Best AI tools for< Monitor Security Systems >
20 - AI tool Sites
Ambient.ai
Ambient.ai is an AI-powered physical security software that helps prevent security incidents by detecting threats in real-time, auto-clearing false alarms, and accelerating investigations. The platform uses computer vision intelligence to monitor cameras for suspicious activities, decrease alarms, and enable rapid investigations. Ambient.ai offers rich integration ecosystem, detections for a spectrum of threats, unparalleled operational efficiency, and enterprise-grade privacy to ensure maximum security and efficiency for its users.
AI Bot Eye
AI Bot Eye is an AI-based security system that seamlessly integrates with existing CCTV systems to deliver intelligent insights. From AI-powered Fire Detection to Real-Time Intrusion Alerts, AI Bot Eye elevates security systems with cutting-edge AI technology. The application offers features such as Intrusion Detection, Face Recognition, Fire and Smoke Detection, Speed Cam Mode, Safety Kit Detection, HeatMaps Insights, Foot Traffic Analysis, and Numberplate recognition. AI Bot Eye provides advantages like real-time alerts, enhanced security, efficient traffic monitoring, worker compliance monitoring, and optimized operational efficiency. However, the application has disadvantages such as potential false alarms, initial setup complexity, and dependency on existing CCTV infrastructure. The FAQ section addresses common queries about the application, including integration, customization, and compatibility. AI Bot Eye is suitable for jobs such as security guard, surveillance analyst, system integrator, security consultant, and safety officer. The AI keywords associated with the application include AI-based security system, CCTV integration, intrusion detection, and video analytics. Users can utilize AI Bot Eye for tasks like monitor intrusion, analyze foot traffic, detect fire, recognize faces, and manage vehicle entry.
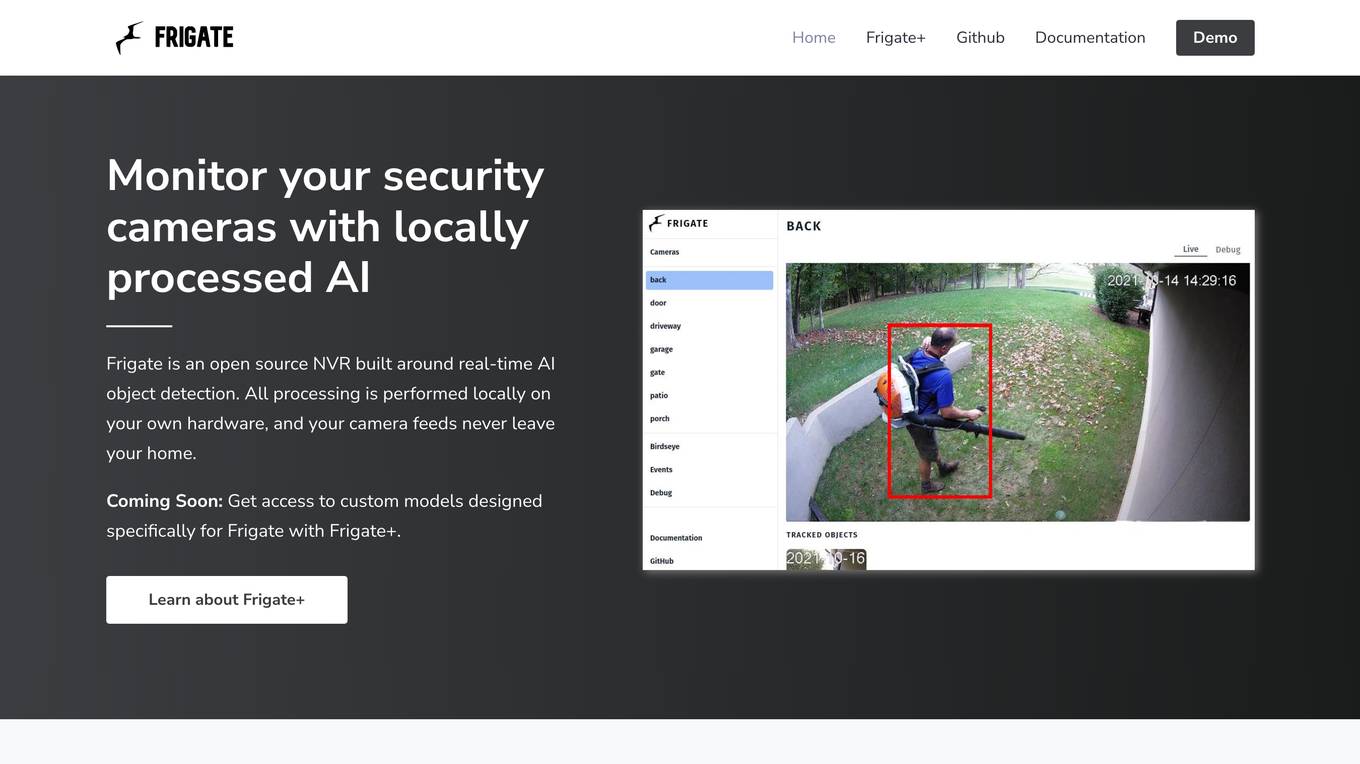
Frigate
Frigate is an open source NVR application that focuses on locally processed AI object detection for security camera monitoring. It offers custom models with Frigate+ to enhance detection accuracy. The application is designed for privacy-focused home automation enthusiasts, aiming to reduce false positives and provide real-time object tracking without sending camera feeds to the cloud. Frigate integrates with Home Assistant and other automation platforms for seamless control and automation of security systems.
Protect AI
Protect AI is a comprehensive platform designed to secure AI systems by providing visibility and manageability to detect and mitigate unique AI security threats. The platform empowers organizations to embrace a security-first approach to AI, offering solutions for AI Security Posture Management, ML model security enforcement, AI/ML supply chain vulnerability database, LLM security monitoring, and observability. Protect AI aims to safeguard AI applications and ML systems from potential vulnerabilities, enabling users to build, adopt, and deploy AI models confidently and at scale.
OpenBuckets
OpenBuckets is a web application designed to help users find and secure open buckets in cloud storage systems. It provides a simple and efficient way to identify and protect sensitive data that may be exposed due to misconfigured cloud storage settings. With OpenBuckets, users can easily scan their cloud storage accounts for publicly accessible buckets and take necessary actions to safeguard their information.
Coram AI
Coram AI is a modern business video security platform that offers AI-powered solutions for various industries such as warehouse, manufacturing, healthcare, education, and more. It provides advanced features like gun detection, productivity alerts, facial recognition, and safety alerts to enhance security and operations. Coram AI's flexible architecture allows users to seamlessly integrate with any IP camera and scale effortlessly to meet their demands. With natural language search capabilities, users can quickly find relevant footage and improve decision-making. Trusted by local businesses and Fortune 500 companies, Coram AI delivers real business value through innovative AI tools and reliable customer support.
Turing AI
Turing AI is a cloud-based video security system powered by artificial intelligence. It offers a range of AI-powered video surveillance products and solutions to enhance safety, security, and operations. The platform provides smart video search capabilities, real-time alerts, instant video sharing, and hardware offerings compatible with various cameras. With flexible licensing options and integration with third-party devices, Turing AI is trusted by customers across industries for its robust and innovative approach to cloud video security.

Fathom5
Fathom5 is a company that specializes in the intersection of AI and industrial systems. They offer a range of products and services to help customers build more resilient, flexible, and efficient industrial systems. Fathom5's approach is unique in that they take a security-first approach to cyber-physical system design. This means that security is built into every stage of the development process, from ideation to engineering to testing to deployment. This approach has been proven to achieve higher system resiliency and faster regulatory compliance at a reduced cost.

Fathom5
Fathom5 is a company that specializes in the intersection of AI and industrial systems. They offer a range of products and services to help customers build the industrial systems of the future. Their solutions are focused on critical infrastructure, making it more resilient, flexible, and efficient.
Ascento
Ascento is an AI-powered security solution that combines robotics and artificial intelligence to secure assets and provide quantitative insights of premises. The application offers features such as detecting people on premises, verifying perimeter integrity, recording property lights, scanning for thermal anomalies, controlling parking lots, and checking doors and windows. Ascento provides advantages like faster threat detection with greater accuracy, cost reduction, autonomous all-terrain robot capabilities, encrypted live communication, and integration with existing video management systems. However, some disadvantages include the need for immediate cost-benefits, training and onboarding requirements, and limited battery life for autonomous charging. The application is suitable for various industries and offers a turnkey solution with 24/7 support and fast replacements.
LogicMonitor
LogicMonitor is a cloud-based infrastructure monitoring platform that provides real-time insights and automation for comprehensive, seamless monitoring with agentless architecture. It offers a wide range of features including infrastructure monitoring, network monitoring, server monitoring, remote monitoring, virtual machine monitoring, SD-WAN monitoring, database monitoring, storage monitoring, configuration monitoring, cloud monitoring, container monitoring, AWS Monitoring, GCP Monitoring, Azure Monitoring, digital experience SaaS monitoring, website monitoring, APM, AIOPS, Dexda Integrations, security dashboards, and platform demo logs. LogicMonitor's AI-driven hybrid observability helps organizations simplify complex IT ecosystems, accelerate incident response, and thrive in the digital landscape.
FriendliAI
FriendliAI is a generative AI infrastructure company that offers efficient, fast, and reliable generative AI inference solutions for production. Their cutting-edge technologies enable groundbreaking performance improvements, cost savings, and lower latency. FriendliAI provides a platform for building and serving compound AI systems, deploying custom models effortlessly, and monitoring and debugging model performance. The application guarantees consistent results regardless of the model used and offers seamless data integration for real-time knowledge enhancement. With a focus on security, scalability, and performance optimization, FriendliAI empowers businesses to scale with ease.
Fastn
Fastn is a no-code, AI-powered orchestration platform for developers to integrate and orchestrate multiple data sources in a single, unified API. It allows users to connect any data flow and create hundreds of app integrations efficiently. Fastn simplifies API integration, ensures API security, and handles data from multiple sources with features like real-time data orchestration, instant API composition, and infrastructure management on autopilot.
AltrumAI
AltrumAI is an AI application that provides a platform for enterprises to control and monitor their AI systems in real-time. It offers solutions for deploying and scaling AI safely and compliantly, addressing compliance, security, and operational risks. The application empowers teams with intuitive policy configuration and enforcement, ensuring secure and seamless integration of Generative AI across the enterprise. AltrumAI aims to mitigate risks such as bias, data leaks, and unreliable AI outputs, while providing comprehensive AI risk coverage through guardrails and real-time monitoring.

spektr
spektr is an AI application that offers hyper-configurable compliance and onboarding solutions. It provides automated KYC/AML checks, continuous compliance monitoring, case management, alert automation, and AI-powered platform features to streamline compliance processes for enterprises. The platform is designed to handle routine tasks, enrich client data, and integrate various compliance tools and data sources. spektr is certified for ISO/IEC 27001:2022 and GDPR compliance, ensuring data security and privacy. It offers no-code and API integration options for flexible customization and seamless integration with existing systems.
Flutch
Flutch is a platform that specializes in custom AI agent development for various tasks. It offers AI agents support with measurable effects, from proof of concept to production. The platform provides integrations with systems and knowledge bases, full analytics, and quality control. Users can manage agents without the need for developers, enabling them to configure prompts, connect knowledge bases, and configure logic through an intuitive web interface. Flutch emphasizes cost control, security, and transparent management of AI agents, ensuring data security and control. The platform also offers a custom agent development service for unique business processes, including business process analysis, AI strategy, integration with systems, team training, and support.
Kami Home
Kami Home is an AI-powered security application that provides effortless safety and security for homes. It offers smart alerts, secure cloud video storage, and a Pro Security Alarm system with 24/7 emergency response. The application uses AI-vision to detect humans, vehicles, and animals, ensuring that users receive custom alerts for relevant activities. With features like Fall Detect for seniors living at home, Kami Home aims to protect families and provide peace of mind through advanced technology.
Spot AI
Spot AI is an AI camera system and video surveillance platform that offers AI Security Guard and AI Operations Assistant services. It provides extra protection without the payroll, scales the best operators, and deploys AI agents to standardize operations, coach teams, and execute real-time actions. The platform converts critical moments into context-rich judgments, launches automatic actions, and allows users to analyze, dissect, grade, and relay video content in seconds. Spot AI offers premium cameras, cloud dashboard for incident resolution, and intelligent video recording with on-edge AI processing. It helps enhance safety, efficiency, and productivity across various industries.
Omnilert
Omnilert is an AI-powered platform that provides active shooter protection and emergency communications solutions. It offers gun detection technology, emergency response automation, and real-time monitoring to help organizations respond swiftly to threats and keep people safe. With a focus on maximizing every critical second, Omnilert revolutionizes safety across various industries by combining AI-powered monitoring software with human verification. The platform is trusted by thousands of customers worldwide for its accuracy, low false positive rate, and innovative approach to safeguarding people, facilities, and operations.

Josh.ai
Josh.ai is an advanced AI control system for the smart home that utilizes natural interfaces like voice and touch to orchestrate technology in all aspects of the home. It aims to inspire, embolden, and delight users by providing an exciting and effortless living experience. Josh.ai is evolving to deliver its supercharged JoshGPT assistant at home and on-the-go, offering seamless integration with connected devices for smart home control and customization. With a focus on privacy, innovation, beauty, peace, comfort, flexibility, simplicity, security, delight, time, wellness, intelligence, and magic, Josh.ai is designed to empower every family member with intuitive control and intelligent assistance.
0 - Open Source AI Tools
20 - OpenAI Gpts

InfoSec Advisor
An expert in the technical, organizational, infrastructural and personnel aspects of information security management systems (ISMS)
Secure Space Advisor
Technical satellite security expert trained on space focused cybersecurity frameworks, best practices and process.
A Monitoring Expert
Expert in host monitoring setup, providing seamless network monitoring solutions.

NetMaster Pro 🌐🛠️
Your AI network guru for setup and fixing connectivity woes! 🌐 Assists with network configurations, troubleshooting, and optimizes your internet experience. 💻✨
Log Analyzer
I'm designed to help You analyze any logs like Linux system logs, Windows logs, any security logs, access logs, error logs, etc. Please do not share information that You would like to keep private. The author does not collect or process any personal data.
Information Assurance Advisor
Ensures information security through policy development and risk assessments.
DevSecOps Guides
Comprehensive resource for integrating security into the software development lifecycle.
Defender for Endpoint Guardian
To assist individuals seeking to learn about or work with Microsoft's Defender for Endpoint. I provide detailed explanations, step-by-step guides, troubleshooting advice, cybersecurity best practices, and demonstrations, all specifically tailored to Microsoft Defender for Endpoint.

NICE Match
Expert advice in education and cybersecurity, based on NICE Framework and CIS Controls