Best AI tools for< Security Manager >
Infographic
20 - AI tool Sites

Start Left® Security
Start Left® Security is an AI-driven application security posture management platform that empowers product teams to automate secure-by-design software from people to cloud. The platform integrates security into every facet of the organization, offering a unified solution that aligns with business goals, fosters continuous improvement, and drives innovation. Start Left® Security provides a gamified DevSecOps experience with comprehensive security capabilities like SCA, SBOM, SAST, DAST, Container Security, IaC security, ASPM, and more.
Mimecast
Mimecast is an AI-powered email and collaboration security application that offers advanced threat protection, cloud archiving, security awareness training, and more. With a focus on protecting communications, data, and people, Mimecast leverages AI technology to provide industry-leading security solutions to organizations globally. The application is designed to defend against sophisticated email attacks, enhance human risk management, and streamline compliance processes.
Concentric AI
Concentric AI is a Managed Data Security Posture Management tool that utilizes Semantic Intelligence to provide comprehensive data security solutions. The platform offers features such as autonomous data discovery, data risk identification, centralized remediation, easy deployment, and data security posture management. Concentric AI helps organizations protect sensitive data, prevent data loss, and ensure compliance with data security regulations. The tool is designed to simplify data governance and enhance data security across various data repositories, both in the cloud and on-premises.
Varonis
Varonis is an AI-powered data security platform that provides end-to-end data security solutions for organizations. It offers automated outcomes to reduce risk, enforce policies, and stop active threats. Varonis helps in data discovery & classification, data security posture management, data-centric UEBA, data access governance, and data loss prevention. The platform is designed to protect critical data across multi-cloud, SaaS, hybrid, and AI environments.
icetana AI
icetana AI is a self-learning AI tool designed for real-time event detection in security surveillance systems. It seamlessly connects to existing security cameras, learns normal patterns, and highlights unusual events without compromising privacy. The system continuously evolves to improve security team decision-making. icetana AI offers a suite of products for safety and security, analytics, forensics, license plate recognition, facial recognition, and automating security workflows. It is ideal for industries like mall management, education, guarding services, safe cities, and more.
Cyguru
Cyguru is an all-in-one cloud-based AI Security Operation Center (SOC) that offers a comprehensive range of features for a robust and secure digital landscape. Its Security Operation Center is the cornerstone of its service domain, providing AI-Powered Attack Detection, Continuous Monitoring for Vulnerabilities and Misconfigurations, Compliance Assurance, SecPedia: Your Cybersecurity Knowledge Hub, and Advanced ML & AI Detection. Cyguru's AI-Powered Analyst promptly alerts users to any suspicious behavior or activity that demands attention, ensuring timely delivery of notifications. The platform is accessible to everyone, with up to three free servers and subsequent pricing that is more than 85% below the industry average.
Cyberday.ai
Cyberday.ai is an AI-powered platform designed to help organizations improve and certify their cybersecurity. The platform offers a comprehensive set of tools and resources to guide users in implementing security tasks, creating policies, and generating compliance reports. With a focus on automation and efficiency, Cyberday.ai streamlines the process of managing information security, from risk assessment to employee training. By leveraging AI technology, Cyberday.ai aims to simplify the complex task of cybersecurity management for organizations of all sizes.
Knostic AI
Knostic AI is an AI application that focuses on Copilot Readiness for Enterprise AI Security. It helps organizations locate and remediate data leaks from AI searches, ensuring data security and compliance. Knostic offers solutions to prevent data leakage, map knowledge boundaries, recommend permission adjustments, and provide independent verification of security posture readiness for AI adoption.
KnowBe4
KnowBe4 is a human risk management platform that offers security awareness training, cloud email security, phishing protection, real-time coaching, compliance training, and AI defense agents. The platform integrates AI to help organizations drive awareness, change user behavior, and reduce human risk. KnowBe4 is trusted by 70,000 organizations worldwide and is known for its comprehensive security products and customer-centric approach.
Abnormal
Abnormal is an AI-powered platform that leverages superhuman understanding of human behavior to protect against email attacks such as phishing, social engineering, and account takeovers. The platform offers unified protection across email and cloud applications, behavioral anomaly detection, account compromise detection, data security, and autonomous AI agents for security operations. Abnormal is recognized as a leader in email security and AI-native security, trusted by over 3,000 customers, including 20% of the Fortune 500. The platform aims to autonomously protect humans, reduce risks, save costs, accelerate AI adoption, and provide industry-leading security solutions.
hCaptcha Enterprise
hCaptcha Enterprise is a comprehensive security platform that protects businesses from a wide range of online threats, including bots, fraud, and abuse. It uses advanced machine learning and threat intelligence to detect and block malicious activity, while providing a frictionless experience for legitimate users. hCaptcha Enterprise is easy to deploy and manage, and it can be customized to meet the specific needs of each business.
VOLT AI
VOLT AI is a cloud-based enterprise security application that utilizes advanced AI technology to intercept threats in real-time. The application offers solutions for various industries such as education, corporate, and cities, focusing on perimeter security, medical emergencies, and weapons detection. VOLT AI provides features like unified cameras, video intelligence, real-time notifications, automated escalations, and digital twin creation for advanced situational awareness. The application aims to enhance safety and security by detecting security risks and notifying users promptly.
Endor Labs
Endor Labs is an AI-powered software supply chain security solution that helps organizations manage their software bills of materials (SBOM), secure their open source dependencies, optimize CI/CD pipeline security, and enhance application security with secret detection. The platform offers advanced features such as AI-assisted OSS selection, compliance management, reachability-based SCA, and repository security posture management. Endor Labs aims to streamline security processes, reduce false positives, and provide actionable insights to improve software supply chain security.
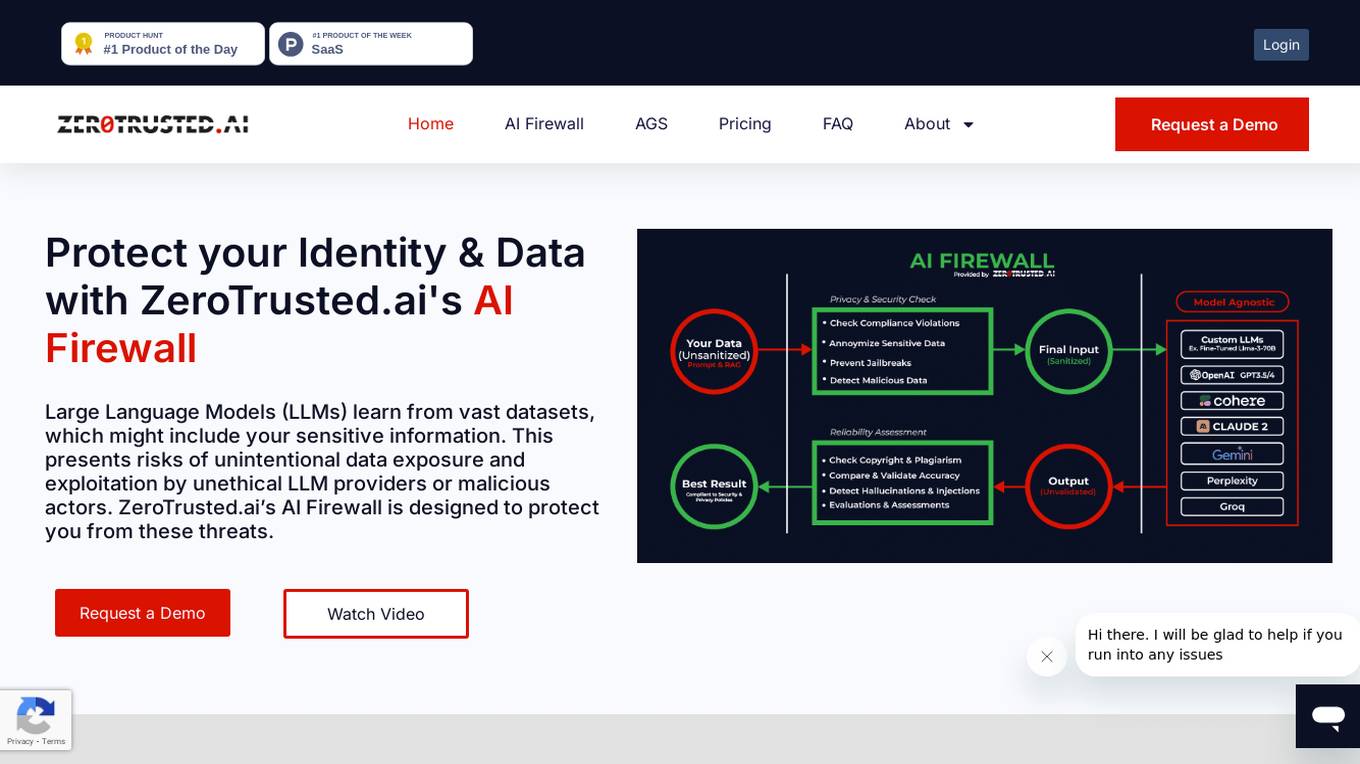
ZeroTrusted.ai
ZeroTrusted.ai is a cybersecurity platform that offers an AI Firewall to protect users from data exposure and exploitation by unethical providers or malicious actors. The platform provides features such as anonymity, security, reliability, integrations, and privacy to safeguard sensitive information. ZeroTrusted.ai empowers organizations with cutting-edge encryption techniques, AI & ML technologies, and decentralized storage capabilities for maximum security and compliance with regulations like PCI, GDPR, and NIST.
SafeSpeak
SafeSpeak is an AI-powered mobile security solution that protects users from phone scams, SIM swaps, and other malicious activities. It uses advanced machine learning and large language models to detect and block threats in real-time. SafeSpeak offers a range of features for both personal and business use, including malicious behavior detection, community immunity, SIM swap detection, weekly and monthly reporting, quick and easy setup, admin dashboard, extensible API, custom reporting, and visibility into tactics, techniques, and procedures (TTPs).
SurePath AI
SurePath AI is an AI platform solution company that governs the workforce use of GenAI. It provides solutions for detecting usage, mitigating risks, and controlling enterprise data access. SurePath AI offers a secure path for GenAI adoption by spotting, securing, and streamlining GenAI use effortlessly. The platform helps prevent data leaks, control access to private models and enterprise data, and manage access to public and private models. It also provides insights and analytics into user activity, policy enforcement, and potential risks.
Hive Defender
Hive Defender is an advanced, machine-learning-powered DNS security service that offers comprehensive protection against a vast array of cyber threats including but not limited to cryptojacking, malware, DNS poisoning, phishing, typosquatting, ransomware, zero-day threats, and DNS tunneling. Hive Defender transcends traditional cybersecurity boundaries, offering multi-dimensional protection that monitors both your browser traffic and the entirety of your machine’s network activity.
Vidrovr
Vidrovr is a video analysis platform that uses machine learning to process unstructured video, image, or audio data. It provides business insights to help drive revenue, make strategic decisions, and automate monotonous processes within a business. Vidrovr's technology can be used to minimize equipment downtime, proactively plan for equipment replacement, leverage AI to empower mission objectives and decision making, monitor persons or topics of interest across various media sources, ensure critical infrastructure is monitored 24/7/365, and protect ecological assets.
Wing Security
Wing Security is a SaaS Security Posture Management (SSPM) solution that helps businesses protect their data by providing full visibility and control over applications, users, and data. The platform offers features such as automated remediation, AI discovery, real-time SaaS visibility, vendor risk management, insider risk management, and more. Wing Security enables organizations to eliminate risky applications, manage user behavior, and protect sensitive data from unauthorized access. With a focus on security first, Wing Security helps businesses leverage the benefits of SaaS while staying protected.
Ambient.ai
Ambient.ai is an AI-powered physical security software that helps prevent security incidents by detecting threats in real-time, auto-clearing false alarms, and accelerating investigations. The platform uses computer vision intelligence to monitor cameras for suspicious activities, decrease alarms, and enable rapid investigations. Ambient.ai offers rich integration ecosystem, detections for a spectrum of threats, unparalleled operational efficiency, and enterprise-grade privacy to ensure maximum security and efficiency for its users.
0 - Open Source Tools
20 - OpenAI Gpts
Cyber Shielder
Expert in cyber security (NIST, OWASP, NIS2, MITRE ATT&CK, DORA) and GDPR, offering clear and concise guidance.
Secure Space Advisor
Technical satellite security expert trained on space focused cybersecurity frameworks, best practices and process.
CyberNews GPT
CyberNews GPT is an assistant that provides the latest security news about cyber threats, hackings and breaches, malware, zero-day vulnerabilities, phishing, scams and so on.
Mónica
CSIRT que lidera un equipo especializado en detectar y responder a incidentes de seguridad, maneja la contención y recuperación, organiza entrenamientos y simulacros, elabora reportes para optimizar estrategias de seguridad y coordina con entidades legales cuando es necesario
Blue Team Guide
it is a meticulously crafted arsenal of knowledge, insights, and guidelines that is shaped to empower organizations in crafting, enhancing, and refining their cybersecurity defenses
弍号機 まもる ISO Guardian
ISO27001およびISO/IEC 27002のベストプラクティスに精通したアドバイザー Expert in ISO27001 and ISO/IEC 27002 best practices.
Your personal GRC & Security Tutor
A training tool for infosec professionals to improve their skills in GRC & security and help obtain related certifications.