Best AI tools for< Vulnerability Manager >
Infographic
20 - AI tool Sites
Cyble
Cyble is a leading threat intelligence platform offering products and services recognized by top industry analysts. It provides AI-driven cyber threat intelligence solutions for enterprises, governments, and individuals. Cyble's offerings include attack surface management, brand intelligence, dark web monitoring, vulnerability management, takedown and disruption services, third-party risk management, incident management, and more. The platform leverages cutting-edge AI technology to enhance cybersecurity efforts and stay ahead of cyber adversaries.
CloudDefense.AI
CloudDefense.AI is an industry-leading multi-layered Cloud Native Application Protection Platform (CNAPP) that safeguards cloud infrastructure and cloud-native apps with expertise, precision, and confidence. It offers comprehensive cloud security solutions, vulnerability management, compliance, and application security testing. The platform utilizes advanced AI technology to proactively detect and analyze real-time threats, ensuring robust protection for businesses against cyber threats.
BigBear.ai
BigBear.ai is an AI-powered decision intelligence solutions provider that offers services across various industries including Government & Defense, Manufacturing & Warehouse Operations, Healthcare & Life Sciences. They specialize in optimizing operational efficiency, force deployment, supply chain management, autonomous systems management, and vulnerability detection. Their solutions are designed to improve situational awareness, streamline production processes, and enhance patient care delivery settings.
Sprinto
Sprinto is a Continuous Security & Compliance Platform that helps organizations manage and maintain compliance with various frameworks such as SOC 2, ISO 27001, NIST, GDPR, HIPAA, and more. It offers features like Vendor Risk Management, Vulnerability Assessment, Access Control Policies, Security Questionnaire, and Change Management. Sprinto automates evidence collection, streamlines workflows, and provides expert support to ensure organizations stay audit-ready and compliant. The platform is AI-powered, scalable, and supports over 40 compliance frameworks, making it a comprehensive solution for security and compliance needs.
DepsHub
DepsHub is an AI-powered tool designed to simplify dependency updates for software development teams. It offers features such as automatic dependency updates, license checks, and security vulnerability scanning. With a noise-free dependency management system, DepsHub ensures secure and efficient management for teams of any size. The tool provides a cross-repository overview, license compliance checks, security alerts, and AI-powered updates based on library changelogs and release notes. DepsHub supports a wide range of languages and frameworks, allowing users to focus on writing code that matters while keeping their dependencies secure and up to date.
CyberUpgrade
CyberUpgrade.net is an AI-powered platform that offers comprehensive cybersecurity and compliance solutions for organizations of all sizes. It provides automated compliance, risk management, vendor risk assessment, policy management, audit management, and 24/7 security support. The platform features a cloud vulnerability scanner, security awareness training, pentesting, business continuity planning, disaster recovery planning, and an AI-powered assistant for seamless security support. CyberUpgrade helps CTOs understand their organization's security status, proposes improvement plans, guides execution, and prepares compliance documentation with a push of a button. It engages every employee individually for evidence collection and situation analysis, ensuring real cybersecurity measures are in place.
Vulnscanner AI
Vulnscanner AI is an AI-powered WordPress security tool that offers affordable and user-friendly website security solutions. It provides instant, jargon-free security reports, step-by-step resolution guides, and customizable security solutions to prevent future attacks. The tool is designed to help small/medium businesses, web professionals, and individuals safeguard their online presence without breaking the bank. With advanced algorithms and military-grade encryption, Vulnscanner AI aims to protect websites from cyber threats and vulnerabilities.
Legit
Legit is an Application Security Posture Management (ASPM) platform that helps organizations manage and mitigate application security risks from code to cloud. It offers features such as Secrets Detection & Prevention, Continuous Compliance, Software Supply Chain Security, and AI Security Posture Management. Legit provides a unified view of AppSec risk, deep context to prioritize issues, and proactive remediation to prevent future risks. It automates security processes, collaborates with DevOps teams, and ensures continuous compliance. Legit is trusted by Fortune 500 companies like Kraft-Heinz for securing the modern software factory.
Endor Labs
Endor Labs is an AI-powered software supply chain security solution that helps organizations manage their software bills of materials (SBOM), secure their open source dependencies, optimize CI/CD pipeline security, and enhance application security with secret detection. The platform offers advanced features such as AI-assisted OSS selection, compliance management, reachability-based SCA, and repository security posture management. Endor Labs aims to streamline security processes, reduce false positives, and provide actionable insights to improve software supply chain security.
Tokenomist.ai
Tokenomist.ai is an AI-powered security service website that helps protect against online attacks by enabling cookies and blocking malicious activities. It uses advanced algorithms to detect and prevent security threats, ensuring a safe browsing experience for users. The platform is designed to safeguard websites from potential risks and vulnerabilities, offering a reliable security solution for online businesses and individuals.
Snyk
Snyk is a developer security platform powered by DeepCode AI, offering solutions for application security, software supply chain security, and secure AI-generated code. It provides comprehensive vulnerability data, license compliance management, and self-service security education. Snyk integrates AI models trained on security-specific data to secure applications and manage tech debt effectively. The platform ensures developer-first security with one-click security fixes and AI-powered recommendations, enhancing productivity while maintaining security standards.
Pixeebot
Pixeebot is an automated product security engineer that helps developers fix vulnerabilities, harden code, squash bugs, and improve code quality. It integrates with your existing workflow and can be used locally via CLI or through the GitHub app. Pixeebot is powered by the open source Codemodder framework, which allows you to build your own custom codemods.
VIDOC
VIDOC is an AI-powered security engineer that automates code review and penetration testing. It continuously scans and reviews code to detect and fix security issues, helping developers deliver secure software faster. VIDOC is easy to use, requiring only two lines of code to be added to a GitHub Actions workflow. It then takes care of the rest, providing developers with a tailored code solution to fix any issues found.
CensysGPT Beta
CensysGPT Beta is a tool that simplifies building queries and empowers users to conduct efficient and effective reconnaissance operations. It enables users to quickly and easily gain insights into hosts on the internet, streamlining the process and allowing for more proactive threat hunting and exposure management.
Protect AI
Protect AI is a comprehensive platform designed to secure AI systems by providing visibility and manageability to detect and mitigate unique AI security threats. The platform empowers organizations to embrace a security-first approach to AI, offering solutions for AI Security Posture Management, ML model security enforcement, AI/ML supply chain vulnerability database, LLM security monitoring, and observability. Protect AI aims to safeguard AI applications and ML systems from potential vulnerabilities, enabling users to build, adopt, and deploy AI models confidently and at scale.
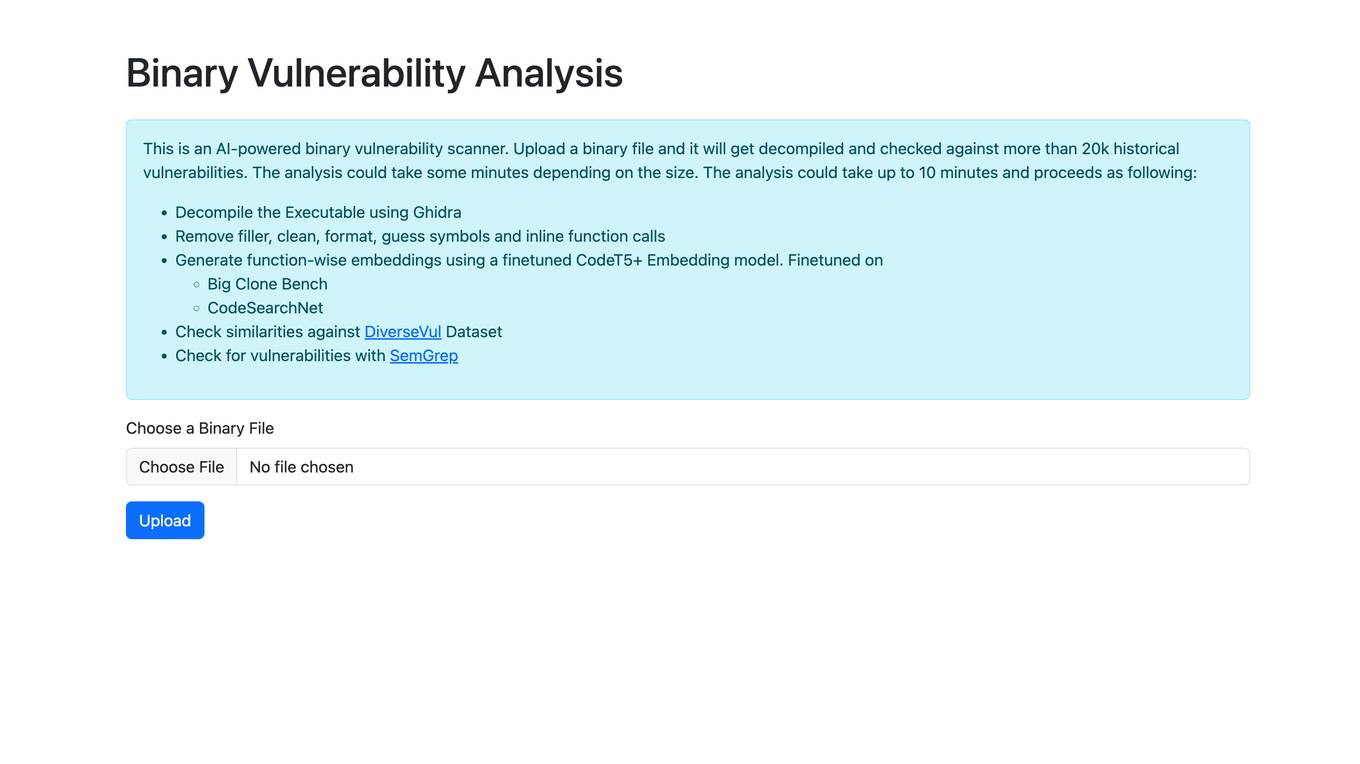
Binary Vulnerability Analysis
The website offers an AI-powered binary vulnerability scanner that allows users to upload a binary file for analysis. The tool decompiles the executable, removes filler, cleans, formats, and checks for historical vulnerabilities. It generates function-wise embeddings using a finetuned CodeT5+ Embedding model and checks for similarities against the DiverseVul Dataset. The tool also utilizes SemGrep to check for vulnerabilities in the binary file.
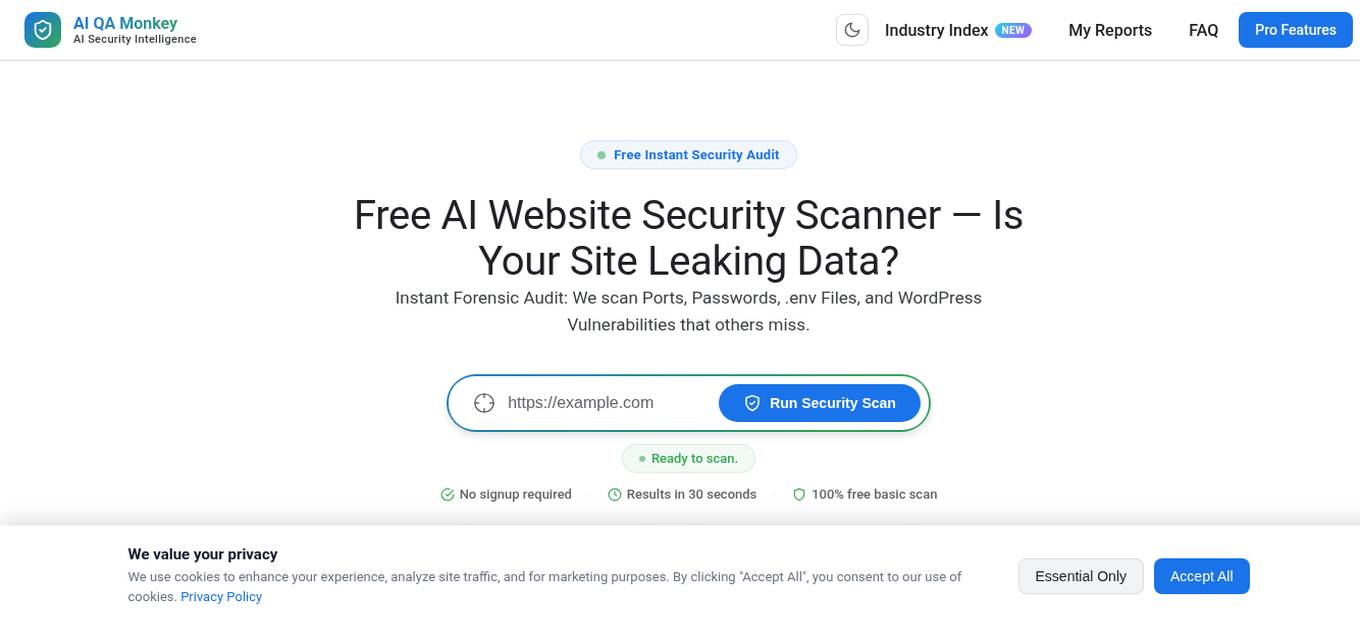
AI QA Monkey
AI QA Monkey is a free website security scanner that offers instant security audits to check website security scores. The tool scans for vulnerabilities such as leaked sensitive data, open ports, passwords, .env files, and WordPress vulnerabilities. It provides a detailed security report with actionable insights and AI-powered fixes. Users can export reports in PDF, JSON, or CSV formats. AI QA Monkey is designed to help businesses improve their security posture and comply with GDPR regulations.
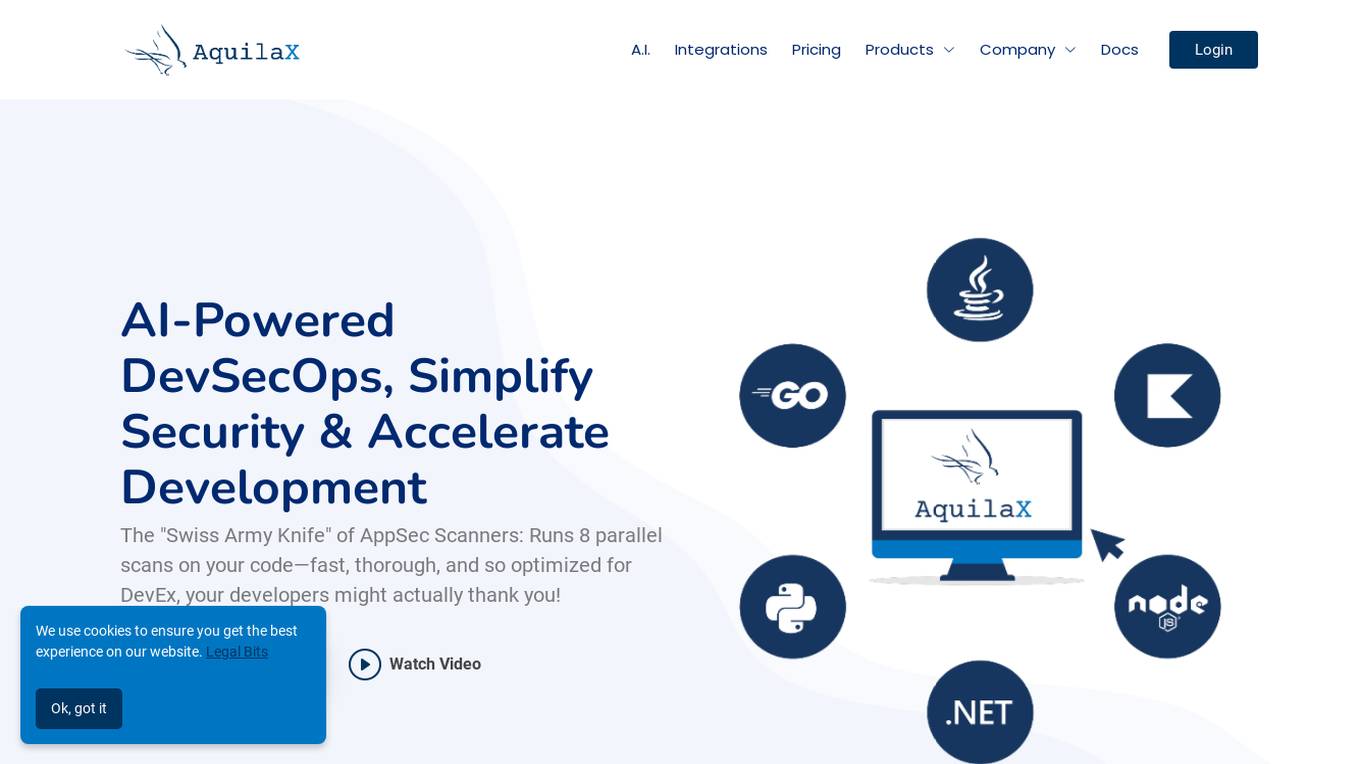
AquilaX
AquilaX is an AI-powered DevSecOps platform that simplifies security and accelerates development processes. It offers a comprehensive suite of security scanning tools, including secret identification, PII scanning, SAST, container scanning, and more. AquilaX is designed to integrate seamlessly into the development workflow, providing fast and accurate results by leveraging AI models trained on extensive datasets. The platform prioritizes developer experience by eliminating noise and false positives, making it a go-to choice for modern Secure-SDLC teams worldwide.
OpenBuckets
OpenBuckets is a web application designed to help users find and secure open buckets in cloud storage systems. It provides a user-friendly interface for scanning and identifying unprotected buckets, allowing users to take necessary actions to secure their data. With OpenBuckets, users can easily detect potential security risks and prevent unauthorized access to their sensitive information stored in the cloud.
Huntr
Huntr is the world's first bug bounty platform for AI/ML. It provides a single place for security researchers to submit vulnerabilities, ensuring the security and stability of AI/ML applications, including those powered by Open Source Software (OSS).
0 - Open Source Tools
20 - OpenAI Gpts
Phoenix Vulnerability Intelligence GPT
Expert in analyzing vulnerabilities with ransomware focus with intelligence powered by Phoenix Security

VulnGPT
Your ally in navigating the CVE deluge. Expert insights for prioritizing and remediating vulnerabilities.
WVA
Web Vulnerability Academy (WVA) is an interactive tutor designed to introduce users to web vulnerabilities while also providing them with opportunities to assess and enhance their knowledge through testing.
NVD - CVE Research Assistant
Expert in CVEs and cybersecurity vulnerabilities, providing precise information from the National Vulnerability Database.
Security Testing Advisor
Ensures software security through comprehensive testing techniques.
Solidity Sage
Your personal Ethereum magician — Simply ask a question or provide a code sample for insights into vulnerabilities, gas optimizations, and best practices. Don't be shy to ask about tooling and legendary attacks.
🛡️ CodeGuardian Pro+ 🛡️
Your AI-powered sentinel for code! Scans for vulnerabilities, offers security tips, and educates on best practices in cybersecurity. 🔍🔐