Best AI tools for< Security Operations Engineer >
Infographic
20 - AI tool Sites
Polymer DSPM
Polymer DSPM is an AI-driven Data Security Posture Management platform that offers Data Loss Prevention (DLP) and Breach Prevention solutions. It provides real-time data visibility, adaptive controls, and automated remediation to prevent data breaches. The platform empowers users to actively manage human-based risks and fosters enterprise-wide behavior change through real-time nudges and risk scoring. Polymer helps organizations secure their data in the age of AI by guiding employees in real-time to prevent accidental sharing of confidential information. It integrates with popular chat, file storage, and GenAI tools to protect sensitive data and reduce noise and data exposure. The platform leverages AI to contextualize risk, trigger security workflows, and actively nudge employees to reduce risky behavior over time.
Velotix
Velotix is an AI-powered data security platform that offers groundbreaking visual data security solutions to help organizations discover, visualize, and use their data securely and compliantly. The platform provides features such as data discovery, permission discovery, self-serve data access, policy-based access control, AI recommendations, and automated policy management. Velotix aims to empower enterprises with smart and compliant data access controls, ensuring data integrity and compliance. The platform helps organizations gain data visibility, control access, and enforce policy compliance, ultimately enhancing data security and governance.
Stellar Cyber
Stellar Cyber is an AI-driven unified security operations platform powered by Open XDR. It offers a single platform with NG-SIEM, NDR, and Open XDR, providing security capabilities to take control of security operations. The platform helps organizations detect, correlate, and respond to threats fast using AI technology. Stellar Cyber is designed to protect the entire attack surface, improve security operations performance, and reduce costs while simplifying security operations.
Bricklayer AI
Bricklayer AI is an automated AI security team that empowers Security Operations Centers (SOCs) to manage alerts, incidents, and threats efficiently. It offers autonomous AI agents designed to work collaboratively with human experts, enabling faster and more effective security operations. Bricklayer AI helps organizations stay ahead of cyber threats by automating labor-intensive tasks and providing real-time analysis and response.
Palo Alto Networks
Palo Alto Networks is a cybersecurity company offering advanced security solutions powered by Precision AI to protect modern enterprises from cyber threats. The company provides network security, cloud security, and AI-driven security operations to defend against AI-generated threats in real time. Palo Alto Networks aims to simplify security and achieve better security outcomes through platformization, intelligence-driven expertise, and proactive monitoring of sophisticated threats.
Cyguru
Cyguru is an all-in-one cloud-based AI Security Operation Center (SOC) that offers a comprehensive range of features for a robust and secure digital landscape. Its Security Operation Center is the cornerstone of its service domain, providing AI-Powered Attack Detection, Continuous Monitoring for Vulnerabilities and Misconfigurations, Compliance Assurance, SecPedia: Your Cybersecurity Knowledge Hub, and Advanced ML & AI Detection. Cyguru's AI-Powered Analyst promptly alerts users to any suspicious behavior or activity that demands attention, ensuring timely delivery of notifications. The platform is accessible to everyone, with up to three free servers and subsequent pricing that is more than 85% below the industry average.
Ambient.ai
Ambient.ai is an AI-powered physical security software that helps prevent security incidents by detecting threats in real-time, auto-clearing false alarms, and accelerating investigations. The platform uses computer vision intelligence to monitor cameras for suspicious activities, decrease alarms, and enable rapid investigations. Ambient.ai offers rich integration ecosystem, detections for a spectrum of threats, unparalleled operational efficiency, and enterprise-grade privacy to ensure maximum security and efficiency for its users.
Torq
Torq is an AI-driven platform that offers Security Hyperautomation Solutions, empowering security teams to detect, prioritize, and respond to threats faster. It provides a range of features and capabilities such as AI Agents, AI SOC Analyst, Case Management, and Integrations. Torq is trusted by top security teams worldwide and is recognized for its ability to mitigate alert fatigue, false positives, and staff burnout. The platform is designed to usher in the era of Autonomous SOC by harnessing AI to enhance security operations.
Protect AI
Protect AI is a comprehensive platform designed to secure AI systems by providing visibility and manageability to detect and mitigate unique AI security threats. The platform empowers organizations to embrace a security-first approach to AI, offering solutions for AI Security Posture Management, ML model security enforcement, AI/ML supply chain vulnerability database, LLM security monitoring, and observability. Protect AI aims to safeguard AI applications and ML systems from potential vulnerabilities, enabling users to build, adopt, and deploy AI models confidently and at scale.
CloudDefense.AI
CloudDefense.AI is an industry-leading multi-layered Cloud Native Application Protection Platform (CNAPP) that safeguards cloud infrastructure and cloud-native apps with expertise, precision, and confidence. It offers comprehensive cloud security solutions, vulnerability management, compliance, and application security testing. The platform utilizes advanced AI technology to proactively detect and analyze real-time threats, ensuring robust protection for businesses against cyber threats.

MLSecOps
MLSecOps is an AI tool designed to drive the field of MLSecOps forward through high-quality educational resources and tools. It focuses on traditional cybersecurity principles, emphasizing people, processes, and technology. The MLSecOps Community educates and promotes the integration of security practices throughout the AI & machine learning lifecycle, empowering members to identify, understand, and manage risks associated with their AI systems.
SharkGate
SharkGate is an AI-driven cybersecurity platform that focuses on protecting websites from various cyber threats. The platform offers solutions for mobile security, password management, quantum computing threats, API security, and cloud security. SharkGate leverages artificial intelligence and machine learning to provide advanced threat detection and response capabilities, ensuring the safety and integrity of digital assets. The platform has received accolades for its innovative approach to cybersecurity and has secured funding from notable organizations.
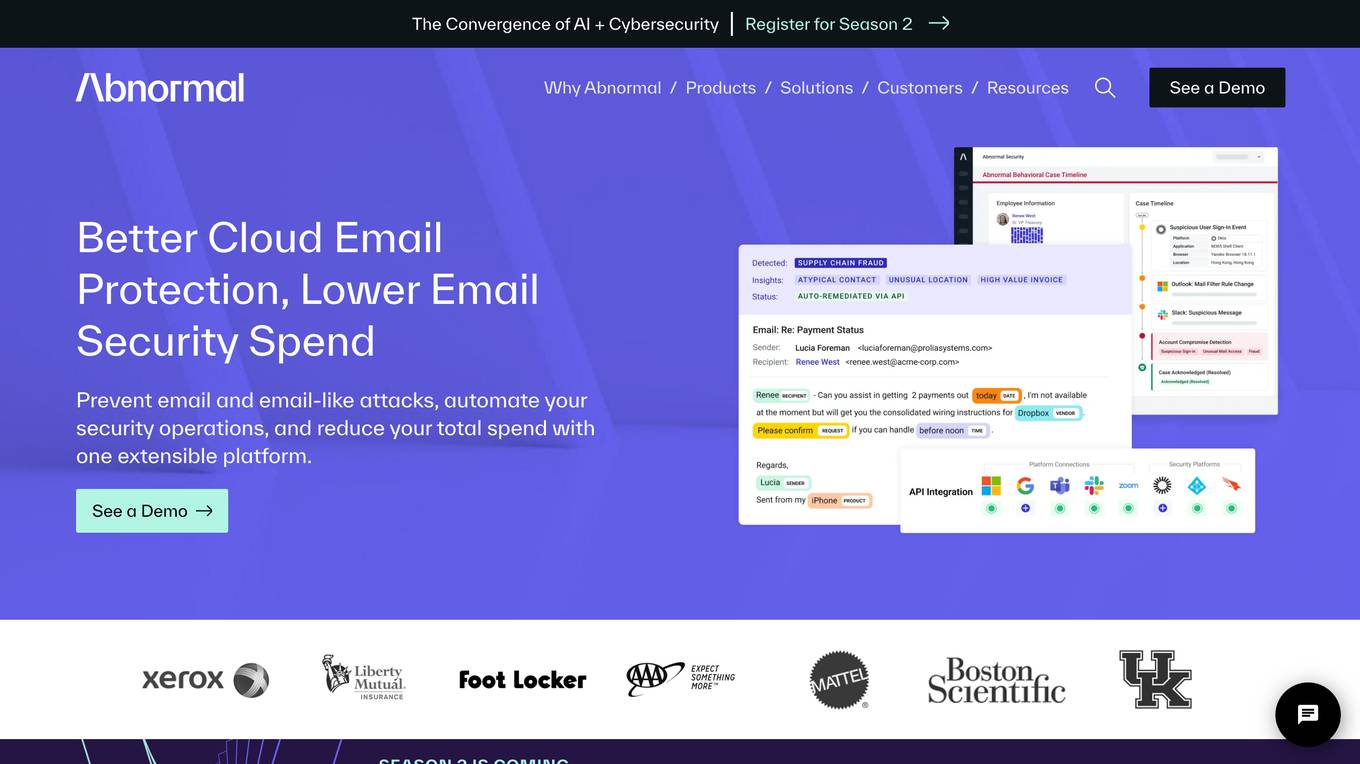
Abnormal
Abnormal is an AI-powered platform that leverages superhuman understanding of human behavior to protect against email attacks such as phishing, social engineering, and account takeovers. The platform offers unified protection across email and cloud applications, behavioral anomaly detection, account compromise detection, data security, and autonomous AI agents for security operations. Abnormal is recognized as a leader in email security and AI-native security, trusted by over 3,000 customers, including 20% of the Fortune 500. The platform aims to autonomously protect humans, reduce risks, save costs, accelerate AI adoption, and provide industry-leading security solutions.
Veriti
Veriti is an AI-driven platform that proactively monitors and safely remediates exposures across the entire security stack, without disrupting the business. It helps organizations maximize their security posture while ensuring business uptime. Veriti offers solutions for safe remediation, MITRE ATT&CK®, healthcare, MSSPs, and manufacturing. The platform correlates exposures to misconfigurations, continuously assesses exposures, integrates with various security solutions, and prioritizes remediation based on business impact. Veriti is recognized for its role in exposure assessments and remediation, providing a consolidated security platform for businesses to neutralize threats before they happen.
AirMDR
AirMDR is an AI-powered Managed Detection and Response (MDR) application that revolutionizes cybersecurity by leveraging artificial intelligence to automate routine tasks, enhance alert triage, investigation, and response processes. The application offers faster, higher-quality, and more affordable cybersecurity solutions, supervised by human experts. AirMDR aims to deliver unprecedented speed, superior quality, and cost-effective outcomes to cater to the unique demands of security operations centers.
n8n
n8n is a powerful workflow automation software and tools that offer advanced AI capabilities. It is a popular platform for technical teams to automate workflows, integrate various services, and build autonomous agents. With over 400 integrations, n8n enables users to save time, streamline operations, and enhance security through AI-driven processes. The tool supports self-hosting, external libraries, and offers enterprise-ready solutions for scaling operations. n8n empowers users to code iteratively, explore advanced AI features, and create complex workflows with ease.
n8n
n8n is a powerful workflow automation software and tool that offers advanced AI capabilities. It is a popular platform for technical teams to automate workflows, integrate various services, and build autonomous agents. With over 400 integrations, n8n enables users to save time, streamline operations, and enhance security through AI-powered solutions. The tool supports self-hosting, external libraries, and a user-friendly interface for both coding and non-coding users.
MixMode
MixMode is the world's most advanced AI for threat detection, offering a dynamic threat detection platform that utilizes patented Third Wave AI technology. It provides real-time detection of known and novel attacks with high precision, self-supervised learning capabilities, and context-awareness to defend against modern threats. MixMode empowers modern enterprises with unprecedented speed and scale in threat detection, delivering unrivaled capabilities without the need for predefined rules or human input. The platform is trusted by top security teams and offers rapid deployment, customization to individual network dynamics, and state-of-the-art AI-driven threat detection.
Vectra AI
Vectra AI is an advanced AI-driven cybersecurity platform that helps organizations detect, prioritize, investigate, and respond to sophisticated cyber threats in real-time. The platform provides Attack Signal Intelligence to arm security analysts with the necessary intel to stop attacks fast. Vectra AI offers integrated signal for extended detection and response (XDR) across various domains such as network, identity, cloud, and endpoint security. Trusted by 1,500 enterprises worldwide, Vectra AI is known for its patented AI security solutions that deliver the best attack signal intelligence on the planet.
Vectra AI
Vectra AI is a leading cybersecurity AI application that stops attacks that others cannot. It is recognized in the Gartner Magic Quadrant 2025 for Network Detection and Response (NDR) as a leader. Vectra AI's platform protects modern networks from advanced threats by providing real-time attack signal intelligence and AI-driven detections. It equips security analysts with the information needed to quickly stop attacks across various security application scenarios. The application covers a wide range of security areas such as SOC modernization, SIEM optimization, IDS replacement, EDR extension, cloud resilience, and more.
1 - Open Source Tools
uusec-waf
UUSEC WAF is an industrial grade free, high-performance, and highly scalable web application and API security protection product that supports AI and semantic engines. It provides intelligent 0-day defense, ultimate CDN acceleration, powerful proactive defense, advanced semantic engine, and advanced rule engine. With features like machine learning technology, cache cleaning, dual layer defense, semantic analysis, and Lua script rule writing, UUSEC WAF offers comprehensive website protection with three-layer defense functions at traffic, system, and runtime layers.
20 - OpenAI Gpts
Network Operations Advisor
Ensures efficient and effective network performance and security.
Network Architecture Advisor
Designs and optimizes organization's network architecture to ensure seamless operations.
CISO AI
Team of experts assisting CISOs, CIOs, Exec Teams, and Board Directors in cyber risk oversight and security program management, providing actionable strategic, operational, and tactical support. Enhanced with advanced technical security architecture and engineering expertise.
ethicallyHackingspace (eHs)® METEOR™ STORM™
Multiple Environment Threat Evaluation of Resources (METEOR)™ Space Threats and Operational Risks to Mission (STORM)™ non-profit product AI co-pilot
Cyber security analyst
Designed to help cybersecurity analysts # ISO # NIST # COBIT # SANS # PCI DSS
The Sabotage Strategist
Playful strategist using humor and proximity to offer 'sabotage' tactics from a 1944 OSS Manual.
T71 Russian Cyber Samovar
Analyzes and updates on cyber-related Russian APTs, cognitive warfare, disinformation, and other infoops.
Incident Response Forensic Techniques
help organizations in investigating computer security incidents and troubleshooting some information technology (IT) operational problems by providing practical guidance on performing computer and network forensics.

The Dorker
I help create precise Google Dork search strings using advanced search operators.
Your personal GRC & Security Tutor
A training tool for infosec professionals to improve their skills in GRC & security and help obtain related certifications.