Best AI tools for< Detect Cloud Security Threats >
20 - AI tool Sites
Cyguru
Cyguru is an all-in-one cloud-based AI Security Operation Center (SOC) that offers a comprehensive range of features for a robust and secure digital landscape. Its Security Operation Center is the cornerstone of its service domain, providing AI-Powered Attack Detection, Continuous Monitoring for Vulnerabilities and Misconfigurations, Compliance Assurance, SecPedia: Your Cybersecurity Knowledge Hub, and Advanced ML & AI Detection. Cyguru's AI-Powered Analyst promptly alerts users to any suspicious behavior or activity that demands attention, ensuring timely delivery of notifications. The platform is accessible to everyone, with up to three free servers and subsequent pricing that is more than 85% below the industry average.
Traceable
Traceable is an AI-driven application designed to enhance API security for Cloud-Native Apps. It collects API traffic across the application landscape and utilizes advanced context-based behavioral analytics AI engine to provide insights on APIs, data exposure, threat analytics, and forensics. The platform offers features for API cataloging, activity monitoring, endpoint details, ownership, vulnerabilities, protection against security events, testing, analytics, and more. Traceable also allows for role-based access control, policy configuration, data classification, and integration with third-party solutions for data collection and security. It is a comprehensive tool for API security and threat detection in modern cloud environments.
CloudDefense.AI
CloudDefense.AI is an industry-leading multi-layered Cloud Native Application Protection Platform (CNAPP) that safeguards cloud infrastructure and cloud-native apps with expertise, precision, and confidence. It offers comprehensive cloud security solutions, vulnerability management, compliance, and application security testing. The platform utilizes advanced AI technology to proactively detect and analyze real-time threats, ensuring robust protection for businesses against cyber threats.
Abnormal Security
Abnormal Security is an AI-powered platform that leverages superhuman understanding of human behavior to protect against email threats such as phishing, social engineering, and account takeovers. The platform is trusted by over 3,000 customers, including 25% of the Fortune 500 companies. Abnormal Security offers a comprehensive cloud email security solution, behavioral anomaly detection, SaaS security, and autonomous AI security agents to provide multi-layered protection against advanced email attacks. The platform is recognized as a leader in email security and AI-native security, delivering unmatched protection and reducing the risk of phishing attacks by 90%.
AquilaX
AquilaX is an AI-powered DevSecOps platform that simplifies security and accelerates development processes. It offers a comprehensive suite of security scanning tools, including secret identification, PII scanning, SAST, container scanning, and more. AquilaX is designed to integrate seamlessly into the development workflow, providing fast and accurate results by leveraging AI models trained on extensive datasets. The platform prioritizes developer experience by eliminating noise and false positives, making it a go-to choice for modern Secure-SDLC teams worldwide.
Palo Alto Networks
Palo Alto Networks is a cybersecurity company offering advanced security solutions powered by Precision AI to protect modern enterprises from cyber threats. The company provides network security, cloud security, and AI-driven security operations to defend against AI-generated threats in real time. Palo Alto Networks aims to simplify security and achieve better security outcomes through platformization, intelligence-driven expertise, and proactive monitoring of sophisticated threats.

Start Left® Security
Start Left® Security is an AI-driven application security posture management platform that empowers product teams to automate secure-by-design software from people to cloud. The platform integrates security into every facet of the organization, offering a unified solution that aligns with business goals, fosters continuous improvement, and drives innovation. Start Left® Security provides a gamified DevSecOps experience with comprehensive security capabilities like SCA, SBOM, SAST, DAST, Container Security, IaC security, ASPM, and more.
SentinelOne
SentinelOne is an advanced enterprise cybersecurity AI platform that offers a comprehensive suite of AI-powered security solutions for endpoint, cloud, and identity protection. The platform leverages artificial intelligence to anticipate threats, manage vulnerabilities, and protect resources across the entire enterprise ecosystem. With features such as Singularity XDR, Purple AI, and AI-SIEM, SentinelOne empowers security teams to detect and respond to cyber threats in real-time. The platform is trusted by leading enterprises worldwide and has received industry recognition for its innovative approach to cybersecurity.
SentinelOne
SentinelOne is an advanced enterprise cybersecurity AI platform that offers a comprehensive suite of AI-powered security solutions for endpoint, cloud, and identity protection. The platform leverages AI technology to anticipate threats, manage vulnerabilities, and protect resources across the enterprise ecosystem. SentinelOne provides real-time threat hunting, managed services, and actionable insights through its unified data lake, empowering security teams to respond effectively to cyber threats. With a focus on automation, efficiency, and value maximization, SentinelOne is a trusted cybersecurity solution for leading enterprises worldwide.
Darktrace
Darktrace is a cybersecurity platform that leverages AI technology to provide proactive protection against cyber threats. It offers cloud-native AI security solutions for networks, emails, cloud environments, identity protection, and endpoint security. Darktrace's AI Analyst investigates alerts at the speed and scale of AI, mimicking human analyst behavior. The platform also includes services such as 24/7 expert support and incident management. Darktrace's AI is built on a unique approach where it learns from the organization's data to detect and respond to threats effectively. The platform caters to organizations of all sizes and industries, offering real-time detection and autonomous response to known and novel threats.
SharkGate
SharkGate is an AI-driven cybersecurity platform that focuses on protecting websites from various cyber threats. The platform offers solutions for mobile security, password management, quantum computing threats, API security, and cloud security. SharkGate leverages artificial intelligence and machine learning to provide advanced threat detection and response capabilities, ensuring the safety and integrity of digital assets. The platform has received accolades for its innovative approach to cybersecurity and has secured funding from notable organizations.
CrowdStrike
CrowdStrike is a leading cybersecurity platform that uses artificial intelligence (AI) to protect businesses from cyber threats. The platform provides a unified approach to security, combining endpoint security, identity protection, cloud security, and threat intelligence into a single solution. CrowdStrike's AI-powered technology enables it to detect and respond to threats in real-time, providing businesses with the protection they need to stay secure in the face of evolving threats.
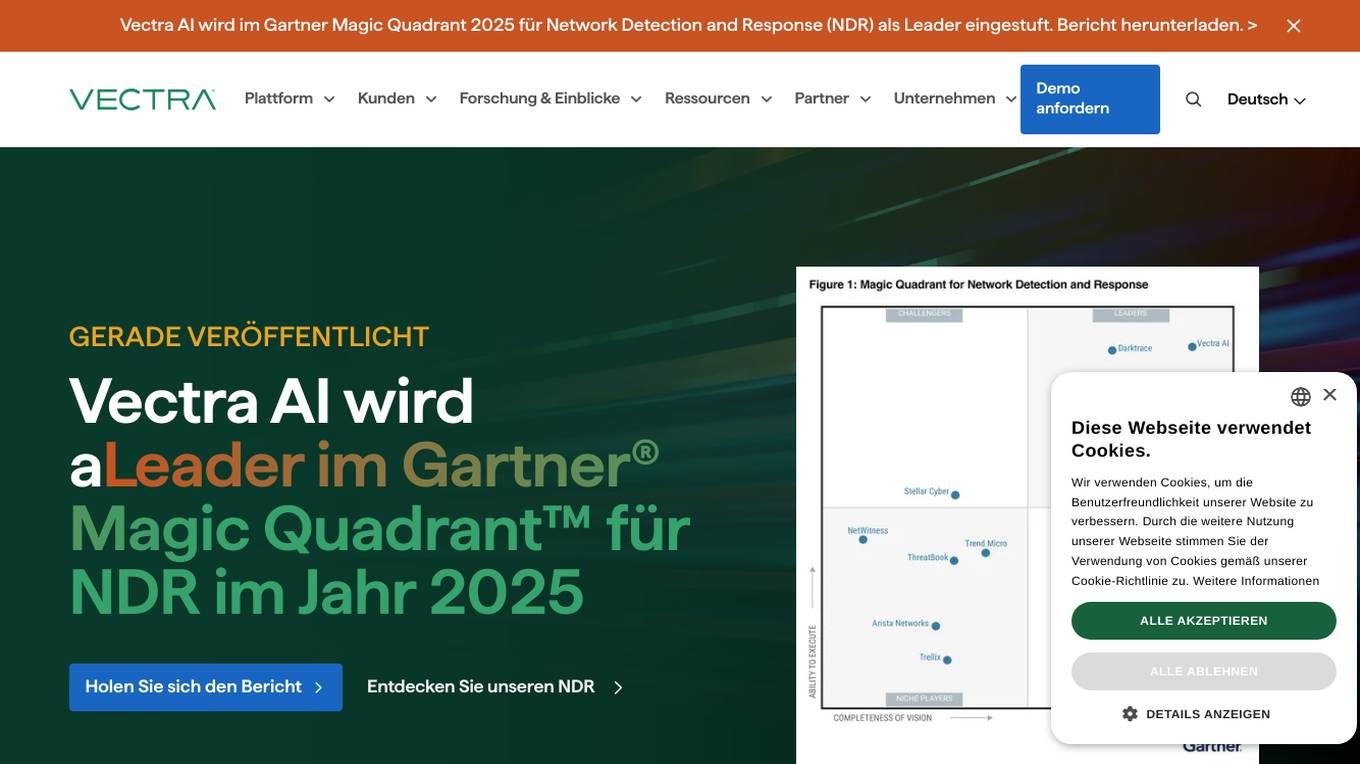
Vectra AI
Vectra AI is a leading cybersecurity AI application that stops attacks that others cannot. It is recognized in the Gartner Magic Quadrant 2025 for Network Detection and Response (NDR) as a leader. Vectra AI's platform protects modern networks from advanced threats by providing real-time attack signal intelligence and AI-driven detections. It equips security analysts with the information needed to quickly stop attacks across various security application scenarios. The application covers a wide range of security areas such as SOC modernization, SIEM optimization, IDS replacement, EDR extension, cloud resilience, and more.
CrowdStrike
CrowdStrike is a cloud-based cybersecurity platform that provides endpoint protection, threat intelligence, and incident response services. It uses artificial intelligence (AI) to detect and prevent cyberattacks. CrowdStrike's platform is designed to be scalable and easy to use, and it can be deployed on-premises or in the cloud. CrowdStrike has a global customer base of over 23,000 organizations, including many Fortune 500 companies.
Censornet
The website is an AI-powered cybersecurity platform that aims to empower and secure every user and every action. It provides total protection through an integrated cloud platform, offering features such as secure access to web and cloud apps, threat detection and mitigation, advanced data protection, secure remote worker solutions, and AI-powered security leveraging intelligence about user activity and devices. The platform helps businesses anticipate threats, manage vulnerabilities, and protect users worldwide.
Vectra AI
Vectra AI is an advanced AI-driven cybersecurity platform that helps organizations detect, prioritize, investigate, and respond to sophisticated cyber threats in real-time. The platform provides Attack Signal Intelligence to arm security analysts with the necessary intel to stop attacks fast. Vectra AI offers integrated signal for extended detection and response (XDR) across various domains such as network, identity, cloud, and endpoint security. Trusted by 1,500 enterprises worldwide, Vectra AI is known for its patented AI security solutions that deliver the best attack signal intelligence on the planet.
Exabeam
Exabeam is a cybersecurity and compliance platform that offers Security Information and Event Management (SIEM) solutions. The platform provides flexible choices for threat detection, investigation, and response, whether through cloud-based AI-driven solutions or on-premises SIEM deployments. Exabeam's AI-driven Security Operations Platform combines advanced threat detection capabilities with automation to deliver faster and more accurate TDIR. With features like UEBA, SOAR, and insider threat detection, Exabeam helps organizations improve security posture and optimize investments. The platform supports various industries and use cases, offering pre-built content, behavioral analytics, and context enrichment for enhanced threat coverage and compliance.
Varonis
Varonis is an AI-powered data security platform that provides end-to-end data security solutions for organizations. It offers automated outcomes to reduce risk, enforce policies, and stop active threats. Varonis helps in data discovery & classification, data security posture management, data-centric UEBA, data access governance, and data loss prevention. The platform is designed to protect critical data across multi-cloud, SaaS, hybrid, and AI environments.
VOLT AI
VOLT AI is a cloud-based enterprise security application that utilizes advanced AI technology to intercept threats in real-time. The application offers solutions for various industries such as education, corporate, and cities, focusing on perimeter security, medical emergencies, and weapons detection. VOLT AI provides features like unified cameras, video intelligence, real-time notifications, automated escalations, and digital twin creation for advanced situational awareness. The application aims to enhance safety and security by detecting security risks and notifying users promptly.
AI CERTs
The website page provides detailed information on AI CERTs, focusing on Google Cloud AI Security and AI Sustainability Strategies. It discusses the importance of AI in cybersecurity, sustainability, and government services. The content covers various topics such as the role of AI in preparing for cyber threats, the significance of AI in shaping a greener future, and the impact of AI on public sector operations. Additionally, it highlights the advantages of AI-driven solutions, the challenges faced in AI adoption, and the future implications of AI security wars.
0 - Open Source AI Tools
20 - OpenAI Gpts
News Bias Analyzer
Fetch and Analyze the Latest News! 📊💡 Get unbiased summaries, detailed bias graphs, and engaging word clouds. Dive into the world of news with a fresh perspective! 🌍📰 Our upgraded News Bias Analyzer GPT is your go-to for insightful analysis of the latest headlines and in-depth articles.
FallacyGPT
Detect logical fallacies and lapses in critical thinking to help avoid misinformation in the style of Socrates
AI Detector
AI Detector GPT is powered by Winston AI and created to help identify AI generated content. It is designed to help you detect use of AI Writing Chatbots such as ChatGPT, Claude and Bard and maintain integrity in academia and publishing. Winston AI is the most trusted AI content detector.
Plagiarism Checker
Plagiarism Checker GPT is powered by Winston AI and created to help identify plagiarized content. It is designed to help you detect instances of plagiarism and maintain integrity in academia and publishing. Winston AI is the most trusted AI and Plagiarism Checker.

BS Meter Realtime
Detects and measures information credibility. Provides a "BS Score" (0-100) based on content analysis for misinformation signs, including factual inaccuracies and sensationalist language. Real-time feedback.
Wowza Bias Detective
I analyze cognitive biases in scenarios and thoughts, providing neutral, educational insights.
Defender for Endpoint Guardian
To assist individuals seeking to learn about or work with Microsoft's Defender for Endpoint. I provide detailed explanations, step-by-step guides, troubleshooting advice, cybersecurity best practices, and demonstrations, all specifically tailored to Microsoft Defender for Endpoint.
Prompt Injection Detector
GPT used to classify prompts as valid inputs or injection attempts. Json output.
Blue Team Guide
it is a meticulously crafted arsenal of knowledge, insights, and guidelines that is shaped to empower organizations in crafting, enhancing, and refining their cybersecurity defenses
PBN Detector
A tool to help you decide if a website is part of a PBN or link network, created solely for link building. >> Get in touch with Gareth if you need a Freelance SEO for link building <<