Best AI tools for< Forensic Analysis >
20 - AI tool Sites
Amped Software
Amped Software develops solutions for the analysis and enhancement of images and videos for forensic, security, and investigative applications. Their tools are used by top forensic labs, law enforcement, military, security, and government agencies worldwide.

Allchemy
Allchemy is a resource-aware AI platform for drug discovery. It combines state-of-the-art computational synthesis with AI algorithms to predict molecular properties. Within minutes, Allchemy creates thousands of synthesizable lead candidates meeting user-defined profiles of drug-likeness, affinity towards specific proteins, toxicity, and a range of other physical-chemical measures. Allchemy encompasses the entire resource-to-drug design process and has been used in academic, corporate and classified environments worldwide to: Design synthesizable leads targeting specific proteins Evolve scaffolds similar to desired drugs Design “circular” drug syntheses from renewable materials Interface with and instruct automated synthesis platforms and optimize pilot-scale processes Operate “iterative synthesis” schemes Predict side reactions and create forensic “synthetic signatures” of hazardous/toxic molecules Design synthetic degradation and recovery cycles for various types of feedstocks and functional target molecules
GeoInfer
GeoInfer is a professional AI-powered geolocation platform that analyzes photographs to determine where they were taken. It uses visual-only inference technology to examine visual elements like architecture, terrain, vegetation, and environmental markers to identify geographic locations without requiring GPS metadata or EXIF data. The platform offers transparent accuracy levels for different use cases, including a Global Model with 1km-100km accuracy ideal for regional and city-level identification. Additionally, GeoInfer provides custom regional models for organizations requiring higher precision, such as meter-level accuracy for specific geographic areas. The platform is designed for professionals in various industries, including law enforcement, insurance fraud investigation, digital forensics, and security research.
AI Debate Competitions
Engage in thought-provoking debates with AI Debate Competitions. Enter the arena of ideas, where every perspective matters. Prepare to challenge and be challenged as you delve into discussions powered by advanced AI technology. Choose from a variety of debate models and languages to tailor your experience. With AI Debate Competitions, you can hone your critical thinking skills, expand your knowledge, and connect with fellow debaters from around the globe.
Ai-SPY
Ai-SPY is an advanced AI audio detection tool that helps users identify whether speech is human or AI-generated. It offers detailed reports, easy integration with API access, and expert human insights for accurate analysis. Ai-SPY leverages a proprietary neural network to provide unparalleled audio authenticity insights, making it a valuable tool for content verification and manipulation detection.
Panda Video
Panda Video is a video hosting platform that offers a variety of AI-powered features to help businesses increase sales and improve security. These features include a mind map tool for visualizing video content, a quiz feature for creating interactive learning experiences, an AI-powered ebook feature for providing supplemental resources, automatic captioning, a search feature for quickly finding specific content within videos, and automatic dubbing for creating videos in multiple languages. Panda Video also offers a variety of other features, such as DRM protection to prevent piracy, smart autoplay to increase engagement, a customizable player appearance, Facebook Pixel integration for retargeting, and analytics to track video performance.
SYSTRAN
SYSTRAN is a professional translation tool that enables multilingual communication and collaboration, providing fast, accurate, and enhanced machine translations for various industries. It offers solutions for global customer service and support, forensics and eDiscovery, content localization, education and eLearning, and big data analysis for government. The tool also includes features like machine translation server, private cloud solutions, model training, and API integration, ensuring efficient and secure online translation. With over 50 years of expertise, SYSTRAN leverages AI technology to deliver precise translations tailored to meet diverse business needs.
MegaMatcher ABIS Online
MegaMatcher ABIS Online is an automated biometric identification system developed by Neurotechnology. It offers a turnkey multi-biometric solution for government and enterprise applications worldwide. The system includes features such as enrollment, biometric matching, identity management, data analysis, and deployment options for cloud services or on-premise solutions. With support for fingerprint, face, iris, and palmprint biometric modalities, the system ensures high accuracy, reliability, and unlimited storage of biometric and demographic information. It also provides easy integration through RESTful API and SDK libraries, along with security features like role-based access control and auditability.
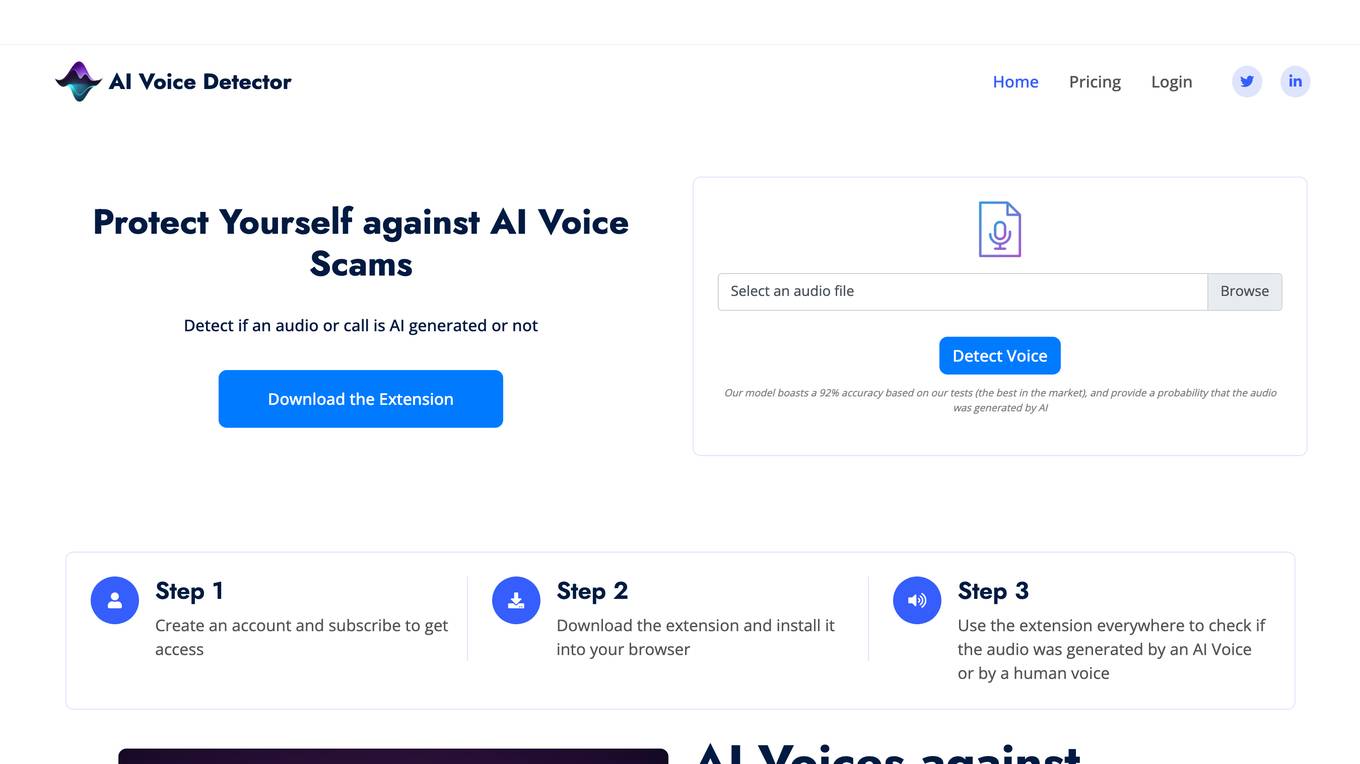
AI Voice Detector
AI Voice Detector is an AI tool designed to protect individuals and businesses from audio manipulation and AI-generated voices. It offers a high accuracy rate in identifying real voices versus AI-generated ones, integrated features to remove background noise and music, and the ability to detect AI cloned voices from various platforms. The tool can be used to scan voices on popular platforms like Youtube, WhatsApp, Tiktok, Zoom, and Google Meet. It helps individuals verify voice messages and calls to prevent falling victim to AI voice scams, while also assisting businesses in authenticating audio messages, calls, and meetings to avoid financial losses.
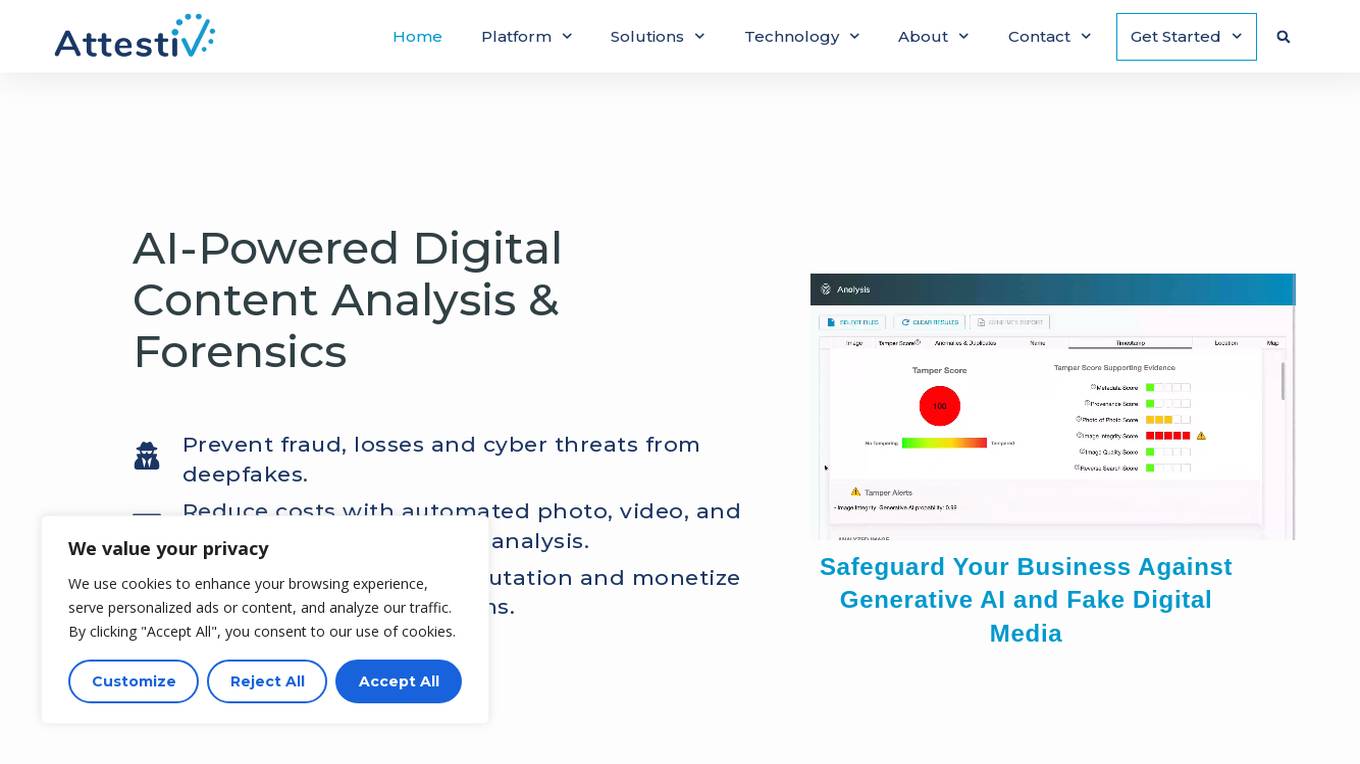
Attestiv
Attestiv is an AI-powered digital content analysis and forensics platform that offers solutions to prevent fraud, losses, and cyber threats from deepfakes. The platform helps in reducing costs through automated photo, video, and document inspection and analysis, protecting company reputation, and monetizing trust in secure systems. Attestiv's technology provides validation and authenticity for all digital assets, safeguarding against altered photos, videos, and documents that are increasingly easy to create but difficult to detect. The platform uses patented AI technology to ensure the authenticity of uploaded media and offers sector-agnostic solutions for various industries.
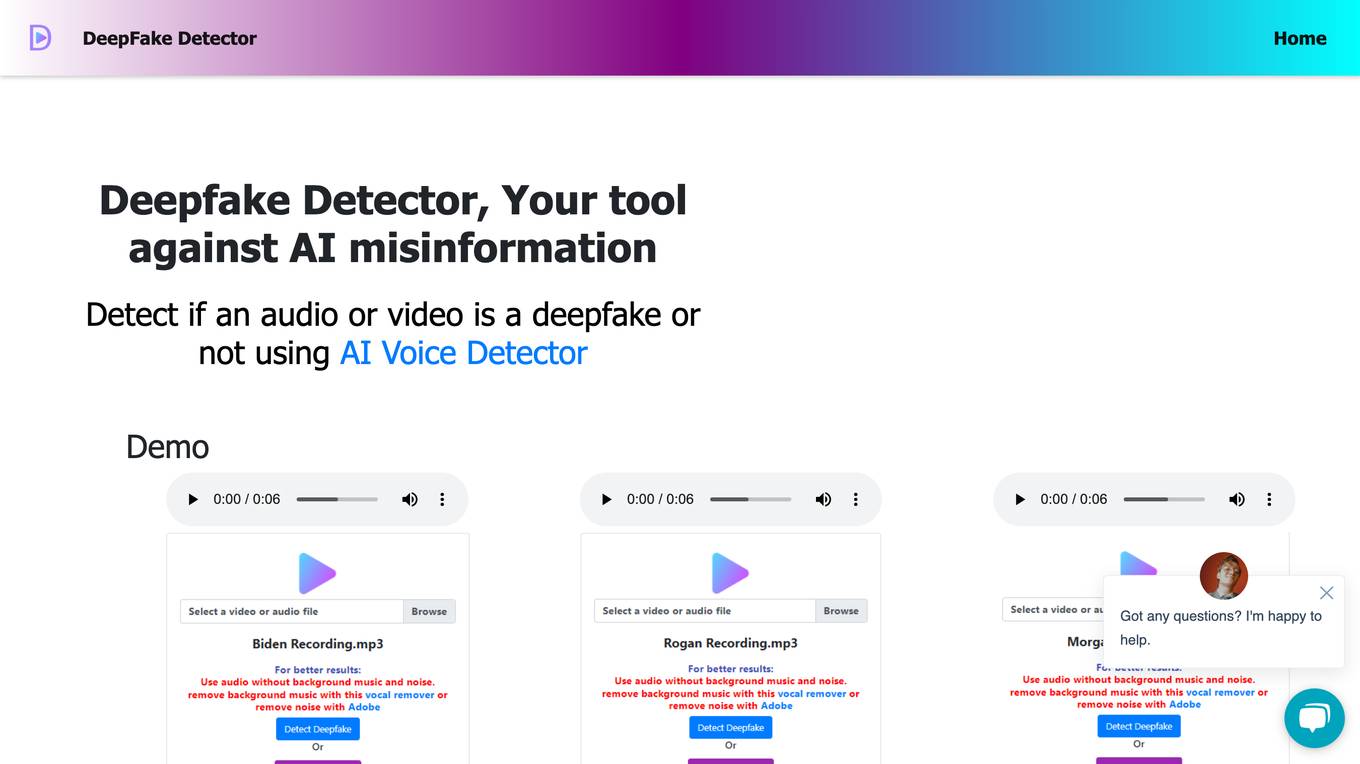
Deepfake Detector
Deepfake Detector is an AI tool designed to identify deepfakes in audio and video files. It offers features such as background noise and music removal, audio and video file analysis, and browser extension integration. The tool helps individuals and businesses protect themselves against deepfake scams by providing accurate detection and filtering of AI-generated content. With a focus on authenticity and reliability, Deepfake Detector aims to prevent financial losses and fraudulent activities caused by deepfake technology.
EchoMark
EchoMark is a cloud-based data leak prevention solution that uses invisible forensic watermarks to protect sensitive information from unauthorized access and exfiltration. It allows organizations to securely share and collaborate on documents and emails without compromising privacy and security. EchoMark's advanced investigation tools can trace the source of a leaked document or email, even if it has been shared via printout or photo.
Polycam
The website offers a cross-platform 3D scanning tool for floor plans and drone mapping. It allows users to capture and collaborate in new ways, providing reality capture for professionals to document, measure, and design various spaces. Users can create instantly shareable 3D models, generate customizable 2D floor plans, capture drone footage for 3D models, and document detailed metrics for site surveys, construction sites, products, and more. The tool is suitable for teams in architecture, engineering, construction, forensics, investigation, product design, manufacturing, media, and entertainment industries.
Wondershare Recoverit
Wondershare Recoverit is a comprehensive data recovery software that can restore lost files from various devices and storage media. It offers advanced features such as enhanced photo and video recovery, hard drive and location recovery, system crashed computer recovery, NAS data recovery, and Linux data recovery. Recoverit supports over 1000 file formats and 2000 storage devices, with a high recovery rate of 98%. It is trusted by over 5 million users across 160 countries and has been awarded 35 advanced patents for its innovative data recovery methods.
Relativity
Relativity is an AI-powered eDiscovery and legal search software solution that helps customers organize data, discover truth, and act on it. It offers a range of features such as proactive security, user experience enhancements, open platform for customization, legendary support, and AI-powered review tools. Relativity is trusted by thousands of organizations to handle sensitive data and streamline data discovery processes.
DISCO
DISCO is an AI-powered ediscovery and litigation hold software that offers comprehensive, cloud-native solutions and services for law firms, corporate legal teams, and educational institutions. With state-of-the-art AI technology, DISCO streamlines legal processes, improves efficiency, and provides better legal outcomes. The platform includes features such as Cecilia AI chatbot, ediscovery cloud-native software, legal hold management, case builder, auto review, and timelines. DISCO also offers professional services like document review, forensic services, and enterprise managed services to support users in their legal workflows.
Splitter.ai
Splitter.ai is an AI-driven audio processing platform developed by a Swedish research company. It offers advanced audio processing technologies, including stem separation/extraction, reverb removal, and direct YouTube splitting. The platform is designed to assist music producers, DJs, artists, forensics engineers, audio engineers, karaoke enthusiasts, police, scientists, and more in enhancing their audio processing tasks. Splitter.ai aims to provide high-quality services through AI-driven solutions to meet the diverse needs of its users.
Loudfame
Loudfame.com is a website that appears to be experiencing a privacy error related to an expired security certificate. The site may be at risk of attackers trying to steal sensitive information such as passwords, messages, or credit card details. Users are advised to proceed with caution due to the security concerns highlighted on the page.
ONERECOVERY
ONERECOVERY is a professional data recovery solution for Windows that offers comprehensive and expert solutions to recover lost data from various storage devices. The software is designed to handle data loss for over 1,000 scenarios, including accidental deletion, formatting errors, virus attacks, and more. ONERECOVERY provides features such as file recovery for Windows and Mac, file duplicate finder, photo and video recovery, hard drive recovery, SD card data recovery, and more. With a user-friendly interface, quick and efficient scanning, and compatibility with diverse operating systems and storage devices, ONERECOVERY is a reliable and secure data recovery tool trusted by millions of users worldwide.
Flagright Solutions
Flagright Solutions is an AI-native AML Compliance & Risk Management platform that offers real-time transaction monitoring, automated case management, AI forensics for screening, customer risk assessment, and sanctions screening. Trusted by financial institutions worldwide, Flagright's platform streamlines compliance workflows, reduces manual tasks, and enhances fraud detection accuracy. The platform provides end-to-end solutions for financial crime compliance, empowering operational teams to collaborate effectively and make reliable decisions. With advanced AI algorithms and real-time processing, Flagright ensures instant detection of suspicious activities, reducing false positives and enhancing risk detection capabilities.
0 - Open Source AI Tools
20 - OpenAI Gpts
API Content Warehouse Leak Help
Comprehensive analysis of Google API Content Warehouse Leak
AML/CFT Expert
Specializes in Anti-Money Laundering/Counter-Financing of Terrorism compliance and analysis.
筆圧特性評価機(Writing Pressure Characterization Machine)
デジタル テキストを除く、手書きの筆圧を分析して性格特性を推測します。(Analyzes handwriting pressure to infer personality traits, excluding digital text.)
Message Header Analyzer
Analyzes email headers for security insights, presenting data in a structured table view.
Crime and Mystery Solver
Expert in solving crimes and mysteries, adept at handling extensive data.

TheDFIRReport Assistant
Detailed insights from TheDFIRReport's 2021-2023 reports, including Detections and Indicators.
Incident Response Forensic Techniques
help organizations in investigating computer security incidents and troubleshooting some information technology (IT) operational problems by providing practical guidance on performing computer and network forensics.
CSI Miami: City of Crime
“Forensic investigator in CSI Miami game, solving crimes with critical thinking.”
Cold Case Cracker
Interactive Simulation Game Solving Cold Cases Just Type Start to Begin
Enciclopedia CCI Vol 1 © Sigma Editores SAS
Líder en Latinoamérica en Criminalística, Criminología, Medicina Legal y Forense, e Investigación Criminal