Best AI tools for< It Security Consultant >
Infographic
10 - AI tool Sites
Loudfame
Loudfame.com is a website that appears to be experiencing a privacy error related to an expired security certificate. The site may be at risk of attackers trying to steal sensitive information such as passwords, messages, or credit card details. Users are advised to proceed with caution due to the security concerns highlighted on the page.

Metasoma Web Security
The website www.metasoma.ai is experiencing a privacy error due to an expired security certificate. Users are warned that their information may be at risk of theft. The site is advised to enhance security measures to protect user data and prevent potential attacks.
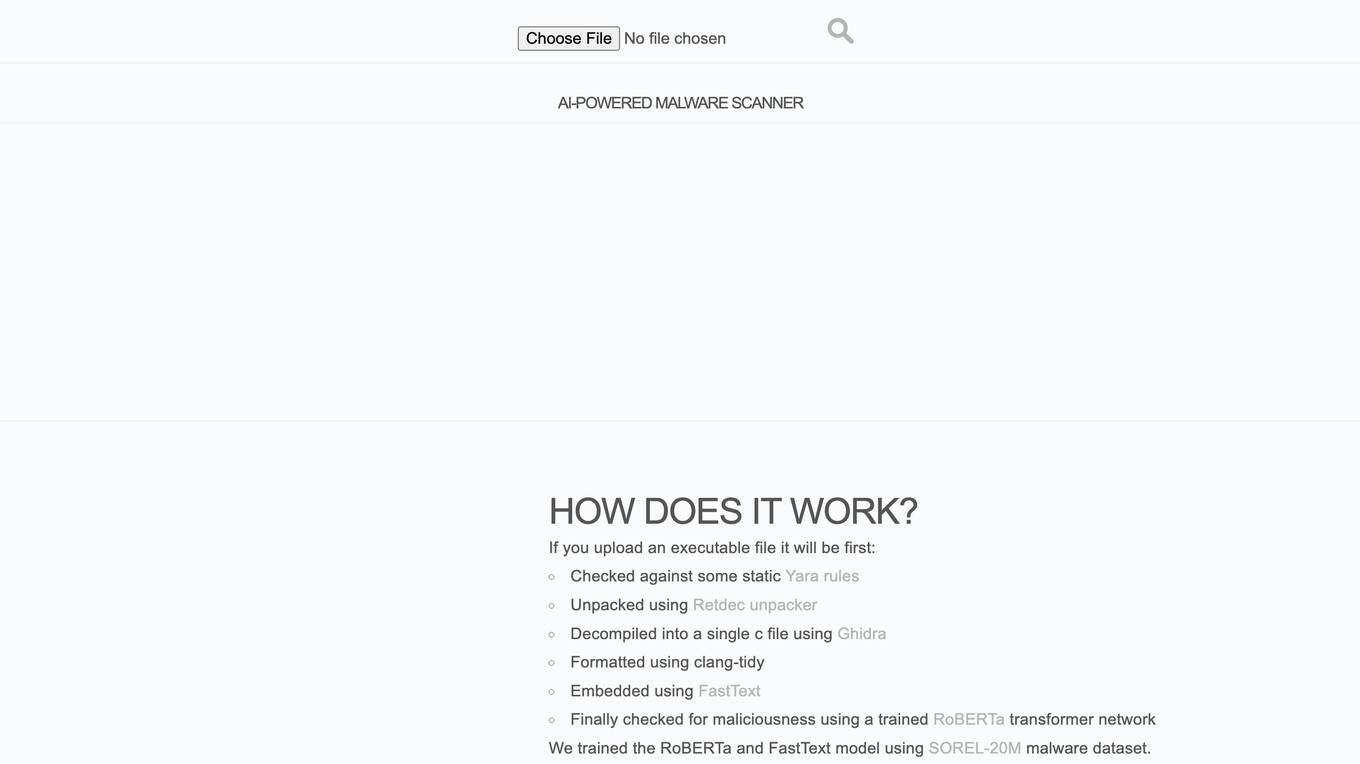
SecureWoof
SecureWoof is an AI-powered Malware Scanner that utilizes advanced technologies such as Yara rules, Retdec unpacker, Ghidra decompiler, clang-tidy formatter, FastText embedding, and RoBERTa transformer network to scan and detect malicious content in executable files. The tool is trained on the SOREL-20M malware dataset to enhance its detection capabilities.

Maximus.guru
Maximus.guru is a website that provides information about a security certificate error related to the domain maximus.guru. The site warns users about potential privacy risks and advises on actions to take in response to the security certificate expiration. It offers insights into the certificate details, expiration date, and potential security threats that users may face. The website aims to educate users on security best practices and how to address security issues related to website connections.
eightify.app
The website eightify.app is a security service powered by Cloudflare to protect itself from online attacks. It helps in preventing unauthorized access and malicious activities on the website by blocking potential threats. Users may encounter a block if they trigger certain actions like submitting specific words or phrases, SQL commands, or malformed data. In such cases, they can contact the site owner to resolve the issue by providing details of the blocked activity and the Cloudflare Ray ID.
Cloudflare Security Service
The website theleap.co is a security service powered by Cloudflare to protect websites from online attacks. It helps in preventing unauthorized access and malicious activities by implementing security measures such as blocking certain actions that could potentially harm the website. Users may encounter a block if they trigger security alerts by submitting suspicious content or commands. In such cases, they are prompted to contact the site owner for resolution.

uselumin.co
The website uselumin.co is experiencing a privacy error related to an invalid security certificate. The error message indicates a potential security threat where attackers may attempt to steal sensitive information such as passwords, messages, or credit card details. The site's security certificate is issued by 'atlahealthcare.com' and expires on May 8, 2026. The error message advises caution when accessing the site due to the security risk posed by the invalid certificate.

yujo.io.tilda.ws
The website yujo.io.tilda.ws is experiencing a privacy error related to its security certificate. Users are warned that their connection may not be private, potentially exposing sensitive information like passwords, messages, or credit card details to attackers. The site's security certificate is not trusted by the computer's operating system, leading to a warning message for users. The error message advises caution and suggests that the issue may be due to misconfiguration or a potential attack on the connection. Users are given the option to proceed to the site at their own risk, despite the security concerns.
rooftops.ai
rooftops.ai is an AI-powered platform that focuses on security verification for online connections. It ensures the safety and integrity of user interactions by reviewing security measures before granting access. The platform utilizes advanced algorithms to detect and prevent potential threats, providing a secure environment for users to engage online.
Sider.ai
Sider.ai is an AI-powered platform that focuses on security verification for online connections. It ensures a safe browsing experience by reviewing the security of your connection before proceeding. The platform uses advanced algorithms to detect and prevent potential threats, providing users with peace of mind while browsing the internet.
2 - Open Source Tools
AIO-Firebog-Blocklists
AIO-Firebog-Blocklists is a comprehensive tool that combines various sources into a single, cohesive blocklist. It offers customizable options to suit individual preferences and needs, ensuring regular updates to stay up-to-date with the latest threats. The tool focuses on performance optimization to minimize impact while maintaining effective filtering. It is designed to help users with ad blocking, malware protection, tracker prevention, and content filtering.
hashbrown
Hashbrown is a lightweight and efficient hashing library for Python, designed to provide easy-to-use cryptographic hashing functions for secure data storage and transmission. It supports a variety of hashing algorithms, including MD5, SHA-1, SHA-256, and SHA-512, allowing users to generate hash values for strings, files, and other data types. With Hashbrown, developers can quickly implement data integrity checks, password hashing, digital signatures, and other security features in their Python applications.
20 - OpenAI Gpts
Website Security with Jim Walker | HackRepair.com
Jim Walker "The Hack Repair Guy" is a WordPress Security Expert. He Manages HackRepair.com and HackGuard.com, a Malware Cleanup and WordPress Management Service.
Incident Response Forensic Techniques
help organizations in investigating computer security incidents and troubleshooting some information technology (IT) operational problems by providing practical guidance on performing computer and network forensics.
IT Log Creator
Formal, technical expert in creating realistic, fictional IT logs. Contact: [email protected]
Blue Team Guide
it is a meticulously crafted arsenal of knowledge, insights, and guidelines that is shaped to empower organizations in crafting, enhancing, and refining their cybersecurity defenses
Password Guardian
I create ultra-secure, random passwords and offer concise security tips.
Tech Timekeeper
IT expert creating a daily IT-themed calendar with concise histories and pen drawings.
Aegis ⛨
Interactive Cybersecurity Tutor capable of autonomous management of your knowledge.
Cyber Audit and Pentest RFP Builder
Generates cybersecurity audit and penetration test specifications.

Sikich CMMC Coach
CMMC Coach: Guiding through CMMC processes with tailored strategies, interactive training, and regulatory compliance. https://www.sikich.com/technology/contact-us/ 877.403.5227 | [email protected]
Wireless Communications Advisor
Advises on wireless communication technologies to enhance organizational efficiency.
DevSecOps Guides
Comprehensive resource for integrating security into the software development lifecycle.