Best AI tools for< Security Analysis >
20 - AI tool Sites
DryRun Security
DryRun Security is an AI-native SAST (Static Application Security Testing) tool that provides next-gen AI-native SAST with unmatched accuracy, lowest noise, zero rules, fast PR feedback, and on-demand full-repo DeepScans. It offers code security intelligence trusted by leading engineering and security teams. The tool uses Contextual Security Analysis to reason about exploitability and impact, inspects data flow across files and services, and catches logic flaws and broken auth that pattern-matching scanners may miss. DryRun Security is optimized for various languages and frameworks and integrates with AI coding tools, SCMs, and communication platforms.
Amped Software
Amped Software develops solutions for the analysis and enhancement of images and videos for forensic, security, and investigative applications. Their tools are used by top forensic labs, law enforcement, military, security, and government agencies worldwide.
ChatWithCloud
ChatWithCloud is a command-line interface (CLI) tool that enables users to interact with AWS Cloud using natural language within the Terminal, powered by generative AI. It allows users to perform various tasks such as cost analysis, security analysis, troubleshooting, and fixing infrastructure issues without the need for an OpenAI API Key. The tool offers both a lifetime license option and a managed subscription model for users' convenience.
STRATxAI
STRATxAI is an AI-powered quantitative investment platform that offers custom AI model portfolios tailored to clients' investment philosophy, risk tolerance, and objectives. The platform harnesses machine learning to deliver data-driven insights for security analysis, portfolio construction, and management. Powered by the proprietary investment engine Alana, STRATxAI processes over 8 billion financial data points daily to uncover hidden alpha beyond traditional methods. Clients benefit from smarter decision-making, better risk-adjusted returns, optimized portfolio management, and savings on resources. The platform is designed to enhance investment decisions for forward-thinking investors by leveraging AI technology.
Semgrep
Semgrep is an AI-powered application designed for static analysis and security testing of code. It helps developers find and fix issues in their code, detect vulnerabilities in the software supply chain, and identify hardcoded secrets. Semgrep offers features such as AI-powered noise filtering, dataflow analysis, and tailored remediation guidance. It is known for its speed, transparency, and extensibility, making it a valuable tool for AppSec teams of all sizes.
Vercel Security Checkpoint
Vercel Security Checkpoint is a web service that provides a security verification process for website owners. It ensures that the browser accessing the website is legitimate and secure. By enabling JavaScript, users can continue with the security checkpoint to safeguard their website from potential threats and unauthorized access.
EdgeDX
EdgeDX is a leading provider of Edge AI Video Analysis Solutions, specializing in security and surveillance, construction and logistics safety, efficient store management, public safety management, and intelligent transportation system. The application offers over 50 intuitive AI apps capable of advanced human behavior analysis, supports various protocols and VMS, and provides features like P2P based mobile alarm viewer, LTE & GPS support, and internal recording with M.2 NVME SSD. EdgeDX aims to protect customer assets, ensure safety, and enable seamless integration with AI Bridge for easy and efficient implementation.
Stellar Cyber
Stellar Cyber is an AI-driven unified security operations platform powered by Open XDR. It offers a single platform with NG-SIEM, NDR, and Open XDR, providing security capabilities to take control of security operations. The platform helps organizations detect, correlate, and respond to threats fast using AI technology. Stellar Cyber is designed to protect the entire attack surface, improve security operations performance, and reduce costs while simplifying security operations.
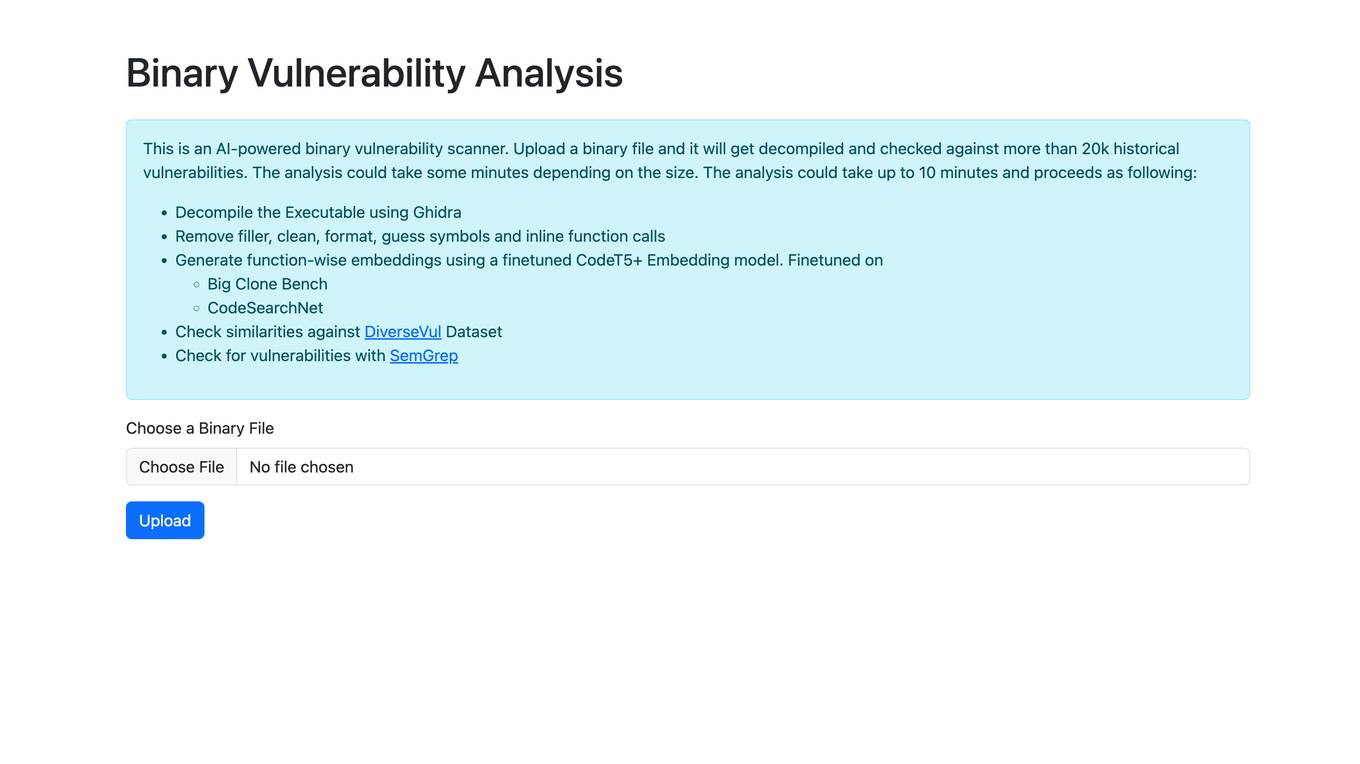
Binary Vulnerability Analysis
The website offers an AI-powered binary vulnerability scanner that allows users to upload a binary file for analysis. The tool decompiles the executable, removes filler, cleans, formats, and checks for historical vulnerabilities. It generates function-wise embeddings using a finetuned CodeT5+ Embedding model and checks for similarities against the DiverseVul Dataset. The tool also utilizes SemGrep to check for vulnerabilities in the binary file.
AquilaX
AquilaX is an AI-powered DevSecOps platform that simplifies security and accelerates development processes. It offers a comprehensive suite of security scanning tools, including secret identification, PII scanning, SAST, container scanning, and more. AquilaX is designed to integrate seamlessly into the development workflow, providing fast and accurate results by leveraging AI models trained on extensive datasets. The platform prioritizes developer experience by eliminating noise and false positives, making it a go-to choice for modern Secure-SDLC teams worldwide.
Codiga
Codiga is a static code analysis tool that helps developers write clean, safe, and secure code. It works in real-time in your IDE and CI/CD pipelines, and it can be customized to meet your specific needs. Codiga supports a wide range of languages and frameworks, and it integrates with popular tools like GitHub, GitLab, and Bitbucket.
ClicKarma
ClicKarma is an AI-driven defense tool designed to protect Google Ads from click frauds. It maximizes ROI by ensuring authentic interactions and eliminating wasted spend from bots and dishonest competitors. The tool offers advanced AI features to analyze and block disruptive click fraud in real-time, safeguarding ad campaigns and enhancing traffic quality. ClicKarma is trusted by over 10,000 advertisers, agencies, and businesses, providing a user-friendly interface for easy setup and operation.
Image Bear AI
Image Bear AI is an advanced image recognition tool that utilizes artificial intelligence to analyze and identify objects within images. The application is designed to assist users in various industries such as e-commerce, security, and healthcare by providing accurate and efficient image analysis capabilities. With its cutting-edge technology, Image Bear AI offers a user-friendly interface and fast processing speeds, making it a valuable tool for businesses looking to streamline their image recognition processes.
GeoInfer
GeoInfer is a professional AI-powered geolocation platform that analyzes photographs to determine where they were taken. It uses visual-only inference technology to examine visual elements like architecture, terrain, vegetation, and environmental markers to identify geographic locations without requiring GPS metadata or EXIF data. The platform offers transparent accuracy levels for different use cases, including a Global Model with 1km-100km accuracy ideal for regional and city-level identification. Additionally, GeoInfer provides custom regional models for organizations requiring higher precision, such as meter-level accuracy for specific geographic areas. The platform is designed for professionals in various industries, including law enforcement, insurance fraud investigation, digital forensics, and security research.
Center for a New American Security
The Center for a New American Security (CNAS) is a bipartisan, non-profit think tank that focuses on national security and defense policy. CNAS conducts research, analysis, and policy development on a wide range of topics, including defense strategy, nuclear weapons, cybersecurity, and energy security. CNAS also provides expert commentary and analysis on current events and policy debates.
InsightFace
InsightFace is an open-source deep face analysis library that provides a rich variety of state-of-the-art algorithms for face recognition, detection, and alignment. It is designed to be efficient for both training and deployment, making it suitable for research institutions and industrial organizations. InsightFace has achieved top rankings in various challenges and competitions, including the ECCV 2022 WCPA Challenge, NIST-FRVT 1:1 VISA, and WIDER Face Detection Challenge 2019.
ContractReader
ContractReader is an audit tool designed to simplify the process of reading and understanding smart contracts. It offers features such as syntax highlighting, testnet support, live onchain values, code comparison in-browser, GPT-4 security reviews, and more. Users can enter a contract address or Etherscan URL to access these functionalities. The tool supports various networks like Mainnet, Goerli, Sepolia, Optimism, Polygon, Arbitrum, and BNB Smart Chain. ContractReader aims to make crypto contracts more accessible and comprehensible for users, providing a user-friendly interface for contract analysis.
AI Insights Hub
The website is a platform dedicated to discussing and analyzing various developments and advancements in the field of AI, particularly focusing on Large Language Models (LLMs) such as GPT-5. It provides detailed insights, release notes, and discussions on AI models, applications, and security concerns. The website covers a wide range of topics related to AI, including prompt injections, spatial joins, memory features, and project-specific memory usage.
Hex
Hex is a collaborative data workspace that provides a variety of tools for working with data, including queries, notebooks, reports, data apps, and AI. It is designed to be easy to use for people of all technical skill levels, and it integrates with a variety of other tools and services. Hex is a powerful tool for data exploration, analysis, and visualization.
Metabob
Metabob is an AI-powered code review tool that helps developers detect, explain, and fix coding problems. It utilizes proprietary graph neural networks to detect problems and LLMs to explain and resolve them, combining the best of both worlds. Metabob's AI is trained on millions of bug fixes performed by experienced developers, enabling it to detect complex problems that span across codebases and automatically generate fixes for them. It integrates with popular code hosting platforms such as GitHub, Bitbucket, Gitlab, and VS Code, and supports various programming languages including Python, Javascript, Typescript, Java, C++, and C.
0 - Open Source AI Tools
20 - OpenAI Gpts
Securia
AI-powered audit ally. Enhance cybersecurity effortlessly with intelligent, automated security analysis. Safe, swift, and smart.
API Content Warehouse Leak Help
Comprehensive analysis of Google API Content Warehouse Leak
Log Analyzer
I'm designed to help You analyze any logs like Linux system logs, Windows logs, any security logs, access logs, error logs, etc. Please do not share information that You would like to keep private. The author does not collect or process any personal data.
Malware Rule Master
Expert in malware analysis and Yara rules, using web sources for specifics.
Fluffy Risk Analyst
A cute sheep expert in risk analysis, providing downloadable checklists.
Threat Intelligence Expert
Patient threat intelligence expert skilled in binary file analysis and YARA rules.