Best AI tools for< Incident Analyst >
Infographic
20 - AI tool Sites
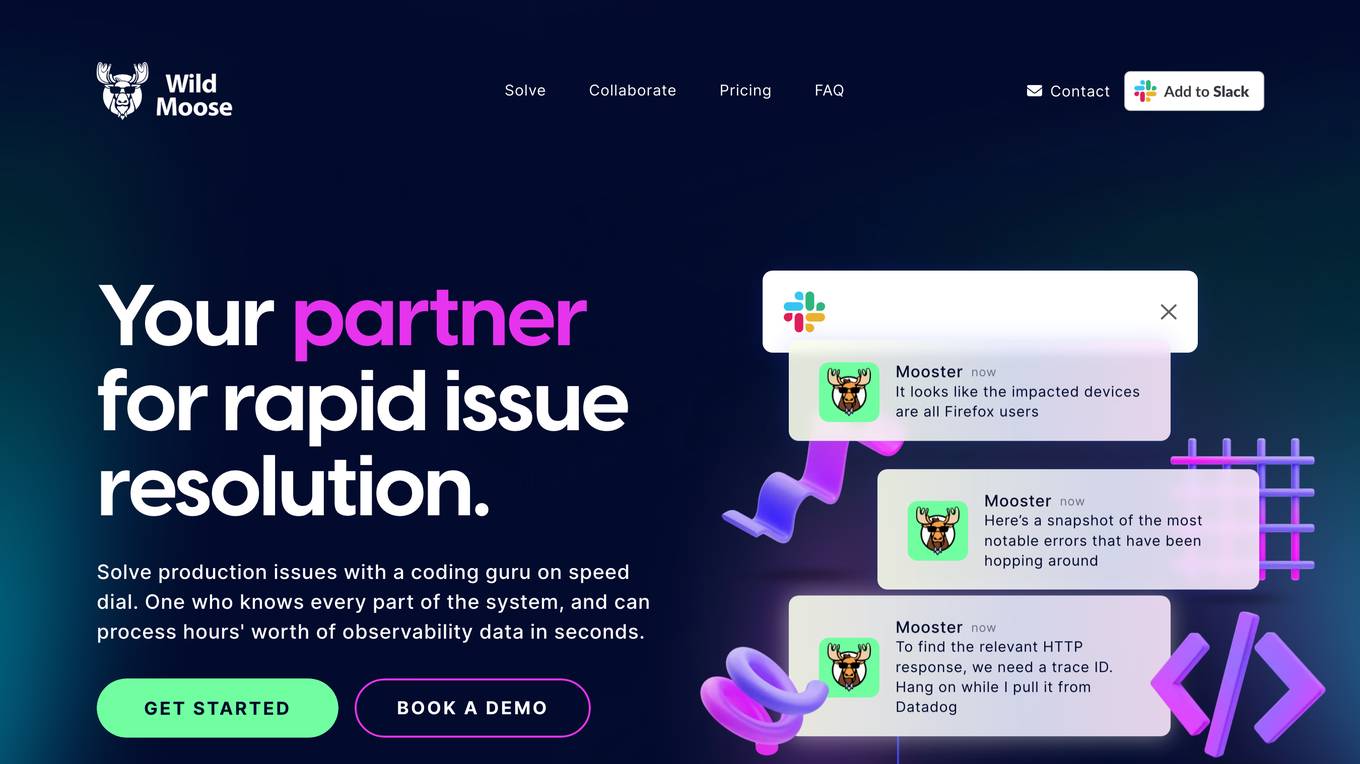
Wild Moose
Wild Moose is an AI-powered SRE Copilot tool designed to help companies handle incidents efficiently. It offers fast and efficient root cause analysis that improves with every incident by automatically gathering and analyzing logs, metrics, and code to pinpoint root causes. The tool converts tribal knowledge into custom playbooks, constantly improves performance with a system model that learns from each incident, and integrates seamlessly with various observability tools and deployment platforms. Wild Moose reduces cognitive load on teams, automates routine tasks, and provides actionable insights in real-time, enabling teams to act fast during outages.

Dropzone AI
Dropzone AI is an award-winning AI application designed to reinforce Security Operations Centers (SOCs) by providing autonomous AI analysts. It replicates the techniques of elite analysts to autonomously investigate alerts, covering various use cases such as phishing, endpoint, network, cloud, identity, and insider threats. The application offers pre-trained AI agents that work alongside human analysts, automating investigation tasks and providing fast, detailed, and accurate reports. With built-in integrations with major security tools, Dropzone AI aims to reduce Mean Time to Respond (MTTR) and allow analysts to focus on addressing real threats.
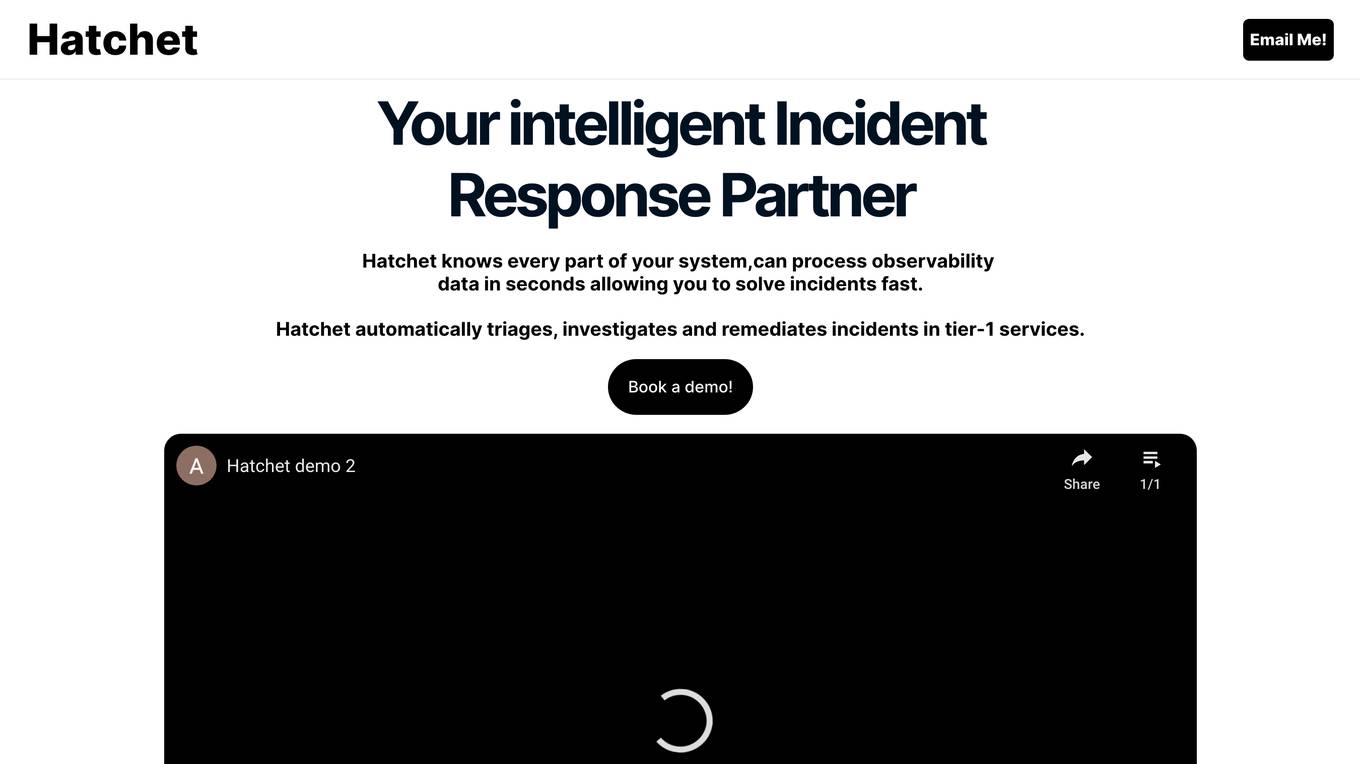
Hatchet
Hatchet is an AI companion designed to assist on-call engineers in incident response by providing intelligent insights and suggestions based on logs, communications channels, and code analysis. It helps save time and money by automating the triaging and investigation process during critical incidents. The tool is built by engineers with a focus on data security, offering self-hosted deployments, permissions, audit trails, SSO, and version control. Hatchet aims to streamline incident resolution for tier-1 services, enabling faster response and potential problem resolution.
OpenBuckets
OpenBuckets is a web application designed to help users find and secure open buckets in cloud storage systems. It provides a simple and efficient way to identify and protect sensitive data that may be exposed due to misconfigured cloud storage settings. With OpenBuckets, users can easily scan their cloud storage accounts for publicly accessible buckets and take necessary actions to safeguard their information.
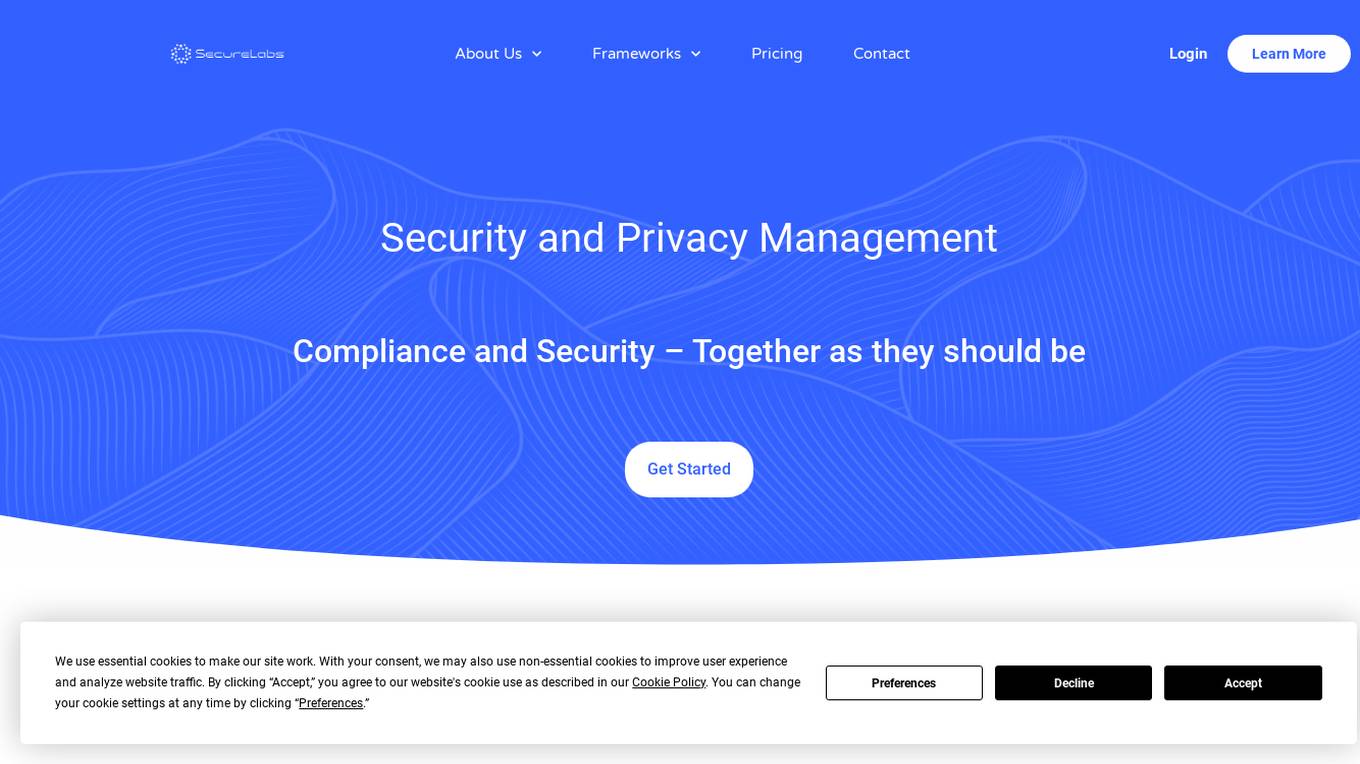
SecureLabs
SecureLabs is an AI-powered platform that offers comprehensive security, privacy, and compliance management solutions for businesses. The platform integrates cutting-edge AI technology to provide continuous monitoring, incident response, risk mitigation, and compliance services. SecureLabs helps organizations stay current and compliant with major regulations such as HIPAA, GDPR, CCPA, and more. By leveraging AI agents, SecureLabs offers autonomous aids that tirelessly safeguard accounts, data, and compliance down to the account level. The platform aims to help businesses combat threats in an era of talent shortages while keeping costs down.
AirMDR
AirMDR is an AI-powered Managed Detection and Response (MDR) application that revolutionizes cybersecurity by leveraging artificial intelligence to automate routine tasks, enhance alert triage, investigation, and response processes. The application offers faster, higher-quality, and more affordable cybersecurity solutions, supervised by human experts. AirMDR aims to deliver unprecedented speed, superior quality, and cost-effective outcomes to cater to the unique demands of security operations centers.
Bricklayer AI
Bricklayer AI is an automated AI security team that empowers Security Operations Centers (SOCs) to manage alerts, incidents, and threats efficiently. It offers autonomous AI agents designed to work collaboratively with human experts, enabling faster and more effective security operations. Bricklayer AI helps organizations stay ahead of cyber threats by automating labor-intensive tasks and providing real-time analysis and response.
Tracecat
Tracecat is an open-source security automation platform that helps you automate security alerts, build AI-assisted workflows, orchestrate alerts, and close cases fast. It is a Tines / Splunk SOAR alternative that is built for builders and allows you to experiment for free. You can deploy Tracecat on your own infrastructure or use Tracecat Cloud with no maintenance overhead. Tracecat is Apache-2.0 licensed, which means it is open vision, open community, and open development. You can have your say in the future of security automation. Tracecat is no-code first, but you can also code as well. You can build automations fast with no-code and customize without vendor lock-in using Python. Tracecat has a click-and-drag workflow builder that allows you to automate SecOps using pre-built actions (API calls, webhooks, data transforms, AI tasks, and more) combined into workflows. No code is required. Tracecat also has a built-in case management system that allows you to open cases directly from workflows and track and manage security incidents all in one platform.
Palo Alto Networks
Palo Alto Networks is a cybersecurity company offering advanced security solutions powered by Precision AI to protect modern enterprises from cyber threats. The company provides network security, cloud security, and AI-driven security operations to defend against AI-generated threats in real time. Palo Alto Networks aims to simplify security and achieve better security outcomes through platformization, intelligence-driven expertise, and proactive monitoring of sophisticated threats.
Cyble
Cyble is a leading threat intelligence platform offering products and services recognized by top industry analysts. It provides AI-driven cyber threat intelligence solutions for enterprises, governments, and individuals. Cyble's offerings include attack surface management, brand intelligence, dark web monitoring, vulnerability management, takedown and disruption services, third-party risk management, incident management, and more. The platform leverages cutting-edge AI technology to enhance cybersecurity efforts and stay ahead of cyber adversaries.
Stellar Cyber
Stellar Cyber is an AI-driven unified security operations platform powered by Open XDR. It offers a single platform with NG-SIEM, NDR, and Open XDR, providing security capabilities to take control of security operations. The platform helps organizations detect, correlate, and respond to threats fast using AI technology. Stellar Cyber is designed to protect the entire attack surface, improve security operations performance, and reduce costs while simplifying security operations.
Resolvd
Resolvd is an AI-powered incident resolution platform that creates a knowledge base of logs, data sources, and applications to autonomously diagnose and resolve incidents. It helps cut time to response by 50%, return hours to developers, simplify data querying, and provide automated anomaly detection. Resolvd uses AI/ML models to analyze logs, aggregate critical context, and deliver insights in workflow, seamlessly integrating with existing systems like Slack, Jira, and PagerDuty.
Darktrace
Darktrace is an essential AI cybersecurity platform that offers proactive protection, cloud-native AI security, comprehensive risk management, and user protection across various devices. It accelerates triage by 10x, defends with confidence, and connects with various integrations. Darktrace ActiveAI Security Platform spots novel threats across organizations, providing solutions for ransomware, APTs, phishing, data loss, and more. With a focus on defense, Darktrace aims to transform cybersecurity by detecting and responding to known and novel threats in real-time.
CrowdStrike
CrowdStrike is a leading cybersecurity platform that uses artificial intelligence (AI) to protect businesses from cyber threats. The platform provides a unified approach to security, combining endpoint security, identity protection, cloud security, and threat intelligence into a single solution. CrowdStrike's AI-powered technology enables it to detect and respond to threats in real-time, providing businesses with the protection they need to stay secure in the face of evolving threats.
CrowdStrike
CrowdStrike is a cloud-based cybersecurity platform that provides endpoint protection, threat intelligence, and incident response services. It uses artificial intelligence (AI) to detect and prevent cyberattacks. CrowdStrike's platform is designed to be scalable and easy to use, and it can be deployed on-premises or in the cloud. CrowdStrike has a global customer base of over 23,000 organizations, including many Fortune 500 companies.
Exabeam
Exabeam is a cybersecurity and compliance platform that offers Security Information and Event Management (SIEM) solutions. The platform provides flexible choices for threat detection, investigation, and response, whether through cloud-based AI-driven solutions or on-premises SIEM deployments. Exabeam's AI-driven Security Operations Platform combines advanced threat detection capabilities with automation to deliver faster and more accurate TDIR. With features like UEBA, SOAR, and insider threat detection, Exabeam helps organizations improve security posture and optimize investments. The platform supports various industries and use cases, offering pre-built content, behavioral analytics, and context enrichment for enhanced threat coverage and compliance.
Darktrace
Darktrace is a cybersecurity platform that leverages AI technology to provide proactive protection against cyber threats. It offers cloud-native AI security solutions for networks, emails, cloud environments, identity protection, and endpoint security. Darktrace's AI Analyst investigates alerts at the speed and scale of AI, mimicking human analyst behavior. The platform also includes services such as 24/7 expert support and incident management. Darktrace's AI is built on a unique approach where it learns from the organization's data to detect and respond to threats effectively. The platform caters to organizations of all sizes and industries, offering real-time detection and autonomous response to known and novel threats.
Torq
Torq is an AI-driven platform that offers Security Hyperautomation Solutions, empowering security teams to detect, prioritize, and respond to threats faster. It provides a range of features and capabilities such as AI Agents, AI SOC Analyst, Case Management, and Integrations. Torq is trusted by top security teams worldwide and is recognized for its ability to mitigate alert fatigue, false positives, and staff burnout. The platform is designed to usher in the era of Autonomous SOC by harnessing AI to enhance security operations.
MixMode
MixMode is the world's most advanced AI for threat detection, offering a dynamic threat detection platform that utilizes patented Third Wave AI technology. It provides real-time detection of known and novel attacks with high precision, self-supervised learning capabilities, and context-awareness to defend against modern threats. MixMode empowers modern enterprises with unprecedented speed and scale in threat detection, delivering unrivaled capabilities without the need for predefined rules or human input. The platform is trusted by top security teams and offers rapid deployment, customization to individual network dynamics, and state-of-the-art AI-driven threat detection.
ODIN
ODIN is a powerful internet scanning search engine designed for scanning and cataloging internet assets. It offers enhanced scanning capabilities, faster refresh rates, and comprehensive visibility into open ports. With over 45 modules covering various aspects like HTTP, Elasticsearch, and Redis, ODIN enriches data and provides accurate and up-to-date information. The application uses AI/ML algorithms to detect exposed buckets, files, and potential vulnerabilities. Users can perform granular searches, access exploit information, and integrate effortlessly with ODIN's API, SDKs, and CLI. ODIN allows users to search for hosts, exposed buckets, exposed files, and subdomains, providing detailed insights and supporting diverse threat intelligence applications.
1 - Open Source Tools
awesome-LLM-AIOps
The 'awesome-LLM-AIOps' repository is a curated list of academic research and industrial materials related to Large Language Models (LLM) and Artificial Intelligence for IT Operations (AIOps). It covers various topics such as incident management, log analysis, root cause analysis, incident mitigation, and incident postmortem analysis. The repository provides a comprehensive collection of papers, projects, and tools related to the application of LLM and AI in IT operations, offering valuable insights and resources for researchers and practitioners in the field.
20 - OpenAI Gpts
Cyber security analyst
Designed to help cybersecurity analysts # ISO # NIST # COBIT # SANS # PCI DSS
API Content Warehouse Leak Help
Comprehensive analysis of Google API Content Warehouse Leak
Incident Response Forensic Techniques
help organizations in investigating computer security incidents and troubleshooting some information technology (IT) operational problems by providing practical guidance on performing computer and network forensics.

TheDFIRReport Assistant
Detailed insights from TheDFIRReport's 2021-2023 reports, including Detections and Indicators.
Mónica
CSIRT que lidera un equipo especializado en detectar y responder a incidentes de seguridad, maneja la contención y recuperación, organiza entrenamientos y simulacros, elabora reportes para optimizar estrategias de seguridad y coordina con entidades legales cuando es necesario
MITREGPT
Feed me any input and i'll match it with the relevant MITRE ATT&CK techniques and tactics (@mthcht)
Message Header Analyzer
Analyzes email headers for security insights, presenting data in a structured table view.
Malware Rule Master
Expert in malware analysis and Yara rules, using web sources for specifics.
Bug Insider
Analyzes bug bounty writeups and cybersecurity reports, providing structured insights and tips.
MagicUnprotect
This GPT allows to interact with the Unprotect DB to retrieve knowledge about malware evasion techniques