data security, encrypting messages, and adhering to strict privacy standards. Zivy aims to streamline communication processes and enhance productivity by reducing noise and optimizing message delivery.
Evebyte Studio
Evebyte Studio is a Windows software that allows users to easily control physical Android phone devices with a graphical interface, without the need for coding. Users can create and manage tasks on their phones through their PC, enabling efficient management of multiple devices. The software ensures data security and grants users the right to use it. Evebyte Studio simplifies the process of building an AI phone assistant, making it accessible to all users.
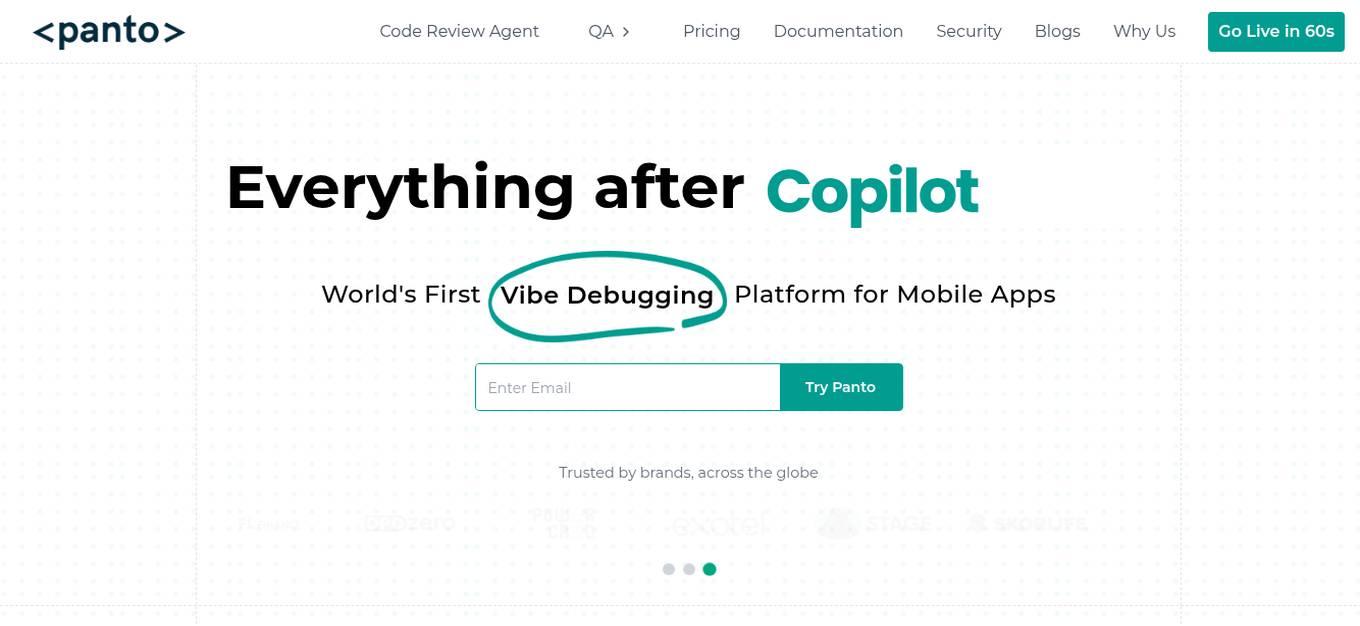
Panto AI
Panto AI is an AI automation testing platform that offers a comprehensive solution for mobile app testing, combining dynamic code reviews, code security checks, and QA automation. It allows users to create, execute, and run mobile test cases in natural language, ensuring reliable and efficient testing processes. With features like self-healing automation, real device testing, and deep failure visibility, Panto AI aims to streamline the QA process and enhance app quality. The platform is designed to be platform-agnostic and supports various integrations, making it suitable for diverse mobile app environments.
Parasoft
Parasoft is an intelligent automated testing and quality platform that offers a range of tools covering every stage of the software development lifecycle. It provides solutions for compliance standards, automated software testing, and various industries' needs. Parasoft helps users accelerate software delivery, ensure quality, and comply with safety and security standards.
Ivie
Ivie is an AI-powered user research tool that automates the collection and analysis of qualitative user insights to help product teams build better products. It offers features such as AI-powered insights, processed user insights, in-depth analysis, automated follow-up questions, multilingual support, and more. Ivie provides advantages like human-like conversations, scalable surveys, customizable AI researchers, quick research setup, and multiple question types. However, it has disadvantages such as limited customization options, potential language barriers, and the need for user training. The frequently asked questions cover topics like supported research types, data security, multilingual research, and research findings presentation. Ivie is suitable for jobs related to user research, product development, customer satisfaction analysis, market research, and concept testing. The application can be used for tasks like conducting customer interviews, analyzing user feedback, creating surveys, synthesizing research findings, and building user personas.
Textero AI Essay Writer
Textero is an AI-powered essay writing tool that offers a comprehensive platform for generating academic essays, research papers, and summaries. It utilizes advanced algorithms and natural language processing models to streamline the writing process for students and researchers. With features like customizable text generation, plagiarism-free content, data security, real references, and time-saving capabilities, Textero aims to provide a reliable and secure platform for all academic writing needs. The tool also offers multilingual capabilities, advanced customization options, and the ability to select different essay types for deeper personalization. Textero is revolutionizing the education sector by making AI essay writing tools more accessible and popular among students.
0 - Open Source Tools
20 - OpenAI Gpts
Security Testing Advisor
Ensures software security through comprehensive testing techniques.
🛡️ CodeGuardian Pro+ 🛡️
Your AI-powered sentinel for code! Scans for vulnerabilities, offers security tips, and educates on best practices in cybersecurity. 🔍🔐
PentestGPT
A cybersecurity expert aiding in penetration testing. Check repo: https://github.com/GreyDGL/PentestGPT
RobotGPT
Expert in ethical hacking, leveraging https://pentestbook.six2dez.com/ and https://book.hacktricks.xyz resources for CTFs and challenges.
Ethical Hacking GPT
Guide to ethical hacking, specializing in NMAP | For Educational Purposes Only | CSV Upload Suggested |

GetPaths
This GPT takes in content related to an application, such as HTTP traffic, JavaScript files, source code, etc., and outputs lists of URLs that can be used for further testing.