Best AI tools for< vulnerability detection >
17 - AI tool Sites
GitHub
GitHub is the world's leading AI-powered developer platform. It provides a suite of tools that help developers build, ship, and maintain software. GitHub's AI capabilities are used to power a variety of features, including code completion, code review, and vulnerability detection.
BigBear.ai
BigBear.ai is an AI-powered decision intelligence solutions provider that offers services across various industries including Government & Defense, Manufacturing & Warehouse Operations, Healthcare & Life Sciences. They specialize in optimizing operational efficiency, force deployment, supply chain management, autonomous systems management, and vulnerability detection. Their solutions are designed to improve situational awareness, streamline production processes, and enhance patient care delivery settings.

Smaty.xyz
Smaty.xyz is a comprehensive platform that provides a suite of tools for code generation and security auditing. With Smaty.xyz, developers can quickly and easily generate high-quality code in multiple programming languages, ensuring consistency and reducing development time. Additionally, Smaty.xyz offers robust security auditing capabilities, enabling developers to identify and address vulnerabilities in their code, mitigating risks and enhancing the overall security of their applications.
Endor Labs
Endor Labs is an AI-powered software supply chain security solution that helps organizations manage their software bills of materials (SBOM), secure their open source dependencies, optimize CI/CD pipeline security, and enhance application security with secret detection. The platform offers advanced features such as AI-assisted OSS selection, compliance management, reachability-based SCA, and repository security posture management. Endor Labs aims to streamline security processes, reduce false positives, and provide actionable insights to improve software supply chain security.

MobiHeals
MobiHeals is a comprehensive mobile application security testing platform that offers cloud-based static and dynamic analysis for vulnerability assessment. It helps in detecting security vulnerabilities and quality issues in mobile applications at different stages of development, testing, and operation. The platform is cost-efficient, scalable, and compliant with global cybersecurity guidelines, providing actionable reports and real source code suggestions for quick fixes. MobiHeals aims to deliver trust by ensuring the security of your customer's mobile apps.
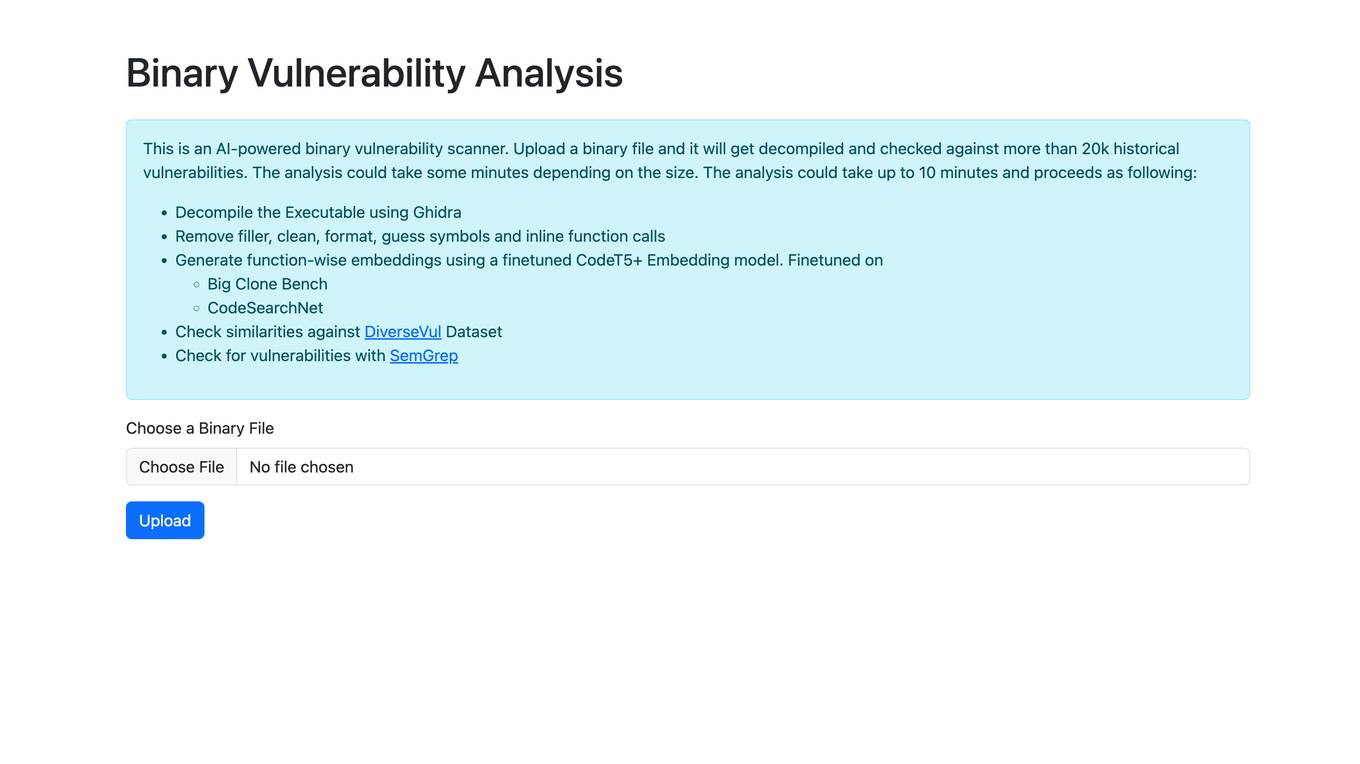
Binary Vulnerability Analysis
Binary Vulnerability Analysis is an AI-powered binary vulnerability scanner. It decompiles a binary file and checks it against more than 20k historical vulnerabilities. The analysis could take up to 10 minutes and proceeds as following: Decompile the Executable using Ghidra Remove filler, clean, format, guess symbols and inline function calls Generate function-wise embeddings using a finetuned CodeT5+ Embedding model. Finetuned on Big Clone Bench CodeSearchNet Check similarities against DiverseVul Dataset Check for vulnerabilities with SemGrep
OpenBuckets
OpenBuckets is a web application designed to help users find and secure open buckets in cloud storage systems. It provides a user-friendly interface for scanning and identifying publicly accessible buckets, allowing users to take necessary actions to secure their data. With OpenBuckets, users can easily detect potential security risks and protect their sensitive information stored in cloud storage. The application is a valuable tool for individuals and organizations looking to enhance their data security measures in the cloud.
Huntr
Huntr is the world's first bug bounty platform for AI/ML. It provides a single place for security researchers to submit vulnerabilities, ensuring the security and stability of AI/ML applications, including those powered by Open Source Software (OSS).
CensysGPT Beta
CensysGPT Beta is a tool that simplifies building queries and empowers users to conduct efficient and effective reconnaissance operations. It enables users to quickly and easily gain insights into hosts on the internet, streamlining the process and allowing for more proactive threat hunting and exposure management.
Protect AI
Protect AI is a comprehensive platform designed to secure AI systems by providing visibility and manageability to detect and mitigate unique AI security threats. The platform empowers organizations to embrace a security-first approach to AI, offering solutions for AI Security Posture Management, ML model security enforcement, AI/ML supply chain vulnerability database, LLM security monitoring, and observability. Protect AI aims to safeguard AI applications and ML systems from potential vulnerabilities, enabling users to build, adopt, and deploy AI models confidently and at scale.
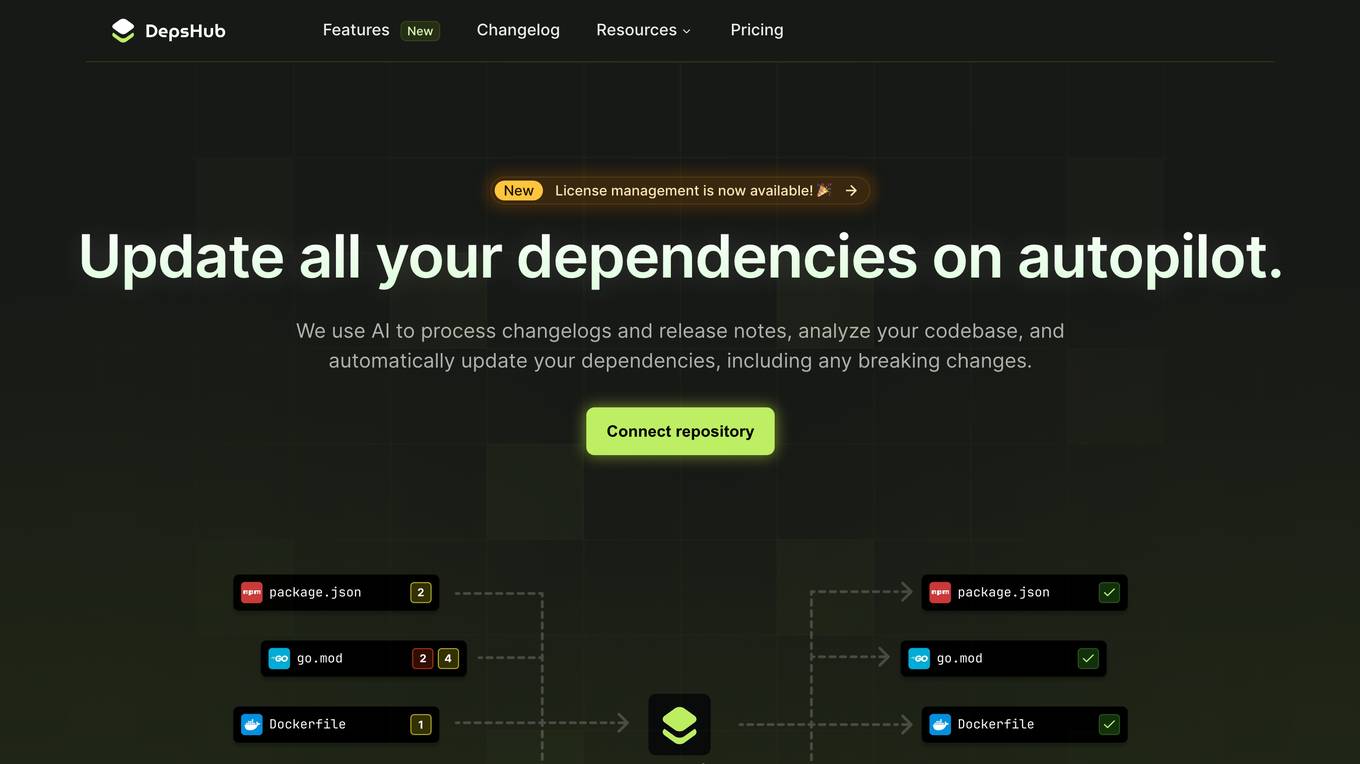
DepsHub
DepsHub is an AI-powered tool designed to simplify dependency updates for software development teams. It offers features such as automatic dependency updates, license checks, and security vulnerability scanning. The tool analyzes library changelogs, release notes, and codebases to automatically update dependencies, including handling breaking changes. DepsHub provides noise-free dependency management, cross-repository overview, license compliance, and security alerts. It helps users save time by monitoring and updating dependencies efficiently, supporting various languages and frameworks. The tool integrates with popular platforms like Github, Gitlab, Bitbucket, and offers features like automatic version bump, multiplatform support, and workspace overview.
Equixly
Equixly is an AI-powered virtual hacker tool designed to secure APIs by identifying and fixing vulnerabilities in real-time. It helps users eliminate blind spots by continuously scanning APIs for flaws, making integration less time-consuming and enabling faster release of secure code. Equixly offers scalable API penetration testing, rapid remediation, and attack simulation based on OWASP Top 10 API risks. It provides inventory mapping of API landscapes, simplifies compliance tracking, and minimizes data exposure. Equixly is a comprehensive solution for enhancing API security and ensuring regulatory compliance.
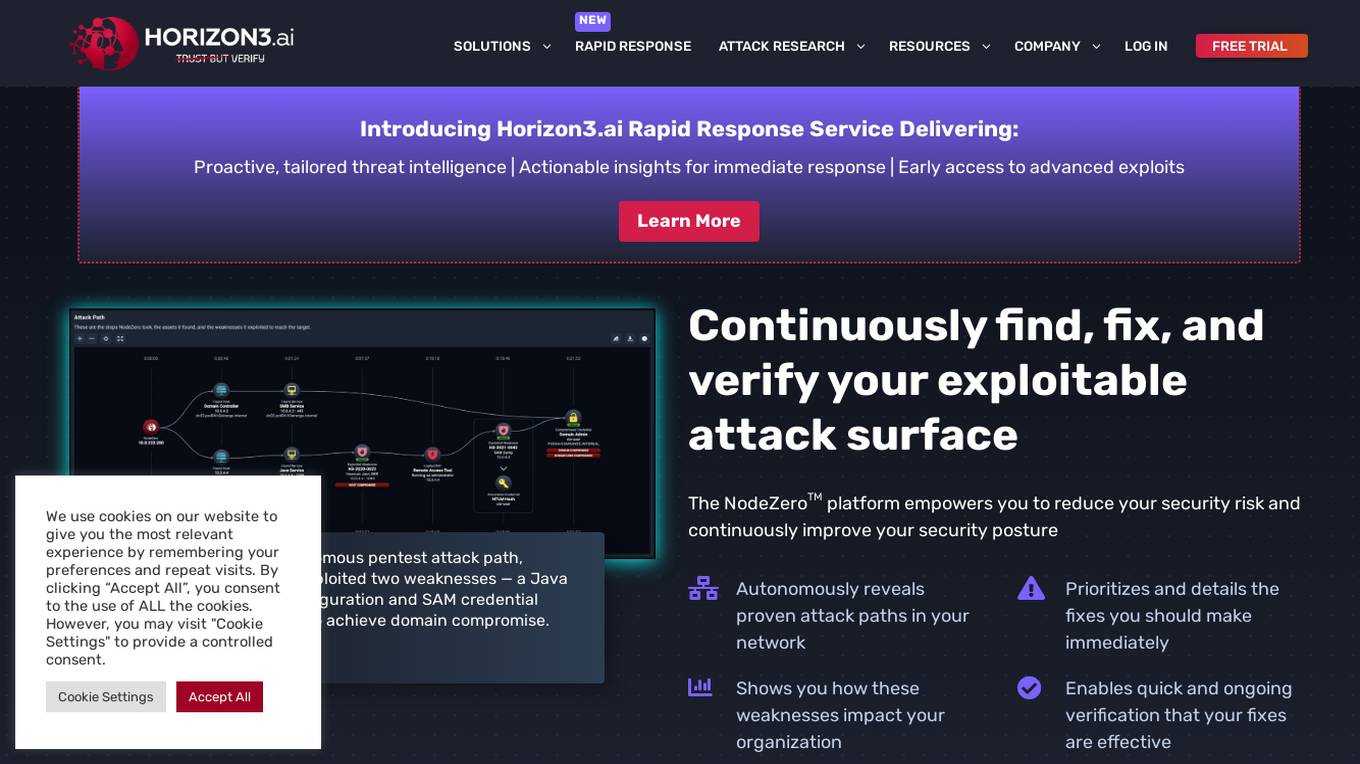
NodeZero™ Platform
Horizon3.ai Solutions offers the NodeZero™ Platform, an AI-powered autonomous penetration testing tool designed to enhance cybersecurity measures. The platform combines expert human analysis by Offensive Security Certified Professionals with automated testing capabilities to streamline compliance processes and proactively identify vulnerabilities. NodeZero empowers organizations to continuously assess their security posture, prioritize fixes, and verify the effectiveness of remediation efforts. With features like internal and external pentesting, rapid response capabilities, AD password audits, phishing impact testing, and attack research, NodeZero is a comprehensive solution for large organizations, ITOps, SecOps, security teams, pentesters, and MSSPs. The platform provides real-time reporting, integrates with existing security tools, reduces operational costs, and helps organizations make data-driven security decisions.
ZeroThreat
ZeroThreat is a web app and API security scanner that helps businesses identify and fix vulnerabilities in their web applications and APIs. It uses a combination of static and dynamic analysis techniques to scan for a wide range of vulnerabilities, including OWASP Top 10, CWE Top 25, and SANS Top 25. ZeroThreat also provides continuous monitoring and alerting, so businesses can stay on top of new vulnerabilities as they emerge.
Pixeebot
Pixeebot is an automated product security engineer that helps developers fix vulnerabilities, harden code, squash bugs, and improve code quality. It integrates with your existing workflow and can be used locally via CLI or through the GitHub app. Pixeebot is powered by the open source Codemodder framework, which allows you to build your own custom codemods.
VIDOC
VIDOC is an AI-powered security engineer that automates code review and penetration testing. It continuously scans and reviews code to detect and fix security issues, helping developers deliver secure software faster. VIDOC is easy to use, requiring only two lines of code to be added to a GitHub Actions workflow. It then takes care of the rest, providing developers with a tailored code solution to fix any issues found.
Pentest Copilot
Pentest Copilot is an AI-powered assistant for penetration testers. It provides real-time guidance and recommendations, helping testers to identify and exploit vulnerabilities more efficiently. Pentest Copilot is designed to be used alongside existing penetration testing tools and techniques, and it can be customized to fit the specific needs of each tester.
20 - Open Source AI Tools
trickPrompt-engine
This repository contains a vulnerability mining engine based on GPT technology. The engine is designed to identify logic vulnerabilities in code by utilizing task-driven prompts. It does not require prior knowledge or fine-tuning and focuses on prompt design rather than model design. The tool is effective in real-world projects and should not be used for academic vulnerability testing. It supports scanning projects in various languages, with current support for Solidity. The engine is configured through prompts and environment settings, enabling users to scan for vulnerabilities in their codebase. Future updates aim to optimize code structure, add more language support, and enhance usability through command line mode. The tool has received a significant audit bounty of $50,000+ as of May 2024.

watchtower
AIShield Watchtower is a tool designed to fortify the security of AI/ML models and Jupyter notebooks by automating model and notebook discoveries, conducting vulnerability scans, and categorizing risks into 'low,' 'medium,' 'high,' and 'critical' levels. It supports scanning of public GitHub repositories, Hugging Face repositories, AWS S3 buckets, and local systems. The tool generates comprehensive reports, offers a user-friendly interface, and aligns with industry standards like OWASP, MITRE, and CWE. It aims to address the security blind spots surrounding Jupyter notebooks and AI models, providing organizations with a tailored approach to enhancing their security efforts.
Awesome-Code-LLM
Analyze the following text from a github repository (name and readme text at end) . Then, generate a JSON object with the following keys and provide the corresponding information for each key, in lowercase letters: 'description' (detailed description of the repo, must be less than 400 words,Ensure that no line breaks and quotation marks.),'for_jobs' (List 5 jobs suitable for this tool,in lowercase letters), 'ai_keywords' (keywords of the tool,user may use those keyword to find the tool,in lowercase letters), 'for_tasks' (list of 5 specific tasks user can use this tool to do,in lowercase letters), 'answer' (in english languages)
awesome-gpt-security
Awesome GPT + Security is a curated list of awesome security tools, experimental case or other interesting things with LLM or GPT. It includes tools for integrated security, auditing, reconnaissance, offensive security, detecting security issues, preventing security breaches, social engineering, reverse engineering, investigating security incidents, fixing security vulnerabilities, assessing security posture, and more. The list also includes experimental cases, academic research, blogs, and fun projects related to GPT security. Additionally, it provides resources on GPT security standards, bypassing security policies, bug bounty programs, cracking GPT APIs, and plugin security.

Academic_LLM_Sec_Papers
Academic_LLM_Sec_Papers is a curated collection of academic papers related to LLM Security Application. The repository includes papers sorted by conference name and published year, covering topics such as large language models for blockchain security, software engineering, machine learning, and more. Developers and researchers are welcome to contribute additional published papers to the list. The repository also provides information on listed conferences and journals related to security, networking, software engineering, and cryptography. The papers cover a wide range of topics including privacy risks, ethical concerns, vulnerabilities, threat modeling, code analysis, fuzzing, and more.
pint-benchmark
The Lakera PINT Benchmark provides a neutral evaluation method for prompt injection detection systems, offering a dataset of English inputs with prompt injections, jailbreaks, benign inputs, user-agent chats, and public document excerpts. The dataset is designed to be challenging and representative, with plans for future enhancements. The benchmark aims to be unbiased and accurate, welcoming contributions to improve prompt injection detection. Users can evaluate prompt injection detection systems using the provided Jupyter Notebook. The dataset structure is specified in YAML format, allowing users to prepare their datasets for benchmarking. Evaluation examples and resources are provided to assist users in evaluating prompt injection detection models and tools.

h4cker
This repository is a comprehensive collection of cybersecurity-related references, scripts, tools, code, and other resources. It is carefully curated and maintained by Omar Santos. The repository serves as a supplemental material provider to several books, video courses, and live training created by Omar Santos. It encompasses over 10,000 references that are instrumental for both offensive and defensive security professionals in honing their skills.
awesome-MLSecOps
Awesome MLSecOps is a curated list of open-source tools, resources, and tutorials for MLSecOps (Machine Learning Security Operations). It includes a wide range of security tools and libraries for protecting machine learning models against adversarial attacks, as well as resources for AI security, data anonymization, model security, and more. The repository aims to provide a comprehensive collection of tools and information to help users secure their machine learning systems and infrastructure.

LLM4SE
The collection is actively updated with the help of an internal literature search engine.
NeMo-Guardrails
NeMo Guardrails is an open-source toolkit for easily adding _programmable guardrails_ to LLM-based conversational applications. Guardrails (or "rails" for short) are specific ways of controlling the output of a large language model, such as not talking about politics, responding in a particular way to specific user requests, following a predefined dialog path, using a particular language style, extracting structured data, and more.

ps-fuzz
The Prompt Fuzzer is an open-source tool that helps you assess the security of your GenAI application's system prompt against various dynamic LLM-based attacks. It provides a security evaluation based on the outcome of these attack simulations, enabling you to strengthen your system prompt as needed. The Prompt Fuzzer dynamically tailors its tests to your application's unique configuration and domain. The Fuzzer also includes a Playground chat interface, giving you the chance to iteratively improve your system prompt, hardening it against a wide spectrum of generative AI attacks.
LLM-Tool-Survey
This repository contains a collection of papers related to tool learning with large language models (LLMs). The papers are organized according to the survey paper 'Tool Learning with Large Language Models: A Survey'. The survey focuses on the benefits and implementation of tool learning with LLMs, covering aspects such as task planning, tool selection, tool calling, response generation, benchmarks, evaluation, challenges, and future directions in the field. It aims to provide a comprehensive understanding of tool learning with LLMs and inspire further exploration in this emerging area.
FigStep
FigStep is a black-box jailbreaking algorithm against large vision-language models (VLMs). It feeds harmful instructions through the image channel and uses benign text prompts to induce VLMs to output contents that violate common AI safety policies. The tool highlights the vulnerability of VLMs to jailbreaking attacks, emphasizing the need for safety alignments between visual and textual modalities.

AutoAudit
AutoAudit is an open-source large language model specifically designed for the field of network security. It aims to provide powerful natural language processing capabilities for security auditing and network defense, including analyzing malicious code, detecting network attacks, and predicting security vulnerabilities. By coupling AutoAudit with ClamAV, a security scanning platform has been created for practical security audit applications. The tool is intended to assist security professionals with accurate and fast analysis and predictions to combat evolving network threats.
garak
Garak is a free tool that checks if a Large Language Model (LLM) can be made to fail in a way that is undesirable. It probes for hallucination, data leakage, prompt injection, misinformation, toxicity generation, jailbreaks, and many other weaknesses. Garak's a free tool. We love developing it and are always interested in adding functionality to support applications.
specification
OWASP CycloneDX is a full-stack Bill of Materials (BOM) standard that provides advanced supply chain capabilities for cyber risk reduction. The specification supports various types of Bill of Materials including Software, Hardware, Machine Learning, Cryptography, Manufacturing, and Operations. It also includes support for Vulnerability Disclosure Reports, Vulnerability Exploitability eXchange, and CycloneDX Attestations. CycloneDX helps organizations accurately inventory all components used in software development to identify risks, enhance transparency, and enable rapid impact analysis. The project is managed by the CycloneDX Core Working Group under the OWASP Foundation and is supported by the global information security community.
20 - OpenAI Gpts
Phoenix Vulnerability Intelligence GPT
Expert in analyzing vulnerabilities with ransomware focus with intelligence powered by Phoenix Security
WVA
Web Vulnerability Academy (WVA) is an interactive tutor designed to introduce users to web vulnerabilities while also providing them with opportunities to assess and enhance their knowledge through testing.
NVD - CVE Research Assistant
Expert in CVEs and cybersecurity vulnerabilities, providing precise information from the National Vulnerability Database.

VulnGPT
Your ally in navigating the CVE deluge. Expert insights for prioritizing and remediating vulnerabilities.
Security Testing Advisor
Ensures software security through comprehensive testing techniques.
Solidity Sage
Your personal Ethereum magician — Simply ask a question or provide a code sample for insights into vulnerabilities, gas optimizations, and best practices. Don't be shy to ask about tooling and legendary attacks.
🛡️ CodeGuardian Pro+ 🛡️
Your AI-powered sentinel for code! Scans for vulnerabilities, offers security tips, and educates on best practices in cybersecurity. 🔍🔐