Best AI tools for< Analyze Vulnerabilities >
20 - AI tool Sites
Pentest Copilot
Pentest Copilot by BugBase is an ultimate ethical hacking assistant that guides users through each step of the hacking journey, from analyzing web apps to root shells. It eliminates redundant research, automates payload and command generation, and provides intelligent contextual analysis to save time. The application excels at data extraction, privilege escalation, lateral movement, and leaving no trace behind. With features like secure VPN integration, total control over sessions, parallel command processing, and flexibility to choose between local or cloud execution, Pentest Copilot offers a seamless and efficient hacking experience without the need for Kali Linux installation.
Ferhat Erata
Ferhat Erata is an AI application developed by a Computer Science PhD graduate from Yale University. The application focuses on training transformers to solve NP-complete problems using reinforcement learning and improving test-time compute strategies for reasoning. It also explores learning randomized reductions and program properties for security, privacy, and side-channel resilience. Ferhat Erata is currently an Applied Scientist at the Automated Reasoning Group at AWS, working on Neuro-Symbolic AI to prevent factual errors caused by LLM hallucinations using mathematically sound Automated Reasoning checks.
Darktrace
Darktrace is an essential AI cybersecurity platform that offers proactive protection, cloud-native AI security, comprehensive risk management, and user protection across various devices. It accelerates triage by 10x, defends with confidence, and connects with various integrations. Darktrace ActiveAI Security Platform spots novel threats across organizations, providing solutions for ransomware, APTs, phishing, data loss, and more. With a focus on defense, Darktrace aims to transform cybersecurity by detecting and responding to known and novel threats in real-time.
VULNWatch
VULNWatch is a web security platform that simplifies and makes website security accessible. The platform offers automated assessments using AI-powered tools with over 13 years of experience. It empowers business owners and developers to identify and address vulnerabilities quickly and easily in one place. VULNWatch provides effective web security assessment, including fingerprinting, protection against SQL injections, and web shells, with a focus on communication and collaboration with clients to ensure tailored cybersecurity solutions.
AquilaX
AquilaX is an AI-powered DevSecOps platform that simplifies security and accelerates development processes. It offers a comprehensive suite of security scanning tools, including secret identification, PII scanning, SAST, container scanning, and more. AquilaX is designed to integrate seamlessly into the development workflow, providing fast and accurate results by leveraging AI models trained on extensive datasets. The platform prioritizes developer experience by eliminating noise and false positives, making it a go-to choice for modern Secure-SDLC teams worldwide.
DeepSource
DeepSource is a Unified DevSecOps Platform that secures the entire development lifecycle with static analysis and AI. It offers code quality and SAST, open-source security, and is trusted by over 6,000 companies. The platform helps in finding and fixing security vulnerabilities before code is merged, with a low false-positive rate and customizable security gates for pull requests. DeepSource is built for modern software development, providing features like Autofix™ AI, code coverage, and integrations with popular tools like Jira and GitHub Issues. It offers detailed reports, issue suppression, and metric thresholds to ensure clean and secure code shipping.
Traceable
Traceable is an AI-driven application designed to enhance API security for Cloud-Native Apps. It collects API traffic across the application landscape and utilizes advanced context-based behavioral analytics AI engine to provide insights on APIs, data exposure, threat analytics, and forensics. The platform offers features for API cataloging, activity monitoring, endpoint details, ownership, vulnerabilities, protection against security events, testing, analytics, and more. Traceable also allows for role-based access control, policy configuration, data classification, and integration with third-party solutions for data collection and security. It is a comprehensive tool for API security and threat detection in modern cloud environments.
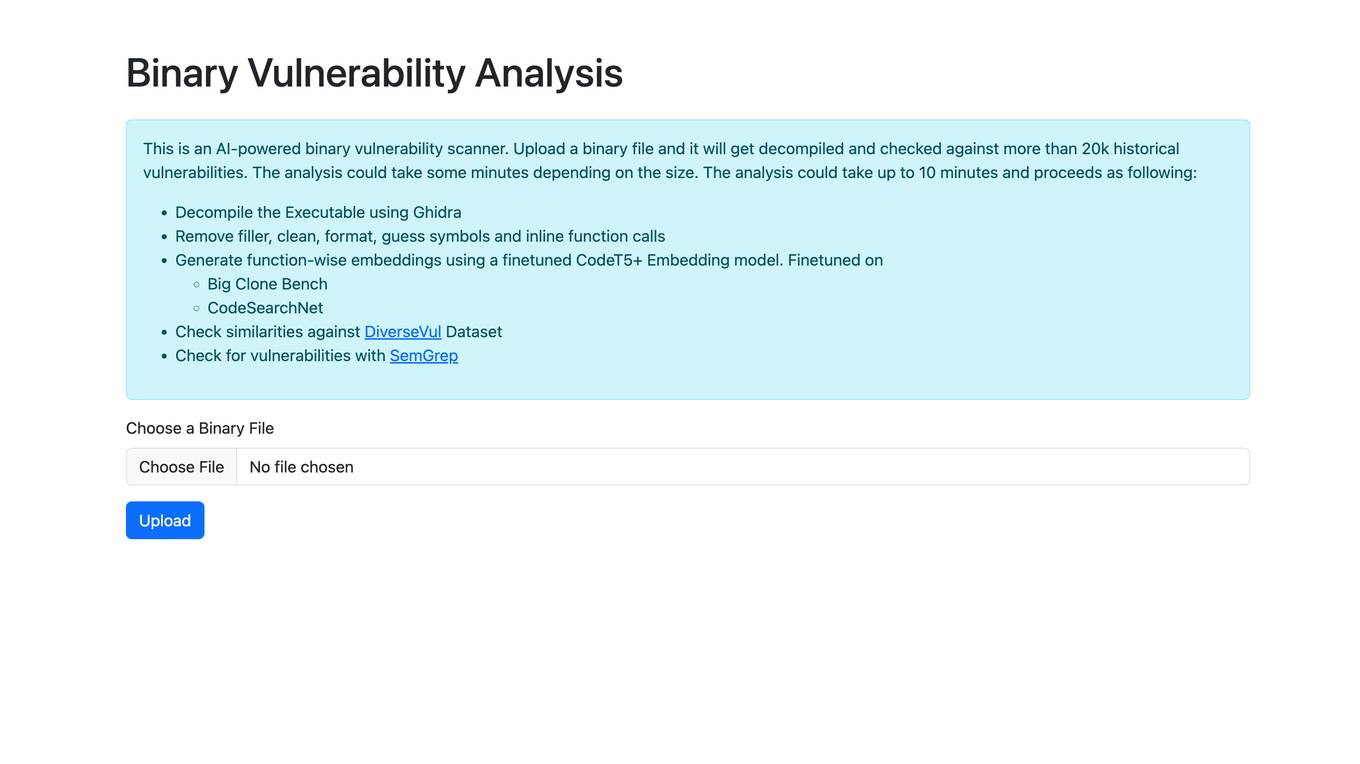
Binary Vulnerability Analysis
The website offers an AI-powered binary vulnerability scanner that allows users to upload a binary file for analysis. The tool decompiles the executable, removes filler, cleans, formats, and checks for historical vulnerabilities. It generates function-wise embeddings using a finetuned CodeT5+ Embedding model and checks for similarities against the DiverseVul Dataset. The tool also utilizes SemGrep to check for vulnerabilities in the binary file.
SentinelOne
SentinelOne is an advanced enterprise cybersecurity AI platform that offers a comprehensive suite of AI-powered security solutions for endpoint, cloud, and identity protection. The platform leverages artificial intelligence to anticipate threats, manage vulnerabilities, and protect resources across the entire enterprise ecosystem. With features such as Singularity XDR, Purple AI, and AI-SIEM, SentinelOne empowers security teams to detect and respond to cyber threats in real-time. The platform is trusted by leading enterprises worldwide and has received industry recognition for its innovative approach to cybersecurity.
CloudDefense.AI
CloudDefense.AI is an industry-leading multi-layered Cloud Native Application Protection Platform (CNAPP) that safeguards cloud infrastructure and cloud-native apps with expertise, precision, and confidence. It offers comprehensive cloud security solutions, vulnerability management, compliance, and application security testing. The platform utilizes advanced AI technology to proactively detect and analyze real-time threats, ensuring robust protection for businesses against cyber threats.
ODIN
ODIN is a powerful internet scanning search engine designed for scanning and cataloging internet assets. It offers enhanced scanning capabilities, faster refresh rates, and comprehensive visibility into open ports. With over 45 modules covering various aspects like HTTP, Elasticsearch, and Redis, ODIN enriches data and provides accurate and up-to-date information. The application uses AI/ML algorithms to detect exposed buckets, files, and potential vulnerabilities. Users can perform granular searches, access exploit information, and integrate effortlessly with ODIN's API, SDKs, and CLI. ODIN allows users to search for hosts, exposed buckets, exposed files, and subdomains, providing detailed insights and supporting diverse threat intelligence applications.
Elicit
Elicit is a research tool that uses artificial intelligence to help researchers analyze research papers more efficiently. It can summarize papers, extract data, and synthesize findings, saving researchers time and effort. Elicit is used by over 800,000 researchers worldwide and has been featured in publications such as Nature and Science. It is a powerful tool that can help researchers stay up-to-date on the latest research and make new discoveries.
Plerdy
Plerdy is a comprehensive suite of conversion rate optimization tools that helps businesses track, analyze, and convert their website visitors into buyers. With a range of features including website heatmaps, session replay software, pop-up software, website feedback tools, and more, Plerdy provides businesses with the insights they need to improve their website's usability and conversion rates.
TimeComplexity.ai
TimeComplexity.ai is an AI tool that helps users analyze the runtime complexity of their code. It can be used across different programming languages without the need for headers, imports, or a main statement. Users can input their code and get insights into its time complexity. However, it is important to note that the results may not always be accurate, so caution is advised when using the tool.
StockGPT
StockGPT is an AI-powered financial research assistant that provides knowledge of earnings releases, financial reports, and fundamental information for S&P 500 and Nasdaq companies. It offers features like AI search, customizable filters, up-to-date data, and industry research to help users analyze companies and markets more efficiently.
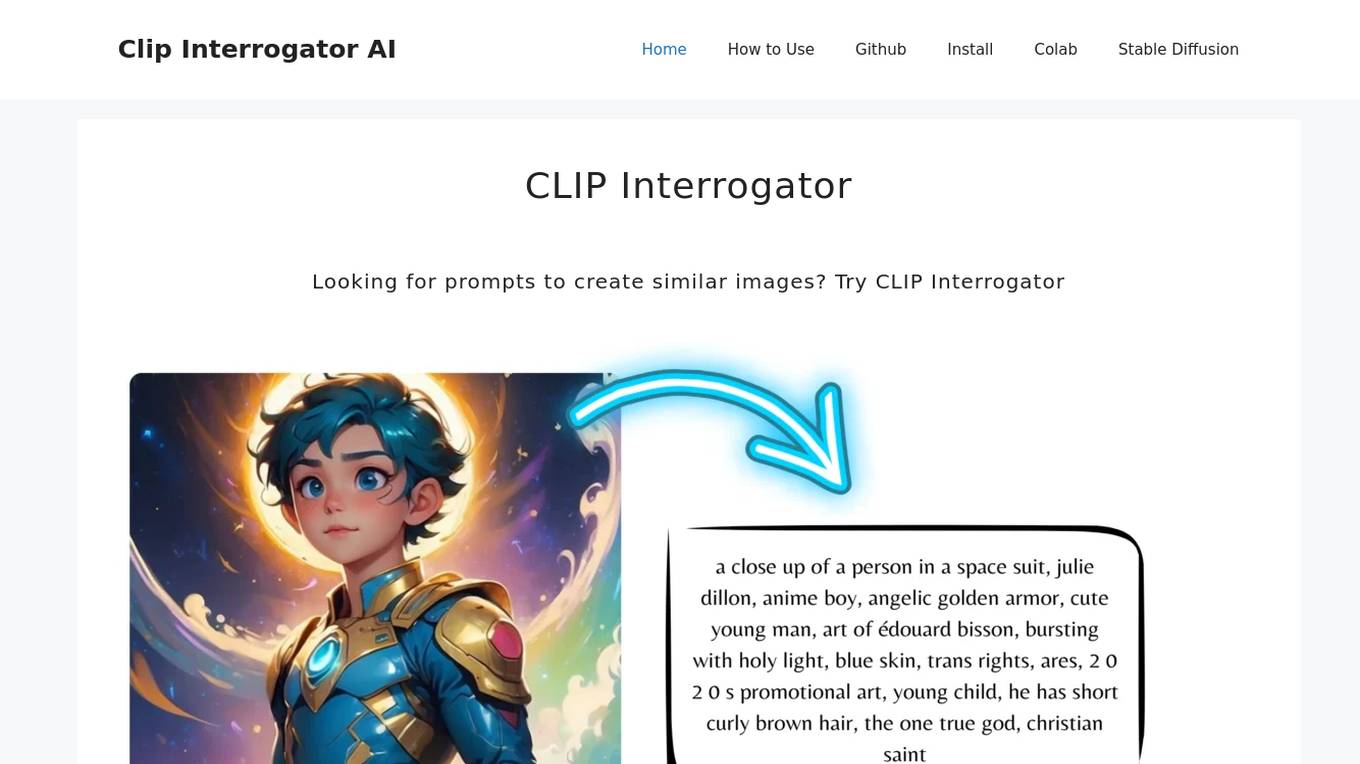
CLIP Interrogator
CLIP Interrogator is a tool that uses the CLIP (Contrastive Language–Image Pre-training) model to analyze images and generate descriptive text or tags. It effectively bridges the gap between visual content and language by interpreting the contents of images through natural language descriptions. The tool is particularly useful for understanding or replicating the style and content of existing images, as it helps in identifying key elements and suggesting prompts for creating similar imagery.
Surveyed.live
Surveyed.live is an AI-powered video survey platform that allows businesses to collect feedback and insights from customers through customizable survey templates. The platform offers features such as video surveys, AI touch response, comprehensible dashboard, Chrome extension, actionable insights, integration, predefined library, appealing survey creation, customer experience statistics, and more. Surveyed.live helps businesses enhance customer satisfaction, improve decision-making, and drive business growth by leveraging AI technology for video reviews and surveys. The platform caters to various industries including hospitality, healthcare, education, customer service, delivery services, and more, providing a versatile solution for optimizing customer relationships and improving overall business performance.
DINGR
DINGR is an AI-powered solution designed to help gamers analyze their performance in League of Legends. The tool uses AI algorithms to provide accurate insights into gameplay, comparing performance metrics with friends and offering suggestions for improvement. DINGR is currently in development, with a focus on enhancing the gaming experience through data-driven analysis and personalized feedback.
Comment Explorer
Comment Explorer is a free tool that allows users to analyze comments on YouTube videos. Users can gain insights into audience engagement, sentiment, and top subjects of discussion. The tool helps content creators understand the impact of their videos and improve interaction with viewers.
AI Tech Debt Analysis Tool
This website is an AI tool that helps senior developers analyze AI tech debt. AI tech debt is the technical debt that accumulates when AI systems are developed and deployed. It can be difficult to identify and quantify AI tech debt, but it can have a significant impact on the performance and reliability of AI systems. This tool uses a variety of techniques to analyze AI tech debt, including static analysis, dynamic analysis, and machine learning. It can help senior developers to identify and quantify AI tech debt, and to develop strategies to reduce it.
4 - Open Source AI Tools

Academic_LLM_Sec_Papers
Academic_LLM_Sec_Papers is a curated collection of academic papers related to LLM Security Application. The repository includes papers sorted by conference name and published year, covering topics such as large language models for blockchain security, software engineering, machine learning, and more. Developers and researchers are welcome to contribute additional published papers to the list. The repository also provides information on listed conferences and journals related to security, networking, software engineering, and cryptography. The papers cover a wide range of topics including privacy risks, ethical concerns, vulnerabilities, threat modeling, code analysis, fuzzing, and more.
HackBot
HackBot is an AI-powered cybersecurity chatbot designed to provide accurate answers to cybersecurity-related queries, conduct code analysis, and scan analysis. It utilizes the Meta-LLama2 AI model through the 'LlamaCpp' library to respond coherently. The chatbot offers features like local AI/Runpod deployment support, cybersecurity chat assistance, interactive interface, clear output presentation, static code analysis, and vulnerability analysis. Users can interact with HackBot through a command-line interface and utilize it for various cybersecurity tasks.
vulnerability-analysis
The NVIDIA AI Blueprint for Vulnerability Analysis for Container Security showcases accelerated analysis on common vulnerabilities and exposures (CVE) at an enterprise scale, reducing mitigation time from days to seconds. It enables security analysts to determine software package vulnerabilities using large language models (LLMs) and retrieval-augmented generation (RAG). The blueprint is designed for security analysts, IT engineers, and AI practitioners in cybersecurity. It requires NVAIE developer license and API keys for vulnerability databases, search engines, and LLM model services. Hardware requirements include L40 GPU for pipeline operation and optional LLM NIM and Embedding NIM. The workflow involves LLM pipeline for CVE impact analysis, utilizing LLM planner, agent, and summarization nodes. The blueprint uses NVIDIA NIM microservices and Morpheus Cybersecurity AI SDK for vulnerability analysis.
Mirror-Flowers
Mirror Flowers is an out-of-the-box code security auditing tool that integrates local static scanning (line-level taint tracking + AST) with AI verification to help quickly discover and locate high-risk issues, providing repair suggestions. It supports multiple languages such as PHP, Python, JavaScript/TypeScript, and Java. The tool offers both single-file and project modes, with features like concurrent acceleration, integrated UI for visual results, and compatibility with multiple OpenAI interface providers. Users can configure the tool through environment variables or API, and can utilize it through a web UI or HTTP API for tasks like single-file auditing or project auditing.
20 - OpenAI Gpts
Phoenix Vulnerability Intelligence GPT
Expert in analyzing vulnerabilities with ransomware focus with intelligence powered by Phoenix Security
学習者弱点ブレイカー(Learner Vulnerabilities Breaker)
児童、生徒、学生のテストの自己採点物を分析し、文化や私生活を考慮した学習のアドバイスを行います。(This program analyzes the self-graded test items of children, students, and students, and advises them on their studies, taking into account their cultural and personal lives.)
Bug Insider
Analyzes bug bounty writeups and cybersecurity reports, providing structured insights and tips.
HackingPT
HackingPT is a specialized language model focused on cybersecurity and penetration testing, committed to providing precise and in-depth insights in these fields.
IDA Pro Plugins recommendation expert.
Ask me to recommend a plugin or script from the official Hex-Rays plugin repository
Wowza Bias Detective
I analyze cognitive biases in scenarios and thoughts, providing neutral, educational insights.
Art Engineer
Analyze and reverse engineer images. Receive style descriptions and image re-creation prompts.