Best AI tools for< Detect Security Bugs >
20 - AI tool Sites
Senior AI
Senior AI is a platform that leverages Artificial Intelligence to help individuals and companies develop and manage software products more efficiently and securely. It offers codebase awareness, bug analysis, security optimization, and productivity enhancements, making software development faster and more reliable. The platform provides different pricing tiers suitable for individuals, power users, small teams, growing teams, and large teams, with the option for enterprise solutions. Senior AI aims to supercharge software development with an AI-first approach, guiding users through the development process and providing tailored code suggestions and security insights.
nunu.ai
nunu.ai is an AI-powered platform designed to revolutionize game testing by leveraging AI agents to conduct end-to-end tests at scale. By automating repetitive tasks, the platform significantly reduces manual QA costs for game studios. With features like human-like testing, multi-platform support, and enterprise-grade security, nunu.ai offers a comprehensive solution for game developers seeking efficient and reliable testing processes.
Bugasura
Bugasura is an AI-enabled bug management software designed for modern technology teams to track, report, and manage issues efficiently. It offers powerful tools such as test management, issue tracker, bug reporters, and performance monitoring. With AI capabilities, Bugasura streamlines the bug tracking process, empowers teams to tackle complex challenges, and provides contextual issue reporting. The platform is known for its simplicity, speed, and effectiveness in managing requirements, tests, and test runs. Bugasura Spaces, an exclusive community for tech leaders, offers valuable resources, blog posts, release notes, and product roadmap insights. Bugasura prioritizes privacy and security with end-to-end encryption and secure authentication protocols.

Start Left® Security
Start Left® Security is an AI-driven application security posture management platform that empowers product teams to automate secure-by-design software from people to cloud. The platform integrates security into every facet of the organization, offering a unified solution that aligns with business goals, fosters continuous improvement, and drives innovation. Start Left® Security provides a gamified DevSecOps experience with comprehensive security capabilities like SCA, SBOM, SAST, DAST, Container Security, IaC security, ASPM, and more.

yujo.io.tilda.ws
The website yujo.io.tilda.ws is experiencing a privacy error related to its security certificate. Users are warned that their connection may not be private, potentially exposing sensitive information like passwords, messages, or credit card details to attackers. The site's security certificate is not trusted by the computer's operating system, leading to a warning message for users. The error message advises caution and suggests that the issue may be due to misconfiguration or a potential attack on the connection. Users are given the option to proceed to the site at their own risk, despite the security concerns.
furwee.ai
The website furwee.ai appears to be experiencing a privacy error related to its security certificate. The error message indicates that the connection may not be private, potentially exposing sensitive information to attackers. The site's security certificate is issued by Go Daddy Secure Certificate Authority - G2 but does not match the domain admin.animaticmedia.com, leading to a common name invalidity error. Users are advised to proceed with caution due to the potential security risks associated with the site.
Vinetribe.co
Vinetribe.co is a website that appears to be experiencing a privacy error related to its security certificate. The site is currently not considered safe due to a mismatch in the security certificate, potentially indicating a security risk for visitors. The error message suggests that the site's security certificate is issued for *.squarespace.com, not vinetribe.co, which could lead to information theft by attackers. Users are advised to proceed with caution and avoid entering sensitive information on the site until the security issue is resolved.
OpenBuckets
OpenBuckets is a web application designed to help users find and secure open buckets in cloud storage systems. It provides a user-friendly interface for scanning and identifying unprotected buckets, allowing users to take necessary actions to secure their data. With OpenBuckets, users can easily detect potential security risks and prevent unauthorized access to their sensitive information stored in the cloud.
VIDOC
VIDOC is an AI-powered security engineer that automates code review and penetration testing. It continuously scans and reviews code to detect and fix security issues, helping developers deliver secure software faster. VIDOC is easy to use, requiring only two lines of code to be added to a GitHub Actions workflow. It then takes care of the rest, providing developers with a tailored code solution to fix any issues found.
Tokenomist.ai
Tokenomist.ai is an AI-powered security service website that helps protect against online attacks by enabling cookies and blocking malicious activities. It uses advanced algorithms to detect and prevent security threats, ensuring a safe browsing experience for users. The platform is designed to safeguard websites from potential risks and vulnerabilities, offering a reliable security solution for online businesses and individuals.
LMarena.ai
LMarena.ai is an AI-powered security service that protects websites from online attacks by enabling cookies and blocking malicious activities. It uses advanced algorithms to detect and prevent security threats, ensuring a safe browsing experience for users. The service is designed to safeguard websites from various types of attacks, such as SQL injections and data manipulation. LMarena.ai offers a reliable and efficient security solution for website owners to maintain the integrity and performance of their online platforms.
Link Shield
Link Shield is an AI-powered malicious URL detection API platform that helps protect online security. It utilizes advanced machine learning algorithms to analyze URLs and identify suspicious activity, safeguarding users from phishing scams, malware, and other harmful threats. The API is designed for ease of integration, affordability, and flexibility, making it accessible to developers of all levels. Link Shield empowers businesses to ensure the safety and security of their applications and online communities.
DryRun Security
DryRun Security is an AI-driven application security tool that provides Contextual Security Analysis to detect and prevent logic flaws, authorization gaps, IDOR, and other code risks. It offers features like code insights, natural language code policies, and customizable notifications and reporting. The tool benefits CISOs, security leaders, and developers by enhancing code security, streamlining compliance, increasing developer engagement, and providing real-time feedback. DryRun Security supports various languages and frameworks and integrates with GitHub and Slack for seamless collaboration.
Engage AI Security
The website new.engage-ai.co is an AI application designed to enhance security on the web by providing warnings and information about potential privacy errors and security threats. It helps users understand and address issues related to security certificates, connection safety, and potential attacks. The application aims to improve online security by alerting users to potential risks and guiding them on how to proceed safely.
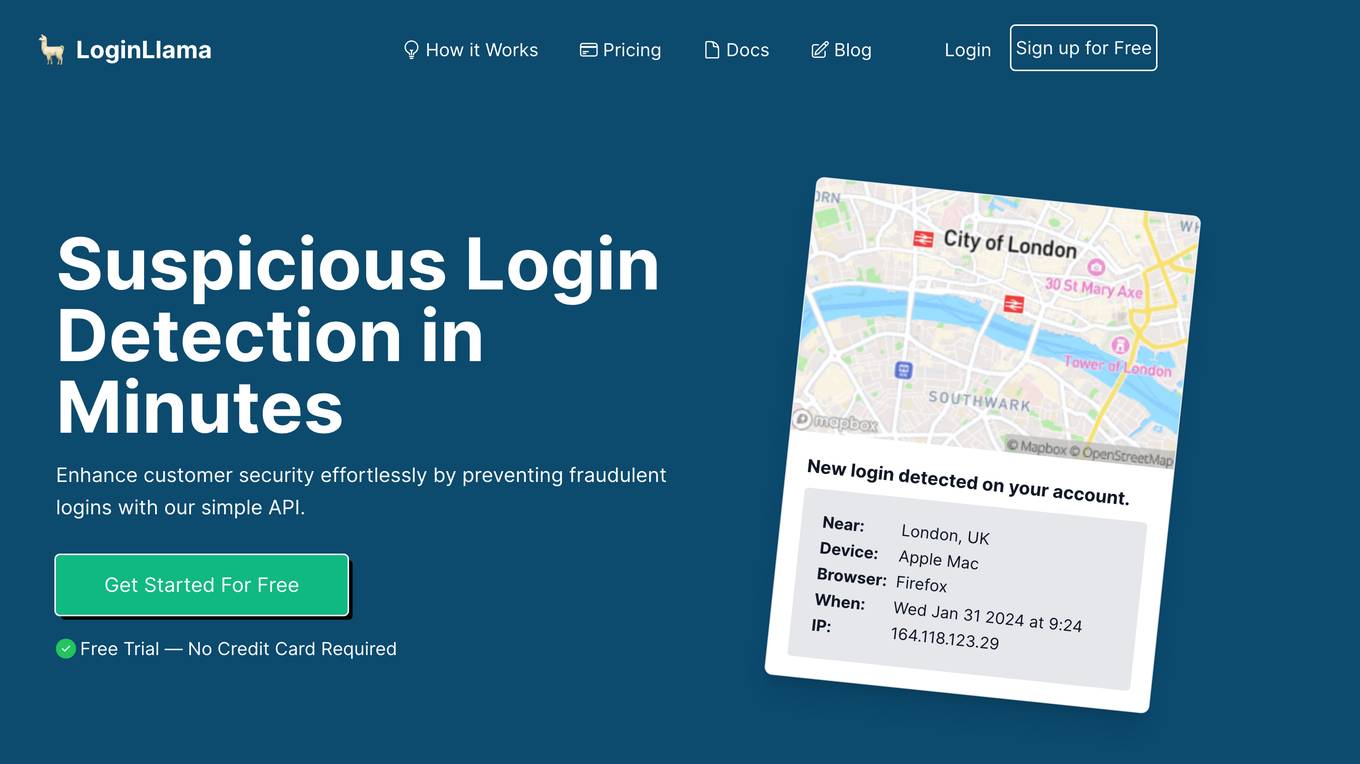
LoginLlama
LoginLlama is an AI-powered suspicious login detection tool designed for developers to enhance customer security effortlessly by preventing fraudulent logins. It offers real-time fraud detection, AI-powered login behavior insights, and easy integration through REST API and official libraries. The tool evaluates login attempts based on multiple ranking factors, historic behavior analysis, AI analysis, request origin, and user agent data to provide enhanced security measures.
Abnormal Security
Abnormal Security is an AI-powered platform that leverages superhuman understanding of human behavior to protect against email threats such as phishing, social engineering, and account takeovers. The platform is trusted by over 3,000 customers, including 25% of the Fortune 500 companies. Abnormal Security offers a comprehensive cloud email security solution, behavioral anomaly detection, SaaS security, and autonomous AI security agents to provide multi-layered protection against advanced email attacks. The platform is recognized as a leader in email security and AI-native security, delivering unmatched protection and reducing the risk of phishing attacks by 90%.
Prompt Security
Prompt Security is a platform that secures all uses of Generative AI in the organization: from tools used by your employees to your customer-facing apps.

Metasoma Web Security
The website www.metasoma.ai is experiencing a privacy error due to an expired security certificate. Users are warned that their information may be at risk of theft. The site is advised to enhance security measures to protect user data and prevent potential attacks.

TeddyAI Web Security Checker
The website teddyai.oiedu.co.uk appears to be experiencing a privacy error, indicating that the connection is not private. The error message warns that attackers might be attempting to steal sensitive information such as passwords, messages, or credit card details. The security certificate for the website is from cpcalendars.bigcityrealty.net, suggesting a potential misconfiguration or a security threat. Users are advised to proceed with caution due to the security risks associated with the site.
VULNWatch
VULNWatch is a web security platform that simplifies and makes website security accessible. The platform offers automated assessments using AI-powered tools with over 13 years of experience. It empowers business owners and developers to identify and address vulnerabilities quickly and easily in one place. VULNWatch provides effective web security assessment, including fingerprinting, protection against SQL injections, and web shells, with a focus on communication and collaboration with clients to ensure tailored cybersecurity solutions.
1 - Open Source AI Tools
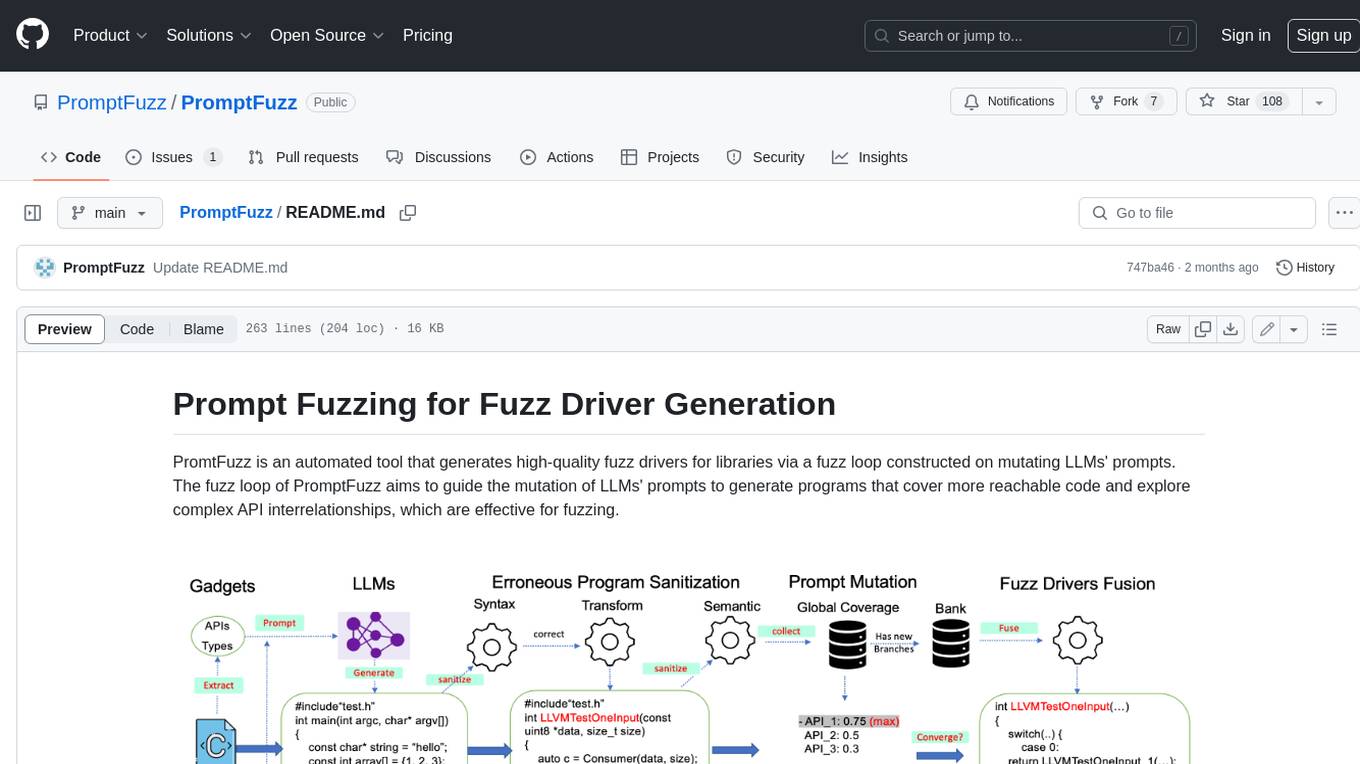
PromptFuzz
**Description:** PromptFuzz is an automated tool that generates high-quality fuzz drivers for libraries via a fuzz loop constructed on mutating LLMs' prompts. The fuzz loop of PromptFuzz aims to guide the mutation of LLMs' prompts to generate programs that cover more reachable code and explore complex API interrelationships, which are effective for fuzzing. **Features:** * **Multiply LLM support** : Supports the general LLMs: Codex, Inocder, ChatGPT, and GPT4 (Currently tested on ChatGPT). * **Context-based Prompt** : Construct LLM prompts with the automatically extracted library context. * **Powerful Sanitization** : The program's syntax, semantics, behavior, and coverage are thoroughly analyzed to sanitize the problematic programs. * **Prioritized Mutation** : Prioritizes mutating the library API combinations within LLM's prompts to explore complex interrelationships, guided by code coverage. * **Fuzz Driver Exploitation** : Infers API constraints using statistics and extends fixed API arguments to receive random bytes from fuzzers. * **Fuzz engine integration** : Integrates with grey-box fuzz engine: LibFuzzer. **Benefits:** * **High branch coverage:** The fuzz drivers generated by PromptFuzz achieved a branch coverage of 40.12% on the tested libraries, which is 1.61x greater than _OSS-Fuzz_ and 1.67x greater than _Hopper_. * **Bug detection:** PromptFuzz detected 33 valid security bugs from 49 unique crashes. * **Wide range of bugs:** The fuzz drivers generated by PromptFuzz can detect a wide range of bugs, most of which are security bugs. * **Unique bugs:** PromptFuzz detects uniquely interesting bugs that other fuzzers may miss. **Usage:** 1. Build the library using the provided build scripts. 2. Export the LLM API KEY if using ChatGPT or GPT4. 3. Generate fuzz drivers using the `fuzzer` command. 4. Run the fuzz drivers using the `harness` command. 5. Deduplicate and analyze the reported crashes. **Future Works:** * **Custom LLMs suport:** Support custom LLMs. * **Close-source libraries:** Apply PromptFuzz to close-source libraries by fine tuning LLMs on private code corpus. * **Performance** : Reduce the huge time cost required in erroneous program elimination.
20 - OpenAI Gpts
Log Analyzer
I'm designed to help You analyze any logs like Linux system logs, Windows logs, any security logs, access logs, error logs, etc. Please do not share information that You would like to keep private. The author does not collect or process any personal data.
Mónica
CSIRT que lidera un equipo especializado en detectar y responder a incidentes de seguridad, maneja la contención y recuperación, organiza entrenamientos y simulacros, elabora reportes para optimizar estrategias de seguridad y coordina con entidades legales cuando es necesario

CISO GPT
Specialized LLM in computer security, acting as a CISO with 20 years of experience, providing precise, data-driven technical responses to enhance organizational security.

Phish or No Phish Trainer
Hone your phishing detection skills! Analyze emails, texts, and calls to spot deception. Become a security pro!
Phoenix Vulnerability Intelligence GPT
Expert in analyzing vulnerabilities with ransomware focus with intelligence powered by Phoenix Security
Defender for Endpoint Guardian
To assist individuals seeking to learn about or work with Microsoft's Defender for Endpoint. I provide detailed explanations, step-by-step guides, troubleshooting advice, cybersecurity best practices, and demonstrations, all specifically tailored to Microsoft Defender for Endpoint.
Prompt Injection Detector
GPT used to classify prompts as valid inputs or injection attempts. Json output.