Hatchet
Your intelligent Incident Response Partner
Hatchet is an AI companion designed to assist on-call engineers in incident response by providing intelligent insights and suggestions based on logs, communications channels, and code analysis. It helps save time and money by automating the triaging and investigation process during critical incidents. The tool is built by engineers with a focus on data security, offering self-hosted deployments, permissions, audit trails, SSO, and version control. Hatchet aims to streamline incident resolution for tier-1 services, enabling faster response and potential problem resolution.
For Tasks:
Click tags to check more tools for each tasksFor Jobs:
Features
Advantages
Disadvantages
Frequently Asked Questions
Alternative AI tools for Hatchet
Similar sites

Hatchet
Hatchet is an AI companion designed to assist on-call engineers in incident response by providing intelligent insights and suggestions based on logs, communications channels, and code analysis. It helps save time and money by automating the triaging and investigation process during critical incidents. The tool is built by engineers with a focus on data security, offering self-hosted deployments, permissions, audit trails, SSO, and version control. Hatchet aims to streamline incident resolution for tier-1 services, enabling faster response and potential problem resolution.
CensysGPT Beta
CensysGPT Beta is a tool that simplifies building queries and empowers users to conduct efficient and effective reconnaissance operations. It enables users to quickly and easily gain insights into hosts on the internet, streamlining the process and allowing for more proactive threat hunting and exposure management.

Dropzone AI
Dropzone AI is an award-winning AI application designed to reinforce Security Operations Centers (SOCs) by providing autonomous AI analysts. It replicates the techniques of elite analysts to autonomously investigate alerts, covering various use cases such as phishing, endpoint, network, cloud, identity, and insider threats. The application offers pre-trained AI agents that work alongside human analysts, automating investigation tasks and providing fast, detailed, and accurate reports. With built-in integrations with major security tools, Dropzone AI aims to reduce Mean Time to Respond (MTTR) and allow analysts to focus on addressing real threats.
Storytell.ai
Storytell.ai is an enterprise-grade AI platform that offers Business-Grade Intelligence across data, focusing on boosting productivity for employees and teams. It provides a secure environment with features like creating project spaces, multi-LLM chat, task automation, chat with company data, and enterprise-AI security suite. Storytell.ai ensures data security through end-to-end encryption, data encryption at rest, provenance chain tracking, and AI firewall. It is committed to making AI safe and trustworthy by not training LLMs with user data and providing audit logs for accountability. The platform continuously monitors and updates security protocols to stay ahead of potential threats.
ArcadianAI
ArcadianAI is a modern security monitoring platform that offers easy and affordable solutions for businesses and individuals. The platform provides security cameras, crime maps, and a 30-day free trial for users to experience its features. ArcadianAI uses AI technology for intrusion detection, smart alerts analytics, AI heatmaps search, and AI detection of people. The platform aims to enhance security measures by intelligently contextualizing, analyzing, and safeguarding premises in real-time using existing CCTV footage.
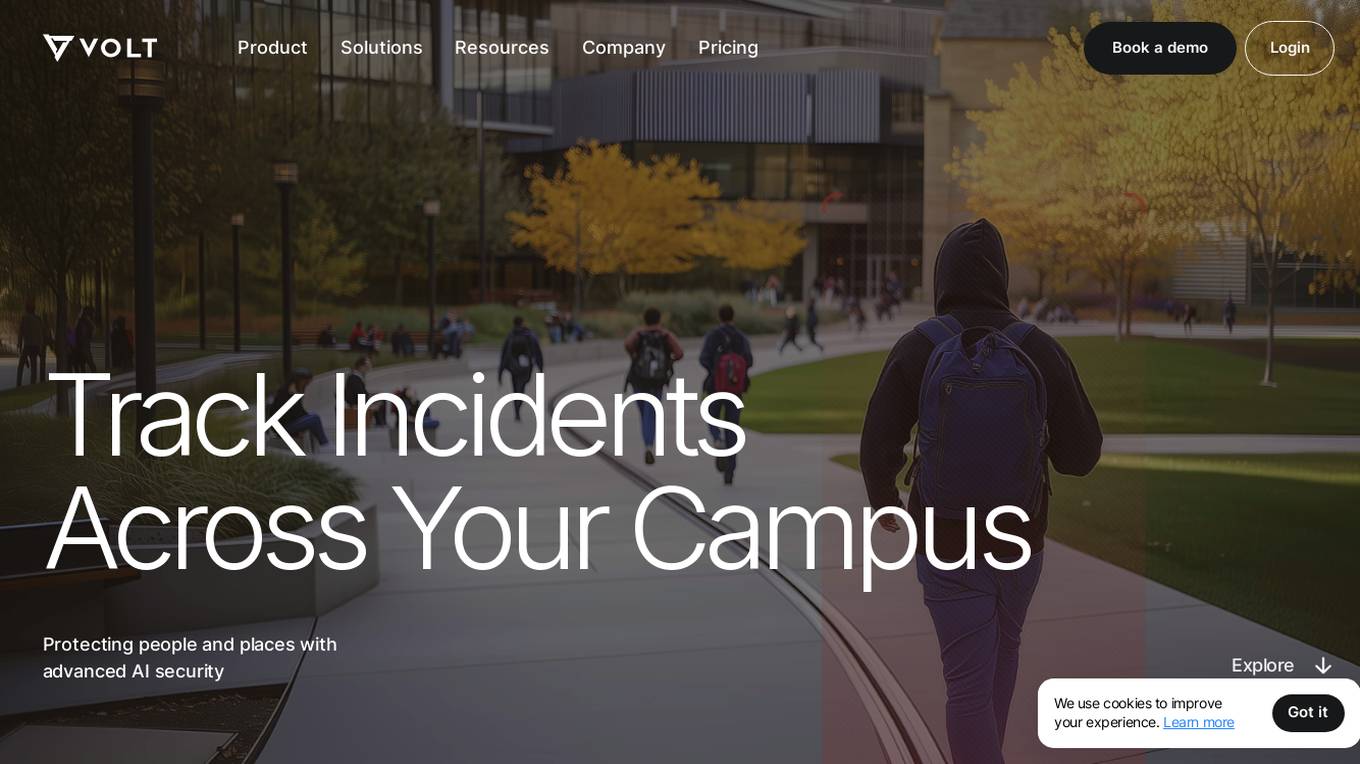
VOLT AI
VOLT AI is a cloud-based enterprise security application that utilizes advanced AI technology to intercept threats in real-time. The application offers solutions for various industries such as education, corporate, and cities, focusing on perimeter security, medical emergencies, and weapons detection. VOLT AI provides features like unified cameras, video intelligence, real-time notifications, automated escalations, and digital twin creation for advanced situational awareness. The application aims to enhance safety and security by detecting security risks and notifying users promptly.
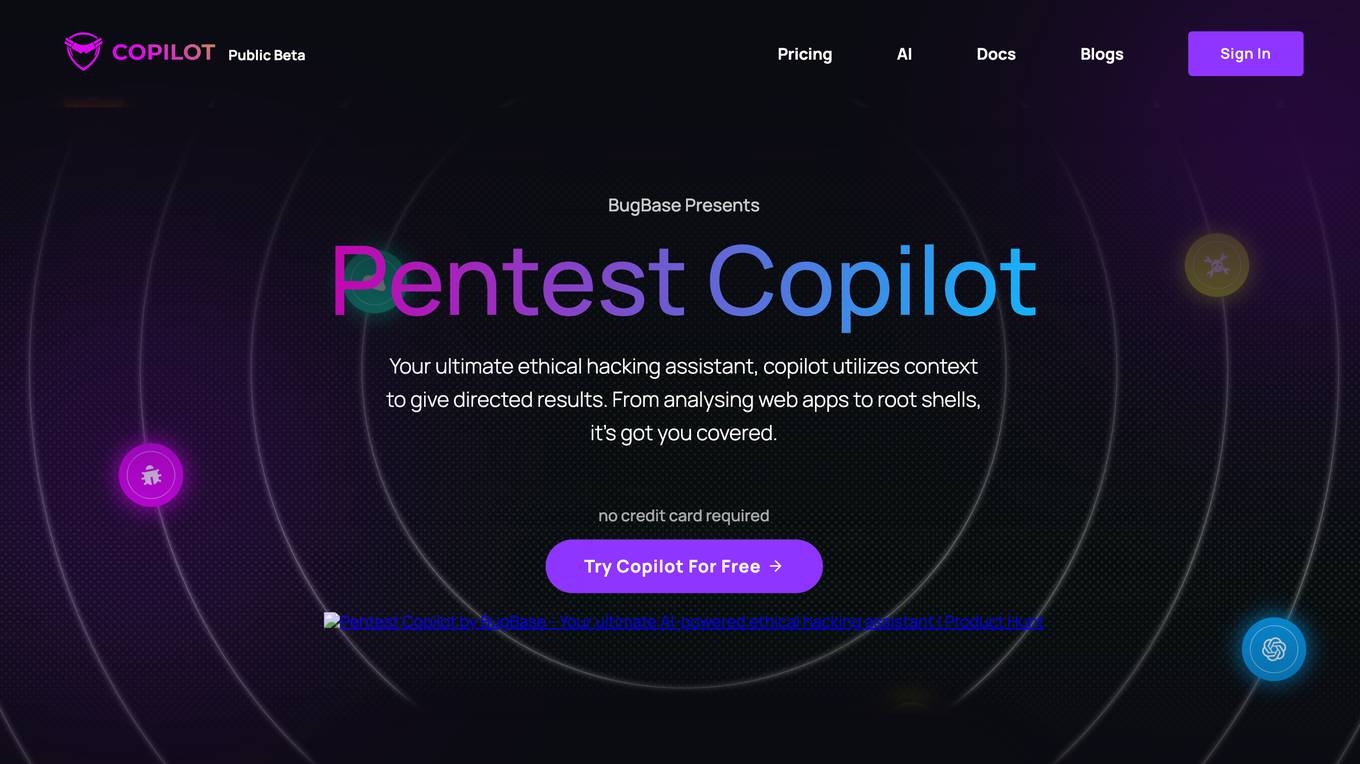
Pentest Copilot
Pentest Copilot by BugBase is an ultimate ethical hacking assistant that guides users through each step of the hacking journey, from analyzing web apps to root shells. It eliminates redundant research, automates payload and command generation, and provides intelligent contextual analysis to save time. The application excels at data extraction, privilege escalation, lateral movement, and leaving no trace behind. With features like secure VPN integration, total control over sessions, parallel command processing, and flexibility to choose between local or cloud execution, Pentest Copilot offers a seamless and efficient hacking experience without the need for Kali Linux installation.
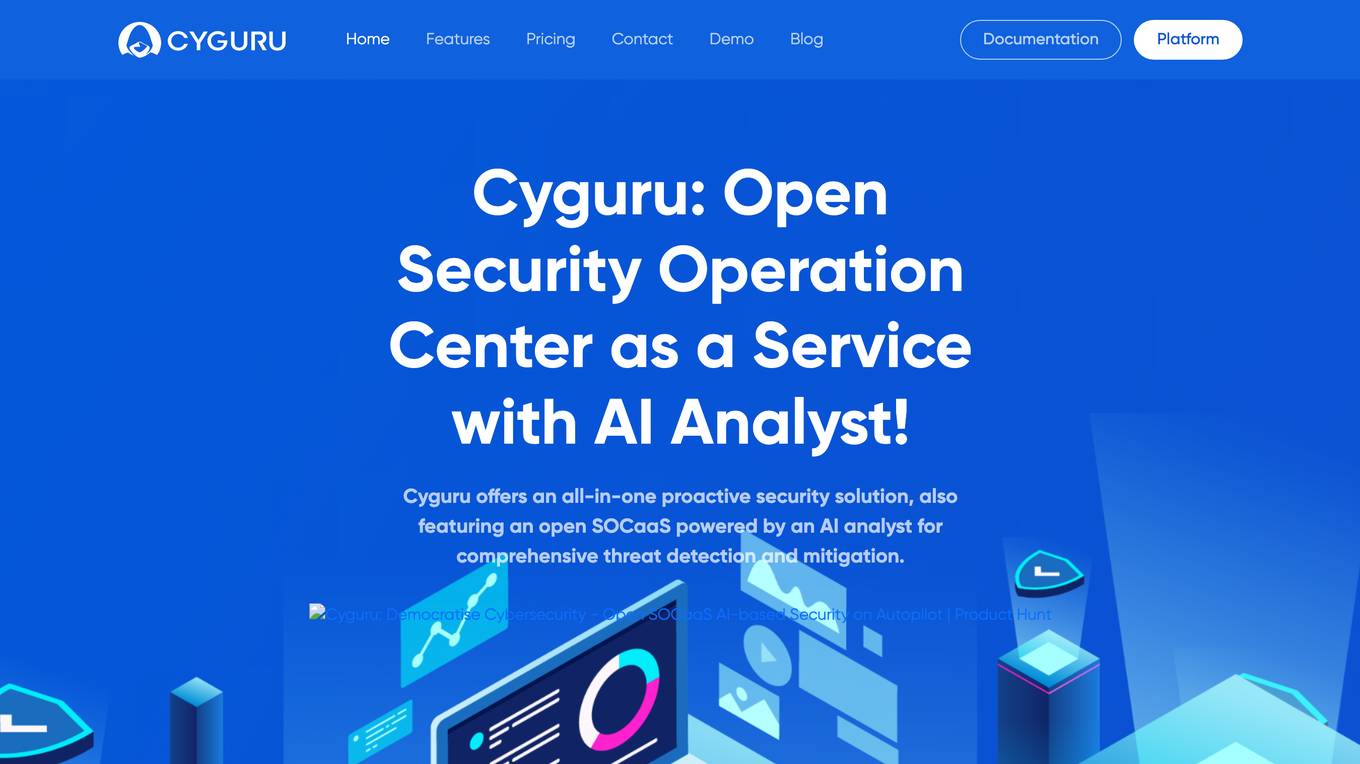
Cyguru
Cyguru is an all-in-one cloud-based AI Security Operation Center (SOC) that offers a comprehensive range of features for a robust and secure digital landscape. Its Security Operation Center is the cornerstone of its service domain, providing AI-Powered Attack Detection, Continuous Monitoring for Vulnerabilities and Misconfigurations, Compliance Assurance, SecPedia: Your Cybersecurity Knowledge Hub, and Advanced ML & AI Detection. Cyguru's AI-Powered Analyst promptly alerts users to any suspicious behavior or activity that demands attention, ensuring timely delivery of notifications. The platform is accessible to everyone, with up to three free servers and subsequent pricing that is more than 85% below the industry average.
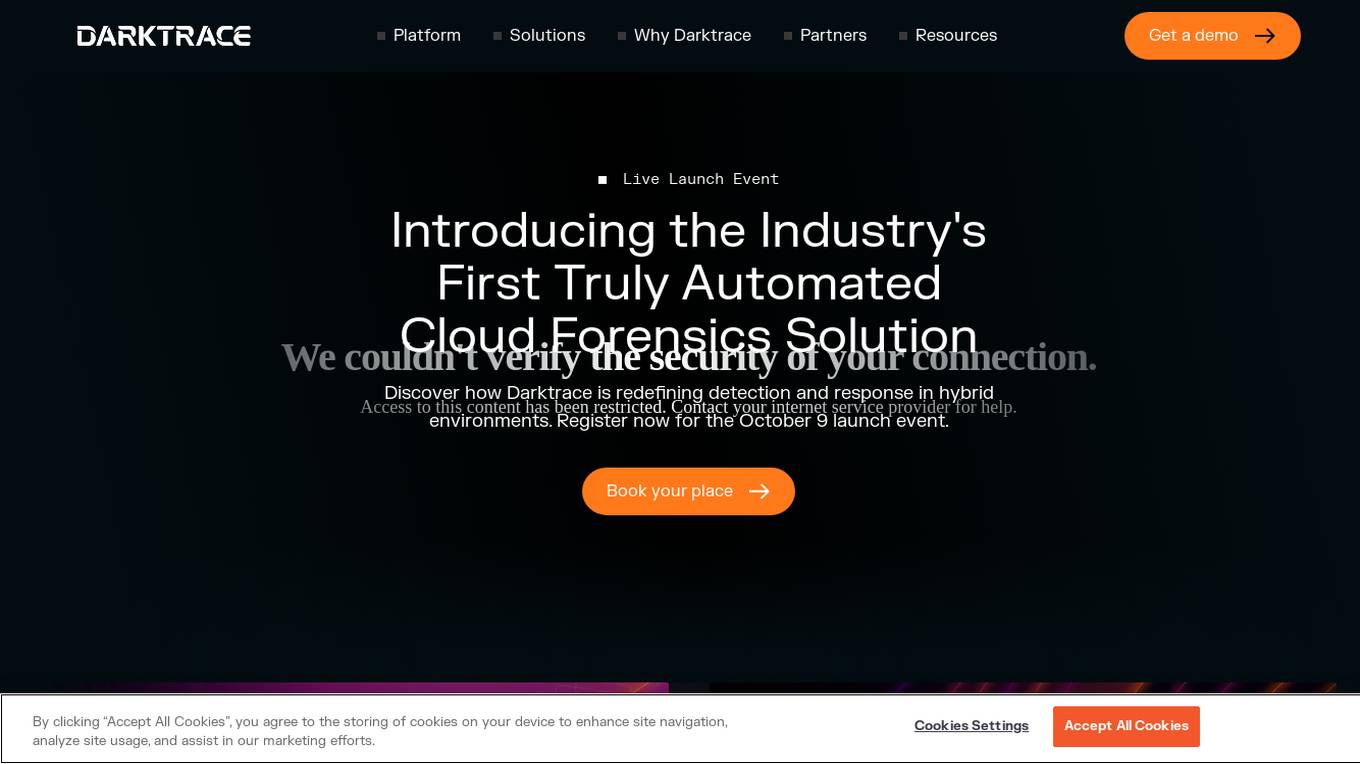
Darktrace
Darktrace is an essential AI cybersecurity platform that offers proactive protection, cloud-native AI security, comprehensive risk management, and user protection across various devices. It accelerates triage by 10x, defends with confidence, and connects with various integrations. Darktrace ActiveAI Security Platform spots novel threats across organizations, providing solutions for ransomware, APTs, phishing, data loss, and more. With a focus on defense, Darktrace aims to transform cybersecurity by detecting and responding to known and novel threats in real-time.
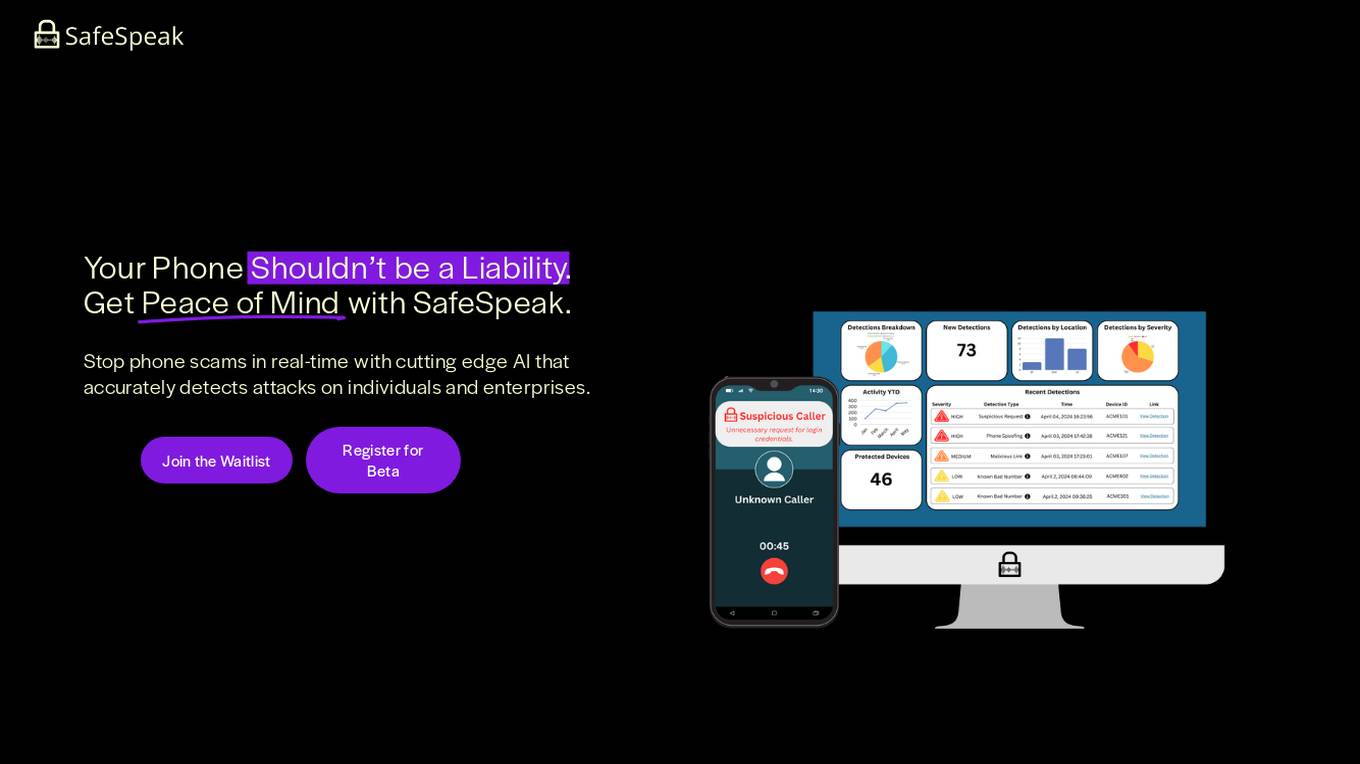
SafeSpeak
SafeSpeak is an AI-powered mobile security solution that protects users from phone scams, SIM swaps, and other malicious activities. It uses advanced machine learning and large language models to detect and block threats in real-time. SafeSpeak offers a range of features for both personal and business use, including malicious behavior detection, community immunity, SIM swap detection, weekly and monthly reporting, quick and easy setup, admin dashboard, extensible API, custom reporting, and visibility into tactics, techniques, and procedures (TTPs).
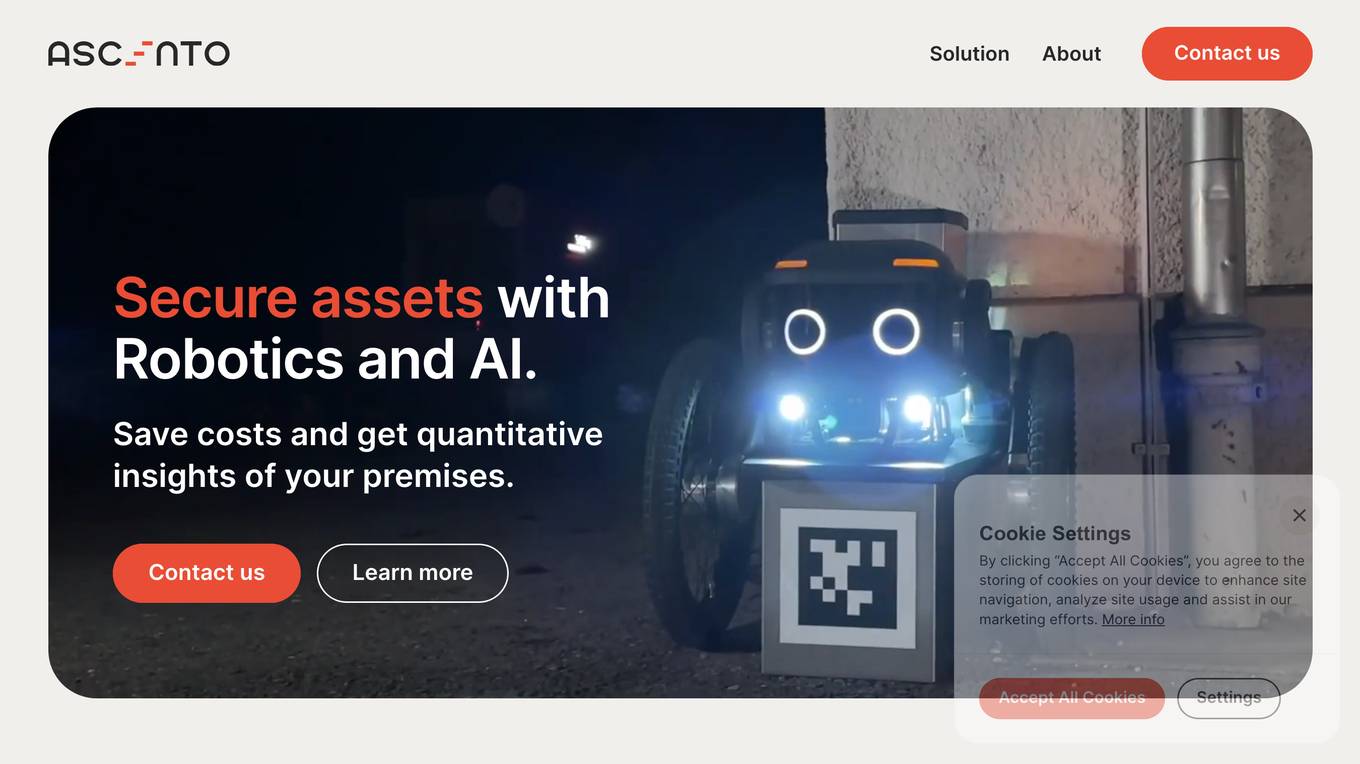
Ascento
Ascento is an AI-powered security solution that combines robotics and artificial intelligence to secure assets and provide quantitative insights of premises. The application offers features such as detecting people on premises, verifying perimeter integrity, recording property lights, scanning for thermal anomalies, controlling parking lots, and checking doors and windows. Ascento provides advantages like faster threat detection with greater accuracy, cost reduction, autonomous all-terrain robot capabilities, encrypted live communication, and integration with existing video management systems. However, some disadvantages include the need for immediate cost-benefits, training and onboarding requirements, and limited battery life for autonomous charging. The application is suitable for various industries and offers a turnkey solution with 24/7 support and fast replacements.
icetana AI
icetana AI is a leading AI security video analytics software product suite that offers real-time surveillance, transforming data into actionable insights. It includes features like license plate recognition, facial recognition, and automated security workflows. The application helps in detecting unusual events, such as loitering, fire, and smoke, and provides solutions for various industries like safe cities, mall management, and retail security. icetana AI is known for its self-learning AI, real-time event detection, reduced false alarms, easy configuration, and scalability, making it a comprehensive solution for security operations.
Polymer DSPM
Polymer DSPM is an AI-driven Data Security Posture Management platform that offers Data Loss Prevention (DLP) and Breach Prevention solutions. It provides real-time data visibility, adaptive controls, and automated remediation to prevent data breaches. The platform empowers users to actively manage human-based risks and fosters enterprise-wide behavior change through real-time nudges and risk scoring. Polymer helps organizations secure their data in the age of AI by guiding employees in real-time to prevent accidental sharing of confidential information. It integrates with popular chat, file storage, and GenAI tools to protect sensitive data and reduce noise and data exposure. The platform leverages AI to contextualize risk, trigger security workflows, and actively nudge employees to reduce risky behavior over time.
Bricklayer AI
Bricklayer AI is an automated AI security team that empowers Security Operations Centers (SOCs) to manage alerts, incidents, and threats efficiently. It offers autonomous AI agents designed to work collaboratively with human experts, enabling faster and more effective security operations. Bricklayer AI helps organizations stay ahead of cyber threats by automating labor-intensive tasks and providing real-time analysis and response.
Pontus
Pontus is an AI tool that enables users to build AI models with trust, manage risk, and ensure compliance effortlessly. It offers features like smart anonymization, rapid audit, and liability reduction, along with privacy-enhancing technology. Pontus allows for on-premise deployment, role-based access controls, and toxicity checking to prevent inappropriate content. The application is designed to work seamlessly with common LLM providers, making it a valuable asset for industries like healthcare, finance, and research.
CYBER AI
CYBER AI is a security report savant powered by DEPLOYH.AI that simplifies cybersecurity for businesses. It offers a range of features to help organizations understand, unlock, and uncover security threats, including security reports, databreach reports, logs, and threat hunting. With CYBER AI, businesses can gain a comprehensive view of their security posture and take proactive steps to mitigate risks.
For similar tasks
Resolvd
Resolvd is an AI-powered incident resolution platform that creates a knowledge base of logs, data sources, and applications to autonomously diagnose and resolve incidents. It helps cut time to response by 50%, return hours to developers, simplify data querying, and provide automated anomaly detection. Resolvd uses AI/ML models to analyze logs, aggregate critical context, and deliver insights in workflow, seamlessly integrating with existing systems like Slack, Jira, and PagerDuty.

Hatchet
Hatchet is an AI companion designed to assist on-call engineers in incident response by providing intelligent insights and suggestions based on logs, communications channels, and code analysis. It helps save time and money by automating the triaging and investigation process during critical incidents. The tool is built by engineers with a focus on data security, offering self-hosted deployments, permissions, audit trails, SSO, and version control. Hatchet aims to streamline incident resolution for tier-1 services, enabling faster response and potential problem resolution.
Koxy AI
Koxy AI is an AI-powered serverless back-end platform that allows users to build globally distributed, fast, secure, and scalable back-ends with no code required. It offers features such as live logs, smart errors handling, integration with over 80,000 AI models, and more. Koxy AI is designed to help users focus on building the best service possible without wasting time on security and latency concerns. It provides a No-SQL JSON-based database, real-time data synchronization, cloud functions, and a drag-and-drop builder for API flows.
SentinelOne
SentinelOne is an advanced enterprise cybersecurity AI platform that offers a comprehensive suite of AI-powered security solutions for endpoint, cloud, and identity protection. The platform leverages artificial intelligence to anticipate threats, manage vulnerabilities, and protect resources across the entire enterprise ecosystem. With features such as Singularity XDR, Purple AI, and AI-SIEM, SentinelOne empowers security teams to detect and respond to cyber threats in real-time. The platform is trusted by leading enterprises worldwide and has received industry recognition for its innovative approach to cybersecurity.
Helicone
Helicone is an open-source platform designed for developers, offering observability solutions for logging, monitoring, and debugging. It provides sub-millisecond latency impact, 100% log coverage, industry-leading query times, and is ready for production-level workloads. Trusted by thousands of companies and developers, Helicone leverages Cloudflare Workers for low latency and high reliability, offering features such as prompt management, uptime of 99.99%, scalability, and reliability. It allows risk-free experimentation, prompt security, and various tools for monitoring, analyzing, and managing requests.
Microtica AI Deployment Tool
Microtica AI Deployment Tool is an advanced platform that leverages artificial intelligence to streamline the deployment process of cloud infrastructure. The tool offers features such as incident investigation with AI assistance, designing and deploying cloud infrastructure using natural language, and automated deployments. With Microtica, users can easily analyze logs, metrics, and system state to identify root causes and solutions, as well as get infrastructure-as-code and architecture diagrams. The platform aims to simplify the deployment process and enhance productivity by integrating AI capabilities into the workflow.
BigPanda
BigPanda is an AI-powered ITOps platform that helps businesses automatically identify actionable alerts, proactively prevent incidents, and ensure service availability. It uses advanced AI/ML algorithms to analyze large volumes of data from various sources, including monitoring tools, event logs, and ticketing systems. BigPanda's platform provides a unified view of IT operations, enabling teams to quickly identify and resolve issues before they impact business-critical services.
For similar jobs

Resolvd
Resolvd is an AI-powered incident resolution platform that creates a knowledge base of logs, data sources, and applications to autonomously diagnose and resolve incidents. It helps cut time to response by 50%, return hours to developers, simplify data querying, and provide automated anomaly detection. Resolvd uses AI/ML models to analyze logs, aggregate critical context, and deliver insights in workflow, seamlessly integrating with existing systems like Slack, Jira, and PagerDuty.

Hatchet
Hatchet is an AI companion designed to assist on-call engineers in incident response by providing intelligent insights and suggestions based on logs, communications channels, and code analysis. It helps save time and money by automating the triaging and investigation process during critical incidents. The tool is built by engineers with a focus on data security, offering self-hosted deployments, permissions, audit trails, SSO, and version control. Hatchet aims to streamline incident resolution for tier-1 services, enabling faster response and potential problem resolution.
Tracecat
Tracecat is an open-source security automation platform that helps you automate security alerts, build AI-assisted workflows, orchestrate alerts, and close cases fast. It is a Tines / Splunk SOAR alternative that is built for builders and allows you to experiment for free. You can deploy Tracecat on your own infrastructure or use Tracecat Cloud with no maintenance overhead. Tracecat is Apache-2.0 licensed, which means it is open vision, open community, and open development. You can have your say in the future of security automation. Tracecat is no-code first, but you can also code as well. You can build automations fast with no-code and customize without vendor lock-in using Python. Tracecat has a click-and-drag workflow builder that allows you to automate SecOps using pre-built actions (API calls, webhooks, data transforms, AI tasks, and more) combined into workflows. No code is required. Tracecat also has a built-in case management system that allows you to open cases directly from workflows and track and manage security incidents all in one platform.
CrowdStrike
CrowdStrike is a leading cybersecurity platform that uses artificial intelligence (AI) to protect businesses from cyber threats. The platform provides a unified approach to security, combining endpoint security, identity protection, cloud security, and threat intelligence into a single solution. CrowdStrike's AI-powered technology enables it to detect and respond to threats in real-time, providing businesses with the protection they need to stay secure in the face of evolving threats.
CrowdStrike
CrowdStrike is a cloud-based cybersecurity platform that provides endpoint protection, threat intelligence, and incident response services. It uses artificial intelligence (AI) to detect and prevent cyberattacks. CrowdStrike's platform is designed to be scalable and easy to use, and it can be deployed on-premises or in the cloud. CrowdStrike has a global customer base of over 23,000 organizations, including many Fortune 500 companies.
Parity
Parity is the world's first AI SRE tool designed to assist on-call engineers working with Kubernetes. It acts as the first line of defense by conducting investigations, determining root causes, and suggesting remediation before the engineer even opens their laptop. With features like Root Cause Analysis in Seconds, Intelligent Runbook Execution, and the ability to chat directly with the cluster, Parity streamlines incident response and enhances operational efficiency.
Stellar Cyber
Stellar Cyber is an AI-driven unified security operations platform powered by Open XDR. It offers a single platform with NG-SIEM, NDR, and Open XDR, providing security capabilities to take control of security operations. The platform helps organizations detect, correlate, and respond to threats fast using AI technology. Stellar Cyber is designed to protect the entire attack surface, improve security operations performance, and reduce costs while simplifying security operations.

Dropzone AI
Dropzone AI is an award-winning AI application designed to reinforce Security Operations Centers (SOCs) by providing autonomous AI analysts. It replicates the techniques of elite analysts to autonomously investigate alerts, covering various use cases such as phishing, endpoint, network, cloud, identity, and insider threats. The application offers pre-trained AI agents that work alongside human analysts, automating investigation tasks and providing fast, detailed, and accurate reports. With built-in integrations with major security tools, Dropzone AI aims to reduce Mean Time to Respond (MTTR) and allow analysts to focus on addressing real threats.
Masterhackers
Masterhackers is an all-in-one cybersecurity application designed to help cybersecurity professionals and students prepare for certifications and interviews. The platform offers a comprehensive set of tools and resources, including practice tests, flashcards, mock interviews, and personalized feedback with AI. Trusted by students worldwide, Masterhackers aims to enhance users' cybersecurity skills and knowledge through interactive learning experiences.
Kubiya
Kubiya is an AI-powered platform designed to reduce Time-To-Automation for Developer and Infrastructure Operations teams. It allows users to focus on high-impact work by automating routine tasks and processes, powered by an Agentic-Native Platform. Kubiya is trusted by world-class engineering and operations teams, offering features such as AI teammates, JIT Permissions, Infrastructure Provisioning, Help Desk support, and Incident Response automation.
Palo Alto Networks
Palo Alto Networks is a cybersecurity company offering advanced security solutions powered by Precision AI to protect modern enterprises from cyber threats. The company provides network security, cloud security, and AI-driven security operations to defend against AI-generated threats in real time. Palo Alto Networks aims to simplify security and achieve better security outcomes through platformization, intelligence-driven expertise, and proactive monitoring of sophisticated threats.
Torq
Torq is an AI-driven platform that offers Security Hyperautomation Solutions, empowering security teams to detect, prioritize, and respond to threats faster. It provides a range of features and capabilities such as AI Agents, AI SOC Analyst, Case Management, and Integrations. Torq is trusted by top security teams worldwide and is recognized for its ability to mitigate alert fatigue, false positives, and staff burnout. The platform is designed to usher in the era of Autonomous SOC by harnessing AI to enhance security operations.

Bricklayer AI
Bricklayer AI is an automated AI security team that empowers Security Operations Centers (SOCs) to manage alerts, incidents, and threats efficiently. It offers autonomous AI agents designed to work collaboratively with human experts, enabling faster and more effective security operations. Bricklayer AI helps organizations stay ahead of cyber threats by automating labor-intensive tasks and providing real-time analysis and response.

Darktrace
Darktrace is an essential AI cybersecurity platform that offers proactive protection, cloud-native AI security, comprehensive risk management, and user protection across various devices. It accelerates triage by 10x, defends with confidence, and connects with various integrations. Darktrace ActiveAI Security Platform spots novel threats across organizations, providing solutions for ransomware, APTs, phishing, data loss, and more. With a focus on defense, Darktrace aims to transform cybersecurity by detecting and responding to known and novel threats in real-time.
XenonStack
XenonStack is an AI application that offers a reasoning foundry for agentic enterprises. It provides unified reasoning foundation enabling seamless orchestration, analytics, infrastructure, and trust across intelligent ecosystems. The platform includes various AI tools such as Akira AI for reasoning and agent orchestration, ElixirData for agentic analytics intelligence, NexaStack for agentic infrastructure automation, MetaSecure for trust, compliance, and defense, and Neural AI for agentic intelligence & autonomous innovation. It also offers pre-built autonomous agents for domain-specific intelligence, seamless integrations, and governed enterprise deployment.
Cloud Observability Middleware
The website provides Full-Stack Cloud Observability services with a focus on Middleware. It offers comprehensive monitoring and analysis tools to help businesses optimize their cloud infrastructure performance. The platform enables users to gain insights into their middleware applications, identify bottlenecks, and improve overall system efficiency.
Security Certificate Advisor
The website provides information about a privacy error related to a security certificate expiration for the IP address 147.139.135.71. It warns users about potential data theft and advises on correcting system clock settings. The site also mentions Certificate Transparency and offers options to enhance web security.
GetLuminal
GetLuminal.com is a website that provides information about a security certificate error related to the website itself. The site warns users about potential privacy risks and advises on actions to take when encountering such errors. It offers insights into security certificate expiration, potential threats from attackers, and guidance on system clock settings. Users can learn about security measures, certificate transparency, and how to enhance web security.
OpenResty
The website is currently displaying a '403 Forbidden' error, which indicates that the server understood the request, but is refusing to fulfill it. This error message is often encountered when trying to access a webpage or resource that is restricted or unavailable to the user. The 'openresty' mentioned in the text refers to a web platform based on NGINX and LuaJIT, commonly used for building high-performance web applications. It is designed to handle a large number of concurrent connections and requests efficiently.
notionsmith.ai
The website notionsmith.ai appears to be experiencing a privacy error related to its security certificate. The error message indicates that the connection is not private and warns of potential information theft. The site's security certificate is issued by Microsoft Azure RSA TLS Issuing CA 08, with the subject *.azurewebsites.net. The error message suggests that the site's security certificate common name is invalid, potentially due to a misconfiguration or an attacker intercepting the connection. Users are advised to proceed to the site at their own risk, as it is flagged as unsafe.

Dialogly
The website dialogly.ai appears to be experiencing a privacy error related to its security certificate. Users are warned that their connection may not be private and attackers could potentially steal sensitive information such as passwords, messages, or credit card details. The site's security certificate is not trusted by the user's computer operating system, which could be due to misconfiguration or a potential attack. The warning advises users to proceed to the site at their own risk, as it is deemed unsafe.
403 Forbidden
The website seems to be experiencing a 403 Forbidden error, which indicates that the server is refusing to respond to the request. This error is often caused by incorrect permissions on the server or misconfigured security settings. The message '403 Forbidden' is a standard HTTP status code that indicates the server understood the request but refuses to authorize it. It is not related to AI technology or applications.
OpenResty Server Manager
The website seems to be experiencing a 403 Forbidden error, which typically indicates that the server is denying access to the requested resource. This error is often caused by incorrect permissions or misconfigurations on the server side. The message 'openresty' suggests that the server may be using the OpenResty web platform. Users encountering this error may need to contact the website administrator for assistance in resolving the issue.
Escape
Escape is an AI-powered Dynamic Application Security Testing (DAST) tool designed to work seamlessly with modern technology stacks, focusing on testing business logic and helping developers remediate vulnerabilities efficiently. It provides a comprehensive platform for API security, including API discovery, security testing, and GraphQL support. Escape offers features such as AI-powered DAST, API discovery & security, business logic security testing, CI/CD integration, and tailored remediations. The tool aims to streamline security workflows, improve risk reduction, and simplify compliance management for various industries.