Huntr
The world's first bug bounty platform for AI/ML
Huntr is the world's first bug bounty platform for AI/ML. It provides a single place for security researchers to submit vulnerabilities, ensuring the security and stability of AI/ML applications, including those powered by Open Source Software (OSS).
For Tasks:
Click tags to check more tools for each tasksFor Jobs:
Features
Advantages
Disadvantages
Frequently Asked Questions
Alternative AI tools for Huntr
Similar sites

Huntr
Huntr is the world's first bug bounty platform for AI/ML. It provides a single place for security researchers to submit vulnerabilities, ensuring the security and stability of AI/ML applications, including those powered by Open Source Software (OSS).
VIDOC
VIDOC is an AI-powered security engineer that automates code review and penetration testing. It continuously scans and reviews code to detect and fix security issues, helping developers deliver secure software faster. VIDOC is easy to use, requiring only two lines of code to be added to a GitHub Actions workflow. It then takes care of the rest, providing developers with a tailored code solution to fix any issues found.
Semgrep
Semgrep is an AI-powered application designed for static analysis and security testing of code. It helps developers find and fix issues in their code, detect vulnerabilities in the software supply chain, and identify hardcoded secrets. Semgrep offers features such as AI-powered noise filtering, dataflow analysis, and tailored remediation guidance. It is known for its speed, transparency, and extensibility, making it a valuable tool for AppSec teams of all sizes.
Cyguru
Cyguru is an all-in-one cloud-based AI Security Operation Center (SOC) that offers a comprehensive range of features for a robust and secure digital landscape. Its Security Operation Center is the cornerstone of its service domain, providing AI-Powered Attack Detection, Continuous Monitoring for Vulnerabilities and Misconfigurations, Compliance Assurance, SecPedia: Your Cybersecurity Knowledge Hub, and Advanced ML & AI Detection. Cyguru's AI-Powered Analyst promptly alerts users to any suspicious behavior or activity that demands attention, ensuring timely delivery of notifications. The platform is accessible to everyone, with up to three free servers and subsequent pricing that is more than 85% below the industry average.
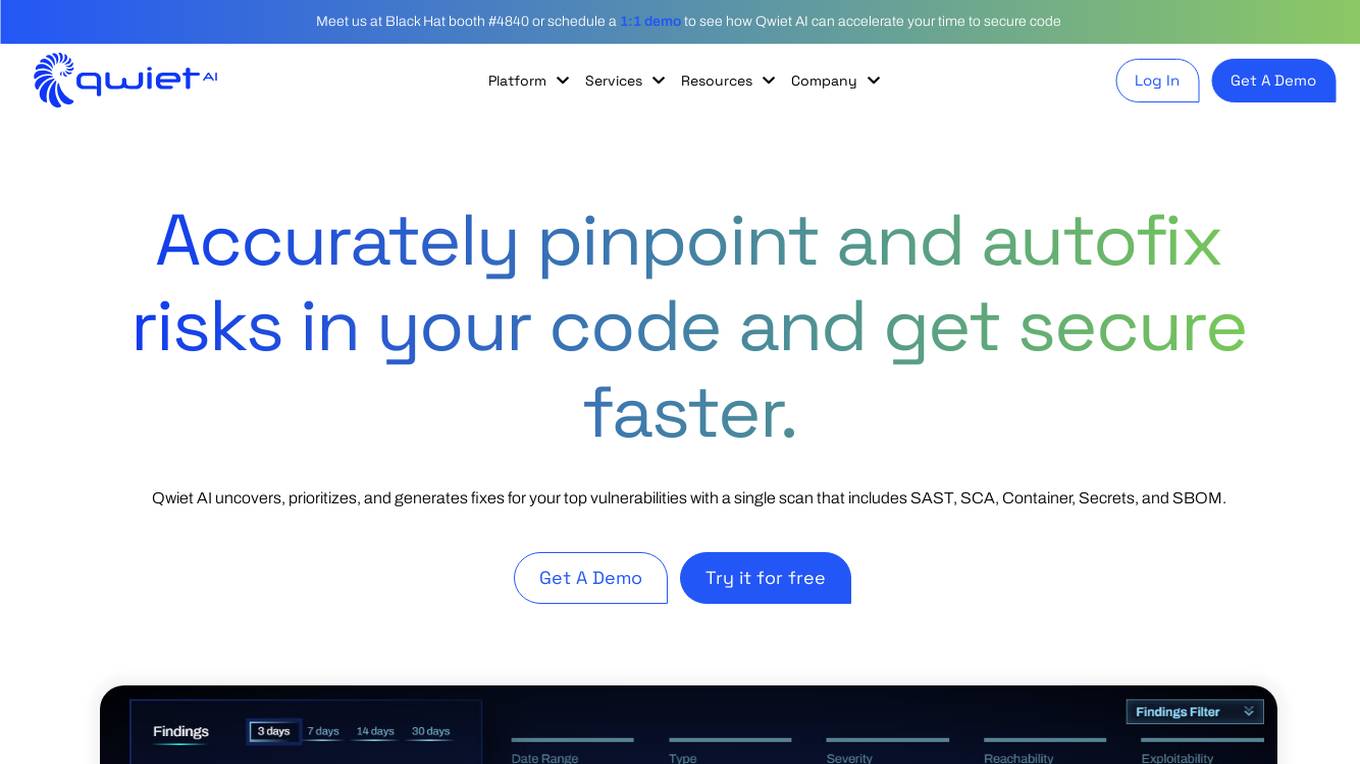
Qwiet AI
Qwiet AI is a code vulnerability detection platform that accelerates secure coding by uncovering, prioritizing, and generating fixes for top vulnerabilities with a single scan. It offers features such as AI-enhanced SAST, contextual SCA, AI AutoFix, Container Security, SBOM, and Secrets detection. Qwiet AI helps InfoSec teams in companies to accurately pinpoint and autofix risks in their code, reducing false positives and remediation time. The platform provides a unified vulnerability dashboard, prioritizes risks, and offers tailored fix suggestions based on the full context of the code.
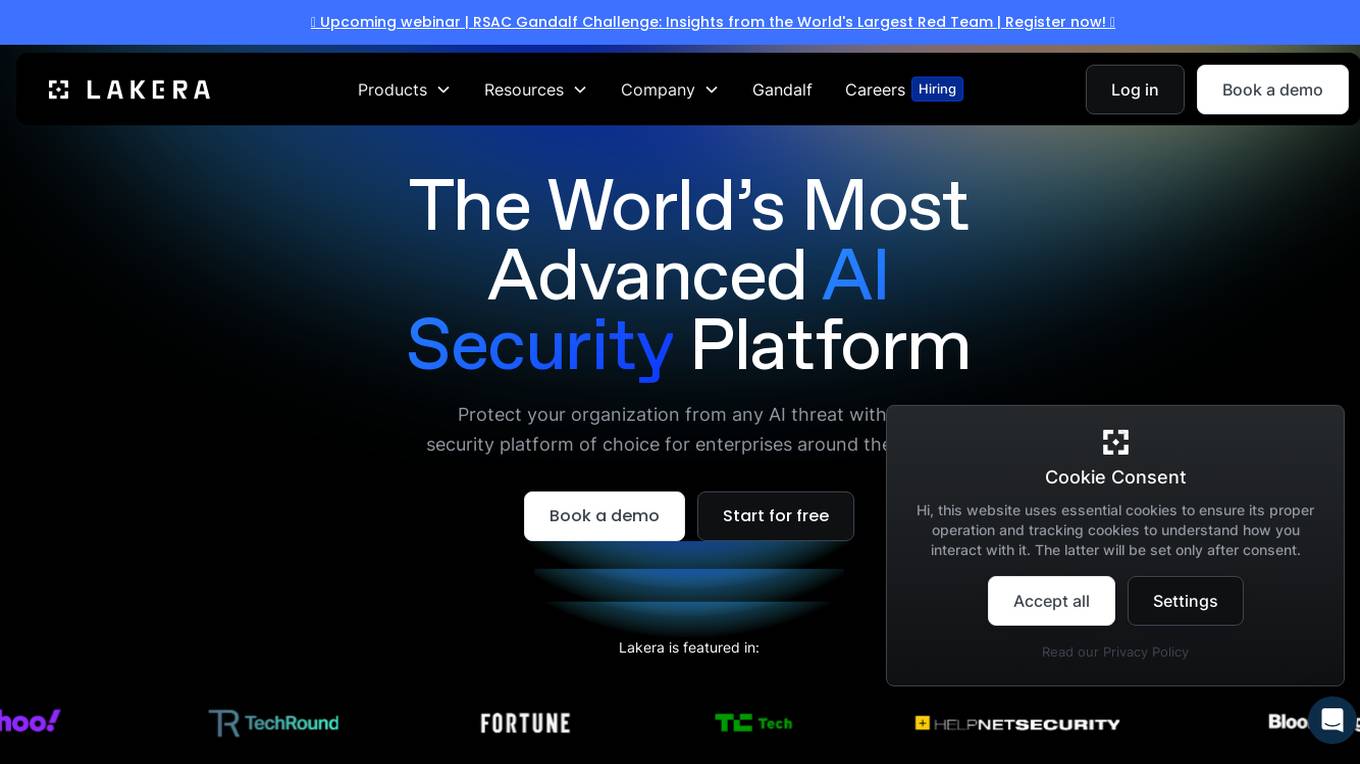
Lakera
Lakera is the world's most advanced AI security platform designed to protect organizations from AI threats. It offers solutions for prompt injection detection, unsafe content identification, PII and data loss prevention, data poisoning prevention, and insecure LLM plugin design. Lakera is recognized for setting global AI security standards and is trusted by leading enterprises, foundation model providers, and startups. The platform is powered by a proprietary AI threat database and aligns with global AI security frameworks.
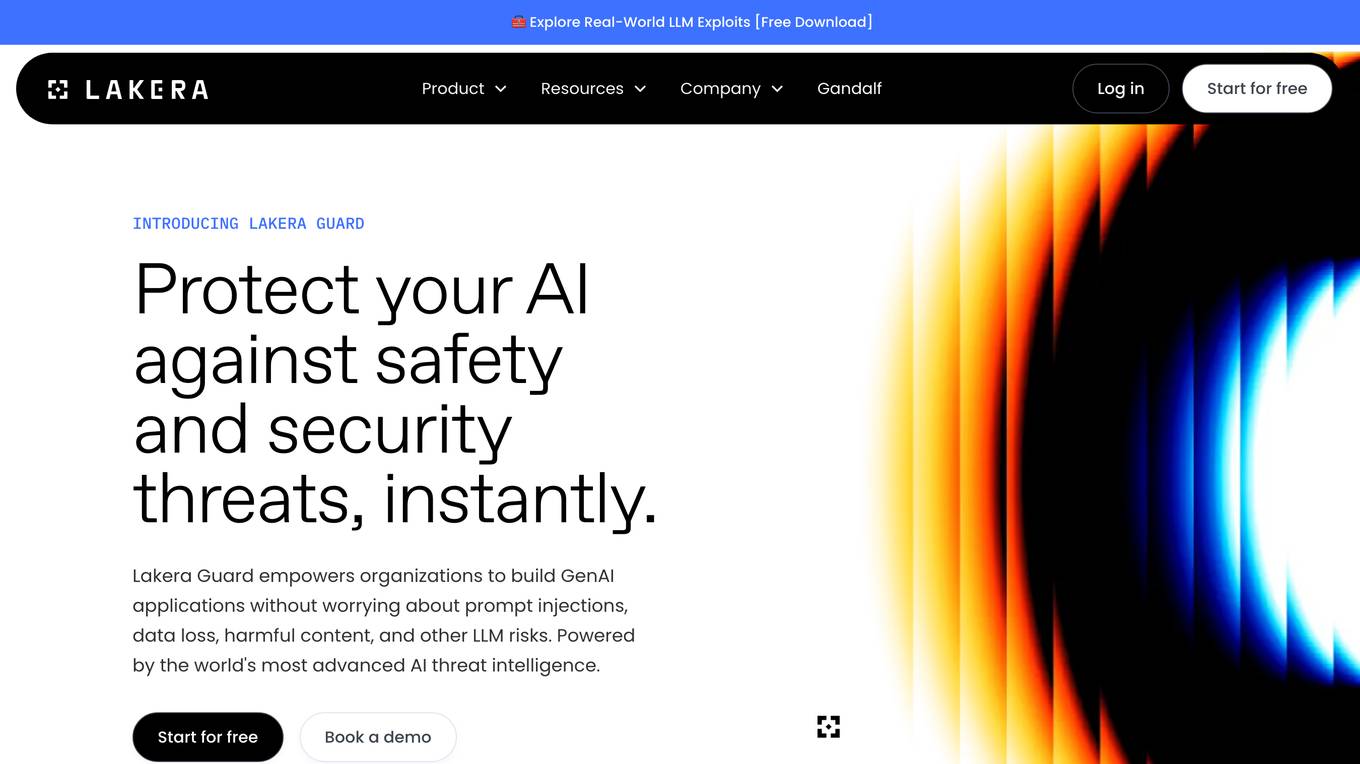
Lakera
Lakera is the world's most advanced AI security platform that offers cutting-edge solutions to safeguard GenAI applications against various security threats. Lakera provides real-time security controls, stress-testing for AI systems, and protection against prompt attacks, data loss, and insecure content. The platform is powered by a proprietary AI threat database and aligns with global AI security frameworks to ensure top-notch security standards. Lakera is suitable for security teams, product teams, and LLM builders looking to secure their AI applications effectively and efficiently.
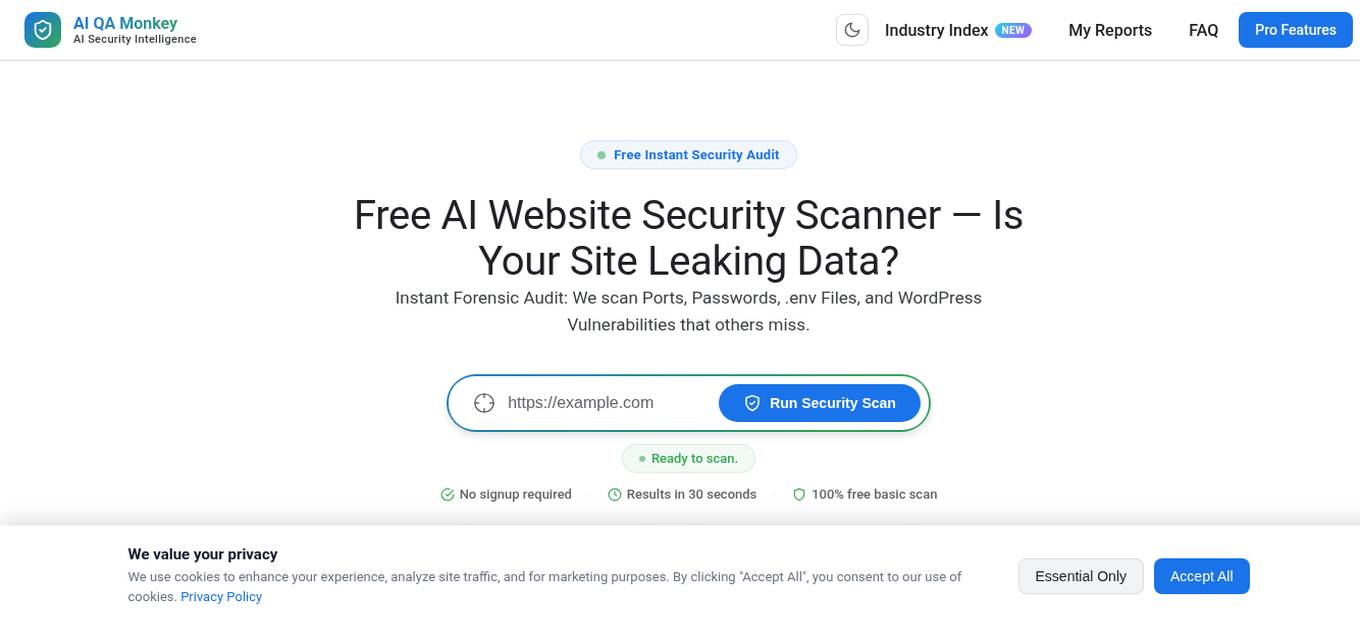
AI QA Monkey
AI QA Monkey is a free website security scanner that offers instant security audits to check website security scores. The tool scans for vulnerabilities such as leaked sensitive data, open ports, passwords, .env files, and WordPress vulnerabilities. It provides a detailed security report with actionable insights and AI-powered fixes. Users can export reports in PDF, JSON, or CSV formats. AI QA Monkey is designed to help businesses improve their security posture and comply with GDPR regulations.
Prompt Security
Prompt Security is a platform that secures all uses of Generative AI in the organization: from tools used by your employees to your customer-facing apps.
DeepSource
DeepSource is a Unified DevSecOps Platform that secures the entire development lifecycle with static analysis and AI. It offers code quality and SAST, open-source security, and is trusted by over 6,000 companies. The platform helps in finding and fixing security vulnerabilities before code is merged, with a low false-positive rate and customizable security gates for pull requests. DeepSource is built for modern software development, providing features like Autofix™ AI, code coverage, and integrations with popular tools like Jira and GitHub Issues. It offers detailed reports, issue suppression, and metric thresholds to ensure clean and secure code shipping.
PROTECTSTAR
PROTECTSTAR is an AI-powered cybersecurity application that offers Secure Erasure, Anti Spy, Antivirus AI, and Firewall AI features to protect users from cyber threats. With a focus on privacy and security, PROTECTSTAR aims to provide innovative products using Artificial Intelligence technology. The application has been trusted by over 7 million satisfied users globally and is known for its outstanding detection rate of 99.956%. PROTECTSTAR is committed to environmental sustainability and energy efficiency, as evidenced by its dark mode feature to reduce energy consumption and become CO2-neutral.
ZeroThreat
ZeroThreat is a web app and API security scanner that helps businesses identify and fix vulnerabilities in their web applications and APIs. It uses a combination of static and dynamic analysis techniques to scan for a wide range of vulnerabilities, including OWASP Top 10, CWE Top 25, and SANS Top 25. ZeroThreat also provides continuous monitoring and alerting, so businesses can stay on top of new vulnerabilities as they emerge.
SMshrimant
SMshrimant is a personal website belonging to a Bug Bounty Hunter, Security Researcher, Penetration Tester, and Ethical Hacker. The website showcases the creator's skills and experiences in the field of cybersecurity, including bug hunting, security vulnerability reporting, open-source tool development, and participation in Capture The Flag competitions. Visitors can learn about the creator's projects, achievements, and contact information for inquiries or collaborations.
Glog
Glog is an AI application focused on making software more secure by providing remediation advice for security vulnerabilities in software code based on context. It is capable of automatically fixing vulnerabilities, thus reducing security risks and protecting against cyber attacks. The platform utilizes machine learning and AI to enhance software security and agility, ensuring system reliability, integrity, and safety.
Sider.ai
Sider.ai is an AI-powered platform that focuses on security verification for online connections. It ensures a safe browsing experience by reviewing the security of your connection before proceeding. The platform uses advanced algorithms to detect and prevent potential threats, providing users with peace of mind while browsing the internet.
Escape
Escape is an AI-powered Dynamic Application Security Testing (DAST) tool designed to work seamlessly with modern technology stacks, focusing on testing business logic and helping developers remediate vulnerabilities efficiently. It provides a comprehensive platform for API security, including API discovery, security testing, and GraphQL support. Escape offers features such as AI-powered DAST, API discovery & security, business logic security testing, CI/CD integration, and tailored remediations. The tool aims to streamline security workflows, improve risk reduction, and simplify compliance management for various industries.
For similar tasks

Huntr
Huntr is the world's first bug bounty platform for AI/ML. It provides a single place for security researchers to submit vulnerabilities, ensuring the security and stability of AI/ML applications, including those powered by Open Source Software (OSS).
AlgorithmWatch
AlgorithmWatch is a non-governmental, non-profit organization based in Berlin and Zurich. They aim to create a world where algorithms and Artificial Intelligence (AI) strengthen justice, human rights, democracy, and sustainability. The organization conducts research, advocacy, and awareness campaigns to address the ethical implications and societal impacts of AI technologies. Through publications, projects, and events, AlgorithmWatch strives to promote transparency, accountability, and fairness in the development and deployment of AI systems.
For similar jobs

Huntr
Huntr is the world's first bug bounty platform for AI/ML. It provides a single place for security researchers to submit vulnerabilities, ensuring the security and stability of AI/ML applications, including those powered by Open Source Software (OSS).

SMshrimant
SMshrimant is a personal website belonging to a Bug Bounty Hunter, Security Researcher, Penetration Tester, and Ethical Hacker. The website showcases the creator's skills and experiences in the field of cybersecurity, including bug hunting, security vulnerability reporting, open-source tool development, and participation in Capture The Flag competitions. Visitors can learn about the creator's projects, achievements, and contact information for inquiries or collaborations.
Equixly
Equixly is an AI-powered application designed to help users secure their APIs by identifying vulnerabilities and weaknesses through continuous security testing. The platform offers features such as scalable API PenTesting, attack simulation, mapping of attack surfaces, compliance simplification, and data exposure minimization. Equixly aims to streamline the process of identifying and fixing API security risks, ultimately enabling users to release secure code faster and reduce their attack surface.
Binary Vulnerability Analysis
The website offers an AI-powered binary vulnerability scanner that allows users to upload a binary file for analysis. The tool decompiles the executable, removes filler, cleans, formats, and checks for historical vulnerabilities. It generates function-wise embeddings using a finetuned CodeT5+ Embedding model and checks for similarities against the DiverseVul Dataset. The tool also utilizes SemGrep to check for vulnerabilities in the binary file.
Pentest Copilot
Pentest Copilot by BugBase is an ultimate ethical hacking assistant that guides users through each step of the hacking journey, from analyzing web apps to root shells. It eliminates redundant research, automates payload and command generation, and provides intelligent contextual analysis to save time. The application excels at data extraction, privilege escalation, lateral movement, and leaving no trace behind. With features like secure VPN integration, total control over sessions, parallel command processing, and flexibility to choose between local or cloud execution, Pentest Copilot offers a seamless and efficient hacking experience without the need for Kali Linux installation.
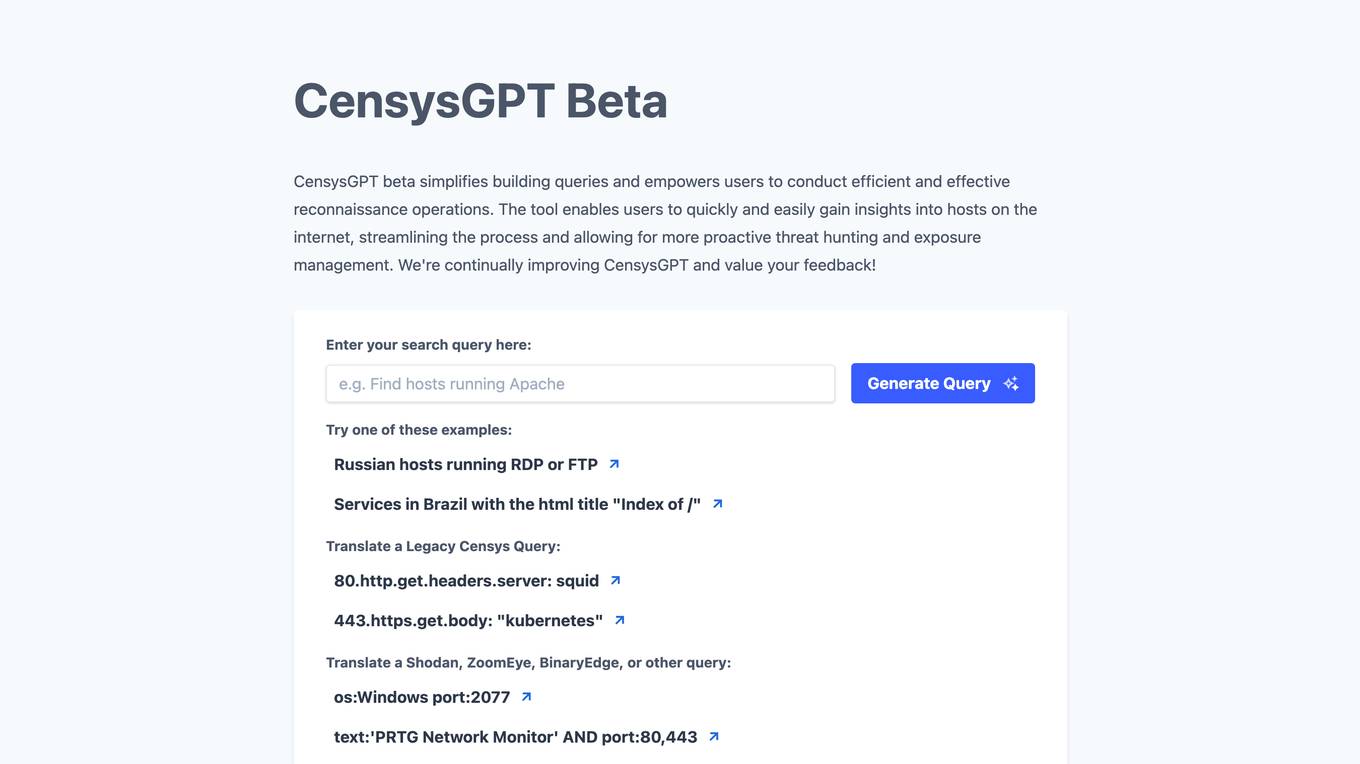
CensysGPT Beta
CensysGPT Beta is a tool that simplifies building queries and empowers users to conduct efficient and effective reconnaissance operations. It enables users to quickly and easily gain insights into hosts on the internet, streamlining the process and allowing for more proactive threat hunting and exposure management.

Qwiet AI
Qwiet AI is a code vulnerability detection platform that accelerates secure coding by uncovering, prioritizing, and generating fixes for top vulnerabilities with a single scan. It offers features such as AI-enhanced SAST, contextual SCA, AI AutoFix, Container Security, SBOM, and Secrets detection. Qwiet AI helps InfoSec teams in companies to accurately pinpoint and autofix risks in their code, reducing false positives and remediation time. The platform provides a unified vulnerability dashboard, prioritizes risks, and offers tailored fix suggestions based on the full context of the code.
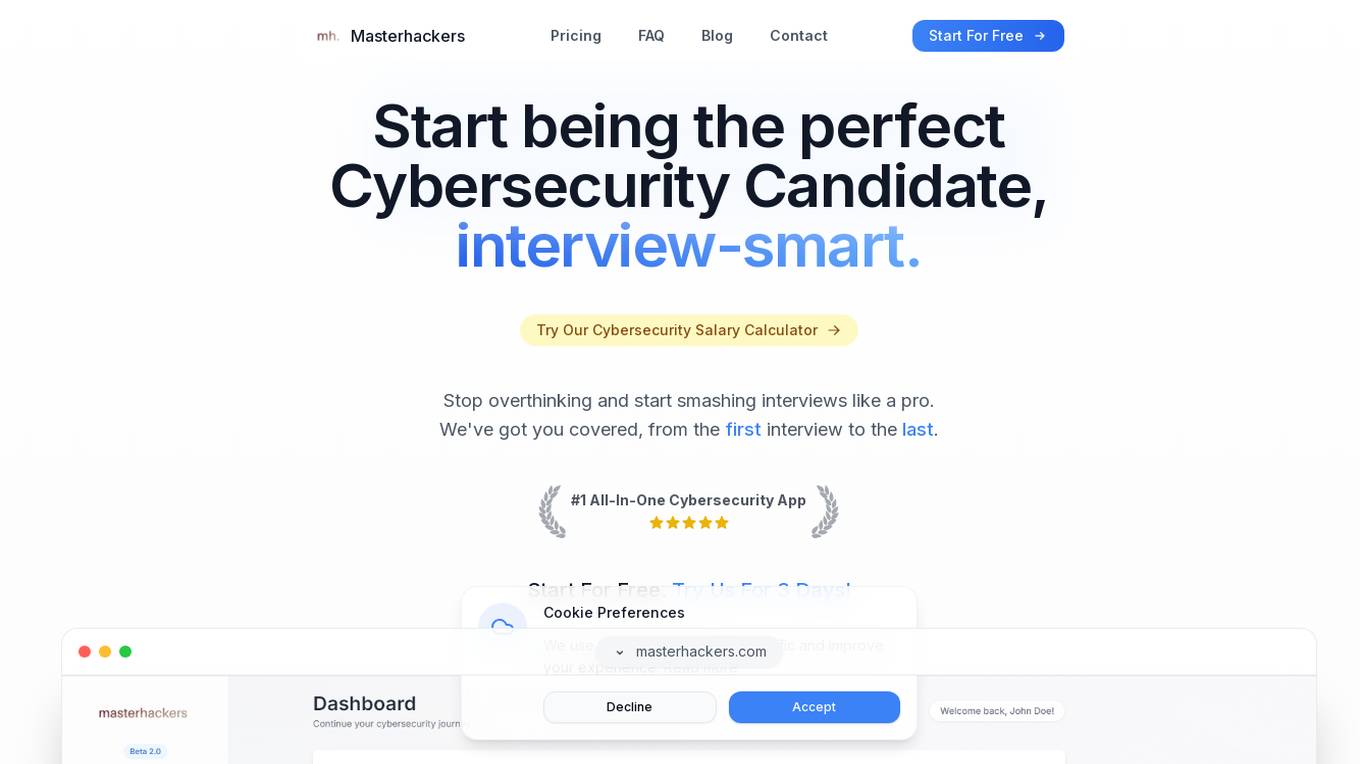
Masterhackers
Masterhackers is an all-in-one cybersecurity application designed to help cybersecurity professionals and students prepare for certifications and interviews. The platform offers a comprehensive set of tools and resources, including practice tests, flashcards, mock interviews, and personalized feedback with AI. Trusted by students worldwide, Masterhackers aims to enhance users' cybersecurity skills and knowledge through interactive learning experiences.
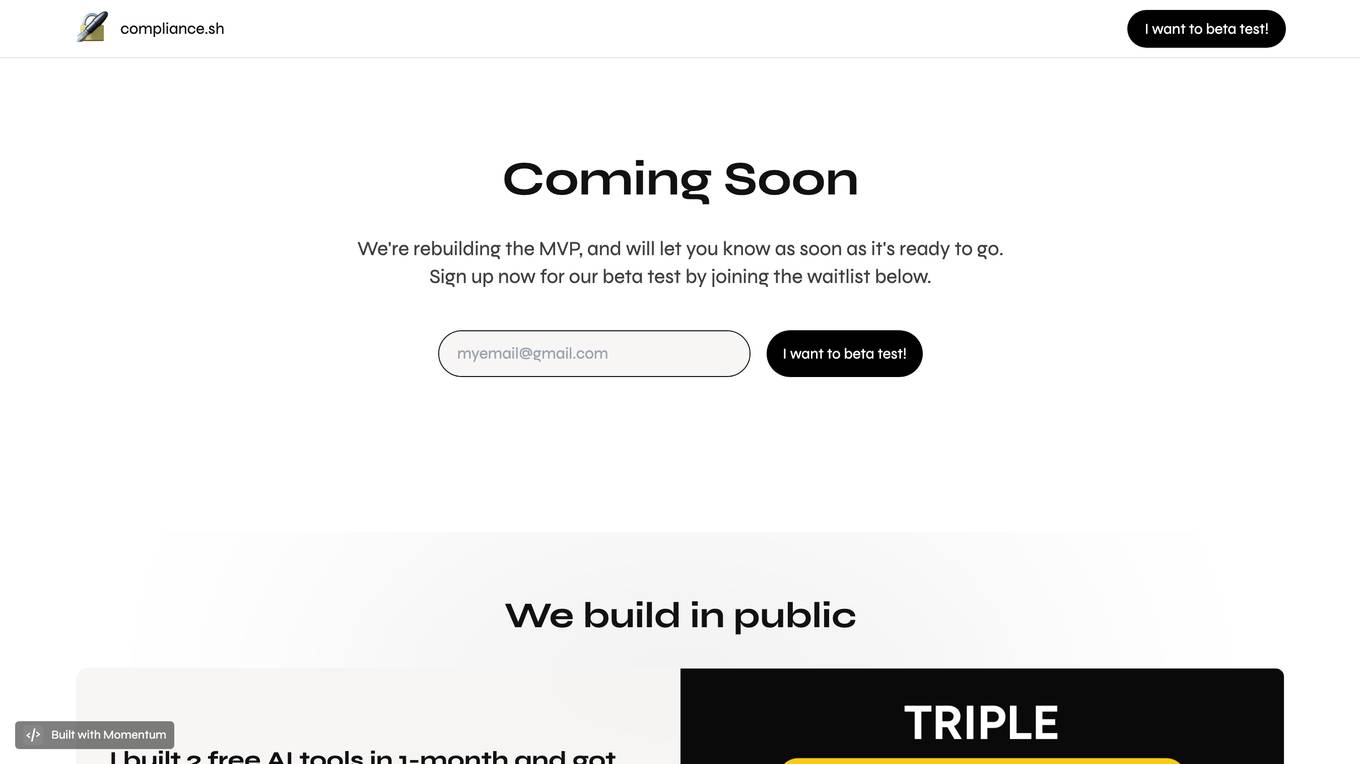
Compliance.sh
Compliance.sh is a website that provides services related to compliance and privacy. It offers tools and resources to help individuals and businesses ensure they are following regulations and protecting sensitive information. The platform covers a wide range of compliance topics and provides guidance on best practices to maintain trust and security. Users can access information in multiple languages and receive technical support for any inquiries.