Best AI tools for< Information Security Consultant >
Infographic
20 - AI tool Sites

Metasoma Web Security
The website www.metasoma.ai is experiencing a privacy error due to an expired security certificate. Users are warned that their information may be at risk of theft. The site is advised to enhance security measures to protect user data and prevent potential attacks.

StudentMate
The website studentmate.shuchir.dev is a platform that focuses on enhancing security and privacy for users while browsing the web. It provides information about potential privacy errors, such as insecure connections and invalid certificates, and offers guidance on how to protect personal data. The site educates users on common security threats and how to identify and mitigate them, ultimately aiming to create a safer online environment for everyone.
SharkGate
SharkGate is an AI-driven cybersecurity platform that focuses on protecting websites from various cyber threats. The platform offers solutions for mobile security, password management, quantum computing threats, API security, and cloud security. SharkGate leverages artificial intelligence and machine learning to provide advanced threat detection and response capabilities, ensuring the safety and integrity of digital assets. The platform has received accolades for its innovative approach to cybersecurity and has secured funding from notable organizations.
ISMS Copilot
ISMS Copilot is an AI-powered assistant designed to simplify ISO 27001 preparation for both experts and beginners. It offers various features such as ISMS scope definition, risk assessment and treatment, compliance navigation, incident management, business continuity planning, performance tracking, and more. The tool aims to save time, provide precise guidance, and ensure ISO 27001 compliance. With a focus on security and confidentiality, ISMS Copilot is a valuable resource for small businesses and information security professionals.
Veriti
Veriti is an AI-driven platform that proactively monitors and safely remediates exposures across the entire security stack, without disrupting the business. It helps organizations maximize their security posture while ensuring business uptime. Veriti offers solutions for safe remediation, MITRE ATT&CK®, healthcare, MSSPs, and manufacturing. The platform correlates exposures to misconfigurations, continuously assesses exposures, integrates with various security solutions, and prioritizes remediation based on business impact. Veriti is recognized for its role in exposure assessments and remediation, providing a consolidated security platform for businesses to neutralize threats before they happen.
rooftops.ai
rooftops.ai is an AI-powered platform that focuses on security verification for online connections. It ensures the safety and integrity of user interactions by reviewing security measures before granting access. The platform utilizes advanced algorithms to detect and prevent potential threats, providing a secure environment for users to engage online.
Exabeam
Exabeam is a cybersecurity and compliance platform that offers Security Information and Event Management (SIEM) solutions. The platform provides flexible choices for threat detection, investigation, and response, whether through cloud-based AI-driven solutions or on-premises SIEM deployments. Exabeam's AI-driven Security Operations Platform combines advanced threat detection capabilities with automation to deliver faster and more accurate TDIR. With features like UEBA, SOAR, and insider threat detection, Exabeam helps organizations improve security posture and optimize investments. The platform supports various industries and use cases, offering pre-built content, behavioral analytics, and context enrichment for enhanced threat coverage and compliance.
Cyberday.ai
Cyberday.ai is an AI-powered platform designed to help organizations improve and certify their cybersecurity. The platform offers a comprehensive set of tools and resources to guide users in implementing security tasks, creating policies, and generating compliance reports. With a focus on automation and efficiency, Cyberday.ai streamlines the process of managing information security, from risk assessment to employee training. By leveraging AI technology, Cyberday.ai aims to simplify the complex task of cybersecurity management for organizations of all sizes.
Concentric AI
Concentric AI is a Managed Data Security Posture Management tool that utilizes Semantic Intelligence to provide comprehensive data security solutions. The platform offers features such as autonomous data discovery, data risk identification, centralized remediation, easy deployment, and data security posture management. Concentric AI helps organizations protect sensitive data, prevent data loss, and ensure compliance with data security regulations. The tool is designed to simplify data governance and enhance data security across various data repositories, both in the cloud and on-premises.
chckr.io
The website chckr.io is experiencing a privacy error due to an expired security certificate. Users are warned that their connection may not be private, potentially exposing sensitive information to attackers. The site provides information about the security warning, certificate details, and suggestions to improve web security. It aims to enhance user awareness and security practices on the web.

uselumin.co
The website uselumin.co is experiencing a privacy error related to an invalid security certificate. The error message indicates a potential security threat where attackers may attempt to steal sensitive information such as passwords, messages, or credit card details. The site's security certificate is issued by 'atlahealthcare.com' and expires on May 8, 2026. The error message advises caution when accessing the site due to the security risk posed by the invalid certificate.

yujo.io.tilda.ws
The website yujo.io.tilda.ws is experiencing a privacy error related to its security certificate. Users are warned that their connection may not be private, potentially exposing sensitive information like passwords, messages, or credit card details to attackers. The site's security certificate is not trusted by the computer's operating system, leading to a warning message for users. The error message advises caution and suggests that the issue may be due to misconfiguration or a potential attack on the connection. Users are given the option to proceed to the site at their own risk, despite the security concerns.

iQ Suite
iQ Suite is an advanced AI application developed by Blue Hex Software, offering a comprehensive suite of AI solutions to empower businesses with cutting-edge generative AI capabilities. The application revolutionizes workflows, amplifies productivity, and enhances customer experience by delivering insights beyond imagination, supreme data analytics, and transforming data into knowledge with AI-driven document analysis. iQ Suite ensures data security at the core, with advanced encryption and protection protocols, seamless integration with existing systems, and real-time monitoring capabilities. The application also offers customizable security settings and personalized solutions tailored to meet specific business needs.
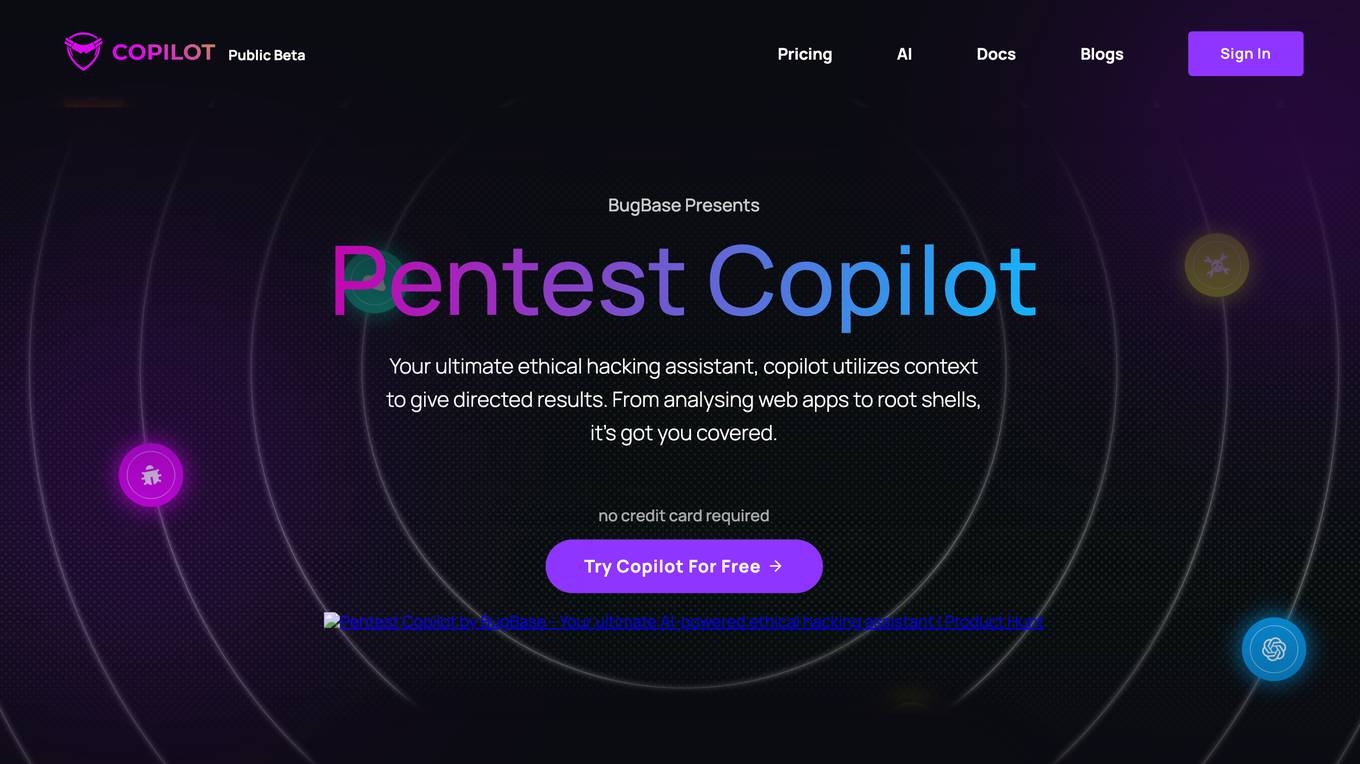
Pentest Copilot
Pentest Copilot by BugBase is an ultimate ethical hacking assistant that guides users through each step of the hacking journey, from analyzing web apps to root shells. It eliminates redundant research, automates payload and command generation, and provides intelligent contextual analysis to save time. The application excels at data extraction, privilege escalation, lateral movement, and leaving no trace behind. With features like secure VPN integration, total control over sessions, parallel command processing, and flexibility to choose between local or cloud execution, Pentest Copilot offers a seamless and efficient hacking experience without the need for Kali Linux installation.
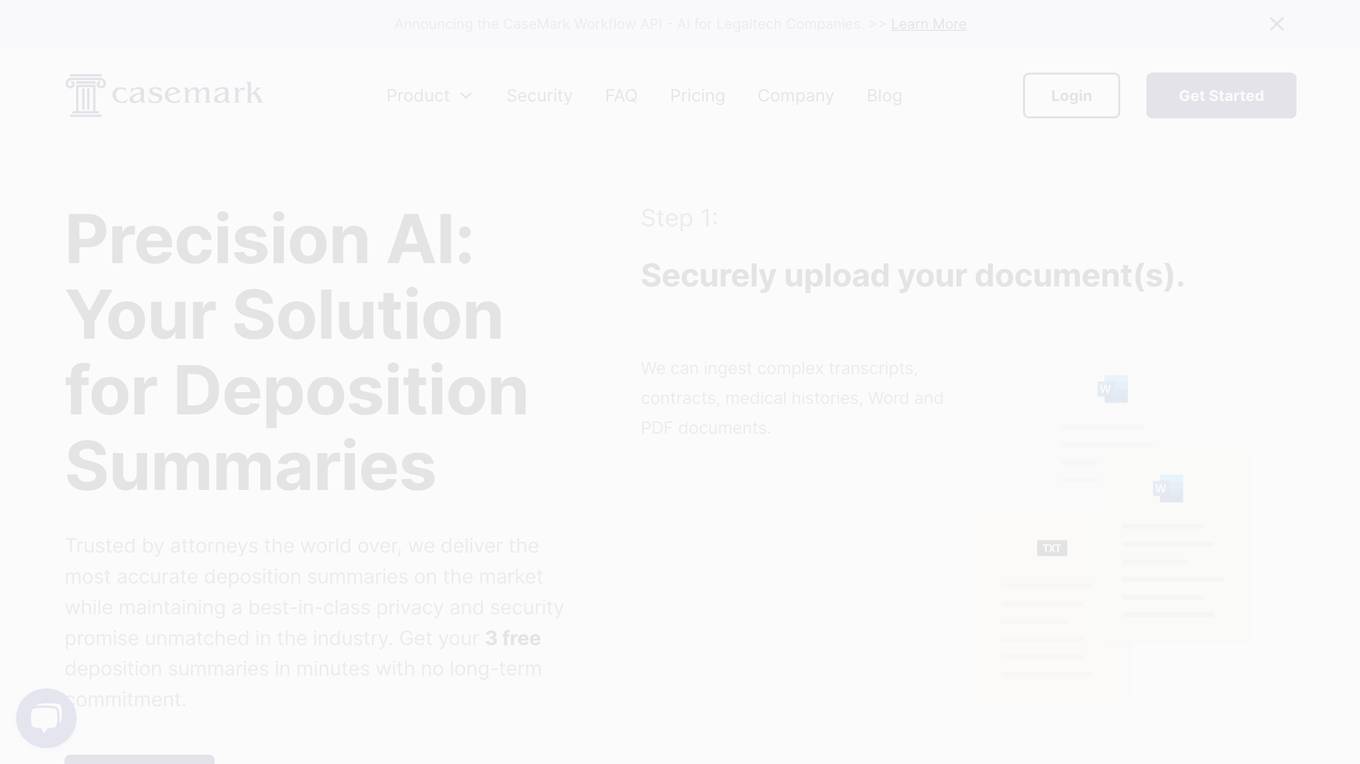
CaseMark
CaseMark is an AI-powered platform designed to empower legal professionals by providing automated workflow and summarization services. It offers concise summaries of legal documents, such as deposition summaries, medical records summaries, trial summaries, and more. With features like custom workflows, integration with existing platforms, enterprise-class security, and the ability to select the best LLM for each use case, CaseMark aims to streamline legal processes and improve efficiency. Trusted by over 6,000 lawyers and legal tech companies, CaseMark is a privacy-first platform that helps users save time and focus on critical legal matters.
Loudfame
Loudfame.com is a website that appears to be experiencing a privacy error related to an expired security certificate. The site may be at risk of attackers trying to steal sensitive information such as passwords, messages, or credit card details. Users are advised to proceed with caution due to the security concerns highlighted on the page.
Dreamervision.ai
Dreamervision.ai is an innovative AI tool that utilizes advanced machine learning algorithms to analyze and interpret images and videos. The tool is designed to provide users with valuable insights and information based on visual content, enabling them to make informed decisions and enhance their understanding of the world around them. With its cutting-edge technology, Dreamervision.ai offers a seamless and efficient way to extract meaningful data from visual media, making it a valuable asset for professionals in various industries.
SMshrimant
SMshrimant is a personal website belonging to a Bug Bounty Hunter, Security Researcher, Penetration Tester, and Ethical Hacker. The website showcases the creator's skills and experiences in the field of cybersecurity, including bug hunting, security vulnerability reporting, open-source tool development, and participation in Capture The Flag competitions. Visitors can learn about the creator's projects, achievements, and contact information for inquiries or collaborations.
Hacker AI
Hacker-ai.online is a website that provides resources and information related to hacking and artificial intelligence. The webpage seems to be generated by the domain owner using Sedo Domain Parking. It is important to note that Sedo, the domain parking service, has no relationship with third-party advertisers. The website does not imply any association, endorsement, or recommendation of specific services or trademarks. Users can find resources and information on hacking and AI on this platform.
Vectra AI
Vectra AI is a leading cybersecurity AI application that stops attacks that others cannot. It is recognized in the Gartner Magic Quadrant 2025 for Network Detection and Response (NDR) as a leader. Vectra AI's platform protects modern networks from advanced threats by providing real-time attack signal intelligence and AI-driven detections. It equips security analysts with the information needed to quickly stop attacks across various security application scenarios. The application covers a wide range of security areas such as SOC modernization, SIEM optimization, IDS replacement, EDR extension, cloud resilience, and more.
6 - Open Source Tools
ai-exploits
AI Exploits is a repository that showcases practical attacks against AI/Machine Learning infrastructure, aiming to raise awareness about vulnerabilities in the AI/ML ecosystem. It contains exploits and scanning templates for responsibly disclosed vulnerabilities affecting machine learning tools, including Metasploit modules, Nuclei templates, and CSRF templates. Users can use the provided Docker image to easily run the modules and templates. The repository also provides guidelines for using Metasploit modules, Nuclei templates, and CSRF templates to exploit vulnerabilities in machine learning tools.
TI-Mindmap-GPT
TI MINDMAP GPT is an AI-powered tool designed to assist cyber threat intelligence teams in quickly synthesizing and visualizing key information from various Threat Intelligence sources. The tool utilizes Large Language Models (LLMs) to transform lengthy content into concise, actionable summaries, going beyond mere text reduction to provide insightful encapsulations of crucial points and themes. Users can leverage their own LLM keys for personalized and efficient information processing, streamlining data analysis and enabling teams to focus on strategic decision-making.
OpenRedTeaming
OpenRedTeaming is a repository focused on red teaming for generative models, specifically large language models (LLMs). The repository provides a comprehensive survey on potential attacks on GenAI and robust safeguards. It covers attack strategies, evaluation metrics, benchmarks, and defensive approaches. The repository also implements over 30 auto red teaming methods. It includes surveys, taxonomies, attack strategies, and risks related to LLMs. The goal is to understand vulnerabilities and develop defenses against adversarial attacks on large language models.
awesome-business-of-cybersecurity
The 'Awesome Business of Cybersecurity' repository is a comprehensive resource exploring the cybersecurity market, focusing on publicly traded companies, industry strategy, and AI capabilities. It provides insights into how cybersecurity companies operate, compete, and evolve across 18 solution categories and beyond. The repository offers structured information on the cybersecurity market snapshot, specialists vs. multiservice cybersecurity companies, cybersecurity stock lists, endpoint protection and threat detection, network security, identity and access management, cloud and application security, data protection and governance, security analytics and threat intelligence, non-US traded cybersecurity companies, cybersecurity ETFs, blogs and newsletters, podcasts, market insights and research, and cybersecurity solutions categories.
uusec-waf
UUSEC WAF is an industrial grade free, high-performance, and highly scalable web application and API security protection product that supports AI and semantic engines. It provides intelligent 0-day defense, ultimate CDN acceleration, powerful proactive defense, advanced semantic engine, and advanced rule engine. With features like machine learning technology, cache cleaning, dual layer defense, semantic analysis, and Lua script rule writing, UUSEC WAF offers comprehensive website protection with three-layer defense functions at traffic, system, and runtime layers.
Here-Comes-the-AI-Worm
Large Language Models (LLMs) are now embedded in everyday tools like email assistants, chat apps, and productivity software. This project introduces DonkeyRail, a lightweight guardrail that detects and blocks malicious self-replicating prompts known as RAGworm within GenAI-powered applications. The guardrail is fast, accurate, and practical for real-world GenAI systems, preventing activities like spam, phishing campaigns, and data leaks.
10 - OpenAI Gpts
WVA
Web Vulnerability Academy (WVA) is an interactive tutor designed to introduce users to web vulnerabilities while also providing them with opportunities to assess and enhance their knowledge through testing.
Password Guardian
I create ultra-secure, random passwords and offer concise security tips.
Ethical Hacking GPT
Guide to ethical hacking, specializing in NMAP | For Educational Purposes Only | CSV Upload Suggested |
CISSP Study Strategy Guide
Expert guide for CISSP topics, with detailed explanations and real-world application.
Cyber security analyst
Designed to help cybersecurity analysts # ISO # NIST # COBIT # SANS # PCI DSS