Binary Vulnerability Analysis
AI-powered binary vulnerability scanner
Description:
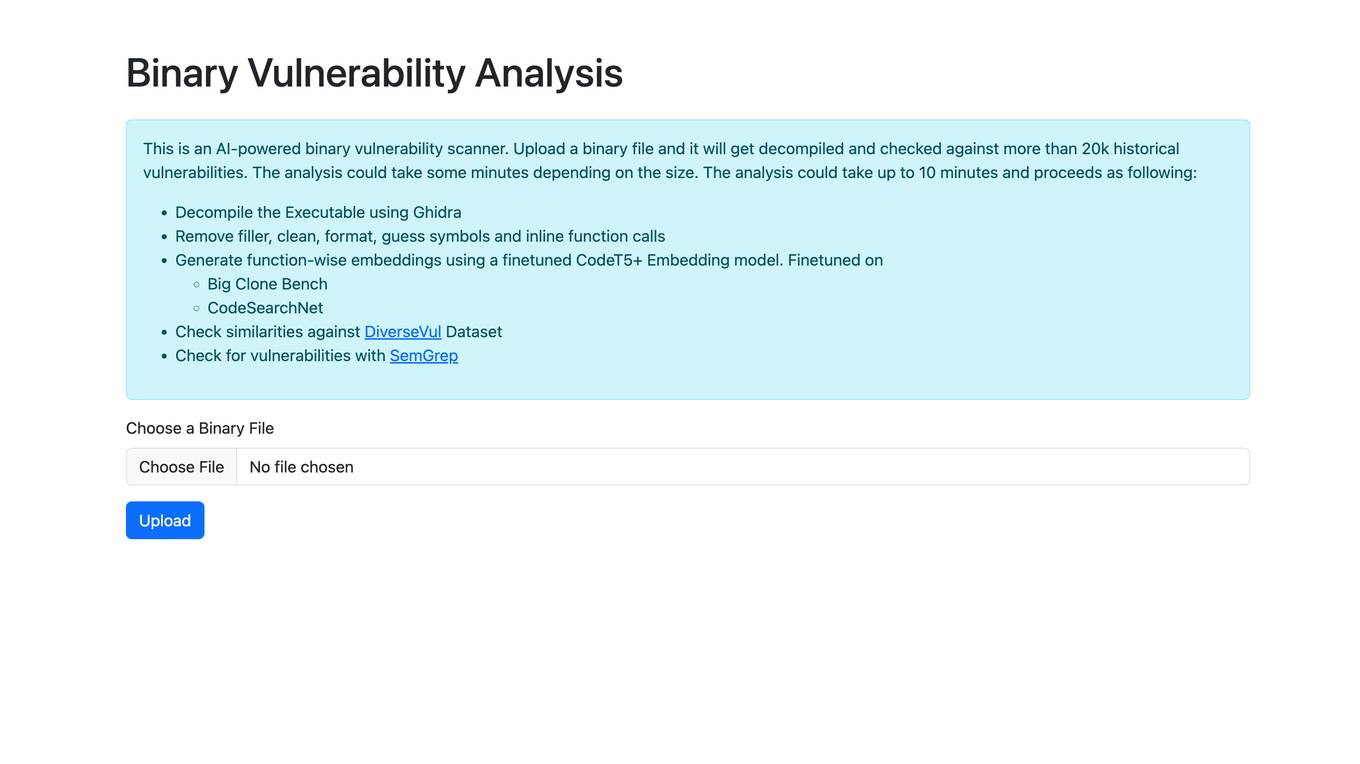
Binary Vulnerability Analysis is an AI-powered binary vulnerability scanner. It decompiles a binary file and checks it against more than 20k historical vulnerabilities. The analysis could take up to 10 minutes and proceeds as following: Decompile the Executable using Ghidra Remove filler, clean, format, guess symbols and inline function calls Generate function-wise embeddings using a finetuned CodeT5+ Embedding model. Finetuned on Big Clone Bench CodeSearchNet Check similarities against DiverseVul Dataset Check for vulnerabilities with SemGrep
For Tasks:
For Jobs:
Features
- Decompile the Executable using Ghidra
- Remove filler, clean, format, guess symbols and inline function calls
- Generate function-wise embeddings using a finetuned CodeT5+ Embedding model
- Finetuned on Big Clone Bench CodeSearchNet
- Check similarities against DiverseVul Dataset
- Check for vulnerabilities with SemGrep
Advantages
- Can identify vulnerabilities in binary files
- Uses AI to power its analysis
- Can decompile and analyze binary files
- Can check against a database of over 20k historical vulnerabilities
- Can generate function-wise embeddings using a finetuned CodeT5+ Embedding model
Disadvantages
- Can take up to 10 minutes to analyze a binary file
- May not be able to identify all vulnerabilities in a binary file
- Requires a binary file to be uploaded for analysis
Frequently Asked Questions
-
Q:What is Binary Vulnerability Analysis?
A:Binary Vulnerability Analysis is an AI-powered binary vulnerability scanner. -
Q:How does Binary Vulnerability Analysis work?
A:Binary Vulnerability Analysis decompiles a binary file and checks it against more than 20k historical vulnerabilities. -
Q:How long does it take to analyze a binary file?
A:The analysis could take up to 10 minutes. -
Q:What are the advantages of using Binary Vulnerability Analysis?
A:Binary Vulnerability Analysis can identify vulnerabilities in binary files, uses AI to power its analysis, can decompile and analyze binary files, can check against a database of over 20k historical vulnerabilities, and can generate function-wise embeddings using a finetuned CodeT5+ Embedding model. -
Q:What are the disadvantages of using Binary Vulnerability Analysis?
A:Binary Vulnerability Analysis can take up to 10 minutes to analyze a binary file, may not be able to identify all vulnerabilities in a binary file, and requires a binary file to be uploaded for analysis.
Alternative AI tools for Binary Vulnerability Analysis
Similar sites
IBM Watsonx
Accelerate responsible, transparent and explainable workflows for generative AI built on third-party platforms
UBIAI
Stop Wasting Time. Accelerate Manual Labeling 10x With The Full Power Of AI-Data Labeling.
Refact.ai
Powerful AI coding assistant that combines completion, refactoring, chat, and more