Best AI tools for< Monitor Network Security >
20 - AI tool Sites
Hive Defender
Hive Defender is an advanced, machine-learning-powered DNS security service that offers comprehensive protection against a vast array of cyber threats including but not limited to cryptojacking, malware, DNS poisoning, phishing, typosquatting, ransomware, zero-day threats, and DNS tunneling. Hive Defender transcends traditional cybersecurity boundaries, offering multi-dimensional protection that monitors both your browser traffic and the entirety of your machine’s network activity.
Nexigen
Nexigen is an award-winning IT and cybersecurity partner that provides expert service, support, and strategic insights to enterprises, SMBs, and fast-growing startups. They offer managed IT services, IT support, professional services, artificial intelligence solutions, cybersecurity, cloud solutions, and network services. With a team of over 70 employees and a focus on confidence-as-a-service™, Nexigen ensures businesses are always on and moving ahead.
Stellar Cyber
Stellar Cyber is an AI-driven unified security operations platform powered by Open XDR. It offers a single platform with NG-SIEM, NDR, and Open XDR, providing security capabilities to take control of security operations. The platform helps organizations detect, correlate, and respond to threats fast using AI technology. Stellar Cyber is designed to protect the entire attack surface, improve security operations performance, and reduce costs while simplifying security operations.
Palo Alto Networks
Palo Alto Networks is a cybersecurity company offering advanced security solutions powered by Precision AI to protect modern enterprises from cyber threats. The company provides network security, cloud security, and AI-driven security operations to defend against AI-generated threats in real time. Palo Alto Networks aims to simplify security and achieve better security outcomes through platformization, intelligence-driven expertise, and proactive monitoring of sophisticated threats.
Netify
Netify provides network intelligence and visibility. Its solution stack starts with a Deep Packet Inspection (DPI) engine that passively collects data on the local network. This lightweight engine identifies applications, protocols, hostnames, encryption ciphers, and other network attributes. The software can be integrated into network devices for traffic identification, firewalling, QoS, and cybersecurity. Netify's Informatics engine collects data from local DPI engines and uses the power of a public or private cloud to transform it into network intelligence. From device identification to cybersecurity risk detection, Informatics provides a way to take a proactive approach to manage network threats, bottlenecks, and usage. Lastly, Netify's Data Feeds provide data to help vendors understand how applications behave on the Internet.
Veriti
Veriti is an AI-driven platform that proactively monitors and safely remediates exposures across the entire security stack, without disrupting the business. It helps organizations maximize their security posture while ensuring business uptime. Veriti offers solutions for safe remediation, MITRE ATT&CK®, healthcare, MSSPs, and manufacturing. The platform correlates exposures to misconfigurations, continuously assesses exposures, integrates with various security solutions, and prioritizes remediation based on business impact. Veriti is recognized for its role in exposure assessments and remediation, providing a consolidated security platform for businesses to neutralize threats before they happen.
Cyguru
Cyguru is an all-in-one cloud-based AI Security Operation Center (SOC) that offers a comprehensive range of features for a robust and secure digital landscape. Its Security Operation Center is the cornerstone of its service domain, providing AI-Powered Attack Detection, Continuous Monitoring for Vulnerabilities and Misconfigurations, Compliance Assurance, SecPedia: Your Cybersecurity Knowledge Hub, and Advanced ML & AI Detection. Cyguru's AI-Powered Analyst promptly alerts users to any suspicious behavior or activity that demands attention, ensuring timely delivery of notifications. The platform is accessible to everyone, with up to three free servers and subsequent pricing that is more than 85% below the industry average.
ForbiddenGuard
The website is currently displaying a '403 Forbidden' error, which indicates that the server is refusing to respond to the request. This error message is typically shown when the server understands the request made by the client but refuses to fulfill it. The 'openresty' mentioned in the text is likely the web server software being used. It is important to troubleshoot and resolve the 403 Forbidden error to regain access to the desired content on the website.
Playlab.ai
Playlab.ai is an AI-powered platform that offers a range of tools and applications to enhance online security and protect against cyber attacks. The platform utilizes advanced algorithms to detect and prevent various online threats, such as malicious attacks, SQL injections, and data breaches. Playlab.ai provides users with a secure and reliable online environment by offering real-time monitoring and protection services. With a user-friendly interface and customizable security settings, Playlab.ai is a valuable tool for individuals and businesses looking to safeguard their online presence.
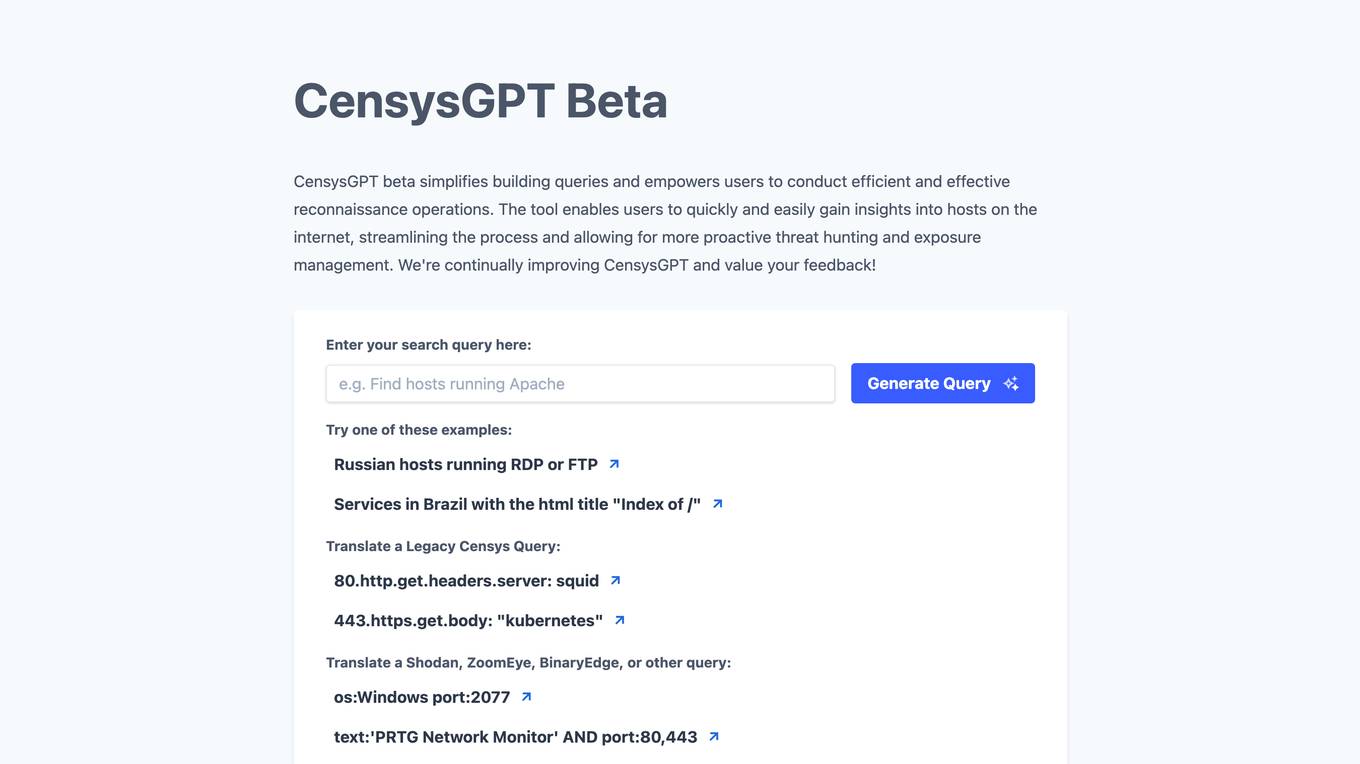
CensysGPT Beta
CensysGPT Beta is a tool that simplifies building queries and empowers users to conduct efficient and effective reconnaissance operations. It enables users to quickly and easily gain insights into hosts on the internet, streamlining the process and allowing for more proactive threat hunting and exposure management.
Security Certificate Advisor
The website provides information about a privacy error related to a security certificate expiration for the IP address 147.139.135.71. It warns users about potential data theft and advises on correcting system clock settings. The site also mentions Certificate Transparency and offers options to enhance web security.

Metasoma Web Security
The website www.metasoma.ai is experiencing a privacy error due to an expired security certificate. Users are warned that their information may be at risk of theft. The site is advised to enhance security measures to protect user data and prevent potential attacks.

uselumin.co
The website uselumin.co is experiencing a privacy error related to an invalid security certificate. The error message indicates a potential security threat where attackers may attempt to steal sensitive information such as passwords, messages, or credit card details. The site's security certificate is issued by 'atlahealthcare.com' and expires on May 8, 2026. The error message advises caution when accessing the site due to the security risk posed by the invalid certificate.

AitoCards
The website aitocards.com seems to be facing a privacy error related to its SSL certificate. The error message indicates that the connection is not private and warns about potential attackers trying to steal sensitive information such as passwords, messages, or credit card details. The certificate in question is issued by cloudflare-dns.com, and the warning suggests that the site's security certificate is invalid. Users are advised to proceed to the site at their own risk, as it may be unsafe due to a potential misconfiguration or interception by an attacker.
Cloudhumans
The website en.cloudhumans.com is experiencing a DNS issue where the IP address is prohibited, causing a conflict within Cloudflare's system. Users encountering this error are advised to refer to the provided link for troubleshooting details. The site is hosted on the Cloudflare network, and the owner is instructed to log in and change the DNS A records to resolve the issue. Additionally, the page provides information about Cloudflare Ray ID and user's IP address, along with performance and security features by Cloudflare.
Sexy.ai
Sexy.ai is an AI-powered security service provided by Cloudflare to protect websites from online attacks. It helps in identifying and blocking malicious activities such as submitting certain words or phrases, SQL commands, or malformed data. The tool uses advanced algorithms to detect potential threats and prevent unauthorized access to websites. Sexy.ai ensures the safety and integrity of online platforms by offering robust security solutions.
Vibe AI
Vibe AI is an AI-powered cybersecurity product designed to secure business data by utilizing advanced AI technologies. It offers real-time alert notifications and developer-friendly APIs to protect digital assets. With military-grade security features, Vibe AI automatically detects threats and provides a pay-as-you-go subscription model for flexible usage. It aims to provide businesses with peace of mind and control over their data security.

403 Forbidden
The website appears to be displaying a '403 Forbidden' error message, which typically means that the user is not authorized to access the requested page. This error is often encountered when trying to access a webpage without the necessary permissions or when the server is configured to deny access. The message 'openresty' may indicate that the server is using the OpenResty web platform. It is important to ensure that the correct permissions are in place and that the requested page exists on the server.
SocialGuard.co
SocialGuard.co is a website that currently faces an issue with an invalid SSL certificate, causing an error code 526. The website is hosted on Cloudflare and provides information on the SSL certificate error. Users visiting the site are advised to wait a few minutes if they encounter the error. For website owners, the error indicates a problem with the SSL certificate validation, possibly due to expiration or incorrect configuration. The site recommends contacting the hosting provider to resolve the issue.
Loudfame
Loudfame.com is a website that appears to be experiencing a privacy error related to an expired security certificate. The site may be at risk of attackers trying to steal sensitive information such as passwords, messages, or credit card details. Users are advised to proceed with caution due to the security concerns highlighted on the page.
1 - Open Source AI Tools
awesome-business-of-cybersecurity
The 'Awesome Business of Cybersecurity' repository is a comprehensive resource exploring the cybersecurity market, focusing on publicly traded companies, industry strategy, and AI capabilities. It provides insights into how cybersecurity companies operate, compete, and evolve across 18 solution categories and beyond. The repository offers structured information on the cybersecurity market snapshot, specialists vs. multiservice cybersecurity companies, cybersecurity stock lists, endpoint protection and threat detection, network security, identity and access management, cloud and application security, data protection and governance, security analytics and threat intelligence, non-US traded cybersecurity companies, cybersecurity ETFs, blogs and newsletters, podcasts, market insights and research, and cybersecurity solutions categories.
20 - OpenAI Gpts
Network Operations Advisor
Ensures efficient and effective network performance and security.
Network Architecture Advisor
Designs and optimizes organization's network architecture to ensure seamless operations.
A Monitoring Expert
Expert in host monitoring setup, providing seamless network monitoring solutions.

NetMaster Pro 🌐🛠️
Your AI network guru for setup and fixing connectivity woes! 🌐 Assists with network configurations, troubleshooting, and optimizes your internet experience. 💻✨
Cyber security analyst
Designed to help cybersecurity analysts # ISO # NIST # COBIT # SANS # PCI DSS
Log Analyzer
I'm designed to help You analyze any logs like Linux system logs, Windows logs, any security logs, access logs, error logs, etc. Please do not share information that You would like to keep private. The author does not collect or process any personal data.
OPSGPT
A technical encyclopedia for network operations, offering detailed solutions and advice.