Best AI tools for< It Security Manager >
Infographic
20 - AI tool Sites

Start Left® Security
Start Left® Security is an AI-driven application security posture management platform that empowers product teams to automate secure-by-design software from people to cloud. The platform integrates security into every facet of the organization, offering a unified solution that aligns with business goals, fosters continuous improvement, and drives innovation. Start Left® Security provides a gamified DevSecOps experience with comprehensive security capabilities like SCA, SBOM, SAST, DAST, Container Security, IaC security, ASPM, and more.
Mimecast
Mimecast is an AI-powered email and collaboration security application that offers advanced threat protection, cloud archiving, security awareness training, and more. With a focus on protecting communications, data, and people, Mimecast leverages AI technology to provide industry-leading security solutions to organizations globally. The application is designed to defend against sophisticated email attacks, enhance human risk management, and streamline compliance processes.
Varonis
Varonis is an AI-powered data security platform that provides end-to-end data security solutions for organizations. It offers automated outcomes to reduce risk, enforce policies, and stop active threats. Varonis helps in data discovery & classification, data security posture management, data-centric UEBA, data access governance, and data loss prevention. The platform is designed to protect critical data across multi-cloud, SaaS, hybrid, and AI environments.
Cyguru
Cyguru is an all-in-one cloud-based AI Security Operation Center (SOC) that offers a comprehensive range of features for a robust and secure digital landscape. Its Security Operation Center is the cornerstone of its service domain, providing AI-Powered Attack Detection, Continuous Monitoring for Vulnerabilities and Misconfigurations, Compliance Assurance, SecPedia: Your Cybersecurity Knowledge Hub, and Advanced ML & AI Detection. Cyguru's AI-Powered Analyst promptly alerts users to any suspicious behavior or activity that demands attention, ensuring timely delivery of notifications. The platform is accessible to everyone, with up to three free servers and subsequent pricing that is more than 85% below the industry average.
Knostic AI
Knostic AI is an AI application that focuses on Copilot Readiness for Enterprise AI Security. It helps organizations locate and remediate data leaks from AI searches, ensuring data security and compliance. Knostic offers solutions to prevent data leakage, map knowledge boundaries, recommend permission adjustments, and provide independent verification of security posture readiness for AI adoption.
KnowBe4
KnowBe4 is a human risk management platform that offers security awareness training, cloud email security, phishing protection, real-time coaching, compliance training, and AI defense agents. The platform integrates AI to help organizations drive awareness, change user behavior, and reduce human risk. KnowBe4 is trusted by 70,000 organizations worldwide and is known for its comprehensive security products and customer-centric approach.
Abnormal
Abnormal is an AI-powered platform that leverages superhuman understanding of human behavior to protect against email attacks such as phishing, social engineering, and account takeovers. The platform offers unified protection across email and cloud applications, behavioral anomaly detection, account compromise detection, data security, and autonomous AI agents for security operations. Abnormal is recognized as a leader in email security and AI-native security, trusted by over 3,000 customers, including 20% of the Fortune 500. The platform aims to autonomously protect humans, reduce risks, save costs, accelerate AI adoption, and provide industry-leading security solutions.
hCaptcha Enterprise
hCaptcha Enterprise is a comprehensive security platform that protects businesses from a wide range of online threats, including bots, fraud, and abuse. It uses advanced machine learning and threat intelligence to detect and block malicious activity, while providing a frictionless experience for legitimate users. hCaptcha Enterprise is easy to deploy and manage, and it can be customized to meet the specific needs of each business.
Endor Labs
Endor Labs is an AI-powered software supply chain security solution that helps organizations manage their software bills of materials (SBOM), secure their open source dependencies, optimize CI/CD pipeline security, and enhance application security with secret detection. The platform offers advanced features such as AI-assisted OSS selection, compliance management, reachability-based SCA, and repository security posture management. Endor Labs aims to streamline security processes, reduce false positives, and provide actionable insights to improve software supply chain security.
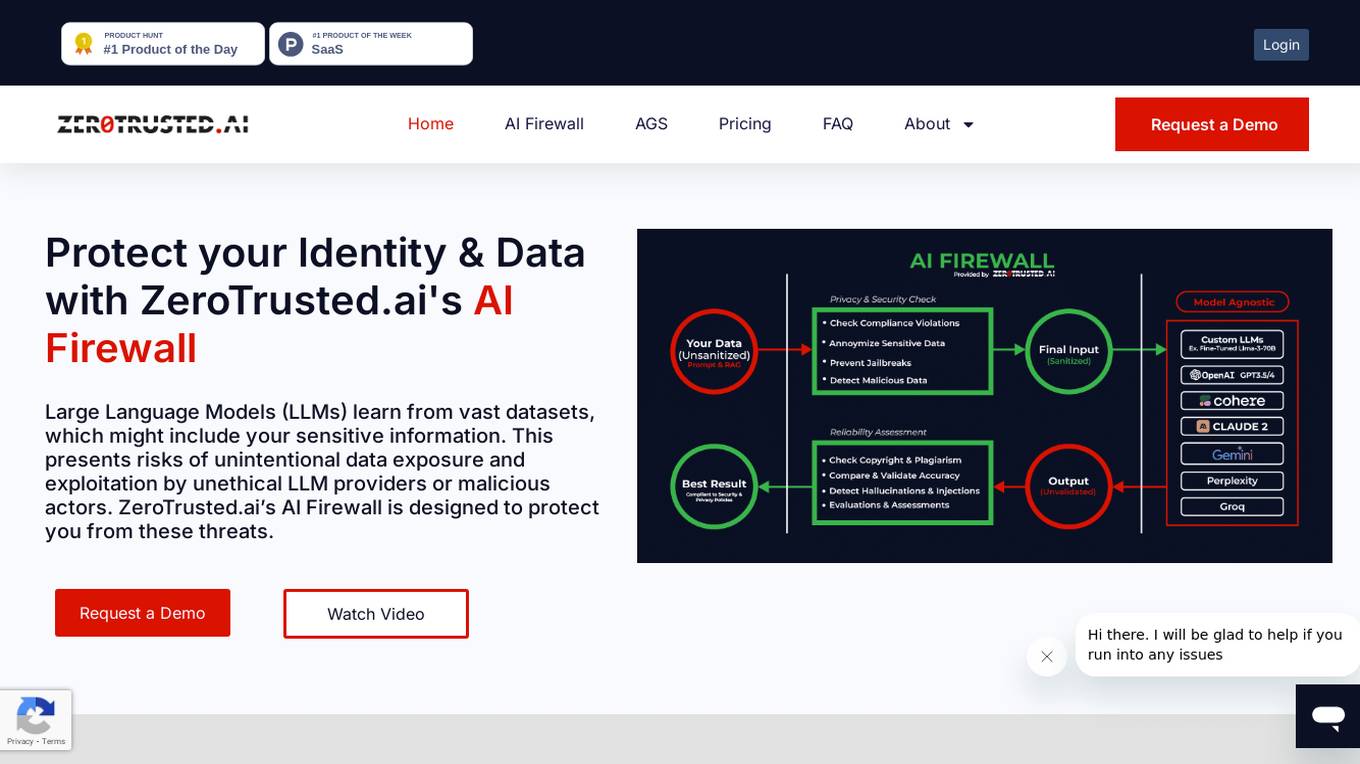
ZeroTrusted.ai
ZeroTrusted.ai is a cybersecurity platform that offers an AI Firewall to protect users from data exposure and exploitation by unethical providers or malicious actors. The platform provides features such as anonymity, security, reliability, integrations, and privacy to safeguard sensitive information. ZeroTrusted.ai empowers organizations with cutting-edge encryption techniques, AI & ML technologies, and decentralized storage capabilities for maximum security and compliance with regulations like PCI, GDPR, and NIST.
SurePath AI
SurePath AI is an AI platform solution company that governs the workforce use of GenAI. It provides solutions for detecting usage, mitigating risks, and controlling enterprise data access. SurePath AI offers a secure path for GenAI adoption by spotting, securing, and streamlining GenAI use effortlessly. The platform helps prevent data leaks, control access to private models and enterprise data, and manage access to public and private models. It also provides insights and analytics into user activity, policy enforcement, and potential risks.
Hive Defender
Hive Defender is an advanced, machine-learning-powered DNS security service that offers comprehensive protection against a vast array of cyber threats including but not limited to cryptojacking, malware, DNS poisoning, phishing, typosquatting, ransomware, zero-day threats, and DNS tunneling. Hive Defender transcends traditional cybersecurity boundaries, offering multi-dimensional protection that monitors both your browser traffic and the entirety of your machine’s network activity.
Exabeam
Exabeam is a cybersecurity and compliance platform that offers Security Information and Event Management (SIEM) solutions. The platform provides flexible choices for threat detection, investigation, and response, whether through cloud-based AI-driven solutions or on-premises SIEM deployments. Exabeam's AI-driven Security Operations Platform combines advanced threat detection capabilities with automation to deliver faster and more accurate TDIR. With features like UEBA, SOAR, and insider threat detection, Exabeam helps organizations improve security posture and optimize investments. The platform supports various industries and use cases, offering pre-built content, behavioral analytics, and context enrichment for enhanced threat coverage and compliance.
SharkGate
SharkGate is an AI-driven cybersecurity platform that focuses on protecting websites from various cyber threats. The platform offers solutions for mobile security, password management, quantum computing threats, API security, and cloud security. SharkGate leverages artificial intelligence and machine learning to provide advanced threat detection and response capabilities, ensuring the safety and integrity of digital assets. The platform has received accolades for its innovative approach to cybersecurity and has secured funding from notable organizations.
Veriti
Veriti is an AI-driven platform that proactively monitors and safely remediates exposures across the entire security stack, without disrupting the business. It helps organizations maximize their security posture while ensuring business uptime. Veriti offers solutions for safe remediation, MITRE ATT&CK®, healthcare, MSSPs, and manufacturing. The platform correlates exposures to misconfigurations, continuously assesses exposures, integrates with various security solutions, and prioritizes remediation based on business impact. Veriti is recognized for its role in exposure assessments and remediation, providing a consolidated security platform for businesses to neutralize threats before they happen.
BforeAI
BforeAI is an AI-powered platform that specializes in fighting cyberthreats with intelligence. The platform offers predictive security solutions to prevent phishing, spoofing, impersonation, hijacking, ransomware, online fraud, and data exfiltration. BforeAI uses cutting-edge AI technology for behavioral analysis and predictive results, going beyond reactive blocklists to predict and prevent attacks before they occur. The platform caters to various industries such as financial, manufacturing, retail, and media & entertainment, providing tailored solutions to address unique security challenges.
Vectra AI
Vectra AI is a leading AI security platform that helps organizations stop advanced cyber attacks by providing an integrated signal for extended detection and response (XDR). The platform arms security analysts with real-time intelligence to detect, prioritize, investigate, and respond to threats across network, identity, cloud, and managed services. Vectra AI's AI-driven detections and Attack Signal Intelligence enable organizations to protect against various attack types and emerging threats, enhancing cyber resilience and reducing risks in critical infrastructure, cloud environments, and remote workforce scenarios. Trusted by over 1100 enterprises worldwide, Vectra AI is recognized for its expertise in AI security and its ability to stop sophisticated attacks that other technologies may miss.
Darktrace
Darktrace is a cybersecurity platform that leverages AI technology to provide proactive protection against cyber threats. It offers cloud-native AI security solutions for networks, emails, cloud environments, identity protection, and endpoint security. Darktrace's AI Analyst investigates alerts at the speed and scale of AI, mimicking human analyst behavior. The platform also includes services such as 24/7 expert support and incident management. Darktrace's AI is built on a unique approach where it learns from the organization's data to detect and respond to threats effectively. The platform caters to organizations of all sizes and industries, offering real-time detection and autonomous response to known and novel threats.
Breacher.ai
Breacher.ai is an AI-powered cybersecurity solution that specializes in deepfake detection and protection. It offers a range of services to help organizations guard against deepfake attacks, including deepfake phishing simulations, awareness training, micro-curriculum, educational videos, and certification. The platform combines advanced AI technology with expert knowledge to detect, educate, and protect against deepfake threats, ensuring the security of employees, assets, and reputation. Breacher.ai's fully managed service and seamless integration with existing security measures provide a comprehensive defense strategy against deepfake attacks.
rooftops.ai
rooftops.ai is an AI-powered platform that focuses on security verification for online connections. It ensures the safety and integrity of user interactions by reviewing security measures before granting access. The platform utilizes advanced algorithms to detect and prevent potential threats, providing a secure environment for users to engage online.
0 - Open Source Tools
20 - OpenAI Gpts
IT Log Creator
Formal, technical expert in creating realistic, fictional IT logs. Contact: [email protected]
Blue Team Guide
it is a meticulously crafted arsenal of knowledge, insights, and guidelines that is shaped to empower organizations in crafting, enhancing, and refining their cybersecurity defenses
Tech Timekeeper
IT expert creating a daily IT-themed calendar with concise histories and pen drawings.
Password Guardian
I create ultra-secure, random passwords and offer concise security tips.
Securia
AI-powered audit ally. Enhance cybersecurity effortlessly with intelligent, automated security analysis. Safe, swift, and smart.
Guardian AI VPN
I'm GPTGuardian VPN, enhancing your GPT experience with top security and connectivity.
👑 Data Privacy for Insurance Companies 👑
Insurance providers collect and process personal health, financial, and property information, making it crucial to implement comprehensive data protection strategies.
👑 Data Privacy for Social Media Companies 👑
Data Privacy for Social Media Companies & Platforms collect detailed personal information, preferences, and interactions of users, making it essential to have strong data privacy policies and practices in place.

VulnGPT
Your ally in navigating the CVE deluge. Expert insights for prioritizing and remediating vulnerabilities.