Best AI tools for< Threat Intelligence Researcher >
Infographic
20 - AI tool Sites
Constella Intelligence
Constella Intelligence is a world-class identity protection and identity risk intelligence platform powered by AI and the world's largest breach data lake. It offers solutions for API integrations, identity theft monitoring, threat intelligence, identity fraud detection, digital risk protection services, executive and brand protection, OSINT cybercrime investigations, and threat monitoring and alerting. Constella provides precise and timely alerts, in-depth real-time identity data signals, and enhanced situational awareness to help organizations combat cyber threats effectively.
MixMode
MixMode is the world's most advanced AI for threat detection, offering a dynamic threat detection platform that utilizes patented Third Wave AI technology. It provides real-time detection of known and novel attacks with high precision, self-supervised learning capabilities, and context-awareness to defend against modern threats. MixMode empowers modern enterprises with unprecedented speed and scale in threat detection, delivering unrivaled capabilities without the need for predefined rules or human input. The platform is trusted by top security teams and offers rapid deployment, customization to individual network dynamics, and state-of-the-art AI-driven threat detection.
Cyble
Cyble is a leading threat intelligence platform offering products and services recognized by top industry analysts. It provides AI-driven cyber threat intelligence solutions for enterprises, governments, and individuals. Cyble's offerings include attack surface management, brand intelligence, dark web monitoring, vulnerability management, takedown and disruption services, third-party risk management, incident management, and more. The platform leverages cutting-edge AI technology to enhance cybersecurity efforts and stay ahead of cyber adversaries.
ODIN
ODIN is a powerful internet scanning search engine designed for scanning and cataloging internet assets. It offers enhanced scanning capabilities, faster refresh rates, and comprehensive visibility into open ports. With over 45 modules covering various aspects like HTTP, Elasticsearch, and Redis, ODIN enriches data and provides accurate and up-to-date information. The application uses AI/ML algorithms to detect exposed buckets, files, and potential vulnerabilities. Users can perform granular searches, access exploit information, and integrate effortlessly with ODIN's API, SDKs, and CLI. ODIN allows users to search for hosts, exposed buckets, exposed files, and subdomains, providing detailed insights and supporting diverse threat intelligence applications.
ODIN
ODIN is a powerful internet scanning search engine designed for scanning and cataloging internet assets. It offers enhanced scanning capabilities, faster refresh rates, and comprehensive visibility into open ports. With over 45 modules covering various services, ODIN provides detailed insights using Lucene query syntax. It identifies potential CVEs, accesses exploit information, and enables reverse searches for threat investigations. ODIN also offers AI/ML-based exposed buckets detection, API integration, and SDKs in multiple languages. Users can search for hosts, exposed buckets, exposed files, and subdomains, with granular searches and seamless integrations. The application is developer-friendly, with APIs, SDKs, and CLI available for automation and programmatic integration.
SentinelOne
SentinelOne is an advanced enterprise cybersecurity AI platform that offers a comprehensive suite of AI-powered security solutions for endpoint, cloud, and identity protection. The platform leverages artificial intelligence to anticipate threats, manage vulnerabilities, and protect resources across the entire enterprise ecosystem. With features such as Singularity XDR, Purple AI, and AI-SIEM, SentinelOne empowers security teams to detect and respond to cyber threats in real-time. The platform is trusted by leading enterprises worldwide and has received industry recognition for its innovative approach to cybersecurity.
OpenBuckets
OpenBuckets is a web application designed to help users find and secure open buckets in cloud storage systems. It provides a simple and efficient way to identify and protect sensitive data that may be exposed due to misconfigured cloud storage settings. With OpenBuckets, users can easily scan their cloud storage accounts for publicly accessible buckets and take necessary actions to safeguard their information.
Palo Alto Networks
Palo Alto Networks is a cybersecurity company offering advanced security solutions powered by Precision AI to protect modern enterprises from cyber threats. The company provides network security, cloud security, and AI-driven security operations to defend against AI-generated threats in real time. Palo Alto Networks aims to simplify security and achieve better security outcomes through platformization, intelligence-driven expertise, and proactive monitoring of sophisticated threats.
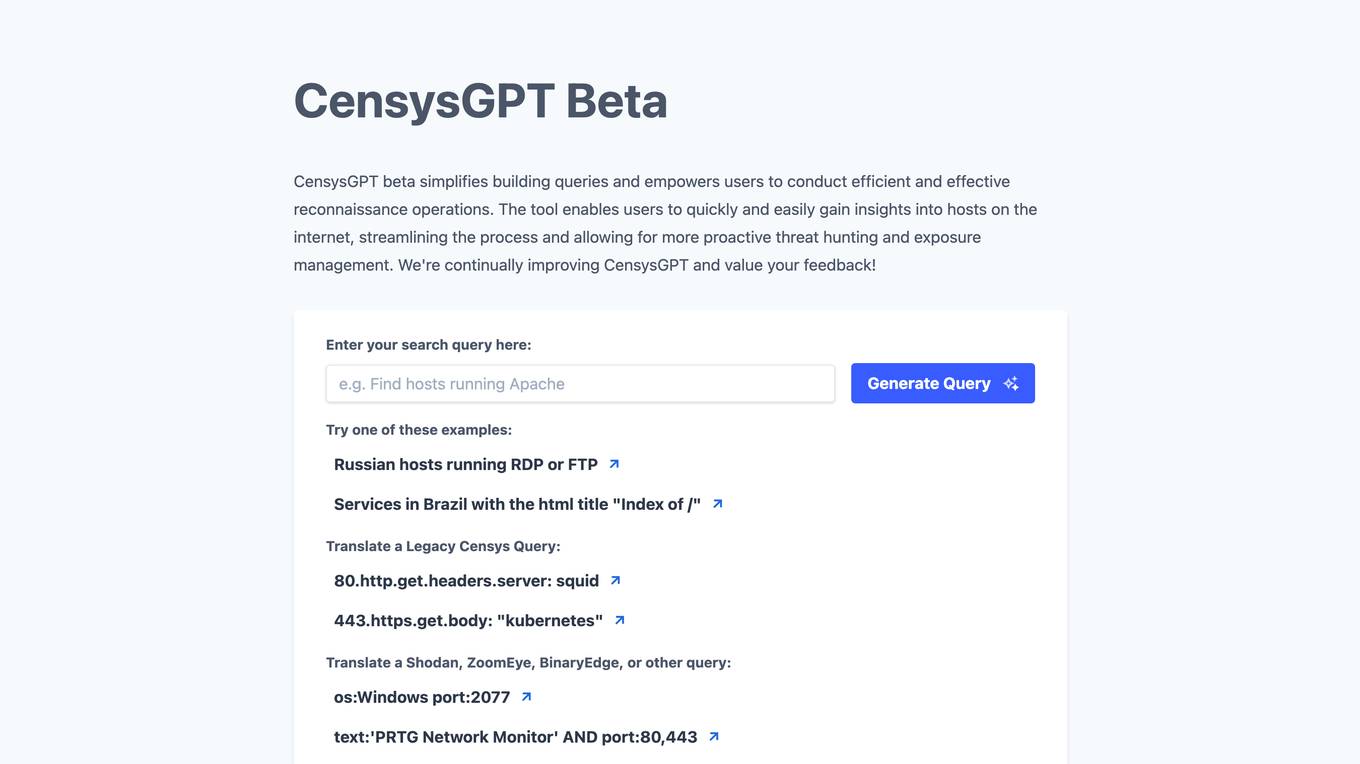
CensysGPT Beta
CensysGPT Beta is a tool that simplifies building queries and empowers users to conduct efficient and effective reconnaissance operations. It enables users to quickly and easily gain insights into hosts on the internet, streamlining the process and allowing for more proactive threat hunting and exposure management.
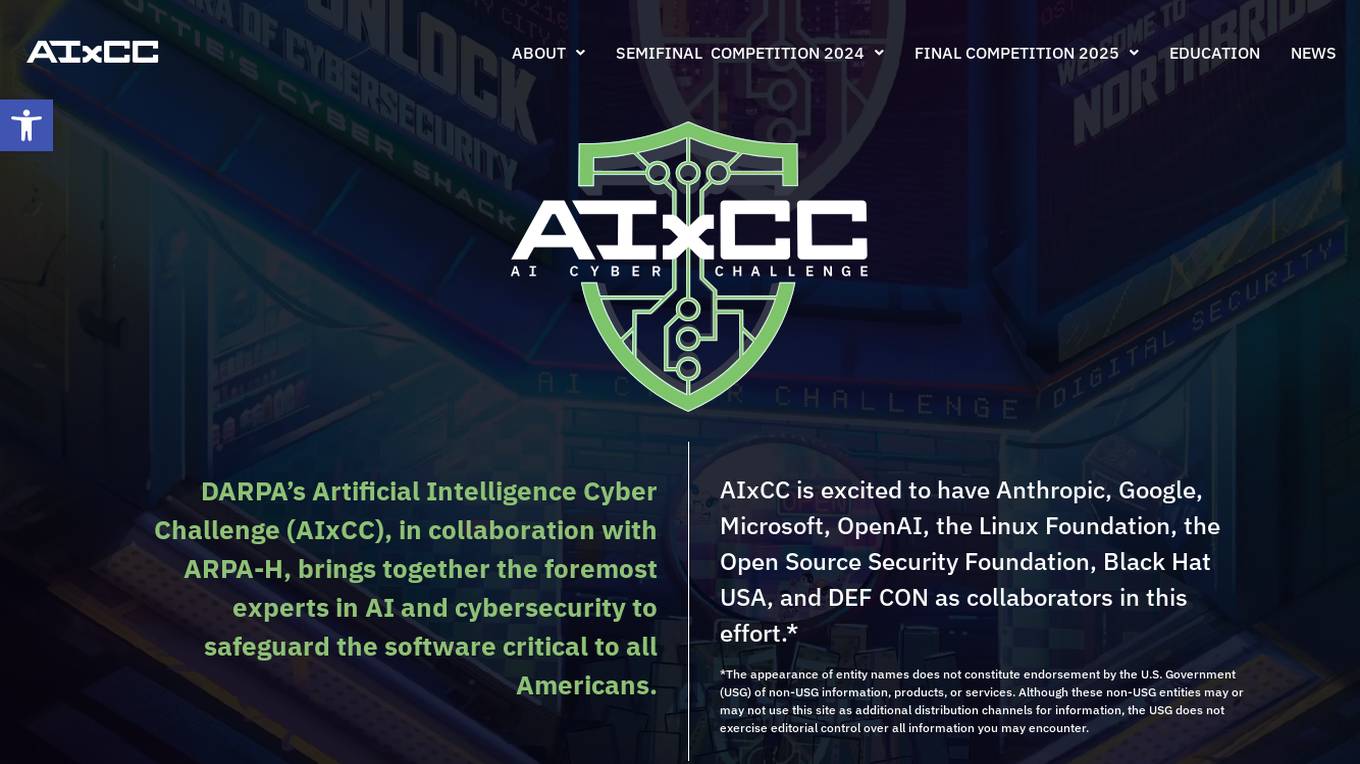
DARPA's Artificial Intelligence Cyber Challenge (AIxCC)
The DARPA's Artificial Intelligence Cyber Challenge (AIxCC) is an AI-driven cybersecurity tool developed in collaboration with ARPA-H and various industry experts like Anthropic, Google, Microsoft, OpenAI, and others. It aims to safeguard critical software infrastructure by utilizing AI technology to enhance cybersecurity measures. The tool provides a platform for experts in AI and cybersecurity to come together and address the evolving threats in the digital landscape.
Lunit AI
Lunit Inc. is a leading provider of AI-powered cancer screening and treatment solutions. The company's mission is to conquer cancer through AI by developing innovative technologies that can help detect and treat cancer earlier and more effectively. Lunit's AI solutions are used by hospitals and clinics around the world to improve the accuracy and efficiency of cancer diagnosis and treatment.
Logically
Logically is an AI-powered platform that helps governments, NGOs, and enterprise organizations detect and address harmful and deliberately inaccurate information online. The platform combines artificial intelligence with human expertise to deliver actionable insights and reduce the harms associated with misleading or deceptive information. Logically offers services such as Analyst Services, Logically Intelligence, Point Solutions, and Trust and Safety, focusing on threat detection, online narrative detection, intelligence reports, and harm reduction. The platform is known for its expertise in analysis, data science, and government affairs, providing solutions for various sectors including Corporate, Defense, Digital Platforms, Elections, National Security, and NGO Solutions.
Center for a New American Security
The Center for a New American Security (CNAS) is a bipartisan, non-profit think tank that focuses on national security and defense policy. CNAS conducts research, analysis, and policy development on a wide range of topics, including defense strategy, nuclear weapons, cybersecurity, and energy security. CNAS also provides expert commentary and analysis on current events and policy debates.
Orbital Insight GO Platform
Orbital Insight is a leading geospatial data analytics platform that provides users with the ability to query the world with three basic parameters: WHAT type of activity? WHERE on earth? WHEN? The platform automates the most difficult steps of deriving insights, allowing you to answer many challenging geospatial questions. Orbital Insight's GO platform is designed for enterprise collaboration and transforms multiple geospatial data sources to accelerate and streamline team member's research, reporting, due diligence, and more.
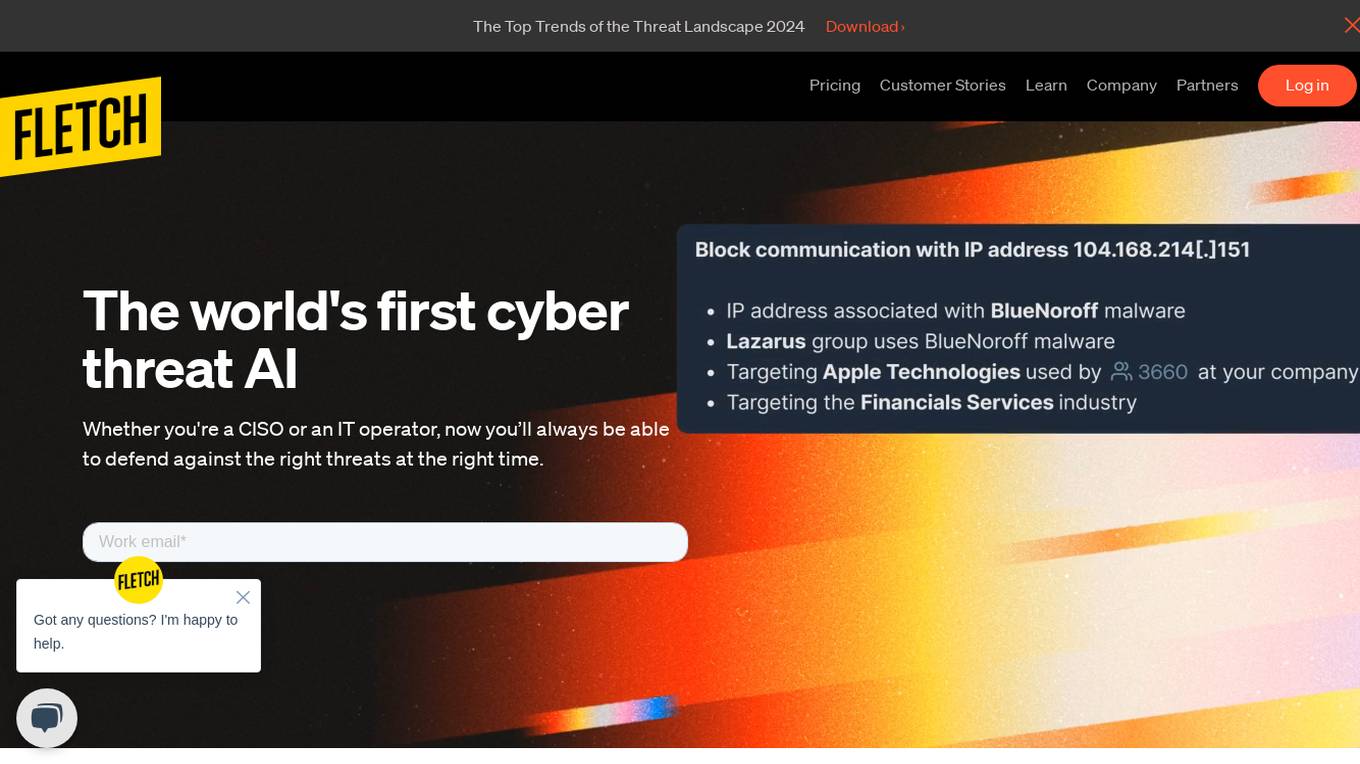
Fletch
Fletch is the world's first cyber threat AI application that helps users stay ahead of cyber threats by automating busywork with AI agents. It continuously trends the threat landscape, forecasts impact, prioritizes alerts, generates tailored advice, and provides daily proactive insights to guide users in defending against threats. Fletch filters and prioritizes alerts, uncovers weaknesses in SaaS supply chains, and offers timely tactical advice to act fast in critical moments. The application also assists in articulating threat messages and provides instant answers through AskFletch chat. Fletch integrates with existing tools, simplifying users' lives and offering hands-on guidance for businesses of all sizes.
Lakera
Lakera is the world's most advanced AI security platform that offers cutting-edge solutions to safeguard GenAI applications against various security threats. Lakera provides real-time security controls, stress-testing for AI systems, and protection against prompt attacks, data loss, and insecure content. The platform is powered by a proprietary AI threat database and aligns with global AI security frameworks to ensure top-notch security standards. Lakera is suitable for security teams, product teams, and LLM builders looking to secure their AI applications effectively and efficiently.
Overwatch Data
Overwatch Data is an AI-powered threat intelligence platform designed to provide fraud and cyber threat intelligence to businesses. The platform utilizes AI agents to monitor over 300k sources, including deep & dark web channels and social media platforms, to deliver real-time threat intelligence. Overwatch helps businesses prevent fraud campaigns, data breaches, and cyberattacks by providing personalized and contextualized intelligence. The platform offers customizable AI agents, tailored intelligence workflows, and context-rich alerts to enable fraud and security teams to respond quickly and confidently to threats.
Vectra AI
Vectra AI is an advanced AI-driven cybersecurity platform that helps organizations detect, prioritize, investigate, and respond to sophisticated cyber threats in real-time. The platform provides Attack Signal Intelligence to arm security analysts with the necessary intel to stop attacks fast. Vectra AI offers integrated signal for extended detection and response (XDR) across various domains such as network, identity, cloud, and endpoint security. Trusted by 1,500 enterprises worldwide, Vectra AI is known for its patented AI security solutions that deliver the best attack signal intelligence on the planet.
Torq
Torq is an AI-driven platform that offers Security Hyperautomation Solutions, empowering security teams to detect, prioritize, and respond to threats faster. It provides a range of features and capabilities such as AI Agents, AI SOC Analyst, Case Management, and Integrations. Torq is trusted by top security teams worldwide and is recognized for its ability to mitigate alert fatigue, false positives, and staff burnout. The platform is designed to usher in the era of Autonomous SOC by harnessing AI to enhance security operations.
Bricklayer AI
Bricklayer AI is an automated AI security team that empowers Security Operations Centers (SOCs) to manage alerts, incidents, and threats efficiently. It offers autonomous AI agents designed to work collaboratively with human experts, enabling faster and more effective security operations. Bricklayer AI helps organizations stay ahead of cyber threats by automating labor-intensive tasks and providing real-time analysis and response.
0 - Open Source Tools
20 - OpenAI Gpts
Threat Intelligence Expert
Patient threat intelligence expert skilled in binary file analysis and YARA rules.
Threat Intel Briefs
Delivers daily, sector-specific cybersecurity threat intel briefs with source citations.
MagicUnprotect
This GPT allows to interact with the Unprotect DB to retrieve knowledge about malware evasion techniques
MITREGPT
Feed me any input and i'll match it with the relevant MITRE ATT&CK techniques and tactics (@mthcht)
MITRE Interpreter
This GPT helps you understand and apply the MITRE ATT&CK Framework, whether you are familiar with the concepts or not.
Malware Rule Master
Expert in malware analysis and Yara rules, using web sources for specifics.
CyberNews GPT
CyberNews GPT is an assistant that provides the latest security news about cyber threats, hackings and breaches, malware, zero-day vulnerabilities, phishing, scams and so on.
fox8 botnet paper
A helpful guide for understanding the paper "Anatomy of an AI-powered malicious social botnet"
T71 Russian Cyber Samovar
Analyzes and updates on cyber-related Russian APTs, cognitive warfare, disinformation, and other infoops.

TheDFIRReport Assistant
Detailed insights from TheDFIRReport's 2021-2023 reports, including Detections and Indicators.
Bug Insider
Analyzes bug bounty writeups and cybersecurity reports, providing structured insights and tips.
Business Consultant(Five forces analysis)
Business consultant conducting Five forces analysis.You can easily create a draft for consideration.