Best AI tools for< Analyze Security Posture >
20 - AI tool Sites
CYBER AI
CYBER AI is a security report savant powered by DEPLOYH.AI that simplifies cybersecurity for businesses. It offers a range of features to help organizations understand, unlock, and uncover security threats, including security reports, databreach reports, logs, and threat hunting. With CYBER AI, businesses can gain a comprehensive view of their security posture and take proactive steps to mitigate risks.

Relyance AI
Relyance AI is a platform that offers 360 Data Governance and Trust solutions. It helps businesses safeguard against fines and reputation damage while enhancing customer trust to drive business growth. The platform provides visibility into enterprise-wide data processing, ensuring compliance with regulatory and customer obligations. Relyance AI uses AI-powered risk insights to proactively identify and address risks, offering a unified trust and governance infrastructure. It offers features such as data inventory and mapping, automated assessments, security posture management, and vendor risk management. The platform is designed to streamline data governance processes, reduce costs, and improve operational efficiency.
Vanna.AI
Vanna.AI is a personalized AI SQL agent that allows users to get actionable insights from their database by simply asking questions. It helps users to write SQL queries efficiently and generate insights without the need for expert SQL knowledge. The application is open-source, highly accurate on complex datasets, designed for security, self-learning, and supports various databases. Vanna.AI is fully customizable to match unique needs and offers enterprise customization options.
Traceable
Traceable is an AI-driven application designed to enhance API security for Cloud-Native Apps. It collects API traffic across the application landscape and utilizes advanced context-based behavioral analytics AI engine to provide insights on APIs, data exposure, threat analytics, and forensics. The platform offers features for API cataloging, activity monitoring, endpoint details, ownership, vulnerabilities, protection against security events, testing, analytics, and more. Traceable also allows for role-based access control, policy configuration, data classification, and integration with third-party solutions for data collection and security. It is a comprehensive tool for API security and threat detection in modern cloud environments.
Sexy.ai
Sexy.ai is an AI-powered security service provided by Cloudflare to protect websites from online attacks. It helps in identifying and blocking malicious activities such as submitting certain words or phrases, SQL commands, or malformed data. The tool uses advanced algorithms to detect potential threats and prevent unauthorized access to websites. Sexy.ai ensures the safety and integrity of online platforms by offering robust security solutions.
Dynatrace
Dynatrace is a modern cloud platform that offers unified observability and security solutions to simplify cloud complexity and drive innovation. Powered by causal AI, Dynatrace provides analytics and automation capabilities to help businesses monitor and secure their full stack, solve digital challenges, and make better business decisions in real-time. Trusted by thousands of global brands, Dynatrace empowers teams to deliver flawless digital experiences, drive intelligent cloud ecosystem automations, and solve any use-case with custom solutions.
Coalition for Secure AI (CoSAI)
The Coalition for Secure AI (CoSAI) is an open ecosystem of AI and security experts dedicated to sharing best practices for secure AI deployment and collaborating on AI security research and product development. It aims to foster a collaborative ecosystem of diverse stakeholders to invest in AI security research collectively, share security expertise and best practices, and build technical open-source solutions for secure AI development and deployment.
TechSpective
TechSpective is an AI tool that provides technology reviews, podcasts, security insights, and Microsoft news and analysis. The platform offers in-depth articles on cybersecurity, artificial intelligence, and emerging technologies. Users can stay informed about the latest trends in the tech industry and learn about innovative products and solutions.

noluai.com
The website page provides detailed insights into the mechanics and technologies behind poker platforms in the online gaming industry. It delves into topics such as Random Number Generators (RNGs), fair play, anti-cheat technologies, server-side logic, player matching, platform stability, multi-table functionality, mobile vs desktop platforms, in-game communication systems, real-time hand histories, hand evaluation algorithms, card shuffling algorithms, security layers, handling player disconnections, payment system integration, casino bonus integration, leaderboards, low latency importance, rebuy and add-on mechanics, automatic tournament scheduling, Sit & Go vs scheduled tournaments, virtual economy, AI opponents, player statistics, sound design, testing processes, technical issues, emerging technologies, regulatory compliance, taxes handling, game variations, card animation, and the future of poker platform mechanics.
Center for a New American Security
The Center for a New American Security (CNAS) is a bipartisan, non-profit think tank that focuses on national security and defense policy. CNAS conducts research, analysis, and policy development on a wide range of topics, including defense strategy, nuclear weapons, cybersecurity, and energy security. CNAS also provides expert commentary and analysis on current events and policy debates.
AquilaX
AquilaX is an AI-powered DevSecOps platform that simplifies security and accelerates development processes. It offers a comprehensive suite of security scanning tools, including secret identification, PII scanning, SAST, container scanning, and more. AquilaX is designed to integrate seamlessly into the development workflow, providing fast and accurate results by leveraging AI models trained on extensive datasets. The platform prioritizes developer experience by eliminating noise and false positives, making it a go-to choice for modern Secure-SDLC teams worldwide.
Research Center Trustworthy Data Science and Security
The Research Center Trustworthy Data Science and Security is a hub for interdisciplinary research focusing on building trust in artificial intelligence, machine learning, and cyber security. The center aims to develop trustworthy intelligent systems through research in trustworthy data analytics, explainable machine learning, and privacy-aware algorithms. By addressing the intersection of technological progress and social acceptance, the center seeks to enable private citizens to understand and trust technology in safety-critical applications.
GetLuminal
GetLuminal.com is a website that provides information about a security certificate error related to the website itself. The site warns users about potential privacy risks and advises on actions to take when encountering such errors. It offers insights into security certificate expiration, potential threats from attackers, and guidance on system clock settings. Users can learn about security measures, certificate transparency, and how to enhance web security.
VULNWatch
VULNWatch is a web security platform that simplifies and makes website security accessible. The platform offers automated assessments using AI-powered tools with over 13 years of experience. It empowers business owners and developers to identify and address vulnerabilities quickly and easily in one place. VULNWatch provides effective web security assessment, including fingerprinting, protection against SQL injections, and web shells, with a focus on communication and collaboration with clients to ensure tailored cybersecurity solutions.
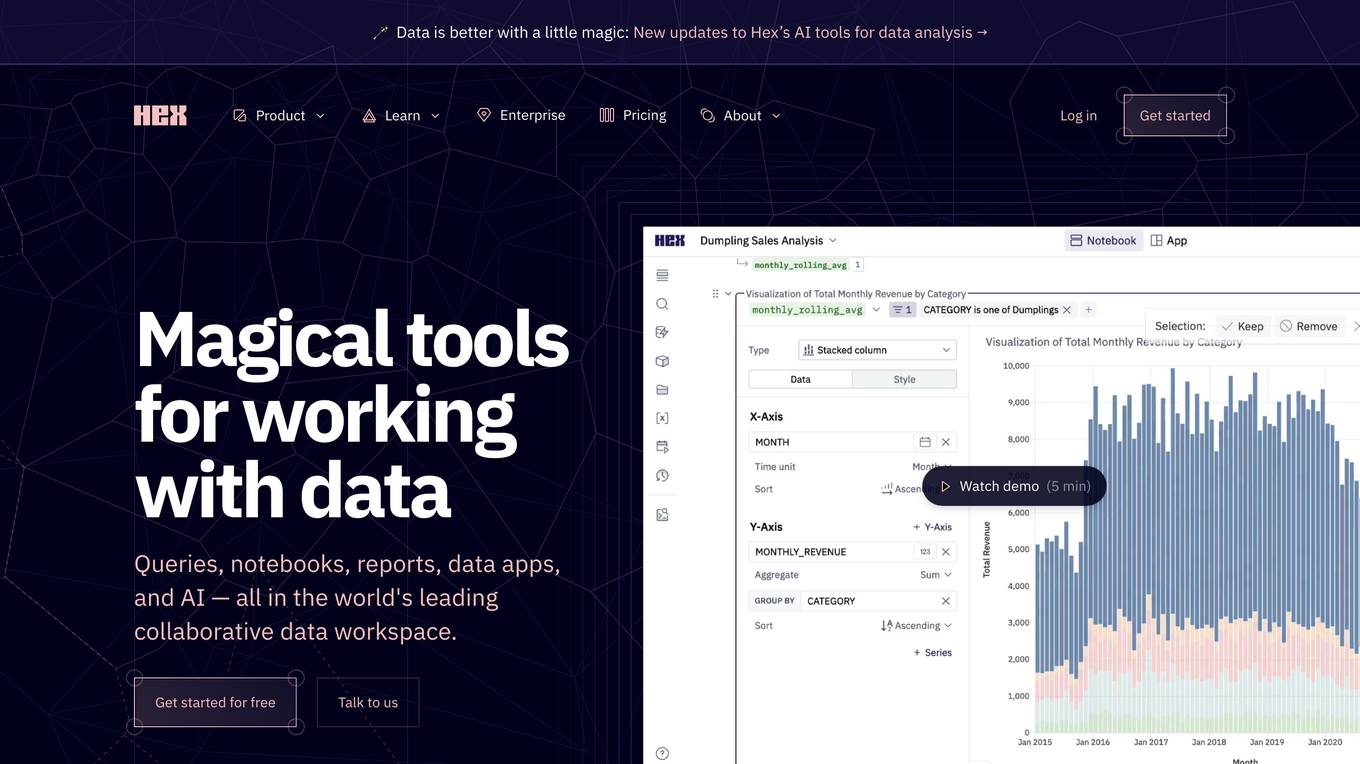
Hex
Hex is a collaborative data workspace that provides a variety of tools for working with data, including queries, notebooks, reports, data apps, and AI. It is designed to be easy to use for people of all technical skill levels, and it integrates with a variety of other tools and services. Hex is a powerful tool for data exploration, analysis, and visualization.
Elastic
Elastic is a Search AI Company that offers a platform for building tailored experiences, search and analytics, data ingestion, visualization, and generative AI solutions. The company provides services like Elastic Cloud for real-time insights, Elastic AI Assistant for retrieval and generation, and Search AI Lake for faster integration with LLMs. Elastic aims to help businesses scale with low-latency search AI and accelerate problem resolution with observability powered by advanced ML and analytics.
Global Threat
Global Threat is an AI-driven platform that provides real-time global threat assessment by continuously monitoring and analyzing various data sources worldwide. It empowers users, governments, organizations, and security teams with comprehensive insights into evolving threats, utilizing advanced data analytics, machine learning algorithms, and predictive modeling. The platform offers actionable intelligence on geopolitical shifts, cyber threats, natural disasters, and public health emergencies to keep users ahead of potential risks. Stay informed, prepared, and protected with unparalleled efficiency and accuracy in a data-driven security intelligence era.
Turing AI
Turing AI is a cloud-based video security system powered by artificial intelligence. It offers a range of AI-powered video surveillance products and solutions to enhance safety, security, and operations. The platform provides smart video search capabilities, real-time alerts, instant video sharing, and hardware offerings compatible with various cameras. With flexible licensing options and integration with third-party devices, Turing AI is trusted by customers across industries for its robust and innovative approach to cloud video security.
Neurotechnology
Neurotechnology is an AI-driven company specializing in biometric technologies, artificial intelligence, and computer vision. With over 35 years of research and development experience, the company offers a wide range of products and solutions for biometric identification, surveillance, and authentication. Neurotechnology's innovative AI applications are used in various industries, including security, law enforcement, and healthcare, to enhance efficiency and accuracy in identity verification and data analysis.
AI Bot Eye
AI Bot Eye is an AI-based security system that seamlessly integrates with existing CCTV systems to deliver intelligent insights. From AI-powered Fire Detection to Real-Time Intrusion Alerts, AI Bot Eye elevates security systems with cutting-edge AI technology. The application offers features such as Intrusion Detection, Face Recognition, Fire and Smoke Detection, Speed Cam Mode, Safety Kit Detection, HeatMaps Insights, Foot Traffic Analysis, and Numberplate recognition. AI Bot Eye provides advantages like real-time alerts, enhanced security, efficient traffic monitoring, worker compliance monitoring, and optimized operational efficiency. However, the application has disadvantages such as potential false alarms, initial setup complexity, and dependency on existing CCTV infrastructure. The FAQ section addresses common queries about the application, including integration, customization, and compatibility. AI Bot Eye is suitable for jobs such as security guard, surveillance analyst, system integrator, security consultant, and safety officer. The AI keywords associated with the application include AI-based security system, CCTV integration, intrusion detection, and video analytics. Users can utilize AI Bot Eye for tasks like monitor intrusion, analyze foot traffic, detect fire, recognize faces, and manage vehicle entry.
1 - Open Source AI Tools
aisbom
AIsbom is a specialized security and compliance scanner for Machine Learning artifacts. It performs Deep Binary Introspection on model files to detect malware risks and legal license violations hidden inside the serialized weights. The tool generates a compliant sbom.json (CycloneDX v1.6) including SHA256 hashes and license data. AIsbom also offers features like remote scanning on Hugging Face, config drift detection, strict mode for allowlisting, migration readiness for upcoming PyTorch changes, and markdown reporting for CI/CD integration. It advocates for a defense-in-depth strategy by combining static analysis and runtime isolation to ensure security. The tool visualizes security posture using an offline viewer and provides a trust factor by allowing users to generate safe mock artifacts for verification.
20 - OpenAI Gpts
SSLLMs Advisor
Helps you build logic security into your GPTs custom instructions. Documentation: https://github.com/infotrix/SSLLMs---Semantic-Secuirty-for-LLM-GPTs
Cyber security analyst
Designed to help cybersecurity analysts # ISO # NIST # COBIT # SANS # PCI DSS

CISO GPT
Specialized LLM in computer security, acting as a CISO with 20 years of experience, providing precise, data-driven technical responses to enhance organizational security.
fox8 botnet paper
A helpful guide for understanding the paper "Anatomy of an AI-powered malicious social botnet"

TheDFIRReport Assistant
Detailed insights from TheDFIRReport's 2021-2023 reports, including Detections and Indicators.

Phish or No Phish Trainer
Hone your phishing detection skills! Analyze emails, texts, and calls to spot deception. Become a security pro!
Log Analyzer
I'm designed to help You analyze any logs like Linux system logs, Windows logs, any security logs, access logs, error logs, etc. Please do not share information that You would like to keep private. The author does not collect or process any personal data.
Message Header Analyzer
Analyzes email headers for security insights, presenting data in a structured table view.
Data Protection Assistant
Expert in data protection laws, ready to analyze documents and answer related queries.
Phoenix Vulnerability Intelligence GPT
Expert in analyzing vulnerabilities with ransomware focus with intelligence powered by Phoenix Security
Incident Response Forensic Techniques
help organizations in investigating computer security incidents and troubleshooting some information technology (IT) operational problems by providing practical guidance on performing computer and network forensics.