Best AI tools for< identify cybersecurity risks >
20 - AI tool Sites
CyberRiskAI
CyberRiskAI is a cybersecurity risk assessment and audit tool that helps businesses identify and mitigate their cybersecurity risks. It offers a fast, accurate, and affordable service for businesses that want to communicate trust to customers. CyberRiskAI's comprehensive checklists and AI-powered assessments provide businesses with valuable insights into potential vulnerabilities, enabling them to prioritize security efforts and build trust with their partners. CyberRiskAI's all-in-one risk assessment template with checklist of controls, comprehensive cybersecurity audit & risk assessment report, and quick and easy to complete features make it a valuable tool for any organization that values the protection of their data and wants to ensure the sustainability of their business.

MLSecOps
MLSecOps is an AI tool designed to drive the field of MLSecOps forward through high-quality educational resources and tools. It focuses on traditional cybersecurity principles, emphasizing people, processes, and technology. The MLSecOps Community educates and promotes the integration of security practices throughout the AI & machine learning lifecycle, empowering members to identify, understand, and manage risks associated with their AI systems.
Concentric AI
Concentric AI is a Managed Data Security Posture Management tool that utilizes Semantic Intelligence to provide comprehensive data security solutions. The platform offers features such as autonomous data discovery, data risk identification, centralized remediation, easy deployment, and data security posture management. Concentric AI helps organizations protect sensitive data, prevent data loss, and ensure compliance with data security regulations. The tool is designed to simplify data governance and enhance data security across various data repositories, both in the cloud and on-premises.
Netify
Netify provides network intelligence and visibility. Its solution stack starts with a Deep Packet Inspection (DPI) engine that passively collects data on the local network. This lightweight engine identifies applications, protocols, hostnames, encryption ciphers, and other network attributes. The software can be integrated into network devices for traffic identification, firewalling, QoS, and cybersecurity. Netify's Informatics engine collects data from local DPI engines and uses the power of a public or private cloud to transform it into network intelligence. From device identification to cybersecurity risk detection, Informatics provides a way to take a proactive approach to manage network threats, bottlenecks, and usage. Lastly, Netify's Data Feeds provide data to help vendors understand how applications behave on the Internet.
AI or Not
AI or Not is an AI-powered tool that helps businesses and individuals detect AI-generated images and audio. It uses advanced machine learning algorithms to analyze content and determine the likelihood of AI manipulation. With AI or Not, users can protect themselves from fraud, misinformation, and other malicious activities involving AI-generated content.
Vectra AI
Vectra AI is a leading AI security platform that helps organizations stop advanced cyber attacks by providing an integrated signal for extended detection and response (XDR). The platform arms security analysts with real-time intelligence to detect, prioritize, investigate, and respond to threats across network, identity, cloud, and managed services. Vectra AI's AI-driven detections and Attack Signal Intelligence enable organizations to protect against various attack types and emerging threats, enhancing cyber resilience and reducing risks in critical infrastructure, cloud environments, and remote workforce scenarios. Trusted by over 1100 enterprises worldwide, Vectra AI is recognized for its expertise in AI security and its ability to stop sophisticated attacks that other technologies may miss.
Nametag
Nametag is an identity verification solution designed specifically for IT helpdesks. It helps businesses prevent social engineering attacks, account takeovers, and data breaches by verifying the identity of users at critical moments, such as password resets, MFA resets, and high-risk transactions. Nametag's unique approach to identity verification combines mobile cryptography, device telemetry, and proprietary AI models to provide unmatched security and better user experiences.
Immunifai
Immunifai is a cybersecurity company that provides AI-powered threat detection and response solutions. The company's mission is to make the world a safer place by protecting organizations from cyberattacks. Immunifai's platform uses machine learning and artificial intelligence to identify and respond to threats in real time. The company's solutions are used by a variety of organizations, including Fortune 500 companies, government agencies, and financial institutions.
Spot a Bot
Spot a Bot is an AI tool that estimates the number of bot accounts on Twitter by analyzing Twitter trends. Due to recent changes in Twitter's API policy, the tool is unable to provide daily trend analyses at the moment. Users can check today's trends, look for past trends, and choose trends from the UK, USA, or Germany. The tool provides statistics such as model accuracy and the total number of accounts and tweets analyzed.
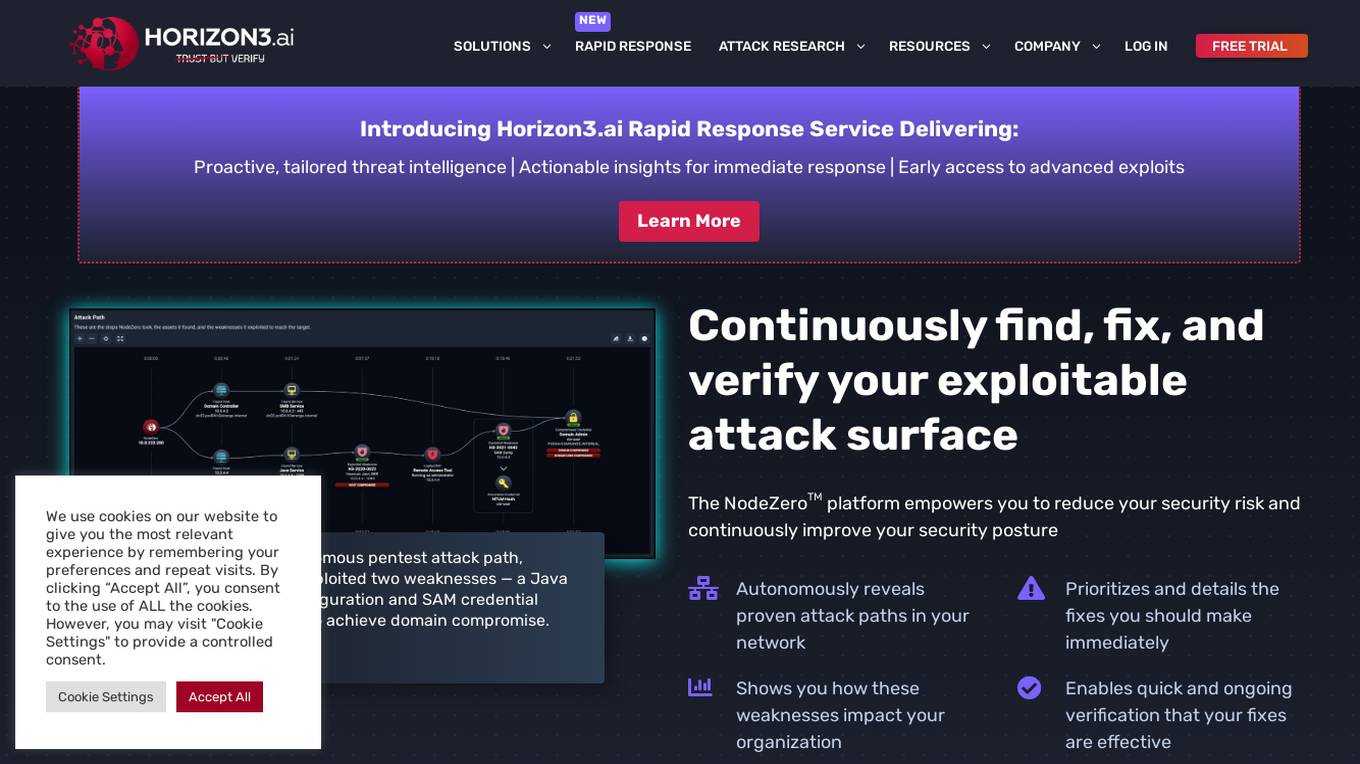
NodeZero™ Platform
Horizon3.ai Solutions offers the NodeZero™ Platform, an AI-powered autonomous penetration testing tool designed to enhance cybersecurity measures. The platform combines expert human analysis by Offensive Security Certified Professionals with automated testing capabilities to streamline compliance processes and proactively identify vulnerabilities. NodeZero empowers organizations to continuously assess their security posture, prioritize fixes, and verify the effectiveness of remediation efforts. With features like internal and external pentesting, rapid response capabilities, AD password audits, phishing impact testing, and attack research, NodeZero is a comprehensive solution for large organizations, ITOps, SecOps, security teams, pentesters, and MSSPs. The platform provides real-time reporting, integrates with existing security tools, reduces operational costs, and helps organizations make data-driven security decisions.
CrowdStrike
CrowdStrike is a cloud-based cybersecurity platform that provides endpoint protection, threat intelligence, and incident response services. It uses artificial intelligence (AI) to detect and prevent cyberattacks. CrowdStrike's platform is designed to be scalable and easy to use, and it can be deployed on-premises or in the cloud. CrowdStrike has a global customer base of over 23,000 organizations, including many Fortune 500 companies.
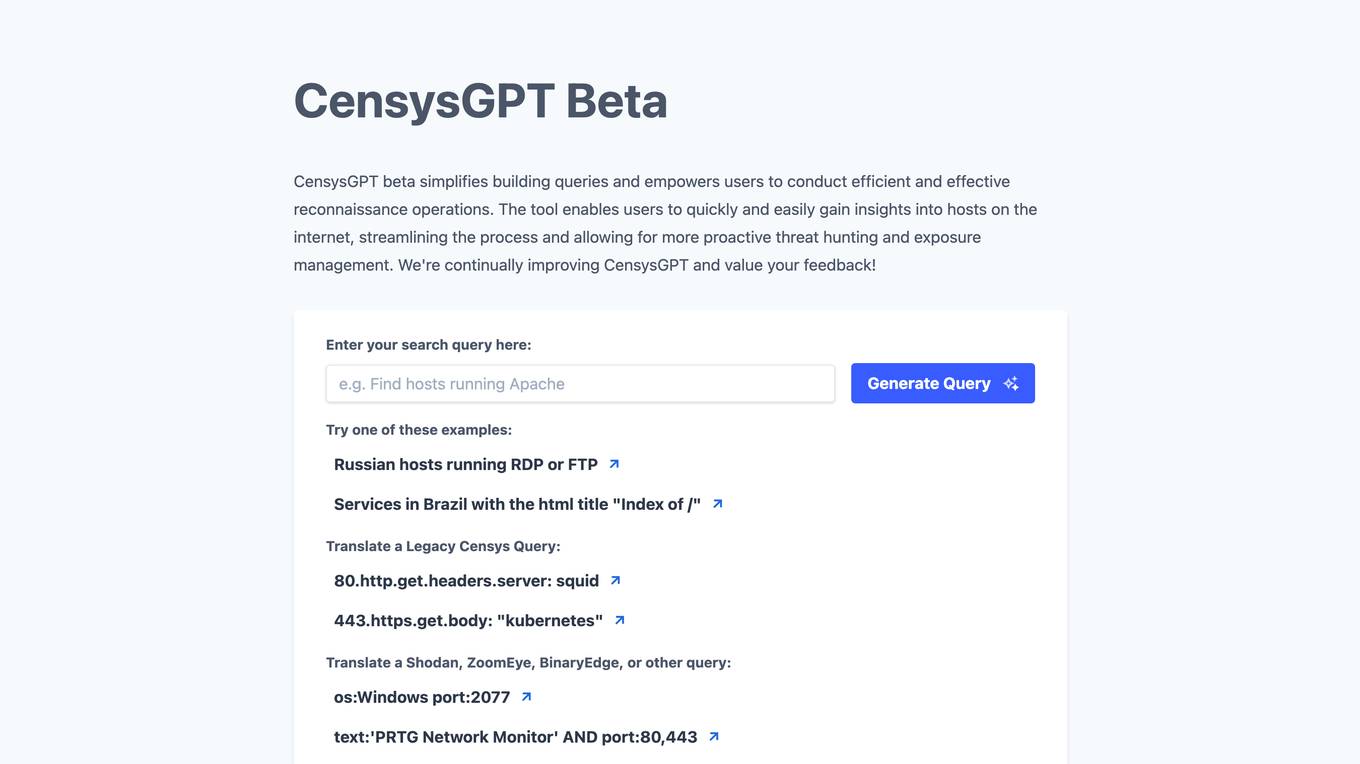
CensysGPT Beta
CensysGPT Beta is a tool that simplifies building queries and empowers users to conduct efficient and effective reconnaissance operations. It enables users to quickly and easily gain insights into hosts on the internet, streamlining the process and allowing for more proactive threat hunting and exposure management.
BladeRunner
BladeRunner is a browser plug-in that highlights AI-generated text directly on the page. It helps users detect AI-generated content in various online platforms, such as social media, news, education, e-commerce, and government communications. In the age of AI, where distinguishing between human and AI-generated content is challenging, BladeRunner serves as a tool to aid users in identifying AI impostors and maintaining accuracy in digital interactions.
Link Shield
Link Shield is an AI-powered malicious URL detection API platform that helps protect online security. It utilizes advanced machine learning algorithms to analyze URLs and identify suspicious activity, safeguarding users from phishing scams, malware, and other harmful threats. The API is designed for ease of integration, affordability, and flexibility, making it accessible to developers of all levels. Link Shield empowers businesses to ensure the safety and security of their applications and online communities.
Deepfake Detector
Deepfake Detector is an AI tool designed to identify deepfake audio and video content with 92% model accuracy. It offers a reliable means to filter out AI-generated content, providing probabilities for further investigation. The tool helps individuals and businesses protect themselves from potential deepfake scams by verifying the authenticity of audio messages, calls, and meetings. With features like AI Noise Remover and easy API integration, Deepfake Detector ensures the highest accuracy in detecting deepfakes and protecting users from financial losses.
AI Voice Detector
AI Voice Detector is an AI tool designed to protect individuals and businesses from audio manipulation and AI voice frauds. It offers a solution to identify whether an audio was generated by an AI voice or a human voice. The tool can be accessed through a browser extension or by uploading audio files. It provides features such as detecting voices from all voice cloning platforms, removing background noise, analyzing short audios, and being used as a browser extension. AI Voice Detector helps individuals and businesses prevent financial losses due to AI voice scams by verifying the authenticity of voice messages, calls, and meetings.
Atom.com
Atom.com is a website that utilizes Cloudflare's security service to protect itself from online attacks. Users may encounter a block when certain actions trigger the security solution. In such cases, users can contact the site owner to resolve the issue by providing details of the incident. Cloudflare Ray ID is used to identify the specific block trigger. The website focuses on maintaining performance and security for its users.
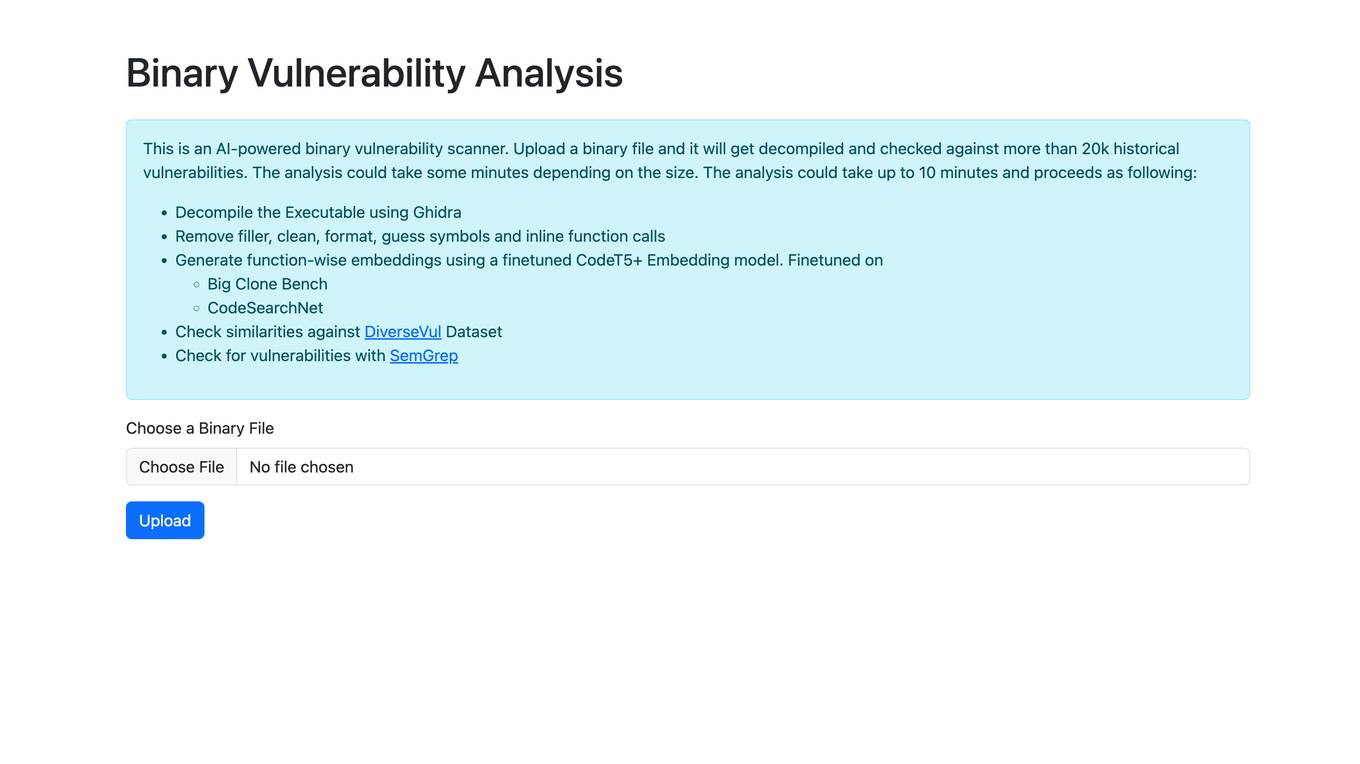
Binary Vulnerability Analysis
The website offers an AI-powered binary vulnerability scanner that allows users to upload a binary file for analysis. The tool decompiles the executable, removes filler, formats the code, and checks for vulnerabilities by comparing against a database of historical vulnerabilities. It utilizes a finetuned CodeT5+ Embedding model to generate function-wise embeddings and checks for similarities against the DiverseVul Dataset. The tool also employs SemGrep to identify vulnerabilities in the code.
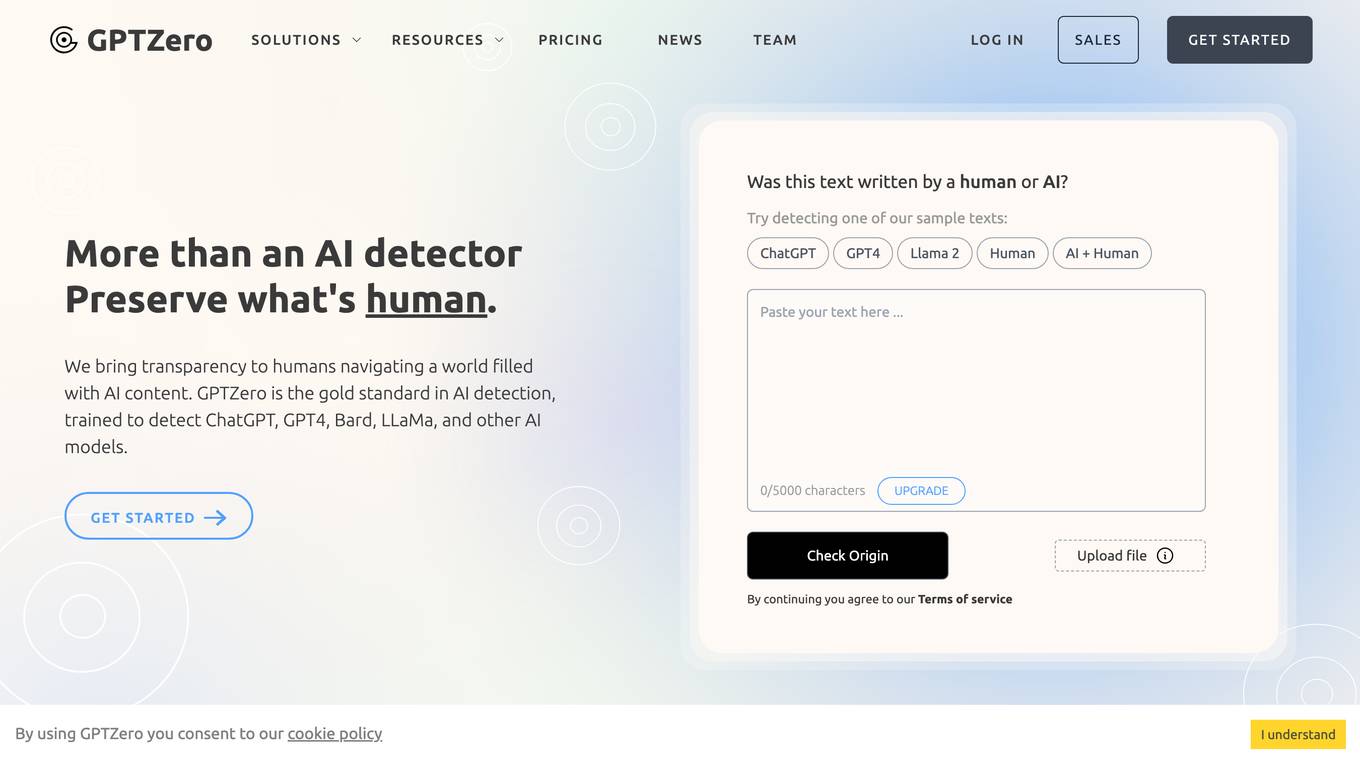
GPTZero
GPTZero is a leading AI detector designed to identify text generated by large language models like ChatGPT, GPT-4, Bard, LLaMa, and others. It utilizes advanced technology to analyze writing patterns and determine the likelihood of AI involvement. GPTZero provides detailed insights into the writing process, highlighting sections potentially written by AI. With its user-friendly interface and various integrations, GPTZero empowers educators, students, writers, recruiters, and cybersecurity professionals to navigate the world of AI-generated content with confidence.
Government Technology Newsletters
Government Technology provides email newsletters that deliver the latest news and updates on various topics relevant to government leaders, including technology trends, artificial intelligence, cybersecurity, digital communities, emergency management, government business, higher education, and K-12 education. These newsletters aim to keep subscribers informed about critical developments and best practices in their respective fields.
20 - Open Source AI Tools
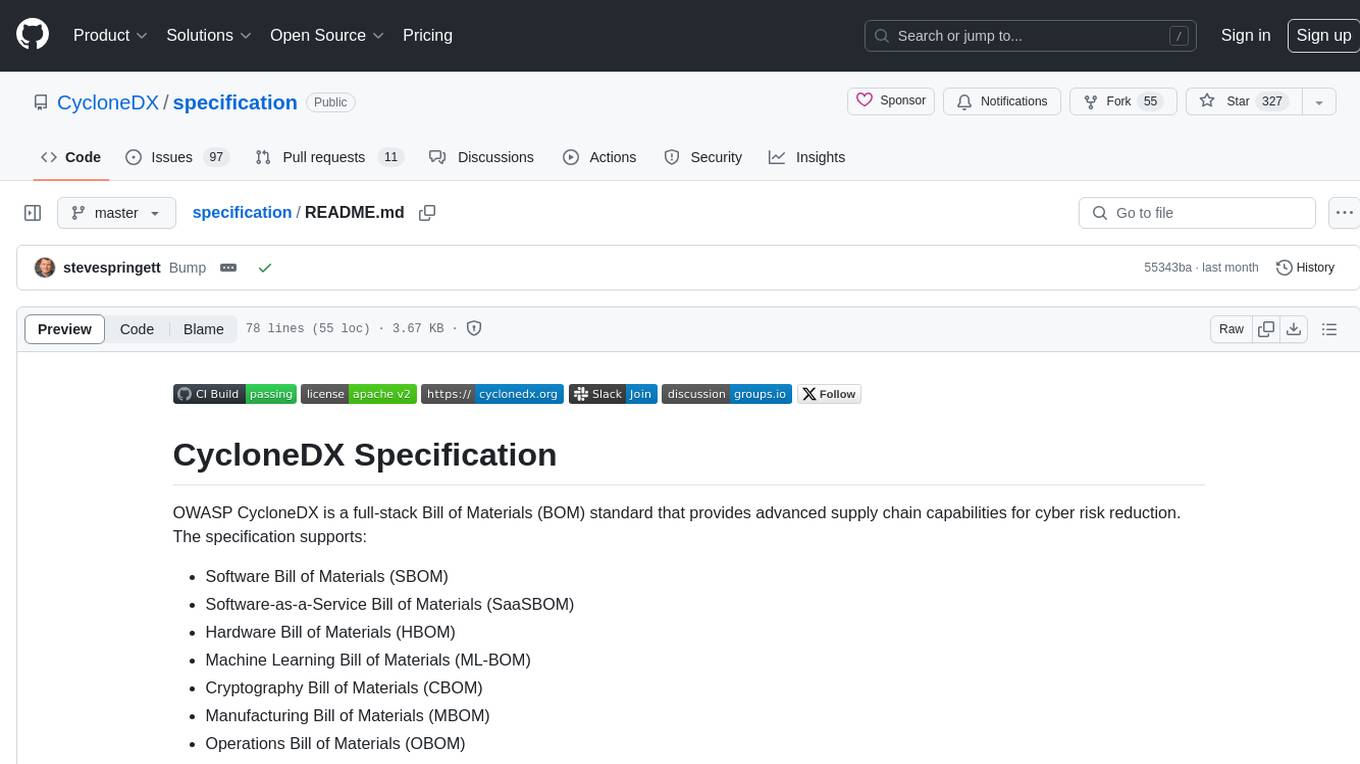
specification
OWASP CycloneDX is a full-stack Bill of Materials (BOM) standard that provides advanced supply chain capabilities for cyber risk reduction. The specification supports various types of Bill of Materials including Software, Hardware, Machine Learning, Cryptography, Manufacturing, and Operations. It also includes support for Vulnerability Disclosure Reports, Vulnerability Exploitability eXchange, and CycloneDX Attestations. CycloneDX helps organizations accurately inventory all components used in software development to identify risks, enhance transparency, and enable rapid impact analysis. The project is managed by the CycloneDX Core Working Group under the OWASP Foundation and is supported by the global information security community.

watchtower
AIShield Watchtower is a tool designed to fortify the security of AI/ML models and Jupyter notebooks by automating model and notebook discoveries, conducting vulnerability scans, and categorizing risks into 'low,' 'medium,' 'high,' and 'critical' levels. It supports scanning of public GitHub repositories, Hugging Face repositories, AWS S3 buckets, and local systems. The tool generates comprehensive reports, offers a user-friendly interface, and aligns with industry standards like OWASP, MITRE, and CWE. It aims to address the security blind spots surrounding Jupyter notebooks and AI models, providing organizations with a tailored approach to enhancing their security efforts.

last_layer
last_layer is a security library designed to protect LLM applications from prompt injection attacks, jailbreaks, and exploits. It acts as a robust filtering layer to scrutinize prompts before they are processed by LLMs, ensuring that only safe and appropriate content is allowed through. The tool offers ultra-fast scanning with low latency, privacy-focused operation without tracking or network calls, compatibility with serverless platforms, advanced threat detection mechanisms, and regular updates to adapt to evolving security challenges. It significantly reduces the risk of prompt-based attacks and exploits but cannot guarantee complete protection against all possible threats.
AiTreasureBox
AiTreasureBox is a versatile AI tool that provides a collection of pre-trained models and algorithms for various machine learning tasks. It simplifies the process of implementing AI solutions by offering ready-to-use components that can be easily integrated into projects. With AiTreasureBox, users can quickly prototype and deploy AI applications without the need for extensive knowledge in machine learning or deep learning. The tool covers a wide range of tasks such as image classification, text generation, sentiment analysis, object detection, and more. It is designed to be user-friendly and accessible to both beginners and experienced developers, making AI development more efficient and accessible to a wider audience.
admyral
Admyral is an open-source Cybersecurity Automation & Investigation Assistant that provides a unified console for investigations and incident handling, workflow automation creation, automatic alert investigation, and next step suggestions for analysts. It aims to tackle alert fatigue and automate security workflows effectively by offering features like workflow actions, AI actions, case management, alert handling, and more. Admyral combines security automation and case management to streamline incident response processes and improve overall security posture. The tool is open-source, transparent, and community-driven, allowing users to self-host, contribute, and collaborate on integrations and features.

cogai
The W3C Cognitive AI Community Group focuses on advancing Cognitive AI through collaboration on defining use cases, open source implementations, and application areas. The group aims to demonstrate the potential of Cognitive AI in various domains such as customer services, healthcare, cybersecurity, online learning, autonomous vehicles, manufacturing, and web search. They work on formal specifications for chunk data and rules, plausible knowledge notation, and neural networks for human-like AI. The group positions Cognitive AI as a combination of symbolic and statistical approaches inspired by human thought processes. They address research challenges including mimicry, emotional intelligence, natural language processing, and common sense reasoning. The long-term goal is to develop cognitive agents that are knowledgeable, creative, collaborative, empathic, and multilingual, capable of continual learning and self-awareness.
Evilginx3-Phishlets
This repository contains custom Evilginx phishlets that are meticulously crafted and updated for real-world applications. It also offers an advanced course, EvilGoPhish Mastery, focusing on phishing and smishing techniques using EvilGoPhish 3.0. The course complements the repository by providing in-depth guidance on deploying these scripts for red team phishing and smishing campaigns.
zippy
ZipPy is a research repository focused on fast AI detection using compression techniques. It aims to provide a faster approximation for AI detection that is embeddable and scalable. The tool uses LZMA and zlib compression ratios to indirectly measure the perplexity of a text, allowing for the detection of low-perplexity text. By seeding a compression stream with AI-generated text and comparing the compression ratio of the seed data with the sample appended, ZipPy can identify similarities in word choice and structure to classify text as AI or human-generated.
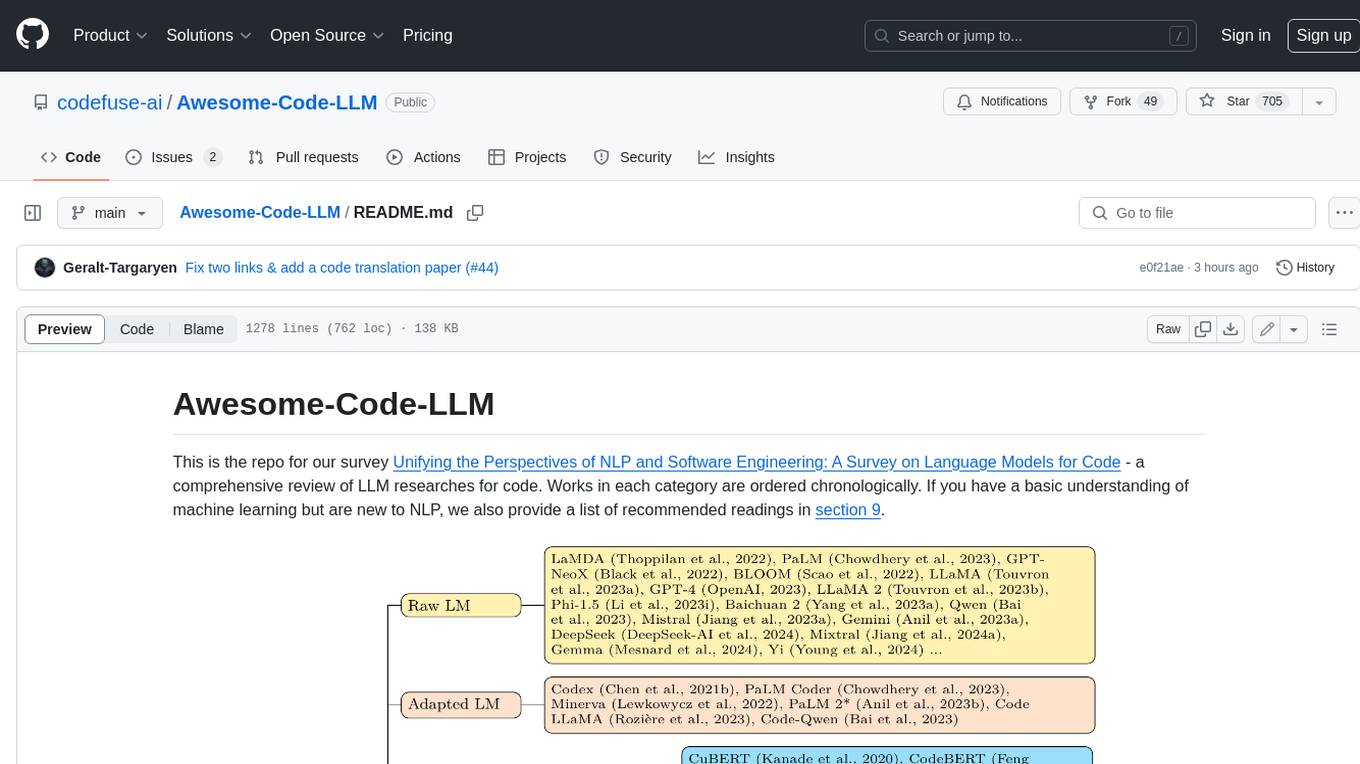
Awesome-Code-LLM
Analyze the following text from a github repository (name and readme text at end) . Then, generate a JSON object with the following keys and provide the corresponding information for each key, in lowercase letters: 'description' (detailed description of the repo, must be less than 400 words,Ensure that no line breaks and quotation marks.),'for_jobs' (List 5 jobs suitable for this tool,in lowercase letters), 'ai_keywords' (keywords of the tool,user may use those keyword to find the tool,in lowercase letters), 'for_tasks' (list of 5 specific tasks user can use this tool to do,in lowercase letters), 'answer' (in english languages)
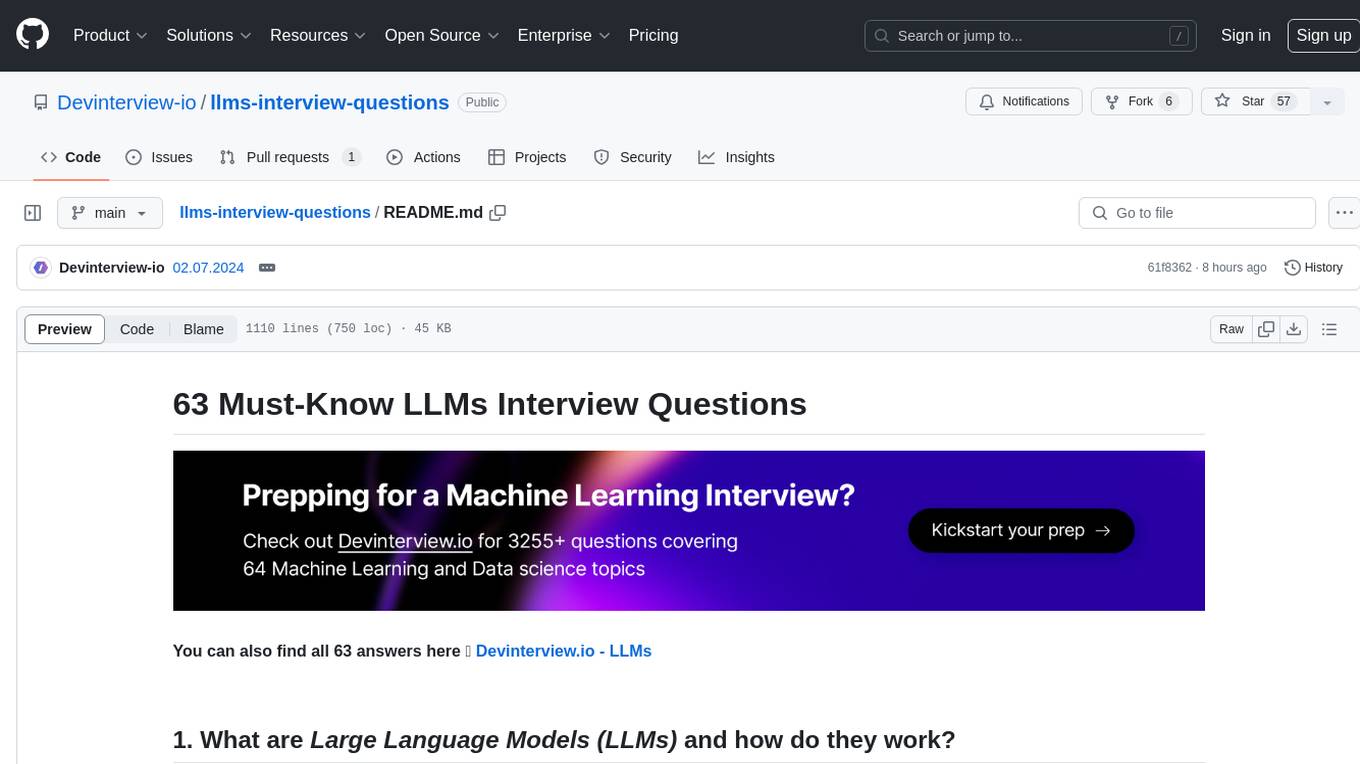
llms-interview-questions
This repository contains a comprehensive collection of 63 must-know Large Language Models (LLMs) interview questions. It covers topics such as the architecture of LLMs, transformer models, attention mechanisms, training processes, encoder-decoder frameworks, differences between LLMs and traditional statistical language models, handling context and long-term dependencies, transformers for parallelization, applications of LLMs, sentiment analysis, language translation, conversation AI, chatbots, and more. The readme provides detailed explanations, code examples, and insights into utilizing LLMs for various tasks.
Awesome_papers_on_LLMs_detection
This repository is a curated list of papers focused on the detection of Large Language Models (LLMs)-generated content. It includes the latest research papers covering detection methods, datasets, attacks, and more. The repository is regularly updated to include the most recent papers in the field.
deid-examples
This repository contains examples demonstrating how to use the Private AI REST API for identifying and replacing Personally Identifiable Information (PII) in text. The API supports over 50 entity types, such as Credit Card information and Social Security numbers, across 50 languages. Users can access documentation and the API reference on Private AI's website. The examples include common API call scenarios and use cases in both Python and JavaScript, with additional content related to PrivateGPT for secure work with Language Models (LLMs).
LLaMA-Factory
LLaMA Factory is a unified framework for fine-tuning 100+ large language models (LLMs) with various methods, including pre-training, supervised fine-tuning, reward modeling, PPO, DPO and ORPO. It features integrated algorithms like GaLore, BAdam, DoRA, LongLoRA, LLaMA Pro, LoRA+, LoftQ and Agent tuning, as well as practical tricks like FlashAttention-2, Unsloth, RoPE scaling, NEFTune and rsLoRA. LLaMA Factory provides experiment monitors like LlamaBoard, TensorBoard, Wandb, MLflow, etc., and supports faster inference with OpenAI-style API, Gradio UI and CLI with vLLM worker. Compared to ChatGLM's P-Tuning, LLaMA Factory's LoRA tuning offers up to 3.7 times faster training speed with a better Rouge score on the advertising text generation task. By leveraging 4-bit quantization technique, LLaMA Factory's QLoRA further improves the efficiency regarding the GPU memory.

PyRIT
PyRIT is an open access automation framework designed to empower security professionals and ML engineers to red team foundation models and their applications. It automates AI Red Teaming tasks to allow operators to focus on more complicated and time-consuming tasks and can also identify security harms such as misuse (e.g., malware generation, jailbreaking), and privacy harms (e.g., identity theft). The goal is to allow researchers to have a baseline of how well their model and entire inference pipeline is doing against different harm categories and to be able to compare that baseline to future iterations of their model. This allows them to have empirical data on how well their model is doing today, and detect any degradation of performance based on future improvements.
langcheck
LangCheck is a Python library that provides a suite of metrics and tools for evaluating the quality of text generated by large language models (LLMs). It includes metrics for evaluating text fluency, sentiment, toxicity, factual consistency, and more. LangCheck also provides tools for visualizing metrics, augmenting data, and writing unit tests for LLM applications. With LangCheck, you can quickly and easily assess the quality of LLM-generated text and identify areas for improvement.
moatless-tools
Moatless Tools is a hobby project focused on experimenting with using Large Language Models (LLMs) to edit code in large existing codebases. The project aims to build tools that insert the right context into prompts and handle responses effectively. It utilizes an agentic loop functioning as a finite state machine to transition between states like Search, Identify, PlanToCode, ClarifyChange, and EditCode for code editing tasks.

comet-llm
CometLLM is a tool to log and visualize your LLM prompts and chains. Use CometLLM to identify effective prompt strategies, streamline your troubleshooting, and ensure reproducible workflows!
20 - OpenAI Gpts
Securia
AI-powered audit ally. Enhance cybersecurity effortlessly with intelligent, automated security analysis. Safe, swift, and smart.
ethicallyHackingspace (eHs)® (Full Spectrum)™
Full Spectrum Space Cybersecurity Professional ™ AI-copilot (BETA)
Threat Intel Briefs
Delivers daily, sector-specific cybersecurity threat intel briefs with source citations.
EU CRA Assistant
Expert in the EU Cyber Resilience Act, providing clear explanations and guidance.
RobotGPT
Expert in ethical hacking, leveraging https://pentestbook.six2dez.com/ and https://book.hacktricks.xyz resources for CTFs and challenges.

VulnGPT
Your ally in navigating the CVE deluge. Expert insights for prioritizing and remediating vulnerabilities.
Cybersecurity Hemingway Analyzer
I analyze cybersecurity content for readability and buzzwords